先看一下运行效果:
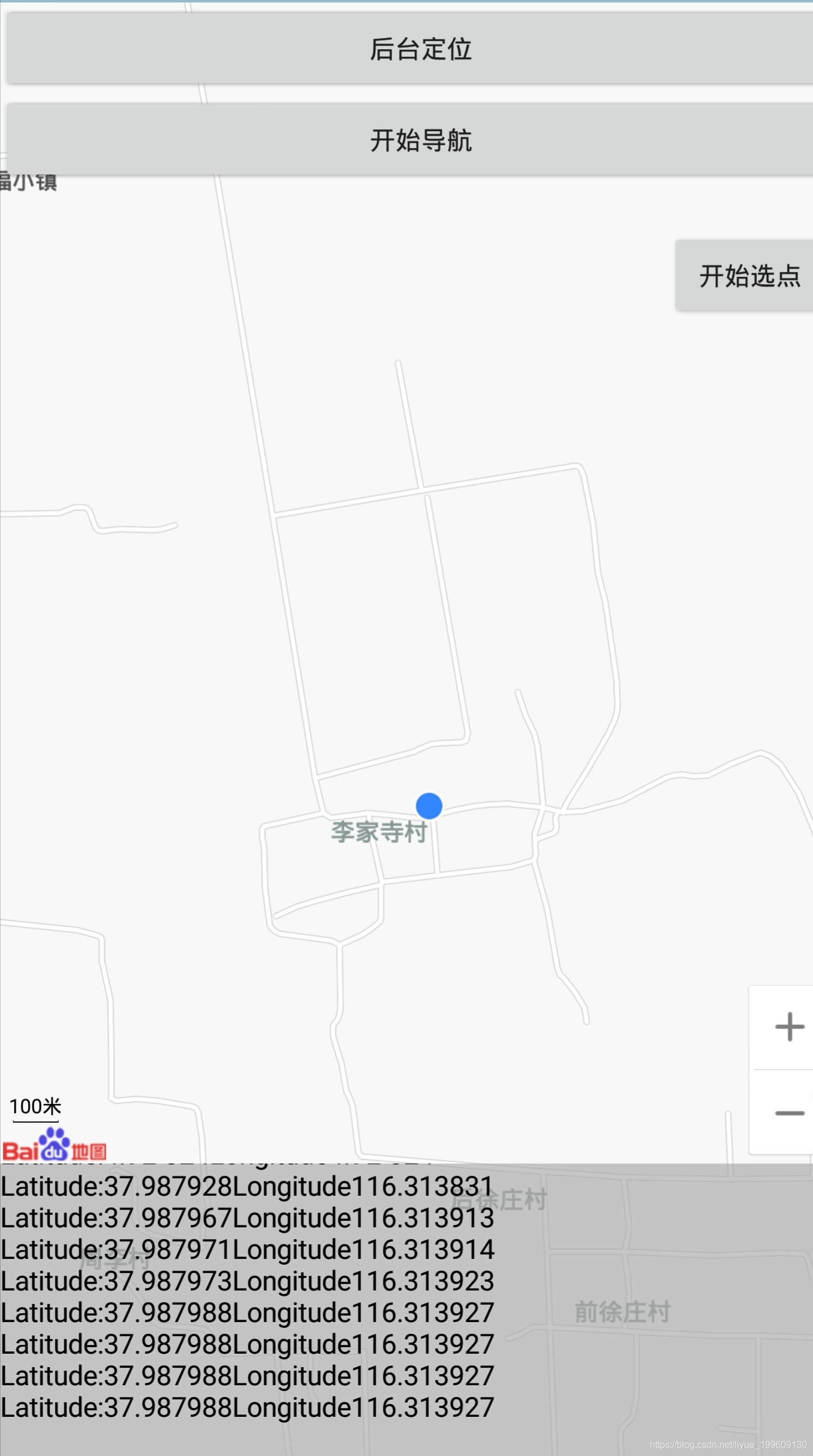
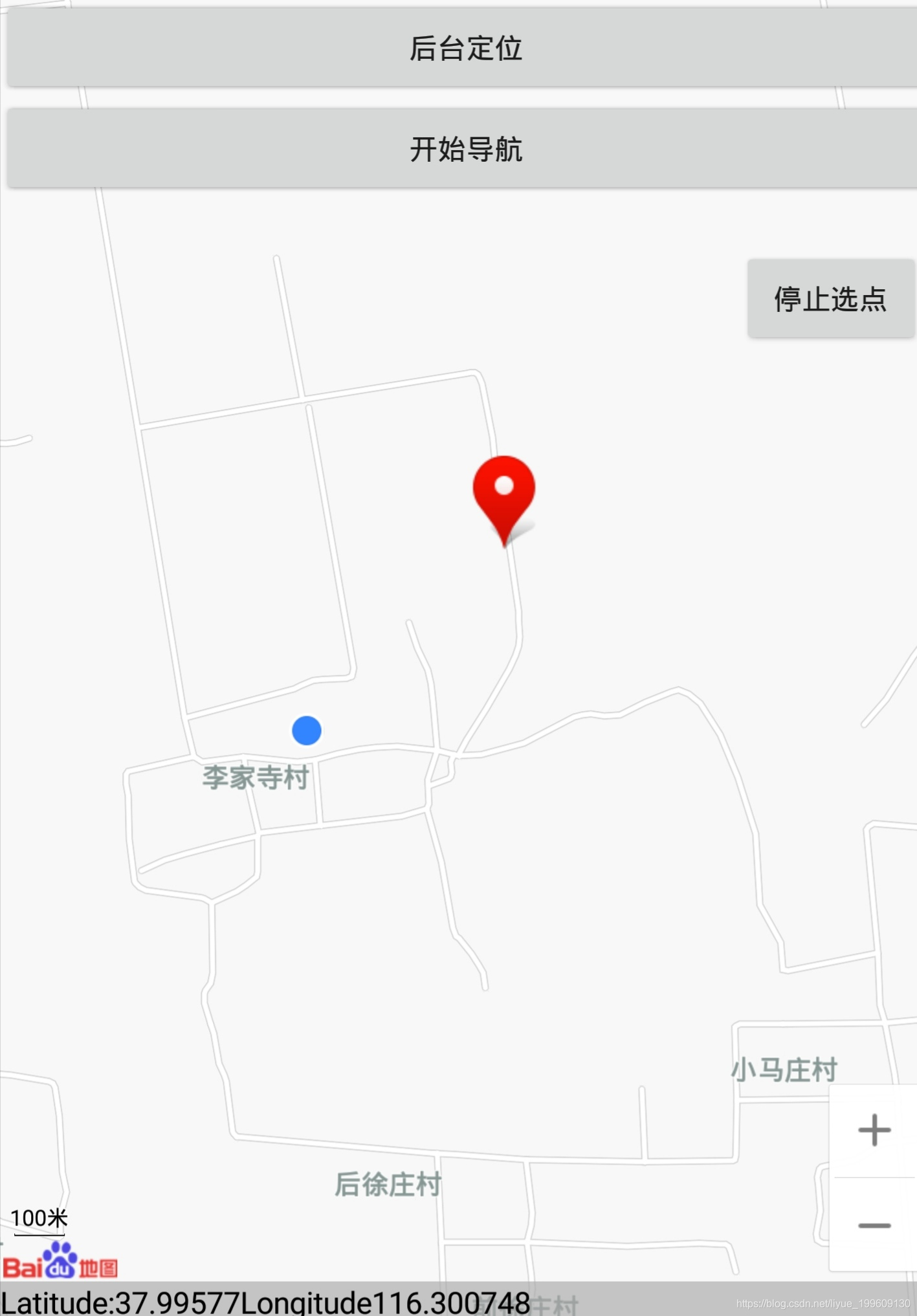
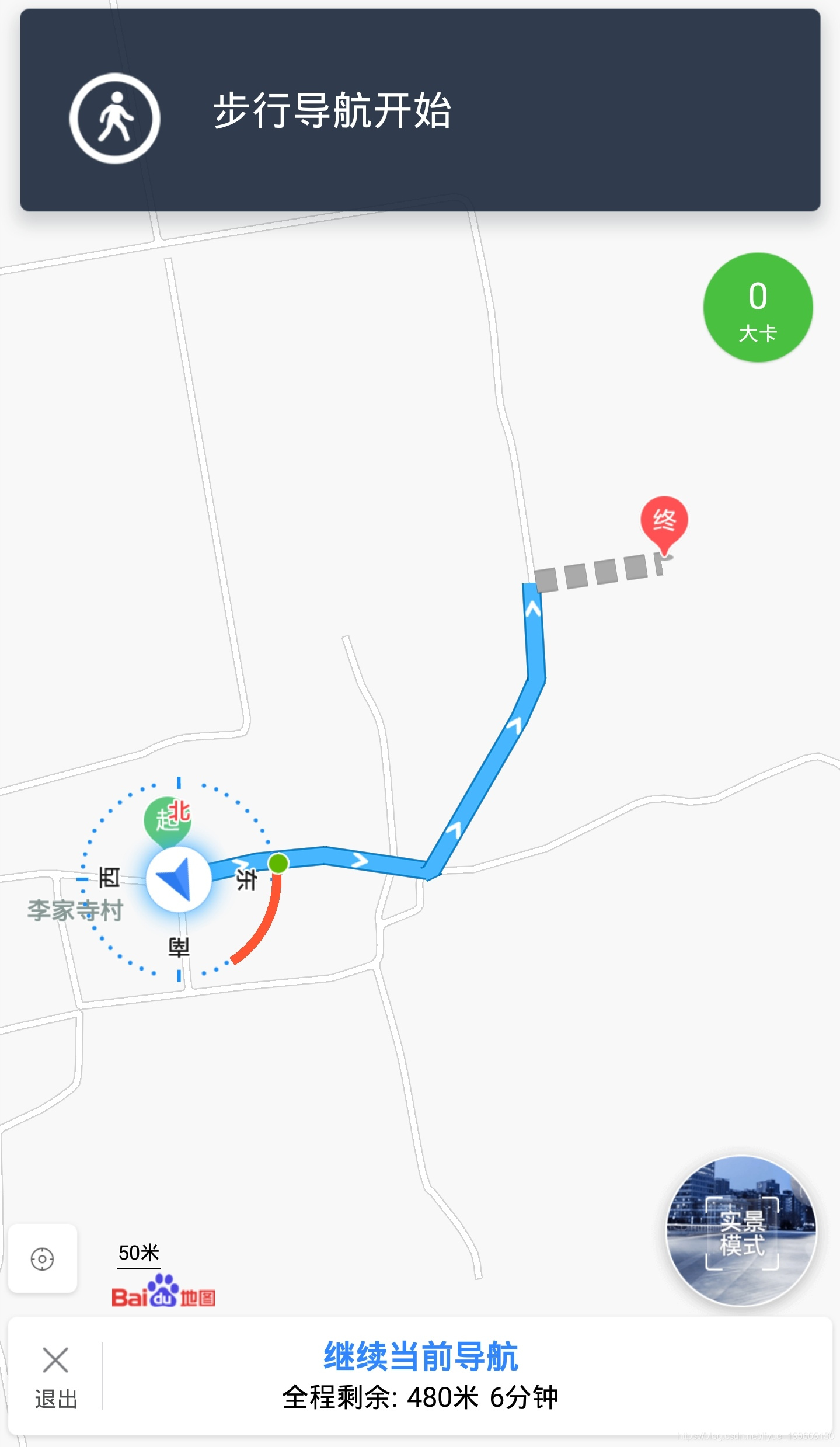
实现功能:后台定位+步行导航(可通过长按屏幕自定义终点,起点为定位点)
后台定位即当程序在后台时依旧执行定位功能,步行导航支持30米-50千米范围内的导航
一 导入SDK并配置相关信息
SDK下载和AK创建详见 Android Studio调用百度地图(一):注册成为百度地图开发者并下载SDK
SDK的导入具体可见百度地图官网
这里我要说的是实现定位和导航时需要注意的地方。
在proguard-rules.pro中添加
-dontoptimize
-ignorewarnings
-keeppackagenames com.baidu.**
-keepattributes Exceptions,InnerClasses,Signature,Deprecated,SourceFile,LineNumberTable,LocalVariable*Table,*Annotation*,Synthetic,EnclosingMethod
-dontwarn com.baidu.**
-dontwarn com.baidu.navisdk.**
-dontwarn com.baidu.navi.**
-keep class com.baidu.** {
*; }
-keep interface com.baidu.** {
*; }
-keep class vi.com.gdi.** {
