本文,我们分析UPDATE消息的处理过程
层3VPN 的UPDATE消息和前面的路由更新报文的接受处理是一样的,从解析属性的地方开始区别,报文如下图:
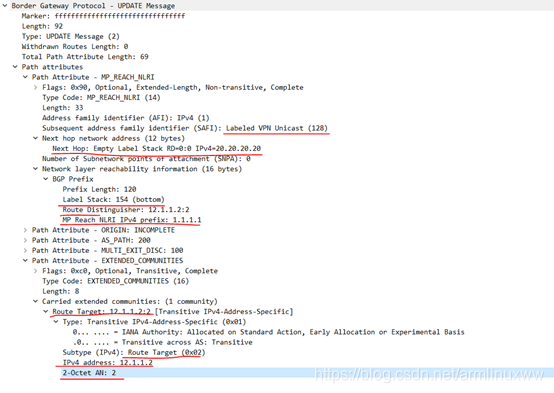
2019/12/26 09:32:44 BGP: : 20.20.20.20 rcvd UPDATE w/ attr: , origin ?, metric 100, extcommunity RT:12.1.1.2:2, path 200
2019/12/26 09:32:44 BGP: : 20.20.20.20 rcvd UPDATE wlen 0 attrlen 69 alen 0
2019/12/26 09:32:44 BGP: : 20.20.20.20 rcvd RD 12.1.1.2:2 1.1.1.1/32 label 154 IPv4 vpn
2019/12/26 09:32:44 BGP: : vpn_leak_to_vrf_update: start (path_vpn=0x5589ff3debf0)
2019/12/26 09:32:44 BGP: : vpn_leak_to_vrf_update_onevrf: skipping: import not set
2019/12/26 09:32:44 BGP: : vpn_leak_to_vrf_update_onevrf: updating 1.1.1.1/32 to vrf VRF 1
2019/12/26 09:32:44 BGP: : vpn_leak_to_vrf_update_onevrf: pfx 1.1.1.1/32: num_labels 1
2019/12/26 09:32:44 BGP: : leak_update: entry: leak-to=VRF 1, p=1.1.1.1/32, type=9, sub_type=0
2019/12/26 09:32:44 BGP: : leak_update: nexthop is valid (in vrf VRF default)
2019/12/26 09:32:44 BGP: : leak_update: ->VRF 1: 1.1.1.1/32: Added new route
2019/12/26 09:32:44 BGP: : group_announce_route_walkcb: afi=IPv4, safi=vpn, p=1.1.1.1/32
2019/12/26 09:32:44 BGP: : subgroup_process_announce_selected: p=1.1.1.1/32, selected=0x5589ff3debf0
2019/12/26 09:32:44 BGP: : bgp_zebra_announce: p=1.1.1.1/32, bgp_is_valid_label: 2
2019/12/26 09:32:44 BGP: : Tx route add VRF 7 1.1.1.1/32 metric 100 tag 0 count 1
2019/12/26 09:32:44 BGP: : nhop [1]: 20.20.20.20 if 0 VRF 0 label 154
2019/12/26 09:32:44 BGP: : bgp_zebra_announce: 1.1.1.1/32: announcing to zebra (recursion set)
2019/12/26 09:32:44 BGP: : u11:s11 send UPDATE w/ attr: , origin ?, extcommunity RT:12.1.1.2:2, path 200
