scanner.py
#!/usr/bin/env python3
"""
域名漏洞扫描脚本
功能:子域名枚举、端口扫描、服务识别、常见漏洞检测
"""
import requests
import socket
import threading
import subprocess
import json
import time
from urllib.parse import urljoin
import dns.resolver
import ssl
import argparse
from concurrent.futures import ThreadPoolExecutor
class DomainVulnerabilityScanner:
def __init__(self, domain, threads=50):
self.domain = domain
self.threads = threads
self.results = {
'domain': domain,
'subdomains': [],
'open_ports': [],
'vulnerabilities': [],
'services': [],
'ssl_info': {}
}
def subdomain_enumeration(self):
"""子域名枚举"""
print(f"[+] 开始子域名枚举: {self.domain}")
# 常见子域名列表
common_subdomains = [
'www', 'mail', 'ftp', 'localhost', 'webmail', 'smtp', 'pop', 'ns1', 'webdisk',
'ns2', 'cpanel', 'whm', 'autodiscover', 'autoconfig', 'm', 'imap', 'test',
'blog', 'pop3', 'dev', 'www2', 'admin', 'forum', 'news', 'vpn', 'ns3', 'mail2',
'new', 'mysql', 'old', 'lists', 'support', 'mobile', 'mx', 'static', 'docs',
'beta', 'shop', 'sql', 'secure', 'demo', 'cp', 'calendar', 'wiki', 'api',
'media', 'email', 'images', 'img', 'www1', 'intranet', 'portal', 'video',
'search', 'cdn', 'remote', 'db', 'forums', 'store', 'relay', 'files',
'newsletter', 'app', 'apps', 'download', 'uploads', 'dns', 'ns4', 'sftp'
]
found_subdomains = []
def check_subdomain(subdomain):
full_domain = f"{subdomain}.{self.domain}"
try:
socket.gethostbyname(full_domain)
found_subdomains.append(full_domain)
print(f" [+] 发现子域名: {full_domain}")
except socket.gaierror:
pass
with ThreadPoolExecutor(max_workers=self.threads) as executor:
executor.map(check_subdomain, common_subdomains)
self.results['subdomains'] = found_subdomains
return found_subdomains
def port_scan(self, host, ports=None):
"""端口扫描"""
if ports is None:
ports = [21, 22, 23, 25, 53, 80, 110, 443, 993, 995, 1433, 1521, 3306, 3389, 5432, 5900, 6379, 27017]
open_ports = []
def scan_port(port):
try:
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(3)
result = sock.connect_ex((host, port))
sock.close()
if result == 0:
service = self.get_service_name(port)
open_ports.append({'port': port, 'service': service})
print(f" [+] {host}:{port} 开放 - {service}")
except Exception:
pass
print(f"[+] 开始端口扫描: {host}")
