0x01 部署
靶机地址:
根据靶机说明,需要找到5个flag
下载镜像, 使用vmware打开, 网络选择NAT模式
0x02 信息收集
nmap扫描网段
nmap -sP 192.168.190.0/24
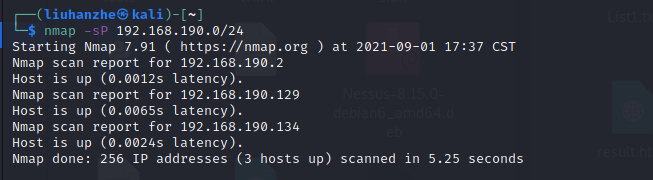
发现目标IP:192.168.190.134
进一步扫描端口
nmap -T5 -A -v -p- 192.168.190.134
扫描结果:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-01 17:38 CST
Happy 24th Birthday to Nmap, may it live to be 124!
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 17:38
Completed NSE at 17:38, 0.00s elapsed
Initiating NSE at 17:38
Completed NSE at 17:38, 0.00s elapsed
Initiating NSE at 17:38
Completed NSE at 17:38, 0.00s elapsed
Initiating Ping Scan at 17:38
Scanning 192.168.190.134 [2 ports]
Completed Ping Scan at 17:38, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 17:38
Completed Parallel DNS resolution of 1 host. at 17:38, 0.00s elapsed
Initiating Connect Scan at 17:38
Scanning 192.168.190.134 [65535 ports]
Discovered open port 80/tcp on 192.168.190.134
Discovered open port 22/tcp on 192.168.190.134
Discovered open port 111/tcp on 192.168.190.134
Discovered open port 48247/tcp on 192.168.190.134
Completed Connect Scan at 17:38, 2.57s elapsed (65535 total ports)
Initiating Service scan at 17:38
Scanning 4 services on 192.168.190.134
Completed Service scan at 17:38, 11.01s elapsed (4 services on 1 host)
NSE: Script scanning 192.168.190.134.
Initiating NSE at 17:38
Completed NSE at 17:39, 1.62s elapsed
Initiating NSE at 17:39
Completed NSE at 17:39, 0.11s elapsed
Initiating NSE at 17:39
Completed NSE at 17:39, 0.00s elapsed
Nmap scan report for 192.168.190.134
Host is up (0.00019s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0)
| ssh-hostkey




 本文详细记录了在Vulnhub上的DC1靶机攻防过程,从部署到信息收集,再到Drupal漏洞利用,最终实现权限提升找到所有flag。在信息收集阶段,通过nmap发现运行Drupal的80端口。利用Drupal已知漏洞,获取Meterpreter shell。通过数据库操作、密码破解和提权技巧,逐步揭示隐藏的flag。
本文详细记录了在Vulnhub上的DC1靶机攻防过程,从部署到信息收集,再到Drupal漏洞利用,最终实现权限提升找到所有flag。在信息收集阶段,通过nmap发现运行Drupal的80端口。利用Drupal已知漏洞,获取Meterpreter shell。通过数据库操作、密码破解和提权技巧,逐步揭示隐藏的flag。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 462
462

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








