1.OVO开门爽!开到南天门了兄弟
from Crypto.Util.number import *
flag = b'BuildCTF{******}'
#随机生成p,q
p = getPrime(1024)
q = getPrime(1024)
#计算模数n
n = p*q
e = 65537
m = bytes_to_long(flag)
#c=m^e%n
c = pow(m, e, n)
print('P = ',p**2)
print('Q = ',q**2)
print('n = ',n)
print('e = ',e)
print('c = ',c)

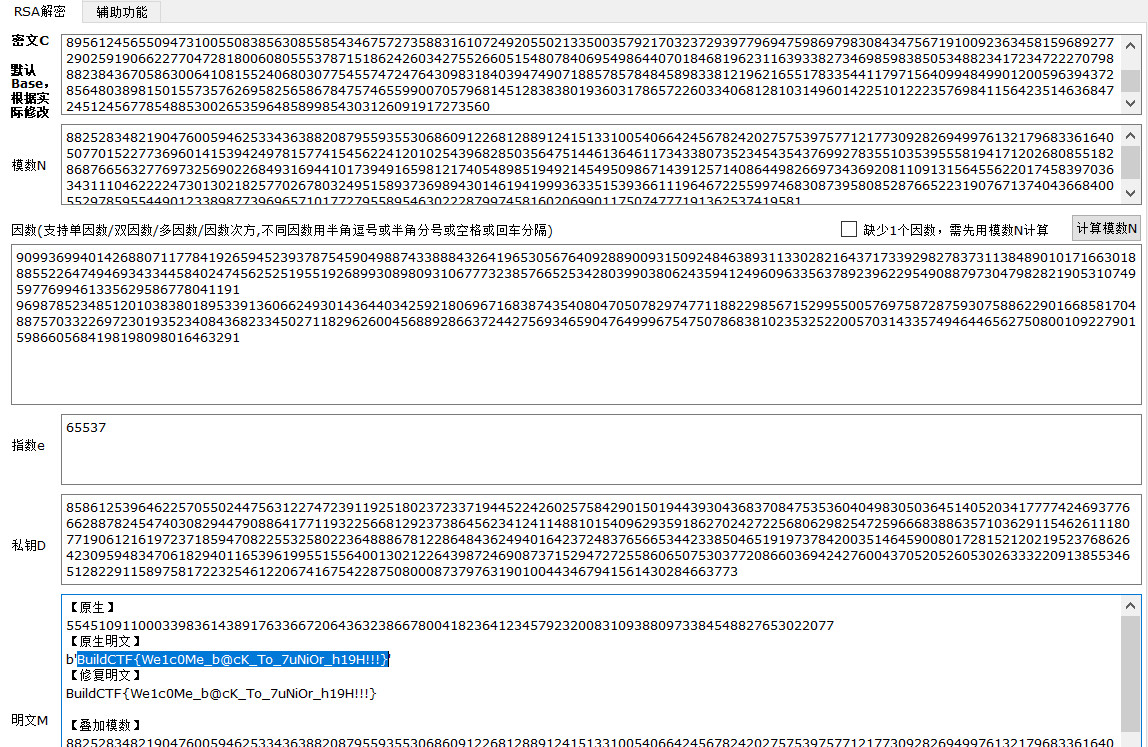
BuildCTF{We1c0Me_b@cK_To_7uNiOr_h19H!!!}
2.我这辈子就是被古典给害了
from Crypto.Util.Padding import pad, unpad
from Crypto.Random import get_random_bytes
from Crypto.Cipher import AES
from secret import flag, key
dict1 = {'A': 0, 'B': 1, 'C': 2, 'D': 3, 'E': 4,
'F': 5, 'G': 6, 'H': 7, 'I': 8, 'J': 9,
'K': 10, 'L': 11, 'M': 12, 'N': 13, 'O': 14,
'P': 15, 'Q': 16, 'R': 17, 'S': 18, 'T': 19,
'U': 20, 'V': 21, 'W': 22, 'X': 23, 'Y': 24, 'Z': 25}
dict2 = {0: 'A', 1: 'B', 2: 'C', 3: 'D', 4: 'E',
5: 'F', 6: 'G', 7: 'H', 8: 'I', 9: 'J',
10: 'K', 11: 'L', 12: 'M', 13: 'N', 14: 'O',
15: 'P', 16: 'Q', 17: 'R', 18: 'S', 19: 'T',
20: 'U', 21: 'V', 22: 'W', 23: 'X', 24: 'Y', 25: 'Z'}
def generate_key(flag, key):
i = 0
while True:
if len(key) == len(flag):
break
key += flag[i]
i += 1
return key
def cipherText(msg, key_new):
cipher_text = ''
i = 0
for letter in msg:
x = (dict1[letter] + dict1[key_new[i]]) % 26
i += 1
cipher_text += dict2[x]
return cipher_text
def AES_enc(key, value):
key = (key * 2).encode()
cipher = AES.new(key, AES.MODE_ECB)
value = value.encode()
padded_text = pad(value, AES.block_size)
ciphertext = cipher.encrypt(padded_text)
print("AES Encrypted Text =", ciphertext)
def substitute(msg):
msg = msg.replace('{', 'X')
msg = msg.replace('_', 'X')
msg = msg.replace('}', 'X')
msg = msg.upper()
assert msg.isupper()
return msg
message = substitute(flag)
key_new = generate_key(message, key)
cipher = cipherText(message, key_new)
print("Encrypted Text =", cipher)
AES_enc(key, flag)
'''
Encrypted Text = HLMPWKGLYSWFACEWBYRSUKYFAXZFXDKOTZHHSLFCXNICAHPGRIFUF
AES Encrypted Text = b'\x92T{\x1f\x0f"\xbd\xbb\xfa|O\x11\x83\xa0\xec.\x15]\x9f\x9a\xe5\x85Z\x9f@yUm\xbb\xdc\x93\x08\xe5\x8b\xd5\x98\x84\xfa\x91\xe8\xde\x1b}\xcd\x9056\xa3\xbf\xdb\x85J\xcc\xec\x812T\x11\xa7Tl\x15\xf6"'
'''dict1 = {'A': 0, 'B': 1, 'C': 2, 'D': 3, 'E': 4,
'F': 5, 'G': 6, 'H': 7, 'I': 8, 'J': 9,
'K': 10, 'L': 11, 'M': 12, 'N': 13, 'O': 14,
'P': 15, 'Q': 16, 'R': 17, 'S': 18, 'T': 19,
