注:本文为 “黑客亚文化演进” 相关文章合辑。
机翻,未校。
Understanding Hacker Hat Colors
理解黑客的 “帽子颜色”
Or Kadosh
Cybersecurity categorizes hackers by “hat colors,” indicating their ethical standings and intents, which range from malicious black hats to ethical white hats. Each color represents different motivations and methods, crucial for developing strategic defenses against cyber threats.
网络安全通过 “帽子颜色” 对黑客进行分类,这些颜色反映了他们的道德立场和意图,从恶意的黑帽黑客到道德的白帽黑客不等。每种颜色代表不同的动机和方法,这对于制定针对网络威胁的战略性防御措施至关重要。
Unmasking Hacker Types
揭露黑客类型
In discussions about digital security, hackers are often generalized. Yet they vary broadly—both in number and in motivation. They don’t all fit into the same mold. Generally, in the professional cybersecurity world, hackers are categorized by the color of the hat they wear—when it comes to ethics, that is. These categories help security professionals understand the types of motivations and intentions hackers have. This understanding is essential for crafting diverse and effective defenses against an equally diverse set of cyber threats.
在关于数字安全的讨论中,黑客常常被一概而论。然而,他们在数量和动机上都有很大的差异,并非所有黑客都属于同一类。通常,在专业的网络安全领域,黑客根据他们所戴的 “帽子” 颜色进行分类 —— 这里的 “帽子” 指的是道德层面。这些分类帮助安全专家理解黑客的动机和意图。这种理解对于制定多样化且有效的防御措施以应对多样化的网络威胁至关重要。
Hackers lie on a spectrum that stretches from the harmful exploits of black hat hackers , who do so for personal gains or commercial advantage, to ethical white hat hackers —individuals who do what is necessary to keep the internet secure. While both black and white hat hackers are at the two ends of the hacking spectrum, there is a third group that falls between them called grey hat hackers. They do exploratory hacking that sometimes edges into the illegal and unethical. They may find vulnerabilities in a system, but they do not have consent to look at the system in the first place.
黑客的范围从以个人利益或商业利益为目的而进行有害攻击的黑帽黑客,延伸到致力于保护互联网安全的道德白帽黑客。虽然黑帽和白帽黑客分别处于黑客光谱的两端,但在它们之间还有一类被称为灰帽黑客的群体。他们的探索性黑客行为有时会触犯法律和道德规范。他们可能会发现系统中的漏洞,但他们在一开始就没有获得查看该系统的许可。
Understanding these categories aids in better threat analysis and creating robust defensive strategies.
理解这些分类有助于更好地进行威胁分析并制定强大的防御策略。
Further enriching this scene are red hat hackers , who are often more militant in their approach and take matters into their own hands to dismantle the black hats. Blue hat hackers , meanwhile, might test products pre-release for vulnerabilities and seek revenge through hacking. And then there’s the unquenchable thirst for knowledge that drives green hat hackers —novices in the field—who are still learning the ropes.
进一步丰富这一场景的是红帽黑客,他们通常采取更为激进的方式,主动出击以摧毁黑帽黑客。与此同时,蓝帽黑客可能会在产品发布前测试漏洞,并通过黑客行为寻求报复。此外,还有绿帽黑客 —— 该领域的初学者,他们对知识有着无尽的渴望,仍在学习黑客的基本技能。
A unique role is played by each variety in the cybersecurity ecosystem, which makes for a particularly complex problem that requires an equally complex understanding to solve. These professionals need to grasp not just the kinds of cyber attacks that are out there but also the ideal attack configuration for each type. This kind of knowledge is not only the bedrock for building defensive strategies but also for understanding the attack strategies of the threat actors themselves.
在网络安全生态系统中,每种黑客类型都扮演着独特的角色,这使得问题变得尤为复杂,需要同样复杂的理解才能解决。这些专业人士不仅需要了解存在的网络攻击类型,还需要了解每种类型的理想攻击配置。这种知识不仅是构建防御策略的基础,也是理解威胁行为者攻击策略的关键。
White Hat Hackers
白帽黑客
White hat hackers, also known as ethical hackers, are essential in the cybersecurity domain. They fight side by side with us in the attempt to safeguard organizations’ digital assets. These are the true good guys in the hacking arena. They find, uncover, and testify to the existence of flaws and weaknesses in our digital systems. We pay them to do this, and they do it well. They are our inside track to understanding what it is that makes a system secure or insecure.
白帽黑客,也被称为道德黑客,在网络安全领域至关重要。他们与我们并肩作战,努力保护组织的数字资产。他们是黑客领域的真正 “好人”。他们发现、揭露并证实我们数字系统中存在的缺陷和弱点。我们付钱让他们做这些事,而他们也做得很好。他们是我们了解系统安全或不安全本质的内部渠道。
“The work of white hats is absolutely 100% essential in staying ahead of the cyber threat landscape.” – Jeff Moss
“白帽黑客的工作对于保持领先于网络威胁态势至关重要。”—— 杰夫・莫斯
Their actions center around a proactive method for ensuring cybersecurity. Vulnerability assessments are at the core of this method, and the best way to conduct them is to actually simulate a cyberattack. So, that’s what they do. They find all the points in an organization’s defenses where an attacker could get in and then use those points to find out what else an attacker could do once inside. They do this with a sort of “trust but verify” mindset, where you have to trust that you’re going to find all the weaknesses but also verify that you were right to trust in the first place.
他们的行动围绕着一种积极主动的网络安全保障方法展开。漏洞评估是这种方法的核心,而进行漏洞评估的最好方式是实际模拟网络攻击。因此,他们就是这样做的。他们找出组织防御中攻击者可能进入的所有点,然后利用这些点来找出攻击者进入后还能做些什么。他们以一种 “信任但验证” 的心态来做这件事,你必须相信你会找到所有弱点,但也要验证你最初的信任是否正确。
White hat hackers often have certifications like CEH (Certified Ethical Hacker) and OSCP (Offensive Security Certified Professional) to validate their skills.
白帽黑客通常拥有 CEH(认证道德黑客)和 OSCP(攻击性安全认证专家)等证书来证明他们的技能。
It cannot be emphasized enough how vital white hat hackers are. White hat hackers have come from a diverse range of educational backgrounds, but they usually have some sort of higher education either in computer science or information security. They also tend to have useful and industry-relevant certifications that help validate their skills; two such certifications are the CEH and the OSCP.
白帽黑客的重要性怎么强调都不为过。白帽黑客来自多种教育背景,但他们通常在计算机科学或信息安全方面接受过某种高等教育。他们还倾向于拥有有助于证明其技能的实用且与行业相关的认证;CEH 和 OSCP 就是其中的两种认证。
Consequently, organizations that wish to safeguard their digital assets find help from an unlikely ally: white hat hackers. Partly because of the advanced skills these hackers possess, and partly because of the ethos that white hats uphold, data breaches are prevented from occurring with increasing regularity. Virtually all enterprises in all sectors now have some hacking skills among their workforce. Yet the skills gap in cybersecurity is a well-documented and very real concern that is causing harm to enterprise companies and the economy at large.