with ThreadPoolExecutor(max_workers=self.threads) as executor:
executor.map(scan_port, ports)
return open_ports
def get_service_name(self, port):
"""获取服务名称"""
service_map = {
21: 'FTP', 22: 'SSH', 23: 'Telnet', 25: 'SMTP', 53: 'DNS',
80: 'HTTP', 110: 'POP3', 443: 'HTTPS', 993: 'IMAPS',
995: 'POP3S', 1433: 'MSSQL', 1521: 'Oracle', 3306: 'MySQL',
3389: 'RDP', 5432: 'PostgreSQL', 5900: 'VNC', 6379: 'Redis',
27017: 'MongoDB'
}
return service_map.get(port, 'Unknown')
def check_ssl_vulnerabilities(self, host):
"""检查SSL/TLS漏洞"""
print(f"[+] 检查SSL/TLS配置: {host}")
try:
context = ssl.create_default_context()
with socket.create_connection((host, 443), timeout=5) as sock:
with context.wrap_socket(sock, server_hostname=host) as ssock:
cert = ssock.getpeercert()
cipher = ssock.cipher()
ssl_info = {
'subject': dict(x[0] for x in cert['subject']),
'issuer': dict(x[0] for x in cert['issuer']),
'not_before': cert['notBefore'],
'not_after': cert['notAfter'],
'cipher': cipher
}
self.results['ssl_info'] = ssl_info
# 检查证书过期
import datetime
expire_date = datetime.datetime.strptime(cert['notAfter'], '%b %d %H:%M:%S %Y %Z')
if expire_date < datetime.datetime.now():
self.results['vulnerabilities'].append({
'type': 'SSL',
'severity': 'HIGH',
'description': 'SSL证书已过期',
'host': host
})
print(f" [+] SSL信息: {ssl_info}")
except Exception as e:
print(f" [-] SSL检查失败: {e}")
def web_vulnerability_scan(self, url):
"""Web应用漏洞扫描"""
print(f"[+] Web漏洞扫描: {url}")
vulnerabilities = []
# 检查常见安全头
try:
response = requests.get(url, timeout=10, verify=False)
headers = response.headers
security_headers = {
'X-Frame-Options': '点击劫持保护',
'X-Content-Type-Options': 'MIME类型嗅探保护',
'X-XSS-Protection': 'XSS保护',
'Strict-Transport-Security': 'HSTS',
'Content-Security-Policy': '内容安全策略'
}
for header, description in security_headers.items():
if header not in headers:
vulnerabilities.append({
'type': 'WEB',
'severity': 'MEDIUM',
'description': f'缺少安全头: {header} - {description}',
'url': url
})
except Exception as e:
print(f" [-] Web扫描失败: {e}")
return vulnerabilities
def run_full_scan(self):
"""执行完整扫描"""
print(f"[*] 开始对 {self.domain} 进行漏洞扫描")
start_time = time.time()
# 子域名枚举
subdomains = self.subdomain_enumeration()
# 扫描主域名
targets = [self.domain] + subdomains
