最近当你使用Xcode的Application Loader工具,上传应用程序,需要输入您的苹果开发者账户时,会发现Application loader无法登录账户,而是提示使用app-specific密码登录,原来的密码已经无法正常登录了。
此时就需要重新生成一个app-specific密码,具体步骤如下:
- 打开 Appleid.apple.com ,并使用你的苹果账号登录。
- 进行双重验证,参考https://blog.youkuaiyun.com/fzhlee/article/details/88344723
-
然后在 Security 区域, 选择 Generate Passwords.

- 输入密码的 label 。
-
然后点击 Create.
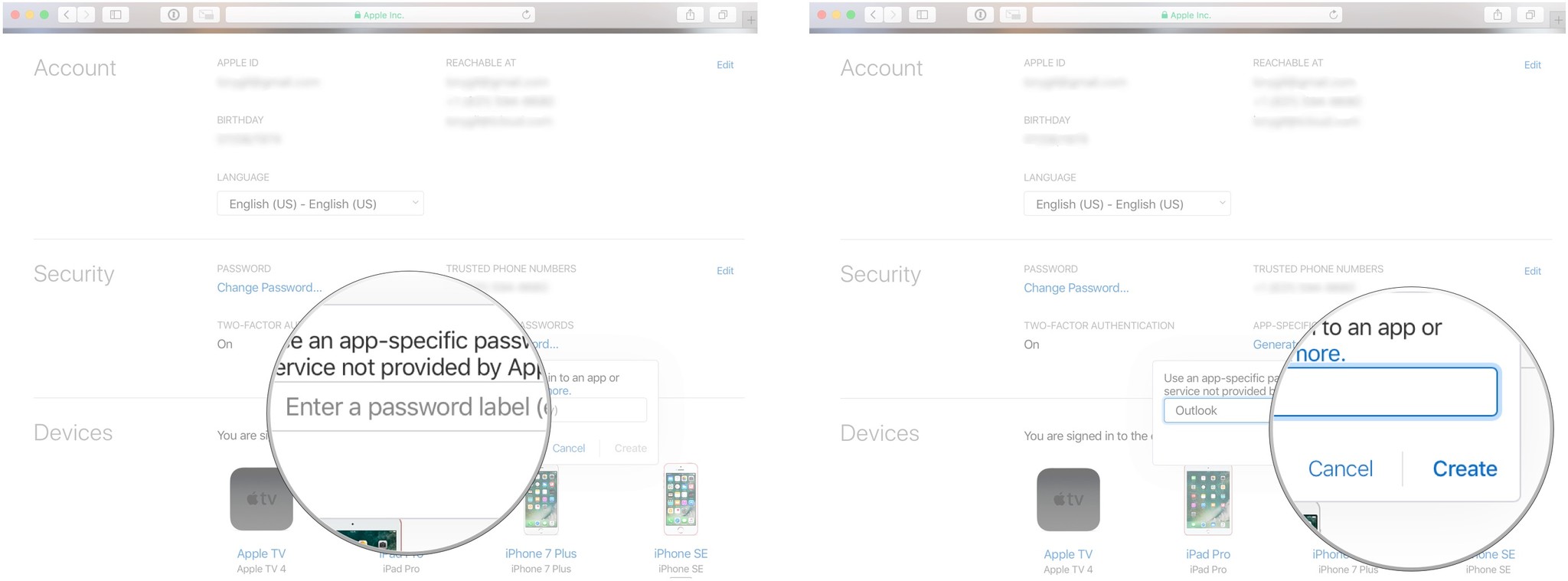
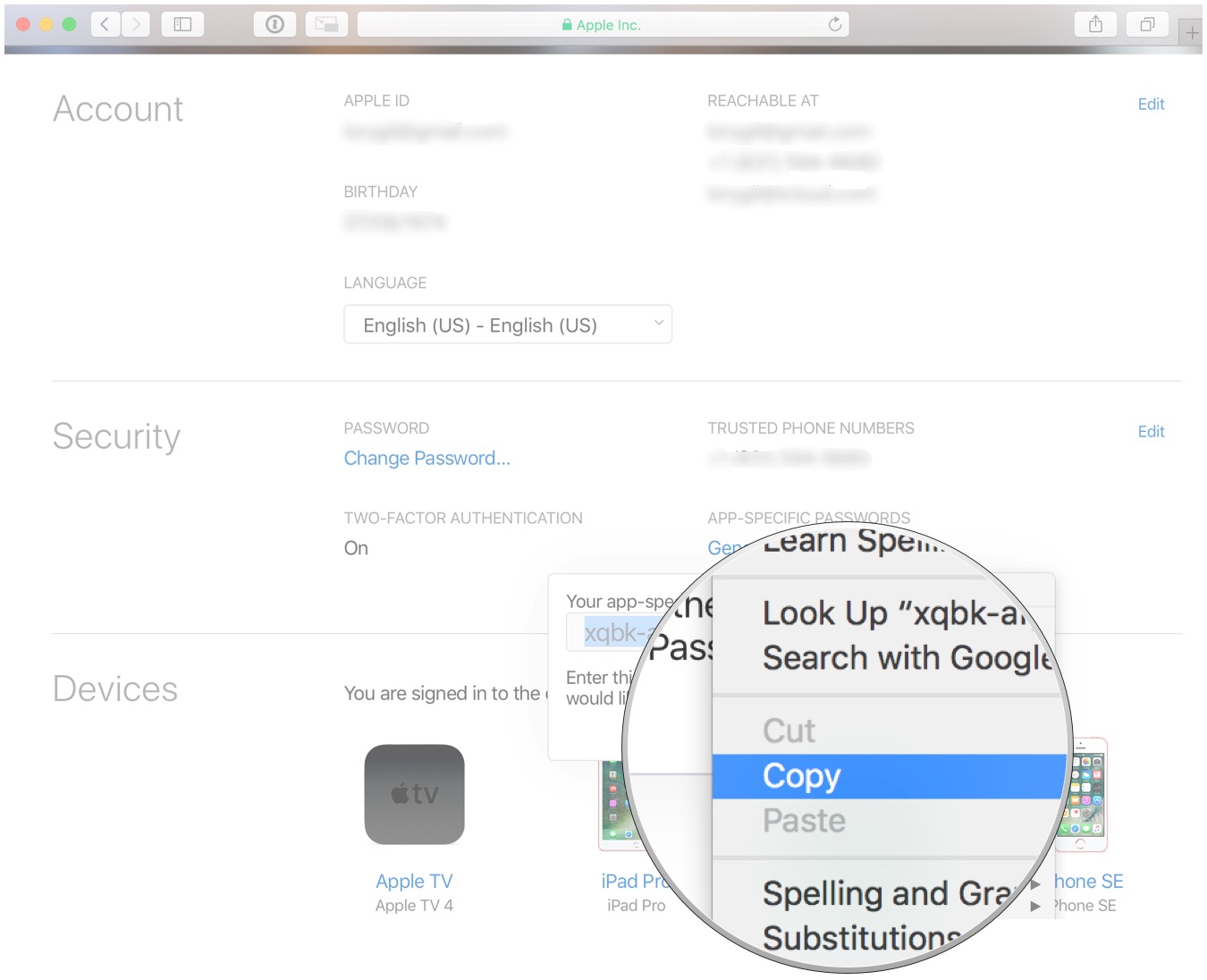
-
最后拷贝生成的 app-specific password即可.









 当使用Xcode的ApplicationLoader工具上传应用遇到无法登录的问题时,本文指导您如何通过生成app-specific密码解决。步骤包括登录Appleid.apple.com,进行双重验证,访问Security区域并创建新的app-specific密码。
当使用Xcode的ApplicationLoader工具上传应用遇到无法登录的问题时,本文指导您如何通过生成app-specific密码解决。步骤包括登录Appleid.apple.com,进行双重验证,访问Security区域并创建新的app-specific密码。

















 9003
9003

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










