参考资料:
3、R3环申请内存时页面保护与_MMVAD_FLAGS.Protection位的对应关系
4、64位CreateProcess逆向:(四)创建进程的过程
虚拟机:VM15
系统:Win7 32位
编译器:VS2019
工具:CE6.5
代码如下:
#include <stdio.h>
#include <Windows.h>
#include <stdlib.h>
#define InitializeObjectAttributes( p, n, a, r, s ) { \
(p)->Length = sizeof( OBJECT_ATTRIBUTES ); \
(p)->RootDirectory = r; \
(p)->Attributes = a; \
(p)->ObjectName = n; \
(p)->SecurityDescriptor = s; \
(p)->SecurityQualityOfService = NULL; \
}
typedef struct _UNICODE_STRING {
USHORT Length;
USHORT MaximumLength;
PWSTR Buffer;
} UNICODE_STRING, * PUNICODE_STRING;
typedef struct _OBJECT_ATTRIBUTES {
ULONG Length;
HANDLE RootDirectory;
PUNICODE_STRING ObjectName;
ULONG Attributes;
PVOID SecurityDescriptor;
PVOID SecurityQualityOfService;
} OBJECT_ATTRIBUTES, * POBJECT_ATTRIBUTES;
typedef DWORD(WINAPI* ZwCreateSectionProc)(
PHANDLE SectionHandle,
ACCESS_MASK DesiredAccess,
POBJECT_ATTRIBUTES ObjectAttributes,
PLARGE_INTEGER MaximumSize,
ULONG SectionPageProtection,
ULONG AllocationAttributes,
HANDLE FileHandle
);
typedef enum _SECTION_INHERIT {
ViewShare = 1,
ViewUnmap = 2
} SECTION_INHERIT;
typedef DWORD(WINAPI* ZwMapViewOfSectionProc)(
HANDLE SectionHandle,
HANDLE ProcessHandle,
PVOID* BaseAddress,
ULONG_PTR ZeroBits,
SIZE_T CommitSize,
PLARGE_INTEGER SectionOffset,
PSIZE_T ViewSize,
SECTION_INHERIT InheritDisposition,
ULONG AllocationType,
ULONG Win32Protect
);
int main()
{
system("pause");
HMODULE h = LoadLibraryA("ntdll.dll");
ZwCreateSectionProc ZwCreateSection = (ZwCreateSectionProc)GetProcAddress(h, "NtCreateSection");
