讲的会有点啰嗦
一次抓包 发现的问题
tcpdump -vvv -X -n -i any -s0 host “xx.xx.xx.xx” and port 22 -w xxx.pcap
然后从数据中发现了一问题,总所周知,ssh 通过加密的方式传递数据 多以 也会把 ssh 当作隧道 通信
然后在抓的数据中发现了一些 tcp协议的数据包,然后分析这些包,全都是建立通信的包,然后再google
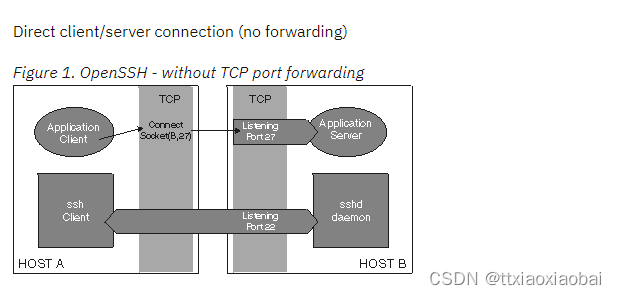
OpenSSH provides TCP port forwarding, also known as tunnelling, which allows other TCP applications to forward their network data over a secure SSH connection. In other words, existing TCP applications that do not encrypt their data before sending it across the network can send their network traffic through an SSH channel, thereby securing it.
Without TCP forwarding, an application’s client connections directly to its server across the network, as shown in Figure 1. To use port forwarding, an existing SSH session must exist.
简单粗俗的理解,我们使用ssh 对linux 操作 就是这个原理,进程间的通信本地 client port2001 tcp server port 27 在传输数据的使用采用ssh 隧道 port 22
所以当重点在ssh 隧道时, 数据转发 也就是tcp forword
好像理解这个也没有多大的作用



####################################################
有一点需要注意的是,数据包中的真实内容如果不采用加密的方式,那谁都可以看到,也就是我们常说的光膀子跳舞 然后虽然抓包能获得原始数据 比如 以十六进制展示,但是 这数据的转义后的意义你是不了解的。
###################################################
ssh 通信 原理 流程
Authentication
The first step is that the SSH server and client authenticate themselves to one another. The server sends a certificate to the client to verify that it is the correct server. When making contact, there is the risk that a third party will get between the two participants and therefore intercept the connection. Since the certificate itself is also encrypted, it cannot be imitated. Once the client knows what the correct certificate is, no third parties can contact the relevant server.
After server authentication, however, the client must also identify itself as being authorized to access the server. A password can be used for this purpose. This (or the encrypted hash value of it) is stored on the server. As a result, users must enter their password each time they log onto the different server during the same session. For this reason, there is an alternative method of client-side authentication using the key pair public key and private key.
The private key is created individually for your own computer and secured with a passphrase that should be longer than a typical password. The private key is stored exclusively on your own computer and always remains secret. If you want to establish an SSH connection, just enter the passphrase and you will gain access to the private key.
There are also public keys on the server (just like on the client itself). The server creates a cryptographic problem with its public key and sends this to the client. The server then decrypts the problem with its own private key, sends the solution back, and informs the server that it is allowed to establish a legitimate connection.
During a session, you only need to enter the passphrase once to connect to any number of servers, At the end of the session, users should log off from their local computers to ensure that no third party with physical access to the local computer can connect to the server.
Encryption
After mutual authentication, the two communication participants establish an encrypted connection. To do this, a key is generated for the session, which expires when the session is over. This is not to be confused with the public/private key pairs, which are only used for key exchange. The key used for symmetric encryption is only valid with this one session. Both client and server have the same key, so any messages that are exchanged can be encrypted and decrypted. Client and server create the key simultaneously, but independently of one another. In the so-called key change algorithm, both parties use certain public and secret information to create the key.
Another form of encryption takes place in SSH through hashing. A hash is a form of signature for the transmitted data. An algorithm generates a unique hash from the data. If data is manipulated, the hash value changes automatically. This way the recipient can know whether data has been changed by third parties along the way. The hash values are designed in such a way that they cannot be easily simulated. It’s not possible to create two different transmissions with the same hash – this is known as collision protection.
SSH ports
TCP ports are endpoints that open servers and clients to enable communication. As with a port, the communication partners receive and send the data packets via these ports. TCP has an address space of 16 bits and therefore 65535 ports are available. However, the internet assigned numbers authority (IANA) has assigned a number of ports (exactly 1024) for certain applications, including the SSH port. By default, all SSH connections run on port 22.







 文章讨论了如何通过SSH进行数据加密通信,包括SSH隧道原理、端口转发的应用、以及抓包时如何处理未加密数据的安全性。重点强调了SSH认证过程和加密机制,以确保数据在传输中的安全性。
文章讨论了如何通过SSH进行数据加密通信,包括SSH隧道原理、端口转发的应用、以及抓包时如何处理未加密数据的安全性。重点强调了SSH认证过程和加密机制,以确保数据在传输中的安全性。
















 442
442

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