2019/12/26 09:32:44 BGP: : u11:s11 send MP_REACH for afi/safi 1/128
2019/12/26 09:32:44 BGP: : u11:s11 send UPDATE RD 12.1.1.2:2 1.1.1.1/32 label 154 IPv4 vpn
2019/12/26 09:32:44 BGP: : u11:s11 send UPDATE len 89 numpfx 1
2019/12/26 09:32:44 BGP: : u11:s11 20.20.20.20 send UPDATE w/ nexthop 10.10.10.10 and RD
属性解析
在属性解析函数 bgp_attr_parse里面,我们分析和层3隧道相关的属性解析。
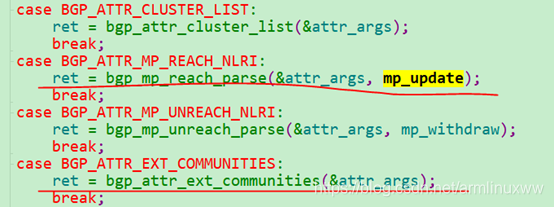
解析MP_REACH_NLRI
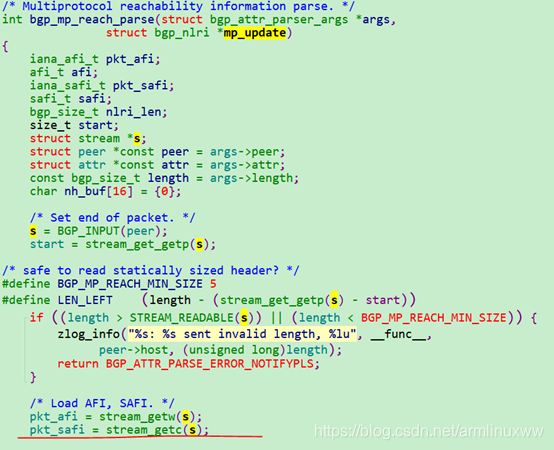
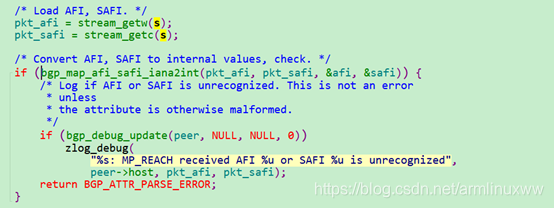
- 首先解析报文的afi和safi的值为1和128,然后转化为FRR 内部自己定义的afi和safi的值。
- 解析下一跳
获取下一跳的长度为12,然后获取RD(8字节),但没有存储,只是跳过,在获取IP地址4字节,存放在attr下一跳nexthop里面。
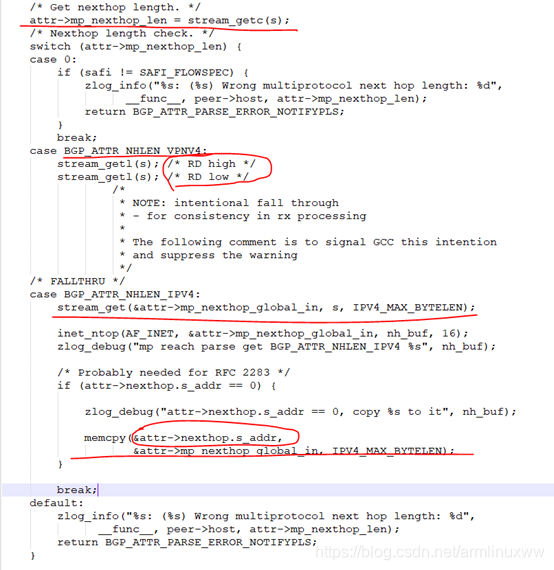
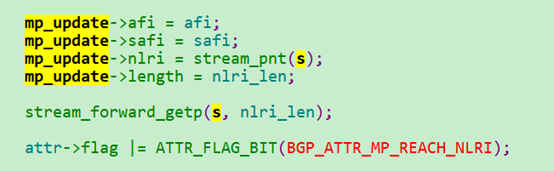
最后存放在bgp_nlri的NLRI_MP_UPDATE里面,nlri保存的是MP_REACH_NLRI信息。
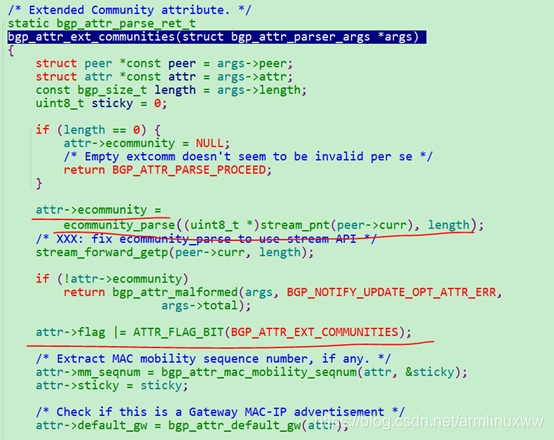
解析EXT_COMMUNITIES
NLRI处理
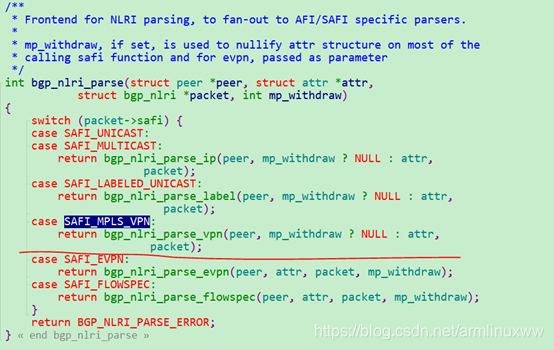
bgp_nlri_parse 函数里面由于前面解析的safi是SAFI_MPLS_VPN,所以NLRI的处理会是bgp_nlri_parse_vpn函数,主要处理过程如下,可以结合上面的报文一起看代码处理过程:
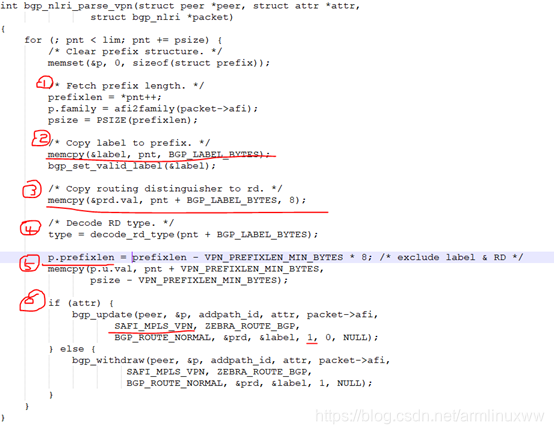
bgp_update 前面分析的时候,大概过程已经分析过了,下面会分析下,前面忽略的L3VPN相关的处理过程。
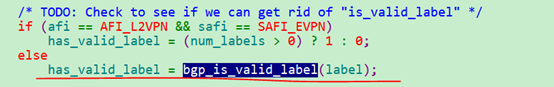
- has_valid_label处理会变成1,因为前面传入了解析出来的label值
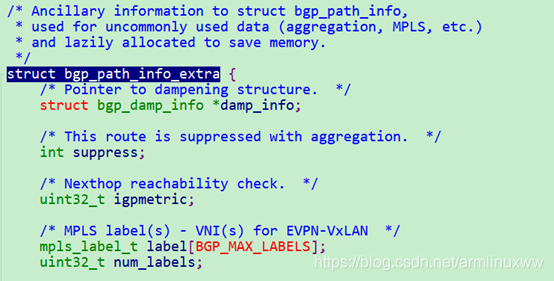
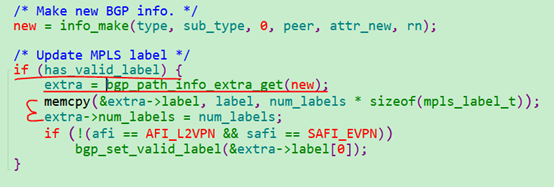
- 在构建struct bgp_path_info的时候,如果label有值,还需要构建struct bgp_path_info_extra,然后把label值存放在info_extra里面
- 把路由信息导入到VRF的BGP里面
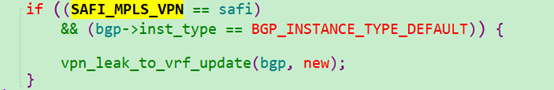
vpn_leak_to_vrf_update 函数处理有点长,主体处理的是把vpn peer收到的路由信息,导入到VRF的BGP里面
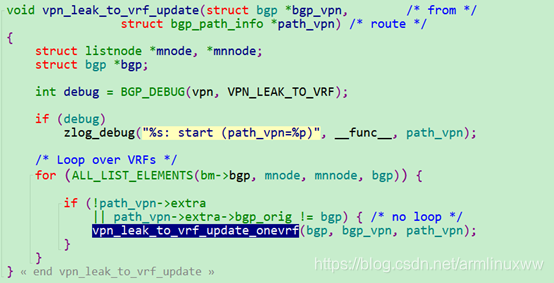
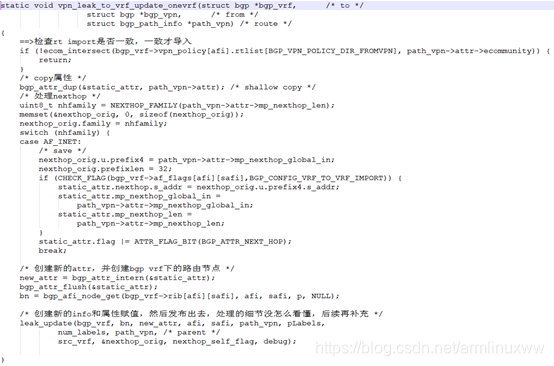
发送端ospf vrf的路由导入BGP处理:
Zebra:
ubuntu# 2019/12/26 13:05:00 ZEBRA: : netlink_parse_info: netlink-listen (NS 0) type RTM_NEWNEIGH(28), len=76, seq=0, pid=0