因此,希望保护其数字资产的组织找到了一个不太可能的盟友:白帽黑客。部分原因是这些黑客拥有的高级技能,部分原因是白帽黑客所秉持的道德准则,数据泄露的发生频率正在逐渐降低。如今,几乎所有行业和领域的公司都拥有具备黑客技能的员工。然而,网络安全领域的技能差距是一个有据可查且非常现实的问题,它正在对企业和整体经济造成伤害。
Black Hat Hackers
黑帽黑客
A dark, abstract digital landscape representing cybersecurity challenges, with glowing computer screens displaying code, and a group of smiling cybersecurity professionals collaborating, discussing strategies in a positive atmosphere.
一幅代表网络安全挑战的黑暗抽象数字景观,发光的电脑屏幕上显示着代码,一群面带微笑的网络安全专业人士正在合作,积极地讨论策略。
What exactly are black hat hackers? They are the most wicked of the wicked in cybersecurity. They are individuals who are maliciously exploiting computer systems and networks for any number of nefarious reasons—financial gain, revenge, or just the thrill of hacking. Black hats, as they are called, operate in the dark world of cybersecurity, with no guiding ethics to decriminalize what they do.
黑帽黑客到底是什么?他们是网络安全领域中最邪恶的存在。他们是出于各种邪恶目的 —— 经济利益、报复,或者仅仅是黑客行为带来的刺激感 —— 恶意利用计算机系统和网络的个人。正如他们被称为黑帽黑客一样,他们在网络安全的黑暗世界中活动,没有任何道德准则来为其行为脱罪。
Black hat hackers wield a range of destructive techniques. The repertoire of these nefarious individuals encompasses phishing, malware distribution, and denial-of-service attacks . One of the most harmful methods they use is zero-day exploitation—targeting unknown software flaws that haven’t been fixed yet. When you consider all that black hat hackers do to undermine recent accounts of shadow resistance, the full impact comes into view: shadow economies losing zillions of dollars, citizens being duped, and whole countries being put in jeopardy—all while these hackers try to make cyberspace a more anarchic place.
黑帽黑客掌握了一系列破坏性技术。这些邪恶之徒的手段包括网络钓鱼、恶意软件分发和拒绝服务攻击。他们使用的一种最具危害性的方法是零日漏洞利用 —— 针对尚未修复的未知软件漏洞。当你考虑到黑帽黑客对最近的影子抵抗活动所做的一切破坏时,其全部影响就会显现出来:影子经济损失数万亿美元,公民被欺骗,整个国家陷入危险 —— 而这些黑客试图让网络空间变得更加无序。
The WannaCry ransomware attack, which affected over 300,000 computers in 150 countries, showcases the severe impact a black hat hacker can have on global systems.
影响了 150 个国家超过 300,000 台计算机的 WannaCry 勒索软件攻击,展示了黑帽黑客对全球系统可能造成的严重影响。
A number of well-publicized incidents demonstrate these hackers’ capacity to inflict real harm. The ransomware attack known as WannaCry, for example, affected a staggering number of computers around the world—over 300,000 in 150 countries—and it brought no small amount of suffering to the users and organizations it affected.
许多广为人知的事件展示了这些黑客造成实际伤害的能力。例如,名为 WannaCry 的勒索软件攻击影响了全球大量计算机 ——150 个国家的超过 300,000 台 —— 并且给受影响的用户和组织带来了不小的痛苦。
“The WannaCry ransomware attack severely disrupted businesses and government operations. WannaCry wreaked havoc in many places, most notably at the British National Health Service, where it nearly shut down the one-week-ahead emergency preparedness command center in part because it disrupted access to hospital records throughout the NHS network, . . . one of the largest NHS cyber-disruptions since 2012.” Source
“WannaCry 勒索软件攻击严重扰乱了商业和政府的运作。WannaCry 在许多地方造成了巨大破坏,最著名的是在英国国家卫生服务系统,它几乎关闭了提前一周准备的紧急准备指挥中心,部分原因是它扰乱了整个 NHS 网络的医院记录访问权限,…… 这是自 2012 年以来 NHS 最大的网络中断之一。” 来源
Black hat hacking is a complex and multifaceted phenomenon. Although our understanding of the psychology behind it is still evolving, we do know that these individuals often find themselves unable to manage their fears and emotions in a productive way. For some, hacking is about seeking a buzz or high voltage experience; for others, it’s a way of acting out or rebelling against authority figures and the establishment. But we also know that not every black hat hacker fits these molds, and many operate under a logic that sees them doing what is, in some sense, a service to society.
黑帽黑客行为是一个复杂且多面的现象。尽管我们对背后的心理学理解仍在不断发展,但我们确实知道,这些个体常常发现自己无法以一种富有成效的方式管理自己的恐惧和情绪。对一些人来说,黑客行为是为了寻求刺激或高强度的体验;对另一些人来说,这是一种对权威人物和体制的反抗行为。但我们同样知道,并非每一个黑帽黑客都符合这些模式,许多人是在一种逻辑下运作的,这种逻辑在某种意义上是为社会提供了一种服务。
Preventing black hat hacking requires a multifaceted approach, including robust security measures, regular updates, and employee training. Organizations that understand the motivations and methods of black hat hackers can better protect themselves and their clients, reducing the risk of falling victim to these cybercriminals.
防止黑帽黑客行为需要一种多管齐下的方法,包括强大的安全措施、定期更新和员工培训。理解黑帽黑客的动机和方法的组织能够更好地保护自己和客户,降低成为这些网络犯罪分子受害者的风险。
Grey Hat Hackers
灰帽黑客
A digital landscape with a gray-hued cityscape, featuring abstract representations of computer code and networks, with cheerful individuals collaborating around a glowing computer screen, showcasing a positive atmosphere of teamwork in cybersecurity.
一幅带有灰色调的城市景观的数字景观,其中包含计算机代码和网络的抽象表示,快乐的人们围绕着发光的电脑屏幕合作,展示了网络安全中团队合作的积极氛围。
Grey hat hackers occupy a distinctive position in the cybersecurity landscape, existing between ethical and malicious hacking. These individuals are usually quite skilled and employ their knowledge to uncover vulnerabilities in computer systems and networks. Unlike their ethical counterparts, however, grey hats typically work without any prior consent and often without even advising anyone of what they’ve done until well after the fact. What they do and how they do it isn’t very secure or sensible, to be honest, for several reasons that will become clear. But grey hat hacking is a phenomenon with which we need to reckon. So let’s start by giving grey hats the credit they aren’t very accustomed to getting.
灰帽黑客在网络安全领域占据了一个独特的位置,处于道德黑客和恶意黑客之间。这些个体通常相当熟练,运用他们的知识来发现计算机系统和网络中的漏洞。然而,与他们的道德同行不同,灰帽黑客通常在没有任何事先许可的情况下工作,甚至在事后很久才告知任何人他们所做的事情。老实说,他们所做的事情以及他们做事的方式并不安全或明智,原因稍后会清楚。但灰帽黑客行为是一个我们需要正视的现象。那么,让我们先从给予灰帽黑客他们不太习惯得到的认可开始。
Grey hat hackers sometimes disclose vulnerabilities publicly to ensure they are addressed promptly, though this approach can create legal and ethical challenges.
