说明:“考点拾遗”系列基于日常为学员和网友做的答疑整理,主要涉及教材中没有完全覆盖到的知识点。
以下内容主要参考的NIST SP 800-162和NIST SP 800-178,本人水平有限,请以原文为准。
ACL(IBAC):
注意ACL是以客体为出发点的权限控制实现(具体请查阅CISSP教材访问控制矩阵、访问控制列表、访问能力表相关知识点内容)。
在IBAC模型中,如果一个主体提供的凭证与ACL中要求的凭证相匹配,则该主体被给予对客体的访问权。每个主体对该客体可执行的操作(读、写、编辑、删除等)权限,由客体所有者单独管理。每个客体都有自己的ACL和分配给每个主体的一组特权。
在IBAC模型中,授权决定在任何特定的访问请求之前做出,并导致主体被添加到ACL中。这个决定是静态的,需要一个通知过程来应对主体、客体或上下文可能发生的变化,当上述因素变化时,通知客体所有者重新评估和修改ACL。
如果涉及跨机构访问,即机构A的用户需要访问机构B的资源时,需要在机构B中预先为机构A的用户创建账号,并在访问列表中预先填写许可的操作。
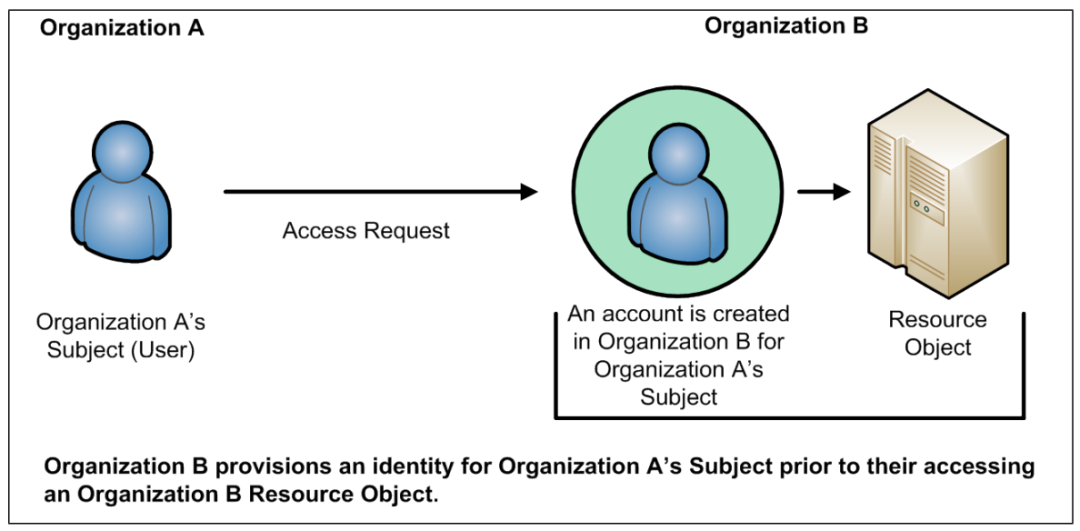
IBAC模型的特征:
-
每个客体对应一个ACL;
-
权限逐一的分配给单个主体。
RBAC
基于角色的访问控制模型采用了可分配给主体、具有特定权限集合的预定义角色。在处理主体的访问请求时,访问控制机制评估已分配给该主体的角色,以及该角色已被授权对客体执行的操作集(权限集合),然后呈现和执行访问决策。
与IBAC相似,授权决定是静态的,在访





 本文解析了访问控制领域的三种核心模型:IBAC、RBAC及ABAC。分别介绍了它们的工作原理、特点及其应用场景,并强调了ABAC模型在动态访问控制方面的优势。
本文解析了访问控制领域的三种核心模型:IBAC、RBAC及ABAC。分别介绍了它们的工作原理、特点及其应用场景,并强调了ABAC模型在动态访问控制方面的优势。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 336
336

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