2019/12/26 13:05:00 ZEBRA: : Neighbor Entry received is not on a VLAN or a BRIDGE, ignoring
2019/12/26 13:05:00 ZEBRA: : netlink_parse_info: netlink-listen (NS 0) type RTM_NEWNEIGH(28), len=76, seq=0, pid=0
2019/12/26 13:05:00 ZEBRA: : Neighbor Entry received is not on a VLAN or a BRIDGE, ignoring
2019/12/26 13:05:08 ZEBRA: : zebra message[ZEBRA_ROUTE_ADD:7:45] comes from socket [42]
2019/12/26 13:05:08 ZEBRA: : Read 1 packets from client: ospf
2019/12/26 13:05:08 ZEBRA: : rib_add_multipath: 7:1.1.1.1/32: Inserting route rn 0x56275b8132b0, re 0x56275b812140 (ospf) existing (nil)
2019/12/26 13:05:08 ZEBRA: : rib_add_multipath: dumping RE entry 0x56275b812140 for 1.1.1.1/32 vrf 7
2019/12/26 13:05:08 ZEBRA: : 1.1.1.1/32: uptime == 118014, type == 6, instance == 0, table == 1
2019/12/26 13:05:08 ZEBRA: : 1.1.1.1/32: metric == 100, mtu == 0, distance == 110, flags == 0, status == 0
2019/12/26 13:05:08 ZEBRA: : 1.1.1.1/32: nexthop_num == 1, nexthop_active_num == 0
2019/12/26 13:05:08 ZEBRA: : 1.1.1.1/32: NH 12.1.1.1[5] vrf 1(7) with flags
2019/12/26 13:05:08 ZEBRA: : 1.1.1.1/32: dump complete
2019/12/26 13:05:08 ZEBRA: : rib_link: 7:1.1.1.1/32: rn 0x56275b8132b0 adding dest
2019/12/26 13:05:08 ZEBRA: : rib_meta_queue_add: 7:1.1.1.1/32: queued rn 0x56275b8132b0 into sub-queue 2
2019/12/26 13:05:08 ZEBRA: : 7:1.1.1.1/32: Processing rn 0x56275b8132b0
2019/12/26 13:05:08 ZEBRA: : 7:1.1.1.1/32: Examine re 0x56275b812140 (ospf) status 2 flags 0 dist 110 metric 100
2019/12/26 13:05:08 ZEBRA: : 7:1.1.1.1/32: After processing: old_selected 0x0 new_selected 0x56275b812140 old_fib 0x0 new_fib 0x56275b812140