灰帽黑客有时会公开披露漏洞,以确保它们能够得到及时处理,尽管这种方法可能会带来法律和伦理上的挑战。
An important feature of grey hat hackers is how they handle vulnerability disclosure. In certain instances—like the critical security flaws made public during the Facebook Bug Incident or the ASUS routers case—these hackers have taken on the companies involved and have pushed them to make necessary changes and improvements. But as David Tidmarsh has noted, this very noble-sounding behavior for grey hats wears thin when you start to see the potential cybersecurity ripple effects of what they’re doing.
灰帽黑客的一个重要特点是他们如何处理漏洞披露。在某些情况下 —— 比如在 Facebook Bug 事件或 ASUS 路由器案件中公开的重大安全漏洞 —— 这些黑客向相关公司施压,促使其做出必要的改变和改进。但正如大卫・蒂德马什指出的那样,这种听起来很高尚的灰帽行为,当你开始看到他们所做事情可能引发的网络安全连锁反应时,就显得有些单薄了。
“The hacker straddles between white and black, potentially causing ripples in the cybersecurity domain.” – David Tidmarsh
“黑客处于白帽和黑帽之间,可能会在网络安全领域引发连锁反应。”—— 大卫・蒂德马什
Grey hat hackers find themselves in a murky ethical situation. Their discoveries can significantly improve the security of our online systems, but the way they go about doing this is often illegal and, thus, punishable by law. They hack into systems that they have no right to access in order to find vulnerabilities that they think need to be fixed. By doing this, they are breaking the law, yet their reasons for doing so and the results that they obtain might compel one to argue that they are, in fact, quite virtuous.
灰帽黑客发现自己处于一个模糊的伦理境地。他们的发现可以显著提高我们在线系统的安全性,但他们的行为方式通常是非法的,因此会受到法律制裁。他们入侵他们无权访问的系统,以寻找他们认为需要修复的漏洞。通过这样做,他们正在触犯法律,然而,他们这样做的原因以及他们所取得的结果可能会让人认为他们实际上是相当高尚的。
It is compelling that certain grey hat hackers make a successful shift into white hat roles. They don’t always wear the good guy’s badge with pride, but they might as well, since they help with cybersecurity—sometimes after donning a skin-tight “Cyber Security Avenger” costume on Halloween. Individuals like Kevin Mitnick and Marcus Hutchins highlight recent history in showing how some grey hat hackers leverage their skills within positive, ethical confines. What do you say we start with them? Veering from their past as bad boys and donning the positive “good guy” cap is a story worth telling and one with significant recent history attached to it.
一些灰帽黑客成功地转变为白帽黑客,这是令人信服的。他们并不总是自豪地佩戴 “好人” 的徽章,但他们也确实如此,因为他们帮助了网络安全 —— 有时甚至在万圣节穿上紧身的 “网络安全复仇者” 服装。像凯文・米特尼克和马库斯・哈钦斯这样的人物,展示了近年来一些灰帽黑客如何在其积极、道德的范围内利用他们的技能。我们何不从他们开始呢?从过去的 “坏男孩” 转变为戴上积极的 “好人” 帽子,这是一个值得一讲的故事,也是一个有着重要近期历史的故事。
Comprehending grey hat hackers is essential within cybersecurity because they exemplify the shortcomings of today’s ethical guidelines. Their existence also illustrates the much-needed necessity for robust systems and secure practices. They play a nuanced role. Yet, when you read the media stories, you get the impression that these hackers do it all for the love of the badge. In reality, though, these hackers occupy a rather complex space, and for many, the role isn’t so virtuous after all.
理解灰帽黑客在网络安全中至关重要,因为他们展示了当今道德准则的不足。他们的存在也凸显了对强大系统和安全实践的迫切需求。他们扮演了一个微妙的角色。然而,当你阅读媒体报道时,你会觉得这些黑客所做的一切都是为了徽章的荣耀。但实际上,这些黑客处于一个相当复杂的空间,对许多人来说,这个角色并不那么高尚。
Red Hat Hackers
红帽黑客

一幅充满活力的数字景观,其中包含红色和黑色帽子的抽象表示,象征着红帽黑客和黑帽黑客之间的冲突,周围环绕着发光的电路图案和二进制代码,传达出一种行动和警惕的感觉。
Amidst the cybersecurity scene, red hat hackers are perhaps the most aggressive and controversial group. Working outside the law, red hats zealously track down black hat hackers—those who exploit system vulnerabilities for their own gain. Red hats are not always the good guys. And unlike white hats, who hack only with permission and mostly for benign reasons, red hats don’t ask for anyone’s permission to engage in what can only be called vigilante justice.
在网络安全领域中,红帽黑客或许是其中最具攻击性和争议性的群体。他们在法律之外行动,热切地追踪那些为了自身利益而利用系统漏洞的黑帽黑客。红帽黑客并不总是 “好人”。与只在获得许可且大多出于善意的情况下进行黑客行为的白帽黑客不同,红帽黑客不会征求任何人的许可来进行所谓的 “义警式正义”。
“The Cybersecurity and Infrastructure Security Agency describes red hat hackers as ‘offensive security experts who operate in the jurisdictional gray area between hacktivism and criminality.'”
“网络安全和基础设施安全局将红帽黑客描述为‘在黑客主义和犯罪之间的司法灰色地带运作的攻击性安全专家’。”
Red hat hackers are sometimes likened to “digital vigilantes,” as they pursue their own form of justice against cybercriminals.
红帽黑客有时被比作 “数字义警”,因为他们追求自己对网络犯罪分子的正义。
Often, the reason red hat hackers do what they do is a thirst for vengeance or a desire to protect the digital world. But make no mistake: They’re not just sitting around waiting for the bad guys to attack before they spring into action like some sort of digital superhero. Red hat hackers are proactive in securing the digital world, taking the fight to bots, hackers, and other cybercriminals before these nefarious sorts can do any harm.
通常,红帽黑客之所以这么做,是因为他们渴望复仇,或者希望保护数字世界。但不要搞错:他们并不是像某种数字超级英雄一样,坐等坏人发动攻击后再采取行动。红帽黑客在保护数字世界方面是积极主动的,他们在那些不法分子造成任何伤害之前,就主动出击对抗机器人、黑客和其他网络犯罪分子。
Their existence and ethical boundaries are debated, too. Some see them as heroes in an unrelenting battle against cybercrime; other critics see them as reckless and undisciplined, self-styled cyber cowboys who could lead us all into a bad place if the next big breach is justified by the “unnecessary” forensics of the last big breach. The red-hat ethics is very much in play when considering the next set of hacking heroes.
他们的存在及其道德界限也备受争议。一些人将他们视为在与网络犯罪的不懈斗争中的英雄;而另一些批评者则认为他们是鲁莽且缺乏纪律的 “网络牛仔”,如果下一次重大漏洞被上一次重大漏洞的 “不必要” 取证所正当化,他们可能会把我们所有人带入一个糟糕的境地。在考虑下一组黑客英雄时,红帽黑客的道德问题非常关键。
The complex interplay between vigilantism and legality in the cybersecurity world is brought to light by the work of the so-called red hat hackers. If we don’t understand why these figures in this murky world are doing what they do, we can’t really explore the full dynamics of cybersecurity. But it’s not quite the same thing, as you will see if you read this short article explaining the largely unremarked-upon world of red hat hackers.
