目录
ez_usb
题目描述:
简单的流量。
解题思路:
下载附件,解压得到一个流量包,如题,是USB流量分析。

观察发现主要有2.4.1、2.8.1、2.10.1三个Source的键盘输入,分别进行筛选并导出;



然后利用kali自带的tshark工具提取对应的内容;
tshark -T json -r 241.pcapng > 241.json
tshark -T json -r 281.pcapng > 2101.json
tshark -T json -r 2101.pcapng > 281.json
//用法 tshark -T json -r 数据包名称 > 要导出的文件得到的文件json文件用Notepad++打开,其中的usb.capdata标黄部分对应的就是键盘操作 ;
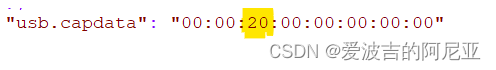
然后通过编写Python脚本来对应键盘操作的具体内容;
#!/usr/bin/env python
# -*- coding:utf-8 -*-
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
output = []
keys = open('usbdata.txt')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
print("".join(output))
for i in range(len(output)):
try:
a=output.index('<DEL>')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="<CAP>":
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output :' + "".join(output))
usb.src == "2.4.1"没有发现
usb.src == "2.8.1"得到以下内容:
526172211a0700<CAP>c<CAP>f907300000d00000000000000c4527424943500300000002<CAP>a000000<CAP>02b9f9b0530778b5541d33080020000000666c61672<CAP>e<CAP>747874<CAP>b9b<CAP>a013242f3a<CAP>fc<CAP>000b092c229d6e994167c05<CAP>a7<CAP>8708b271f<CAP>fc<CAP>042ae3d251e65536<CAP>f9a<CAP>da87c77406b67d0<CAP>e6316684766<CAP>a86e844d<CAP>c81aa2<CAP>c72c71348d10c4<CAP>c<DEL>3d7b<CAP>00400700其中,<CAP>是大写锁定,<DEL>是删除键,手工打一遍就行;
本来以为是编码的,尝试解密失败了,然后再看了看,哦!好像是rar文件头诶!?上Winhex!

保存并解压,发现有密码,1-6位爆破一下,发现不行,看来得找密码了;

usb.src == "2.10.1"得到以下内容:
35c535765e50074a这个虽然看着不太像,但是试了试,是密码!
成功得到flag!!!
基于挑战码的双向认证、基于挑战码的双向认证2:
题目描述:
本题含有两个flag,请点击“下发赛题”,本题容器下发后的端口是ssh端口,ssh的账号密码均为:player;ssh登录上去可自行修改密码。请参考说明文档,获取flag,并在本题提交第一个获取到的flag。
请提交“基于挑战码的双向认证”题目容器内的第二个flag。
解题思路:
首先,本题解题关键——谢谢出题师傅!谢谢出题师傅!!谢谢出题师傅!!!
ssh连接 ,习惯性先……尝试……搜索一下……好了,两题flag到手,晚安!!
grep -r "flag{" /
基于挑战码的双向认证3
题目描述:
请点击“下发赛题”,本题容器下发后的端口是ssh端口,ssh的账号密码均为:player;ssh登录上去可自行修改密码。请参考第1题的说明文档,获取flag,并在本题提交flag。
解题思路:
老样子,本题解题关键依旧是——谢谢出题师傅!谢谢出题师傅!!谢谢出题师傅!!!
ssh连接 ,再来习惯性先……尝试……搜索一下……阿巴阿巴……Permission denied来了!
小问题,不要慌,弱口令trytry!!!芜湖,root密码是toor!好耶!
然后嘛,就是熟悉的……尝试……搜索一下……好了,又一个flag到手,晚安啦!!
find / -name flag2.txt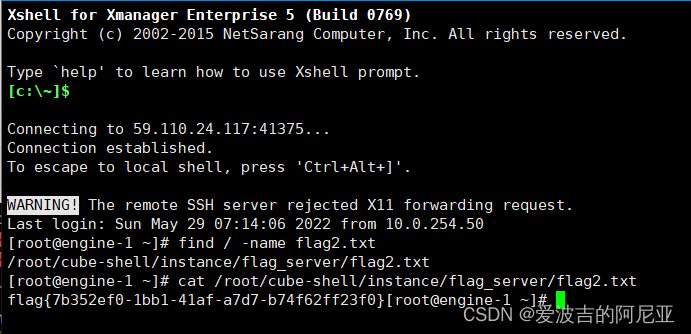
ISO9798
题目描述:
听说 ISO9798-2 很安全,但实际上是这样的吗?
解题思路:
感谢Crypto师傅大发慈悲,有生之年做出这么多Crypto,真是太开心了好叭!!!
下发赛题,给的nc连接,要我给他算个SHA256头部的四位;
![]()
正好最近看了看Go语言,发现一个github上大佬的Go语言SHA-256爆破脚本;
链接:https://github.com/hydewww/sha256-go
package main
import (
"bytes"
"crypto/sha256"
"encoding/hex"
"fmt"
"runtime"
"sync"
"time"
)
var (
chars = []byte("ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz1234567890")
tail = []byte("YH864OHM84wAhpLp")
result, _ = hex.DecodeString("96dd533dd79b6a14007dc3e2968080463a92092da555a37c67b1f17d8004b760")
wg sync.WaitGroup
)
func sha(s []byte) {
for _, ch1 := range s {
for _, ch2 := range chars {
for _, ch3 := range chars {
for _, ch4 := range chars {
head := []byte{ch1, ch2, ch3, ch4}
h := sha256.New()
h.Write(head)
h.Write(tail)
if bytes.Equal(h.Sum(nil), result) {
fmt.Println(string(head))
}
}
}
}
}
wg.Done()
}
func main() {
threads := runtime.NumCPU() // 获取cpu逻辑核心数(包括超线程)
start := time.Now()
/* len(chars) = sum * sthreads + (sum+1) * (threads-sthreads) */
snum := len(chars) / threads
sthreads := threads*(1+snum) - len(chars)
wg.Add(threads)
for i := 0; i < threads; i++ {
if i < sthreads {
go sha(chars[snum*i : snum*(i+1)])
} else {
base := snum * sthreads
go sha(chars[base+(snum+1)*(i-sthreads) : base+(snum+1)*(i-sthreads+1)])
}
}
wg.Wait()
end := time.Since(start)
fmt.Println(end)
}爆破完,发给他,又给我提了个问题,阿巴阿巴……

给出的是rA||rB||B,要求的是rB||rA,猜测可能是ECB模式加密,就把0-32,32-64位置互换即可。

























 946
946

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