'U': 20, 'V': 21, 'W': 22, 'X': 23, 'Y': 24, 'Z': 25}
dict2 = {0: 'A', 1: 'B', 2: 'C', 3: 'D', 4: 'E',
5: 'F', 6: 'G', 7: 'H', 8: 'I', 9: 'J',
10: 'K', 11: 'L', 12: 'M', 13: 'N', 14: 'O',
15: 'P', 16: 'Q', 17: 'R', 18: 'S', 19: 'T',
20: 'U', 21: 'V', 22: 'W', 23: 'X', 24: 'Y', 25: 'Z'}
out = "HLMPWKGLYSWFACEWBYRSUKYFAXZFXDKOTZHHSLFCXNICAHPGRIFUF"
letters = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"
##根据题目,flag开头是BuildCTF{转换为BUILDCTFX,至少可以爆破出9位key
##第一轮推出部分key
key = ""
flag = "BUILDCTFX"
n = len(flag)
for i in range(n):
letter = flag[i]
for j in letters:
x = (dict1[letter] + dict1[j]) % 26
if dict2[x] == out[i]:
key = key + j
break
print(key)
#key=GREETINGB
##根据题目,key参与AES加密,且key=key*2,通常key长度为16,推断出key长度是8,第一轮推出key为GREETINGB,那么正常的key是GREETING,从第9位B开始,是叠加flag,即BUILDCTFX。
##第二轮推出部分flag
flag = ""
while True:
key_ = "GREETING"
key = key_ + flag
if len(key) > len(out):
key = key[0:len(out)]
m = len(key)
for i in range(m):
letter = key[i]
for j in letters:
x = (dict1[letter] + dict1[j]) % 26
if dict2[x] == out[i]:
flag = flag + j
break
print(flag)
if len(flag) >= len(out):
break
#flag=BUILDCTFBUILDCTFXYOUXALRBUILDCTFXYOUXALRAEJHRIFADZLLADZX
#替换为{}_BuildCTF{YOU_ALREADY_KNOW_WHAT_A_CLASSICAL_CIPHER_IS}
3.ominous
from Crypto.Util.number import *
from secret import flag
import random
import string
Ominous_dic = ['啊', '米', '诺', '斯']
flag_word = (string.ascii_letters + string.digits + '{}@_!').encode()
assert all(char in flag_word for char in flag)
msg = bytes_to_long(flag)
random.shuffle(Ominous_dic)
def Ominous_enc(msg):
res = 0
for idx, word in enumerate(Ominous_dic):
res += random.randint(0, 200) * ord(word) * (2 ** (50 * (idx + 1)))
return res + msg
cipher = Ominous_enc(msg)
print(f'cipher = {cipher}')
# cipher = 11174132013050242293373893046306047184706656363469879247040688497021from libnum import *
import itertools
import string
flag_word = (string.ascii_letters + string.digits + '{}@_!').encode()
cipher = 11174132013050242293373893046306047184706656363469879247040688497021
Ominous_dic = ['啊', '米', '诺', '斯']
all_list = []
for i in itertools.permutations(Ominous_dic,4):
tmp = [i[0],i[1],i[2],i[3]]
all_list.append(tmp)
for i in all_list:
print(i)
##因为j0最小,对结果影响也最小,先爆破出j1,j2,j3的范围
for j0 in range(0,1):
tmp0 = j0 * ord(i[0]) * (2 ** (50 * (0 + 1)))
for j1 in range(0,201):
tmp1 = j1 * ord(i[1]) * (2 ** (50 * (1 + 1)))