所谓的红帽黑客的工作揭示了网络安全领域中义警行为与合法性之间的复杂相互作用。如果我们不理解这些处于模糊世界中的人物为何要这么做,我们就无法真正探索网络安全的全部动态。但情况并不完全相同,正如你阅读这篇简短的文章时会看到的,它解释了红帽黑客这个鲜为人知的世界。
Blue Hat Hackers
蓝帽黑客
A serene workspace with a computer screen displaying code, surrounded by blueprints and cybersecurity tools, with two smiling engineers discussing ideas, sunlight streaming through a window.
一个宁静的工作空间,电脑屏幕上显示着代码,周围环绕着蓝图和网络安全工具,两名面带微笑的工程师正在讨论想法,阳光透过窗户洒进来。
Blue hat hackers have two key definitions that place them at the intersection of the cybersecurity field. Their role can vary quite a bit and can be pretty interesting, but it is an integral part of the cybersecurity ecosystem.
蓝帽黑客有两种关键定义,使他们处于网络安全领域的交叉点。他们的角色可能会有很大差异,也很有趣,但它是网络安全生态系统的一个重要组成部分。
“Basically, blue hat hackers represent a hybrid form of cybersecurity. They are neither bug bounty hackers, who find and fix bugs, nor are they the kinds of hackers that get hired to do pentests (penetration tests). They are vengeful hackers, using hacking as a way to settle personal grievances.”
“基本上,蓝帽黑客代表了一种混合形式的网络安全。他们既不是寻找和修复漏洞的漏洞赏金黑客,也不是被雇来进行渗透测试的黑客。他们是出于报复心理的黑客,利用黑客行为来解决个人恩怨。”
One way to define blue hat hackers is as agents of retribution. They hack not to steal or gain power but to get back at individuals or groups they think have wronged them. When blue hats hack, they might use any means necessary to accomplish their goals. That might include shutting down computer systems, tampering with data, or stealing access credentials so they can use computing resources while avoiding detection. Poorly written or untested software can also cause problems for blue hats and their targets. For example, they might deploy malware or engage in cyberattacks designed to damage or disrupt their targets. If a blue hat uses a piece of malware to attack a target, and that malware isn’t well designed, the attack might backfire and harm the blue hat’s own system.
定义蓝帽黑客的一种方式是将他们视为报复的代理人。他们黑客行为的目的不是为了偷窃或获取权力,而是为了报复那些他们认为伤害了他们的人或团体。当蓝帽黑客进行黑客行为时,他们可能会使用任何必要的手段来实现目标。这可能包括关闭计算机系统、篡改数据,或者窃取访问凭证以便使用计算资源而不被发现。编写不当或未经测试的软件也会给蓝帽黑客及其目标带来问题。例如,他们可能会部署恶意软件或发动旨在破坏或干扰目标的网络攻击。如果蓝帽黑客使用恶意软件攻击目标,而该恶意软件设计不当,攻击可能会适得其反,反而损害蓝帽黑客自己的系统。
Microsoft’s BlueHat briefings exemplify blue hats working positively by collaborating to enhance software security.
微软的 BlueHat 简报展示了蓝帽黑客通过合作增强软件安全性的积极一面。
In the cybersecurity field, blue hat hackers take on a decidedly constructive role. Companies often hire these external security experts to conduct impartial tests of their unreleased software. Before a product hits the market, blue hats perform penetration tests to expose potential vulnerabilities in these digital creations. They are ethical hackers who simulate cyberattacks to identify weaknesses without causing real harm. Microsoft plays a pivotal role in this context by hosting the BlueHat briefings , where blue hat hackers collaborate with the company’s engineers to enhance software security. These experts help safeguard systems by performing roles akin to white hat hackers , concentrating on detecting vulnerabilities and advising on enhancing security defenses.
在网络安全领域,蓝帽黑客扮演了一个明确的建设性角色。公司经常雇佣这些外部安全专家来对未发布的软件进行公正的测试。在产品上市之前,蓝帽黑客会进行渗透测试,以暴露这些数字产品中的潜在漏洞。他们是道德黑客,通过模拟网络攻击来识别弱点,而不造成实际损害。微软在这方面发挥了关键作用,通过举办 BlueHat 简报,让蓝帽黑客与公司的工程师合作,增强软件安全性。这些专家通过履行类似于白帽黑客的角色来帮助保护系统,专注于检测漏洞并建议增强安全防御。
We know these kinds of hackers exist. They operate in the twilight realm of the dark web, and in some cases, daylight. But those are just blue hat hackers.
我们知道这种黑客是存在的。他们在暗网的暮光地带活动,在某些情况下,也会在光天化日之下行动。但这些人只是蓝帽黑客。
Green Hat Hackers
绿帽黑客
Individuals who are at the earliest stage of their hacking journey often find themselves donning the green hat. These cyber novices are enthralled with developing their hacking skills and are driven by a curiosity that knows no bounds. As they work to elongate their hacking skill set, they seek out the most hackable targets. The commitment required to excel at hacking can be likened to the dedication needed to master a musical instrument (source).
那些处于黑客之旅最初阶段的人通常会戴上绿帽。这些网络新手对发展自己的黑客技能着迷不已,他们的好奇心是无止境的。在他们努力扩展自己的黑客技能集时,他们会寻找最容易被攻击的目标。想要在黑客领域出类拔萃所需要的承诺,可以与掌握一门乐器所需的专注相提并论。
“Script kiddies typically aim to execute pre-existing attacks and do so without a deep understanding of what they are doing. Green hat hackers, on the other hand, are intrigued by technology.” – Privacysense.net
“脚本小子通常旨在执行现成的攻击,并且在没有深刻理解自己所做事情的情况下就这么做了。而绿帽黑客则对技术本身感到好奇。”——Privacysense.net
Green hat hackers are acknowledged as novices and sometimes referred to as “wannabe” hackers. They are at a steep learning curve and are quite different from the more informal “script kiddies.” Script kiddies typically aim to execute pre-existing attacks and do so without a deep understanding of what they are doing (source). Green hat hackers, on the other hand, are intrigued by technology. They come with programming backgrounds and are slowly but surely gaining the knowledge needed to identify—and sometimes fix—system and network vulnerabilities (source).
绿帽黑客被认为是新手,有时被称为 “想要成为黑客的人”。他们处于一个陡峭的学习曲线上,与更随意的 “脚本小子” 有很大不同。脚本小子通常旨在执行现成的攻击,并且在没有深刻理解自己所做事情的情况下就这么做了。而绿帽黑客则对技术本身感到好奇。他们有编程背景,并且正在逐步积累识别 —— 有时甚至修复 —— 系统和网络漏洞所需的知识。
Despite being beginners, green hat hackers’ curiosity can sometimes lead them to discover vulnerabilities unintentionally.