2019/12/26 13:05:08 ZEBRA: : 7:1.1.1.1/32: Adding route rn 0x56275b8132b0, re 0x56275b812140 (ospf)
2019/12/26 13:05:08 ZEBRA: : netlink_route_multipath(): RTM_NEWROUTE 1.1.1.1/32 vrf 7(1)
2019/12/26 13:05:08 ZEBRA: : netlink_route_multipath() (single-path): nexthop via 12.1.1.1 if 5(7)
2019/12/26 13:05:08 ZEBRA: : netlink_talk: netlink-dp (NS 0) type RTM_NEWROUTE(24), len=60 seq=115 flags 0x501
2019/12/26 13:05:08 ZEBRA: : 7:1.1.1.1/32: rn 0x56275b8132b0 dequeued from sub-queue 2
2019/12/26 13:05:08 ZEBRA: : update_from_ctx: 7:1.1.1.1/32: SELECTED
2019/12/26 13:05:08 ZEBRA: : 7:1.1.1.1/32 update_from_ctx(): no fib nhg
2019/12/26 13:05:08 ZEBRA: : 7:1.1.1.1/32 update_from_ctx(): rib nhg matched, changed 'true'
2019/12/26 13:05:08 ZEBRA: : 7:1.1.1.1/32: Redist update re 0x56275b812140 (ospf), old 0x0 (None)
2019/12/26 13:05:08 ZEBRA: : zsend_redistribute_route: ZEBRA_REDISTRIBUTE_ROUTE_ADD to client bgp: type ospf, vrf_id 7, p 1.1.1.1/32
2019/12/26 13:05:08 ZEBRA: : Not Notifying Owner: 6 about prefix 1.1.1.1/32(1) 2 vrf: 7
Bgp:
ubuntu# 2019/12/26 13:05:08 BGP: : vpn_leak_from_vrf_update: from vrf VRF 1
2019/12/26 13:05:08 BGP: : vpn_leak_from_vrf_update: post merge static_attr.ecommunity{12.1.1.2:2}
2019/12/26 13:05:08 BGP: : vpn_leak_from_vrf_update: new_attr->ecommunity{12.1.1.2:2}
2019/12/26 13:05:08 BGP: : leak_update: entry: leak-to=VRF default, p=1.1.1.1/32, type=6, sub_type=3
2019/12/26 13:05:08 BGP: : leak_update: nexthop is valid (in vrf VRF 1)
2019/12/26 13:05:08 BGP: : leak_update: ->VRF default: 1.1.1.1/32: Added new route
2019/12/26 13:05:08 BGP: : vpn_leak_to_vrf_update: start (path_vpn=0x557deca2fe90)