for j2 in range(0,201):
tmp2 = j2 * ord(i[2]) * (2 ** (50 * (2 + 1)))
for j3 in range(0,201):
tmp3 = j3 * ord(i[3]) * (2 ** (50 * (3 + 1)))
res = tmp0 + tmp1 + tmp2 + tmp3
out1 = cipher-res
try:
out = n2s(out1)
if b"BuildCTF{" in out:
print(j0,j1,j2,j3)
pos = True
for j in out:
if j not in flag_word:
pos = False
break
if pos == True:
print(j0,j1,j2,j3)
print(out1)
print(out)
except:
pass
res = 0['诺', '斯', '米', '啊']
0 0 42 119
0 1 42 119
0 2 42 119
0 3 42 119
………………
['斯', '诺', '米', '啊']
0 0 42 119
0 1 42 119
0 2 42 119
0 3 42 119
…………………
发现规律,修正代码缩小爆破范围from libnum import *
import itertools
import string
flag_word = (string.ascii_letters + string.digits + '{}@_!').encode()
cipher = 11174132013050242293373893046306047184706656363469879247040688497021
Ominous_dic = ['啊', '米', '诺', '斯']
all_list = [['诺', '斯', '米', '啊'],['斯', '诺', '米', '啊']]
for i in all_list:
print(i)
##因为j0最小,对结果影响也最小,先爆破出j1,j2,j3的范围
for j0 in range(0,201):
tmp0 = j0 * ord(i[0]) * (2 ** (50 * (0 + 1)))
for j1 in range(0,201):
tmp1 = j1 * ord(i[1]) * (2 ** (50 * (1 + 1)))
for j2 in range(42,43):
tmp2 = j2 * ord(i[2]) * (2 ** (50 * (2 + 1)))
for j3 in range(119,120):
tmp3 = j3 * ord(i[3]) * (2 ** (50 * (3 + 1)))
res = tmp0 + tmp1 + tmp2 + tmp3
out1 = cipher-res
try:
out = n2s(out1)
if b"BuildCTF{" in out:
pos = True
for j in out:
if j not in flag_word:
pos = False
break
if pos == True:
print(j0,j1,j2,j3)
print(out1)
print(out)
except:
pass
res = 0['诺', '斯', '米', '啊']
51 34 42 119
6998911667306495936139354047122483151410244697241827169626933502333
b'BuildCTF{Wh@wsuu_0mwkous!!!}'
51 79 42 119
6998911667306495936139354047120998231835390350462060938975672082813
b'BuildCTF{Wh@vUyE_0mwkous!!!}'
51 82 42 119
6998911667306495936139354047120899237197066727343409856932254654845
b'BuildCTF{Wh@vBhu_0mwkous!!!}'
51 113 42 119
6998911667306495936139354047119876292601055955117348675816941232509
b'BuildCTF{Wh@u}ee_0mwkous!!!}'
51 158 42 119
6998911667306495936139354047118391373026201608337582445165679812989
b'BuildCTF{Wh@t_i5_0mwkous!!!}'
51 161 42 119
6998911667306495936139354047118292378387877985218931363122262385021
b'BuildCTF{Wh@tLXe_0mwkous!!!}'
72 34 42 119
69989116673064959361393540471224831514102 BuildCTF题解与答案汇总
BuildCTF题解与答案汇总





 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 2183
2183