尽管是初学者,绿帽黑客的好奇心有时会让他们无意中发现漏洞。
In the cybersecurity landscape, the potential threat from green hat hackers poses a twofold danger. Their inexperience carries the risk of them causing real damage while attempting to hack systems. Hacking is hard. System flaws are few and far between, and even experienced hackers don’t find them all. Hackers who are in it for the fun or the ego trip (which is the case for most green hat hackers) need to be shown the way back to the straight and narrow. Even when green hats pen test, which is allowed, they’re probably not very good at it, and they’re using not very ethical means to find vulnerabilities. There’s also the risk, not to be underestimated, that these individuals could mistakenly find themselves using a real cyber weapon. When that happens, green hats are more a danger to themselves and the cybersecurity landscape than are some other hacker types (source).
在网络安全领域,绿帽黑客的潜在威胁带来了双重危险。由于缺乏经验,他们在尝试入侵系统时可能会造成真正的损害。黑客行为是艰难的。系统漏洞少之又少,即使是经验丰富的黑客也并非总能找到。那些出于娱乐或虚荣心而参与黑客行为的人(这正是大多数绿帽黑客的情况)需要被引导回到正道。即使绿帽黑客进行渗透测试(这是被允许的),他们可能也不擅长此道,并且他们使用不太道德的手段来寻找漏洞。还有一个不可低估的风险,那就是这些个体可能会误打误撞地使用真正的网络武器。当这种情况发生时,绿帽黑客对自己和网络安全领域的威胁,可能比其他类型的黑客更大。
When green hat hackers deal with the intricacies of hacking, they provide something of a reminder in our field—there is an essential need for direct, continuous learning and for the consideration of ethics in cybersecurity. They serve as a bridge, really, in our profession, reminding us of the basic, unchanging fact that cyber threats will always be with us and are, in truth, always evolving.
当绿帽黑客处理黑客行为的复杂性时,他们为我们这个领域提供了一个提醒 —— 在网络安全中,直接的、持续的学习以及对伦理的考虑是至关重要的。他们实际上是我们这个行业的桥梁,提醒我们一个基本的、不变的事实:网络威胁将永远存在,并且实际上总是在演变。
Conclusion
结论
A vibrant digital landscape with colorful hacker symbols representing different hacker types, surrounded by glowing circuits and a secure server room in the background, with smiling cybersecurity professionals discussing strategies.
一个充满活力的数字景观,色彩斑斓的黑客符号代表着不同类型的黑客,周围环绕着发光的电路和背景中的安全服务器室,面带微笑的网络安全专业人士正在讨论策略。
Understanding the various categories of hackers is fundamental to constructing effective cybersecurity defenses in today’s digital world. From ethical white hat hackers to malicious black hat hackers , each type presents different challenges and just as many opportunities for the cybersecurity industry to learn from.
了解黑客的不同类别对于构建当今数字世界中有效的网络安全防御至关重要。从道德的白帽黑客到恶意的黑帽黑客,每种类型都带来了不同的挑战,同时也为网络安全行业提供了同等多的学习机会。
Continuous education in understanding hacker motives and techniques is crucial for improving cybersecurity measures.
持续的教育,以理解黑客的动机和技术,对于改进网络安全措施至关重要。
Grasping these nuances is essential for boosting our preparedness against cyber threats. Ethical hackers are fundamental to system protection because they find and fix vulnerabilities before malicious hackers can exploit them.
理解这些细微差别对于增强我们对网络威胁的准备至关重要。道德黑客对于系统保护至关重要,因为他们会在恶意黑客利用漏洞之前发现并修复这些漏洞。
“Cybersecurity architectures must assume that a determined adversary can breach any system and then defend as if human life and liberty depend on it (which, in many cases, they do).”
“网络安全架构必须假定一个坚定的对手能够突破任何系统,然后进行防御,就好像人类的生命和自由取决于它一样(在许多情况下,确实如此)。”
To effectively foresee and counteract potential cyber threats, organizations must understand the different types of hackers. Ethical hackers can be employed to help organizations better understand how to secure themselves against the kinds of digital onslaughts that nefarious sorts can inflict. In today’s digital world, organizations and the individuals within them must take some sort of cyber-defense posture.
为了有效地预见并应对潜在的网络威胁,组织必须了解不同类型的黑客。可以雇佣道德黑客来帮助组织更好地了解如何保护自己,免受那些不法分子可能发动的数字攻击。在当今的数字世界中,组织及其内部人员必须采取某种网络防御姿态。
As noted by experts, “Continuous education and robust cybersecurity measures are essential for individuals and organizations to protect against these diverse threats” (source). Grasping this situation fully allows the experts in our employ to ensure that the strategies they craft for our organization make us that much more resilient against threats and hackers of all manners.
正如专家所指出的,“持续的教育和强大的网络安全措施对于个人和组织来说,是抵御这些多样化威胁所必需的”。充分理解这一状况,使我们雇佣的专家能够确保他们为我们组织制定的策略,使我们能够更好地抵御各种威胁和黑客。
FAQ
What are the different types of hackers based on hat colors?
根据帽子颜色,黑客分为哪些不同类型?
Hackers are classified by hat colors, which symbolize their ethics and reasons for hacking. The main types are:
黑客根据帽子颜色进行分类,这些颜色象征着他们的道德和黑客行为的原因。主要类型包括:
-Black Hat Hackers: Malicious hackers who exploit vulnerabilities for harmful gains.
黑帽黑客:恶意黑客,利用漏洞获取有害的利益。
-White Hat Hackers: Ethical hackers who work to protect systems and conduct authorized testing.
白帽黑客:道德黑客,致力于保护系统并进行授权测试。
-Grey Hat Hackers: Individuals who find vulnerabilities without consent, sometimes revealing weaknesses to pressure organizations toward security improvements.
灰帽黑客:未经许可发现漏洞的个人,有时会揭露弱点,以促使组织改善安全状况。
-Red Hat Hackers: Vigilante hackers targeting black hats by any means, including illegal activities.
红帽黑客:义警黑客,通过任何手段(包括非法活动)针对黑帽黑客。
-Blue Hat Hackers: Defined either as agents of revenge or security testers for unreleased products.
蓝帽黑客:被定义为报复的代理人或未发布产品的安全测试者。
-Green Hat Hackers: Novices eager to learn, with varying understanding and skill levels.
绿帽黑客:渴望学习的新手,具有不同的理解和技能水平。
What motivates white hat hackers?
白帽黑客的动机是什么?
Also known as ethical hackers, white hat hackers aim to bolster cybersecurity. Working within the confines of the law, they seek out system vulnerabilities and mend them, thereby helping organizations fortify their defenses against a range of cyber threats.
白帽黑客也被称为道德黑客,他们致力于增强网络安全。他们在法律框架内工作,寻找系统漏洞并加以修复,从而帮助组织加强针对各种网络威胁的防御。
How do black hat hackers operate?
黑帽黑客是如何运作的?
Black hat hackers are the antagonists of the computer world. They are the ones who break into systems and set up botnets for denial-of-service attacks. They write ransomware. They use phishing and other social engineering techniques to compromise systems. They are the ones who really do threaten our national security.
黑帽黑客是计算机世界的反派。他们是那些入侵系统、设置用于拒绝服务攻击的僵尸网络的人。他们编写勒索软件。他们利用网络钓鱼和其他社会工程学手段来破坏系统。他们才是真正威胁我们国家安全的人。
What ethical dilemmas do grey hat hackers face?