ZwMapViewOfSectionProc ZwMapViewOfSection = (ZwMapViewOfSectionProc)GetProcAddress(h, "ZwMapViewOfSection");
HANDLE SectionHandle;
LARGE_INTEGER MaximumSize = { 0 };
MaximumSize.QuadPart = 0x10000;
OBJECT_ATTRIBUTES obj = { 0 };
InitializeObjectAttributes(&obj, NULL, 0x40, 0, 0);
DWORD error = ZwCreateSection(&SectionHandle, SECTION_ALL_ACCESS, NULL, &MaximumSize, PAGE_EXECUTE_READ, SEC_COMMIT, NULL);
PVOID BaseAddress = NULL;
SIZE_T ViewSize = 0;
error = ZwMapViewOfSection(SectionHandle, GetCurrentProcess(), &BaseAddress, 0,
0x10000, NULL, &ViewSize, (SECTION_INHERIT)1, 0, PAGE_EXECUTE_READ);
printf("%x,%x\r\n", BaseAddress, SectionHandle);
DWORD p = 0;
error = VirtualProtect(BaseAddress, 0x10000, PAGE_EXECUTE_READWRITE, &p);
system("pause");
return 0;
}
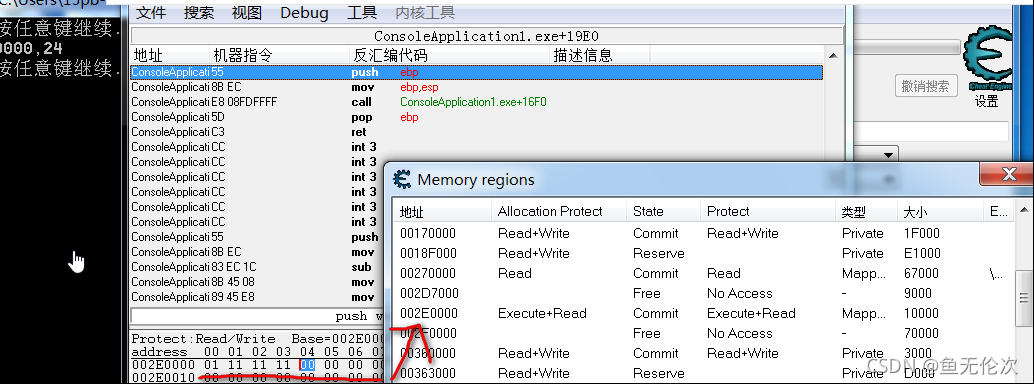
现在CE工具就无法修改内存了
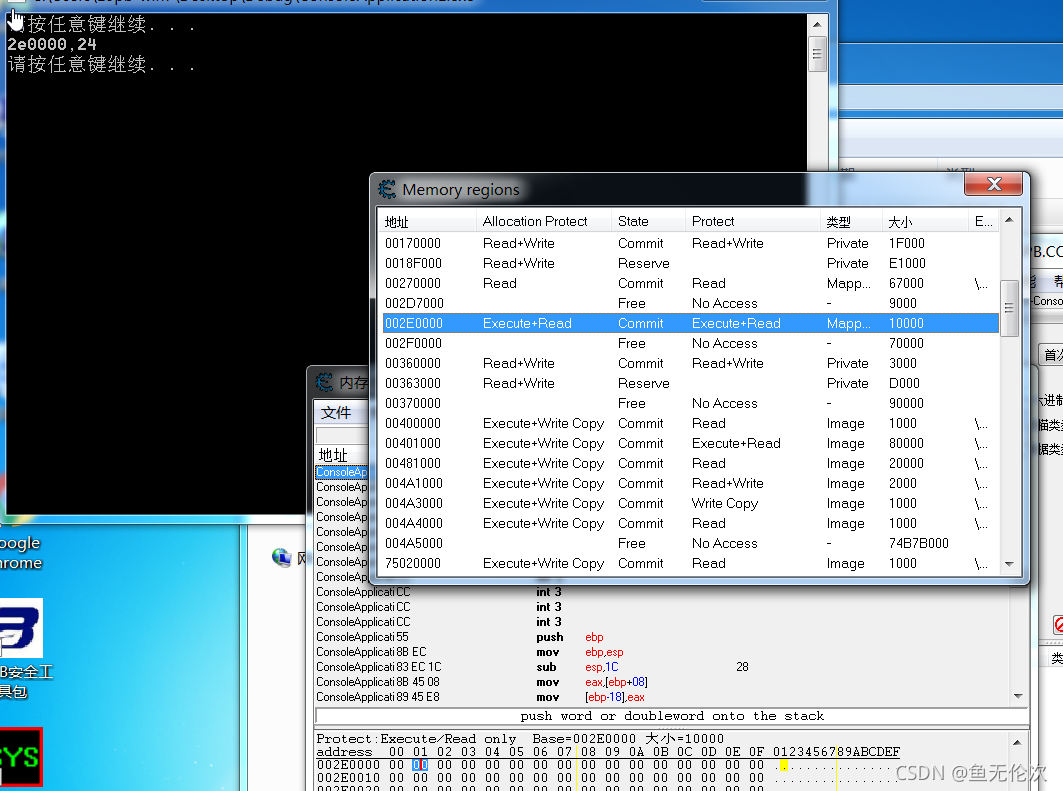
破解方法:
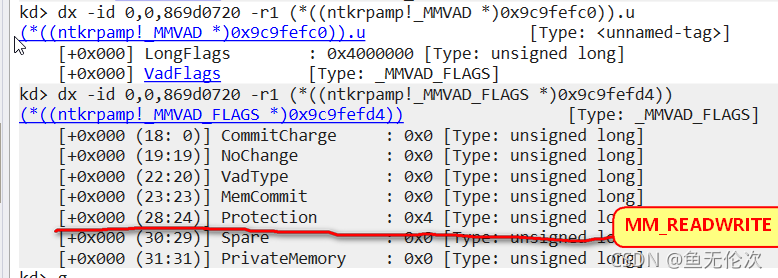
修改_MMVAD_FLAGS.Protection
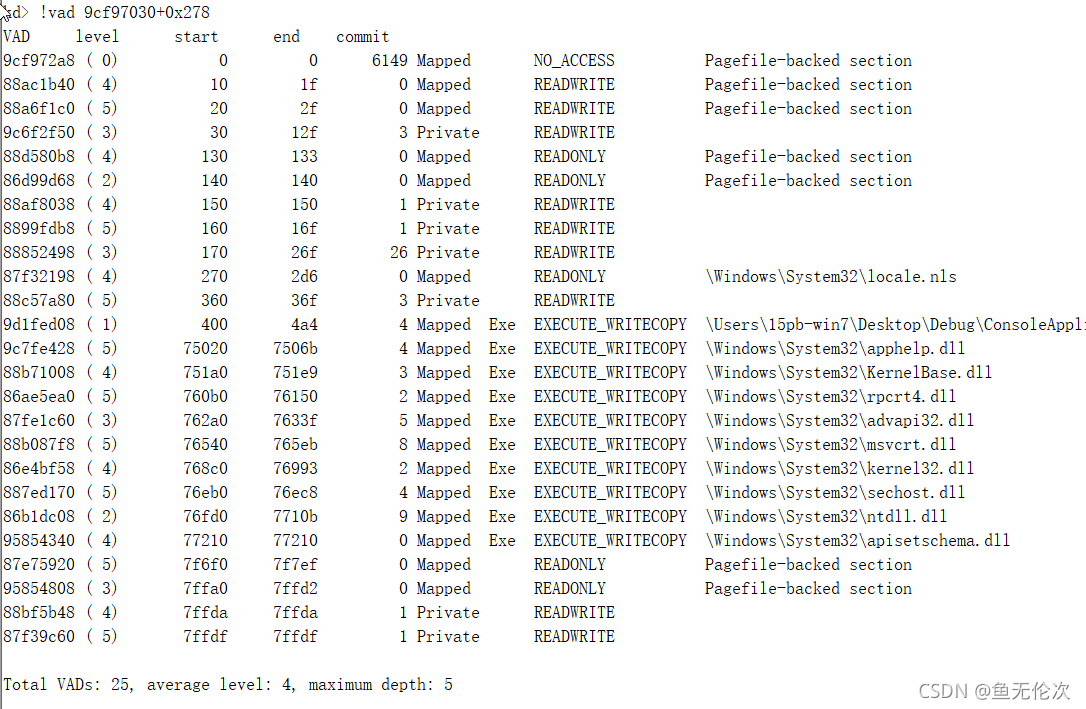
运行前:
运行后:
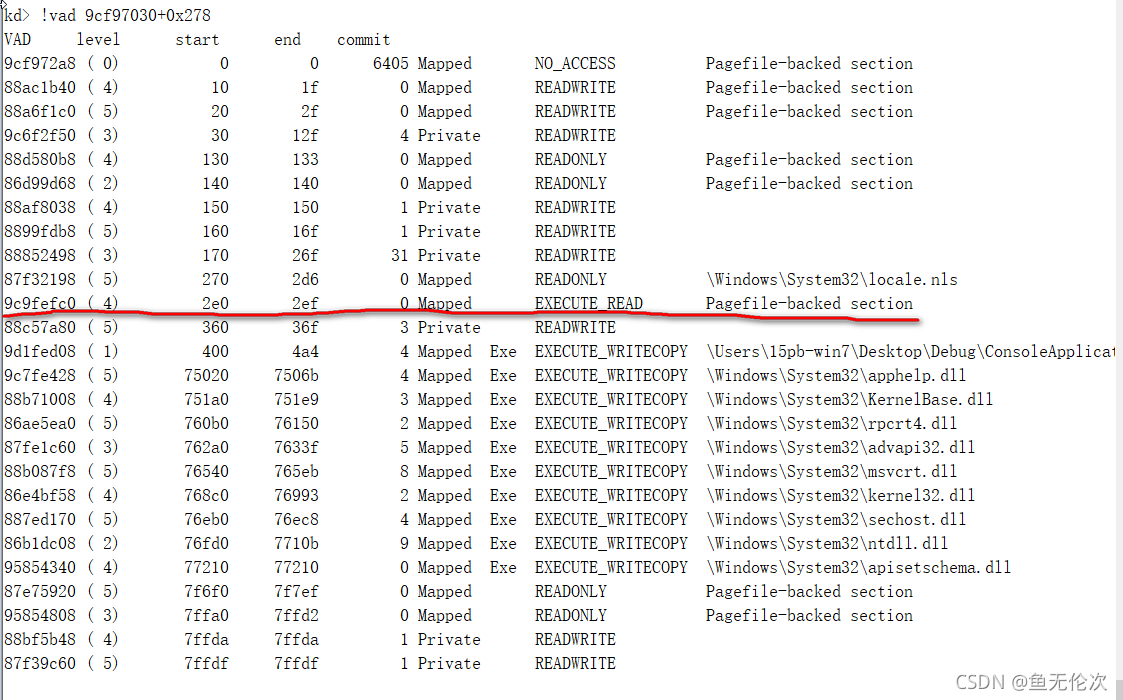
命令:dt _mmvad 9c9fefc0
需要将Protection的值修改成4
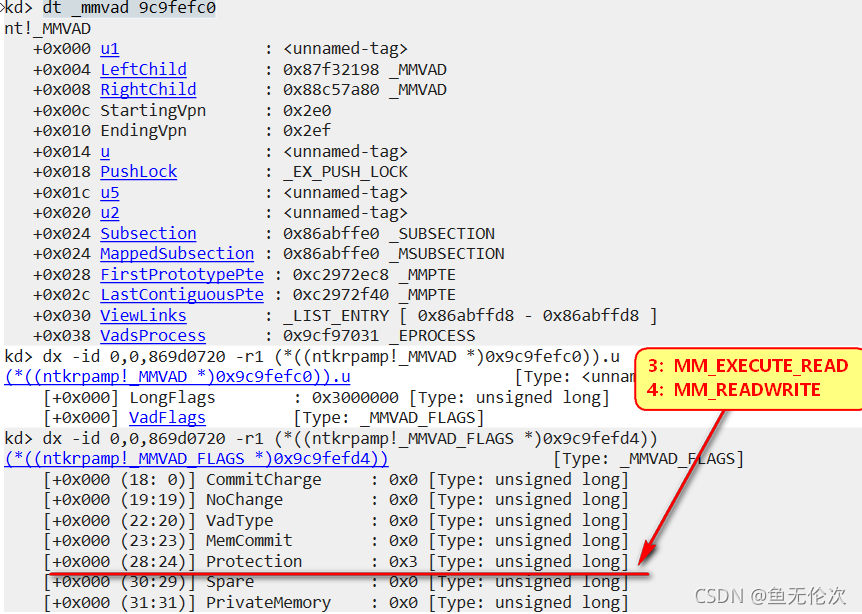
改成4即可
现在就可以正常修改了





 本文探讨了一种在Windows环境下通过修改VAD属性和MMVAD_FLAGS.Protection值,如何绕过内存保护机制,实现对内存的正常修改。具体步骤涉及NTDLL库的ZwCreateSection和ZwMapViewOfSection函数,适用于32位Win7系统和VS2019编译器环境。
本文探讨了一种在Windows环境下通过修改VAD属性和MMVAD_FLAGS.Protection值,如何绕过内存保护机制,实现对内存的正常修改。具体步骤涉及NTDLL库的ZwCreateSection和ZwMapViewOfSection函数,适用于32位Win7系统和VS2019编译器环境。
















 3707
3707

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