2019/12/26 13:05:08 BGP: : vpn_leak_to_vrf_update_onevrf: skipping: import not set
2019/12/26 13:05:08 BGP: : Rx route ADD VRF 7 ospf[0] 1.1.1.1/32 nexthop 12.1.1.1 (type 3 if 5) metric 100 tag 0
2019/12/26 13:05:08 BGP: : group_announce_route_walkcb: afi=IPv4, safi=vpn, p=1.1.1.1/32
2019/12/26 13:05:08 BGP: : subgroup_process_announce_selected: p=1.1.1.1/32, selected=0x557deca2fe90
2019/12/26 13:05:08 BGP: : u4:s4 send UPDATE w/ attr: nexthop 0.0.0.0, metric 100, extcommunity RT:12.1.1.2:2, originator 2.2.2.2, path
2019/12/26 13:05:08 BGP: : u4:s4 send MP_REACH for afi/safi 1/128
2019/12/26 13:05:08 BGP: : u4:s4 send UPDATE RD 12.1.1.2:2 1.1.1.1/32 label 154 IPv4 vpn
2019/12/26 13:05:08 BGP: : u4:s4 send UPDATE len 92 numpfx 1
2019/12/26 13:05:08 BGP: : u4:s4 10.10.10.10 send UPDATE w/ nexthop 20.20.20.20 and RD
2019/12/26 13:05:08 BGP: : 10.10.10.10 rcvd UPDATE w/ attr: , origin ?, extcommunity RT:12.1.1.2:2, path 100 200
2019/12/26 13:05:08 BGP: : 10.10.10.10 rcvd UPDATE wlen 0 attrlen 66 alen 0
2019/12/26 13:05:08 BGP: : 10.10.10.10 rcvd UPDATE about RD 12.1.1.2:2 1.1.1.1/32 label 154 IPv4 vpn -- DENIED due to: as-path contains our own AS;
Bgp端的函数subgroup_update_packet构造的update报文发送
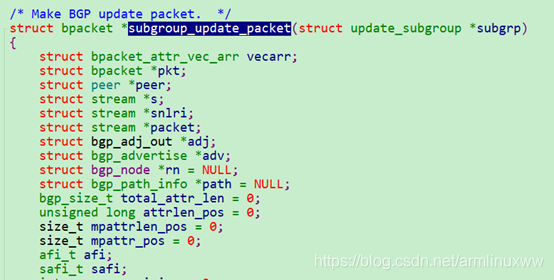
发送的时候如果报文里面nexthop属性为0的话,bpacket_reformat_for_peer 这个函数会改nexthop的IP地址
 BGP与L3VPN路由更新解析
BGP与L3VPN路由更新解析





 本文详细解析了BGP在处理L3VPN UPDATE消息的过程,包括属性解析、下一跳处理、MP_REACH_NLRI解析及路由导入VRF的流程。深入探讨了从接收、解析到发送UPDATE报文的整个过程。
本文详细解析了BGP在处理L3VPN UPDATE消息的过程,包括属性解析、下一跳处理、MP_REACH_NLRI解析及路由导入VRF的流程。深入探讨了从接收、解析到发送UPDATE报文的整个过程。
















 566
566

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