灰帽黑客面临哪些伦理困境?
Operation of grey hat hackers occurs in a legally ambiguous zone. They find and identify vulnerabilities, but they do so without permission. Though what they do often enhances security, it also poses substantial legal risks. This paints them as a somewhat beneficent class of lawbreakers. Yet they can be portrayed as that, without glossing over the potential legal consequences their activities bring to both them and security.
灰帽黑客的运作处于一个法律模糊地带。他们发现并识别漏洞,但他们是未经授权这样做的。尽管他们的行为常常增强了安全性,但也带来了相当大的法律风险。这使他们被视为一种 “有益的” 违法者。然而,他们可以被这样描绘,而不会掩盖他们的活动给自身和安全带来的潜在法律后果。
Why are red hat hackers considered controversial?
为什么红帽黑客被认为是有争议的?
Red hat hackers are some of the most aggressive cybersecurity professionals. They say that their work isn’t too different from what the good guys in law enforcement do: track down criminals and take their operations offline. But the way that red hats go about their work—often using illegal means to achieve their ends—has drawn strong objections from many in the cybersecurity field. To a red hat, someone under a black hat is a malefactor.
红帽黑客是一些最具攻击性的网络安全专业人士。他们声称,他们的工作与执法部门的 “好人” 所做的工作并无太大不同:追踪犯罪分子并使他们的行动脱线。但红帽黑客开展工作的方式 —— 常常使用非法手段来实现他们的目标 —— 已经引起了网络安全领域许多人的强烈反对。对于红帽黑客来说,戴黑帽的人就是犯罪分子。
What roles do blue hat hackers play in cybersecurity?
蓝帽黑客在网络安全中扮演什么角色?
Either blue hat hackers have personal motives for hacking, or they engage in hacking for positive reasons. Testing unreleased software for security problems is a motive that some blue hats have. Helping to make hardware and software more secure is another motive that fits the blue hat hacker category. Unethical hacking is not something blue hats do. Microsoft is a company that occasionally employs blue hats to help them secure their products. BlueHat events are another reason why blue hats can be seen as a positive force in the computing world.
蓝帽黑客要么出于个人动机进行黑客行为,要么出于积极的原因进行黑客行为。有些蓝帽黑客的动机是测试未发布软件的安全问题。帮助使硬件和软件更加安全是另一个符合蓝帽黑客类别的动机。不道德的黑客行为并不是蓝帽黑客所为。微软是一家偶尔会雇佣蓝帽黑客来帮助他们保护产品的公司。BlueHat 活动是另一个原因,使蓝帽黑客被视为计算世界中的积极力量。
What distinguishes green hat hackers from other types?
绿帽黑客与其他类型有什么区别?
Green hat hackers are novices with a powerful curiosity about the world of the internet and cyberspace. They climb the increasingly steep learning curve of cyber skills and may threaten organizations without intending to. However, green hats arguably provide the most useful service of all: They help keep organizations on their toes by finding cybersecurity flaws before the bad guys do.
绿帽黑客是互联网和网络空间世界的好奇心很强的新手。他们正在攀登越来越陡峭的网络安全技能学习曲线,并可能无意中威胁到组织。然而,可以说绿帽黑客提供了最有用的服务:他们在坏人之前发现网络安全漏洞,帮助组织保持警惕。
Leetspeak: The History of Hacking Subculture’s Native Tongue
Leetspeak:黑客亚文化母语的历史
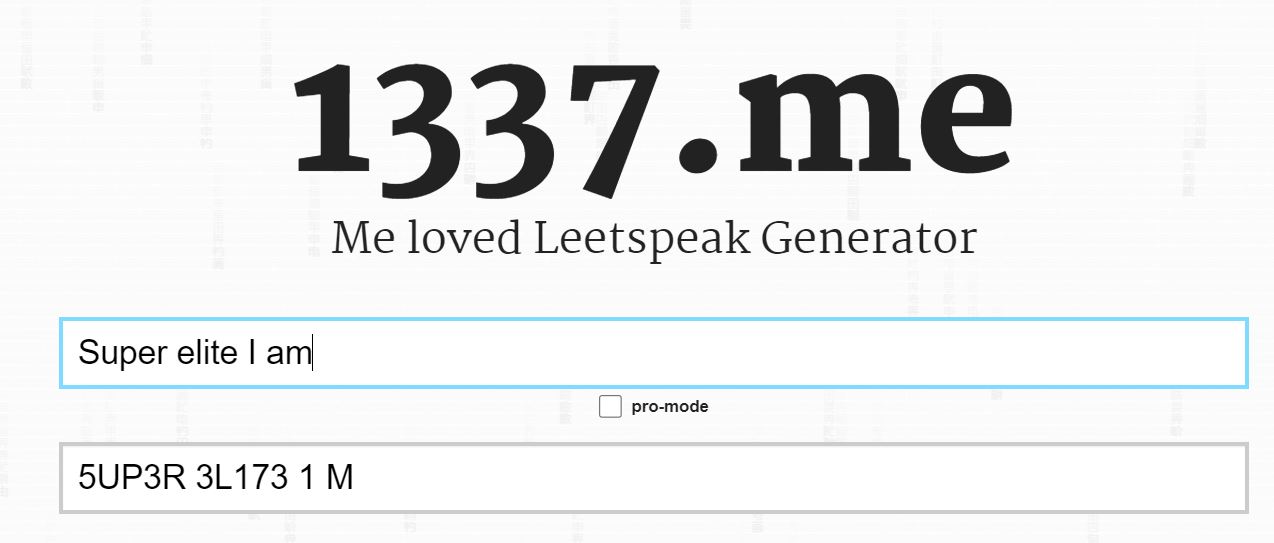
You’ve probably seen leetspeak, also known as 1337 or “l33t,” somewhere on the Internet or in a movie about computer hacking. It’s essentially regular English, but with more hacker slang and with certain letters changed to numbers.
你可能在互联网的某个地方或者关于电脑黑客的电影中见过“黑客语”(leetspeak),它也被称为 1337 或者 “l33t”。它本质上是普通英语,但包含更多的黑客俚语,并且某些字母被换成了数字。
Leetspeak – An Origin Story
黑客语——起源故事
Developed in the early 1980s,leetspeak actually predates the World Wide Web_ by nearly a decade. It started on Bulletin Board Systems when the Internet was first developing and only people with elite status could access certain content. That content often included information that those elites didn’t want anyone outside their circles to find.
黑客语在 20 世纪 80 年代早期形成,实际上比万维网的出现早了近十年。它起源于互联网刚刚兴起时的电子公告板系统(BBS),当时只有具有精英身份的人才能访问某些内容。这些内容通常包含那些精英们不希望圈子外的人发现的信息。
Outsmarting the System
智胜系统
In those days, search functions scanned for specific keywords to identify their targets. Early hacker communities figured out that changing a few of the letters within a word could throw the search engines off the proverbial scent. By using “h3ll0” for “hello,” for example, they could protect the privacy of their content while keeping it readable among themselves.