for target in targets:
# 端口扫描
open_ports = self.port_scan(target)
self.results['open_ports'].extend(open_ports)
# SSL检查
if any(port['port'] == 443 for port in open_ports):
self.check_ssl_vulnerabilities(target)
# Web漏洞扫描
for port_info in open_ports:
if port_info['port'] in [80, 443, 8080, 8443]:
scheme = 'https' if port_info['port'] in [443, 8443] else 'http'
url = f"{scheme}://{target}:{port_info['port']}"
web_vulns = self.web_vulnerability_scan(url)
self.results['vulnerabilities'].extend(web_vulns)
# 生成报告
self.generate_report()
end_time = time.time()
print(f"\n[*] 扫描完成! 用时: {end_time - start_time:.2f}秒")
return self.results
def generate_report(self):
"""生成扫描报告"""
report = f"""
域名漏洞扫描报告
================
目标域名: {self.results['domain']}
扫描时间: {time.strftime('%Y-%m-%d %H:%M:%S')}
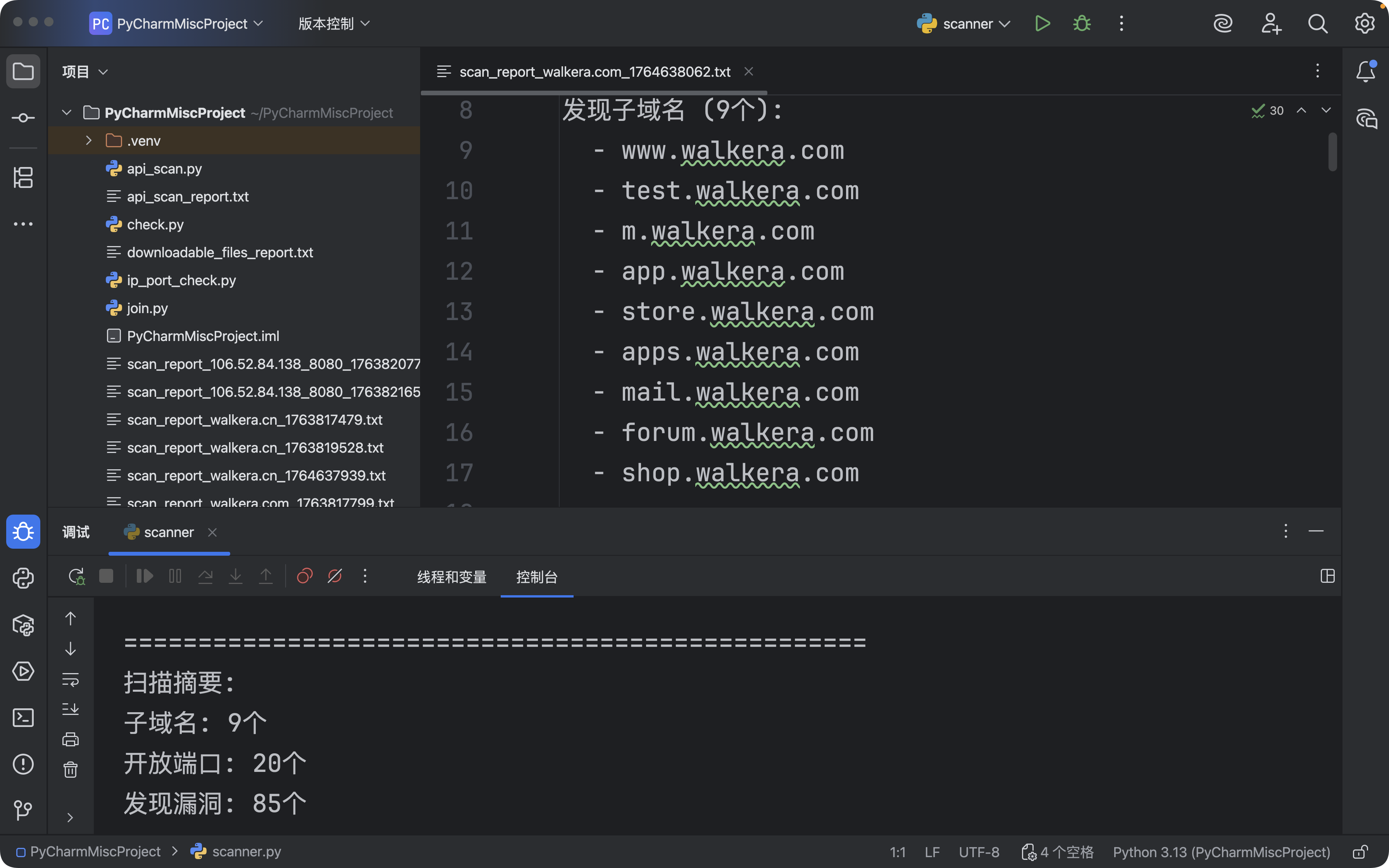
发现子域名 ({len(self.results['subdomains'])}个):
{chr(10).join([' - ' + sub for sub in self.results['subdomains']])}
开放端口:
{chr(10).join([f" - {item['host'] if 'host' in item else self.domain}:{item['port']} ({item['service']})" for item in self.results['open_ports']])}
发现漏洞 ({len(self.results['vulnerabilities'])}个):
"""
for i, vuln in enumerate(self.results['vulnerabilities'], 1):
report += f"""
{i}. 类型: {vuln['type']}
严重性: {vuln['severity']}
描述: {vuln['description']}
目标: {vuln.get('host', vuln.get('url', 'N/A'))}
"""
# 保存报告
filename = f"scan_report_{self.domain}_{int(time.time())}.txt"
with open(filename, 'w', encoding='utf-8') as f:
f.write(report)
print(f"[+] 报告已保存至: {filename}")
return report
def main():
parser = argparse.ArgumentParser(description='域名漏洞扫描器')
parser.add_argument('domain', help='要扫描的域名')
parser.add_argument('-t', '--threads', type=int, default=50, help='线程数 (默认: 50)')
args = parser.parse_args()
scanner = DomainVulnerabilityScanner(args.domain, args.threads)
results = scanner.run_full_scan()
# 输出摘要
print(f"\n{'=' * 50}")
print("扫描摘要:")
print(f"子域名: {len(results['subdomains'])}个")
print(f"开放端口: {len(results['open_ports'])}个")
print(f"发现漏洞: {len(results['vulnerabilities'])}个")
print(f"{'=' * 50}")
if __name__ == "__main__":
main()
扫描效果:























 1845
1845

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