*; }
-dontwarn com.google.protobuf.**
-keep class com.google.protobuf.** {
*;}
-keep interface com.google.protobuf.** {
*;}
在AndroidManifest.xml中添加

二 调用百度地图API实现后台定位和步行导航
1 实现后台定位核心代码
// 定位初始化
private void initLocationSDK() {
mClient = new LocationClient(this);
LocationClientOption mOption = new LocationClientOption();
mOption.setScanSpan(5000);
mOption.setCoorType("bd09ll");//设置坐标类型
mOption.setIsNeedAddress(true);//设置是否需要地址信息,默认为无地址。
mOption.setOpenGps(true);
mClient.setLocOption(mOption);
mClient.registerLocationListener(myLocationListener);
}
//开始后台定位
private void settingLocInForeground() {
//android8.0及以上使用NotificationUtils
if (Build.VERSION.SDK_INT >= 26) {
mNotificationUtils = new NotificationUtils(this);
Notification.Builder builder2 = mNotificationUtils.getAndroidChannelNotification
("适配android 8限制后台定位功能", "正在后台定位");
notification = builder2.build();
} else {
//获取一个Notification构造器
Notification.Builder builder = new Notification.Builder(DeleveryInfo.this);
Intent nfIntent = new Intent(DeleveryInfo.this, DeleveryInfo.class);
builder.setContentIntent(PendingIntent.
getActivity(DeleveryInfo.this, 0, nfIntent, 0)) // 设置PendingIntent
.setContentTitle("适配android 8限制后台定位功能") // 设置下拉列表里的标题
// .setSmallIcon(R.drawable.ic_launcher) // 设置状态栏内的小图标
.setContentText("正在后台定位") // 设置上下文内容
.setWhen(System.currentTimeMillis()); // 设置该通知发生的时间
if (Build.VERSION.SDK_INT >= Build.VERSION_CODES.JELLY_BEAN) {
notification = builder.build(); // 获取构建好的Notification
}
}
notification.defaults = Notification.DEFAULT_SOUND; //设置为默认的声音
//开发者应用如果有后台定位需求,在退到后台的时候,为了保证定位可以在后台一直运行, 可以调用该函数,
//会将定位SDK的SERVICE设置成为前台服务,适配ANDROID 8后台无法定位问题,其他版本下也会提高定位进程存活率
//id - 为通知栏notifation设置唯一id,必须大于0
//notification - 开发者自定义通知
mClient.enableLocInForeground(1001, notification);// 调起前台定位
mClient.disableLocInForeground(true







 本文介绍了如何在Android Studio中集成百度地图SDK,实现在后台持续定位以及步行导航功能。详细步骤包括导入SDK、配置信息、创建定位监听器和实现步行导航。提供关键代码示例,并指出注意事项。
本文介绍了如何在Android Studio中集成百度地图SDK,实现在后台持续定位以及步行导航功能。详细步骤包括导入SDK、配置信息、创建定位监听器和实现步行导航。提供关键代码示例,并指出注意事项。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 5398
5398

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