在那个时候,搜索功能通过扫描特定关键词来识别目标。早期的黑客社区发现,改变一个单词中的几个字母可以让搜索引擎找不到相关内容。例如,用 “h3ll0” 代替 “hello”,他们可以在保护内容隐私的同时,让自己人能够读懂。
The Mark of an “3l33t”
“精英(3l33t)” 的标志
As leetspeak became more well-known, gamers began to use it to present themselves as high status. The phrase “1 4m 3l33t!” (or, “I am elite!”) became a popular way for both gamers and hackers to show that they had reached the top of the pack.
随着黑客语越来越为人所知,游戏玩家开始用它来显示自己的高地位。“1 4m 3l33t!”(也就是 “I am elite!”,我是精英!)成为游戏玩家和黑客们展示自己处于领先地位的流行表达方式。
Levels of L33t
黑客语的等级
Th1s s3nt3nc3 1s wr1tt3n 1n b4sic l33t. (“This sentence is written in basic leet.”)
这个句子是用基础黑客语写的。
It’s pretty understandable, even to someone who isn’t well versed in the world of computer hacking. All you do is get rid of vowels and substitute numbers_ that look similar.
即使对于不太熟悉电脑黑客领域的人来说,这也相当容易理解。你所需要做的就是去掉元音字母,并用看起来相似的数字代替。
The Next Step
下一步
Intermediate-level leet starts to get the consonants involved, and it looks “50meth1n9 l1k3 th15.” It’s more challenging to read than basic leet but still decipherable, particularly to eyes and brains that are already familiar with the basic form. A 5 looks enough like an S, for example, that a reader can go from “is” to “1s” to “15” without excessive confusion.
中级黑客语开始涉及辅音字母,看起来像 “50meth1n9 l1k3 th15.”(“something like this”)。它比基础黑客语更难读懂,但仍然可以破译,特别是对于已经熟悉基础形式的人来说。例如,数字 5 看起来很像字母 S,读者可以从 “is” 到 “1s” 再到 “15”,而不会产生太多混淆。
Advanced Leet
高级黑客语
Advanced leet brings in yet more replacements, including more replacements per letter.
高级黑客语引入了更多的替换方式,包括每个字母有更多的替换选项。
If you read a message in basic or intermediate leet, the replacement for the letter E will almost always be the number 3. Once you get into advanced leet, however, you have a lot more options. You can still indicate E using 3, but you can also use &, €, ë, and even |=-. Just the word leet has dozens of possible translations, from the classic l33t to |&€”|”.
如果你读一条用基础或中级黑客语写的信息,字母 E 的替换通常几乎总是数字 3。然而,一旦进入高级黑客语阶段,你就有更多选择了。你仍然可以用 3 来表示 E,但你也可以用 &、€、ë,甚至 |= - 来表示。仅仅 “leet” 这个单词就有几十种可能的翻译,从经典的 l33t 到 |_&€”|” 等。
Your Basic L33t Vocabulary
你的基础黑客语词汇
As with any dialect, there are words that anyone who is “in the know” has to have in their vocabulary. Many of them have to do with status. (Specifically, the speaker being of a higher status than others.)
和任何方言一样,对于那些 “懂行” 的人来说,有些单词是他们词汇中必须有的。其中很多单词都与地位有关。(具体来说,说话者的地位比其他人高。)
“Pwn”
“Pwn” is one of the most popular leetspeak words in hacker culture. It’s an intentional typo of “own,”_ a word that the early hackers of the 80’s used to mean taking over control of another computer.
“Pwn” 是黑客文化中最流行的黑客语单词之一。它是 “own” 的故意拼写错误,20 世纪 80 年代的早期黑客用 “own” 这个词表示接管控制另一台计算机。
Urban legends offer a number of explanations for how the shift from “own” to “pwn” happened. Some say that it has always been an intentional misspelling, while others say that it was an honest mistake that took off in common usage.
关于从 “own” 到 “pwn” 的转变是如何发生的,有很多都市传说给出了解释。有些人说这一直是故意的拼写错误,而另一些人说这是一个无意的错误,但在日常使用中流行了起来。
In either case, it’s become a popular way to express your victory or defeat. While you can definitely “pwn” someone, it’s also common to admit that you “g0t pwned.” It’s usually pronounced “got poned.”
无论哪种情况,它都成为了表达胜利或失败的流行方式。你当然可以 “pwn” 某人,承认自己 “g0t pwned”(被打败了)也很常见。它通常发音为 “got poned”。
“N00b”
N00b, or “noob” in non-leetspeak, is a shortened form of “newbie.” Programmers and hackers started calling people “newbies” around the same time that they started “owning” each others’ systems. And like “own,” the word newbie evolved into noob and n00b.
N00b,或者在非黑客语中是 “noob”,是 “newbie”(新手)的缩写形式。程序员和黑客在开始 “接管” 彼此的系统时,差不多也开始把人称为 “newbies”。和 “own” 一样,“newbie” 这个词演变成了 “noob” 和 “n00b”。
The new spellings are specifically derogatory. Being a “newb” simply means that you’re new at something, which is perfectly fine in and of itself. If someone’s calling you a “n00b” or “noob,”[_]](https://www.digitaltrends.com/gaming/noob-newbie-word-origins/) however, that usually means that they think you’re not only new or unskilled but also disrespectfully content to be ignorant.
这些新的拼写方式带有明显的贬义。成为一个 “newb” 仅仅意味着你在某方面是新手,这本身并没有什么问题。然而,如果有人叫你 “n00b” 或 “noob”,那通常意味着他们认为你不仅是新手或没有技能,而且还对自己的无知满不在乎。
Haxor
黑客(Haxor)
Like the first leetspeak words, “haxor” expresses the speaker’s claim to the hacking community. It literally means “hacker” or even “to hack.”
和最早的黑客语单词一样,“haxor” 表达了说话者对黑客社区的认同。它字面上的意思是 “黑客”,甚至是 “进行黑客攻击”。
The term “haxor” usually refers to a particularly advanced hacker_ (or haxor) and may even be used in reference to leetspeak itself. For example, “that haxor always types haxor.”
“haxor” 这个词通常指的是一个特别厉害的黑客(或者 haxor),甚至可能用来指代黑客语本身。例如,“that haxor always types haxor.”(那个黑客总是打出 “haxor” 这个词。)
Leetspeak Out in the World
黑客语在现实世界中的应用
Even now, leetspeak continues to evolve and make its way into new corners of our perpetually connected society. Google even uses it to communicate with members of the general public, but with an insider nod to hacker culture.
即使在现在,黑客语仍在不断演变,并进入我们这个始终互联的社会的新领域。谷歌甚至用它与普通大众交流,同时也向黑客文化的内行人士致敬。
Google’s Bug Bounty
谷歌的漏洞赏金计划
The Google Vulnerability Reward Program (VRP), known colloquially as its “bug bounty,” offers rewards to users who can identify and draw Google’s attention to security vulnerabilities that can compromise user data.
谷歌漏洞奖励计划(Google Vulnerability Reward Program,简称 VRP),俗称 “漏洞赏金”,向能够识别并引起谷歌注意那些可能危及用户数据的安全漏洞的用户提供奖励。
If a user finds such a vulnerability in a qualifying Google site, the specifics of which are detailed on the VRP website_, Google will offer a financial reward. Reward amounts range from $100 to $31,337. Remove the comma and the dollar sign from that maximum amount and you have “31337.”
如果用户在符合条件的谷歌网站上发现这样的漏洞(具体细节在 VRP 网站 上有详细说明),谷歌将提供经济奖励。奖励金额从 100 美元到 31337 美元不等。去掉最高金额中的逗号和美元符号,你就得到了 “31337”。
Or, in non-leetspeak, “eleet.”
或者,用非黑客语来说,是 “eleet”(与 1337 的发音类似)。
Hacker Movies
黑客电影
Hacker culture even has its own filmography_. A quick Google search for “hacker movies” will give you lists of what dozens of people believe to be the best. Popular titles include:
黑客文化甚至有自己的电影作品。在谷歌上快速搜索 “hacker movies”(黑客电影),你会得到几十个人认为最好的黑客电影列表。受欢迎的电影包括:
- Untraceable (2008)
《网络犯罪调查》(2008 年) - The Italian Job (2003)
《偷天换日》(2003 年) - The Matrix (1999)
《黑客帝国》(1999 年) - Hackers (1995)
《黑客》(1995 年)
One recent example is the movie adaptation of the novel Ready Player One, the story of one gamer’s search for the industry’s biggest “Easter egg.” The book and the movie both include characters with leetspeak names.
最近的一个例子是小说《头号玩家》改编的电影,讲述了一个游戏玩家寻找该行业最大 “复活节彩蛋” 的故事。原著和电影中都有名字是用黑客语起的角色。
These characters are employees of the big bad corporation, IOI. They are known as the “suxorzs,” or the “sux0rz.” The word is a leetspeak translation of “sixers,” a nickname given because of their avatar names are also their six-digit employee numbers_. It is also the leetspeak term for “this sucks.”_
这些角色是大反派公司 IOI 的员工。他们被称为 “suxorzs” 或者 “sux0rz”。这个词是 “sixers” 的黑客语翻译,“sixers” 这个昵称是因为他们的虚拟角色名字也是他们的 六位员工编号。它也是 黑客语中表示 “这很糟糕” 的词。
Leetspeak and You
黑客语和你
Some people take to leetspeak like a natural second language. These are the people who might go on to pursue a career in hacking – and yes, it is possible. Even legal.
有些人很自然地就把黑客语当作第二语言。这些人可能会继续从事黑客职业——是的,这是可能的,甚至是合法的。
The first step is training in cybersecurity and penetration testing. Through professionally designed courses, like those offered by Cerberus Sentinel, you can learn the techniques that hackers – sorry, haxors – use to access today’s systems.
第一步是进行网络安全和渗透测试方面的培训。通过像 Cerberus Sentinel 提供的那些专业设计的课程,你可以学习黑客(抱歉,是 haxors)用来访问当今系统的技术。
Go ahead – build a career that will let you pwn the h4x0rs. Also, develop some people skills while you’re at it – read my book “The Smartest Person in the Room”_ to learn how.
大胆去做吧——建立一份能让你打败那些厉害黑客(h4x0rs)的职业。同时,在这个过程中培养一些人际交往能力——阅读我的书 《房间里最聪明的人》 来学习怎么做。
How to turn your biggest unknown weakness into your strongest defense.
如何将你最大的未知弱点转化为最强有力的防御
Bestseller by leadership & cybersecurity expert Christian Espinosa that unveils a simple proven and powerful 7 step process that removes the glass ceiling holding you down by awakening your leadership and life skills.
领导力与网络安全专家克里斯蒂安·埃斯皮诺萨(Christian Espinosa)的畅销书,揭示了一个经过验证的简单而强大的七步流程,通过唤醒你的领导能力和生活技能,打破阻碍你发展的玻璃天花板。
“Swiss Army Knife of Cyber/IT/Business/Life help…there is something for everyone here!”
“网络/信息技术/商业/生活方面的‘瑞士军刀’式帮助……这里总有适合每个人的内容!”
“I highly recommend that any cybersecurity leader, or aspiring leader, read this book from cover-to-cover.”
“我强烈建议任何网络安全领域的领导者,或者有志向成为领导者的人,从头到尾通读这本书。”
“Christian Espinosa unveils the hard-hitting truth and bad practices that companies face when they hire inexperienced and ego-centric cybersecurity staff to protect their company’s information.”
“克里斯蒂安·埃斯皮诺萨揭示了公司在雇佣缺乏经验且以自我为中心的网络安全人员来保护公司信息时所面临的残酷现实和不良做法。”
The Smartest Person in the Room Description:
《房间里最聪明的人》内容简介:
Cyberattack—an ominous word that strikes fear in the hearts of nearly everyone, especially business owners, CEOs, and executives. With cyberattacks resulting in often devastating results, it’s no wonder executives hire the best and brightest of the IT world for protection. But are you doing enough? Do you understand your risks? What if the brightest aren’t always the best choice for your company?
网络攻击——一个不祥的词汇,几乎让每个人,尤其是企业主、首席执行官和高管们心生恐惧。由于网络攻击常常会导致毁灭性的后果,难怪高管们会聘请信息技术领域最优秀、最聪明的人才来提供保护。但你做得足够了吗?你了解自己所面临的风险吗?如果最聪明的人并不总是适合你公司的最佳选择,那该怎么办呢?
In The Smartest Person in the Room, Christian Espinosa shows you how to leverage your company’s smartest minds to your benefit and theirs. Learn from Christian’s own journey from cybersecurity engineer to company CEO. He describes why a high IQ is a lost superpower when effective communication, true intelligence, and self-confidence are not embraced. With his seven-step methodology and stories from the field, Christian helps you develop your team’s technical minds so they become better humans and strong leaders who excel in every role. This book provides you with an enlightening perspective of how to turn your biggest unknown weakness into your strongest defense.
在《房间里最聪明的人》一书中,克里斯蒂安·埃斯皮诺萨向你展示了如何利用公司里最聪明的人才,让他们既为你也为他们自己带来好处。从克里斯蒂安自己从网络安全工程师成长为公司首席执行官的历程中汲取经验。他阐述了为什么当缺乏有效的沟通、真正的智慧和自信时,高智商就会失去其超能力的作用。通过他的七步方法论和来自实际领域的故事,克里斯蒂安帮助你培养团队的技术思维,使他们成为更优秀的人才和在各个角色中都表现出色的强大领导者。这本书为你提供了一个具有启发性的视角,让你了解如何将自己最大的未知弱点转化为最强有力的防御。
via:
-
Understanding Hacker Hat Colors - Findings
https://findings.co/understanding-hacker-hat-colors/ -
Leetspeak: The History of Hacking Subculture’s Native Tongue - Christian Espinosa
https://christianespinosa.com/blog/leetspeak-the-history-of-hacking-subcultures-native-tongue/ -
Hacking Away at the Counterculture | POSTMODERN CULTURE
https://www.pomoculture.org/2013/09/26/hacking-away-at-the-counterculture/ -
Hacking Hackers: Ethnographic Insights Into The Hacker Subculture –Definition, Ideology And Argotbysteven William Kleinknecht, B.A.2003
-
Hacker Culture - Douglas Thomas Copyright Date: 2002






















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








