1. Requirement Analysis
1.1 Requirement Analysis for Our Exchange Platform
Centralized and decentralized exchange platforms constitute two distinct types of digital
marketplaces that trade assets, including cryptocurrencies, stocks, and other securities. These
platforms diverge in operational structures, control mechanisms, and security features. The
primary distinctions between centralized and decentralized exchange platforms are outlined
below:
Control and Management:
Centralized exchanges (CEX) operate under the management
and control of a single organization or entity, which serves as an intermediary between buyers
and sellers. These exchanges safeguard users' funds, oversee orders, and ensure efficient
transaction execution. Conversely, decentralized exchanges (DEX) function on a distributed
ledger, typically a blockchain, and do not depend on a central authority for transaction
facilitation. Trades are executed directly between users through smart contracts or other peer
to-peer methods without intermediaries.
Custody of Funds:
In centralized exchanges, users deposit assets into the exchange's wallets,
effectively ceding control of their funds to the exchange and necessitating trust in the
platform. In decentralized exchanges, users maintain control over their assets and private
keys, trading directly from their wallets, eliminating the need to trust a centralized authority
with their funds.
Security:
Centralized exchanges are more susceptible to hacks, given their status as single
points of failure. A compromised centralized exchange can jeopardize users' funds and
sensitive information. In contrast, decentralized exchanges are more secure due to their
distributed nature. They do not store users' funds centrally, reducing the risk of theft and
hacks.
Regulatory Compliance:
Centralized exchanges are under regulatory oversight and must
adhere to regulations, such as Know Your Customer (KYC) and Anti-Money Laundering
(AML) requirements. Decentralized exchanges, lacking a central authority and operating on a
peer-to-peer basis, often function beyond regulatory oversight. This can increase anonymity
but carries risks associated with money laundering and other illicit activities.
In conclusion, centralized and decentralized exchanges exhibit notable differences in control,
fund custody, security, regulatory compliance, performance, liquidity, and user experience.
Each exchange type possesses its advantages and drawbacks, and users should carefully
weigh these factors when selecting the most appropriate platform for their trading
requirements.
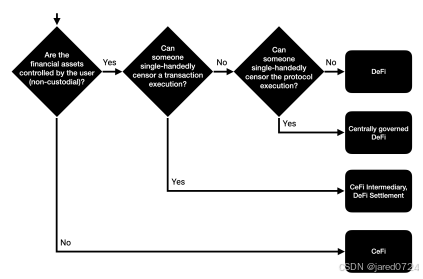
A centralized exchange platform constitutes a digital marketplace where users can purchase, sell,and trade various assets, including cryptocurrencies, stocks, commodities, and other securities. Centralized exchanges operate under a single organization's management as an intermediary between buyers and sellers. To develop a resilient and efficient centralized exchange platform, it is crucial to identify and examine the diverse functional and nonfunctional requirements.
1.2 Functional Requirements:
User Registration and Authentication:
The platform must employ a secure registration and
authentication process, ensuring only authorized users can access the platform and conduct
transactions.
Asset Management:
The platform must enable users to securely deposit, withdraw, and
manage their assets, accommodating various asset types such as cryptocurrencies, stocks, and
commodities.
Trading:
The platform must facilitate the buying, selling, and trading of assets, providing an
efficient order-matching engine to pair buy and sell orders and execute trades.
Order Types:
The platform must support diverse order types, including market orders, limit
orders, and stop orders, affording users flexibility and control over their trading strategies.
Non-functional Requirements:
Performance:
The platform must deliver rapid and responsive user interfaces, order
processing, and data retrieval to ensure a seamless trading experience.
Security:
The platform must adhere to industry-standard security practices, such as
encryption, multi-factor authentication, and routine security audits, to protect user data and
assets.
Usability:
The platform must feature an intuitive and user-friendly interface that caters to
users with diverse levels of experience and expertise.
Maintainability:
The platform must be easily maintainable and upgradable, featuring a
modular architecture, well-documented code, and automated testing procedures.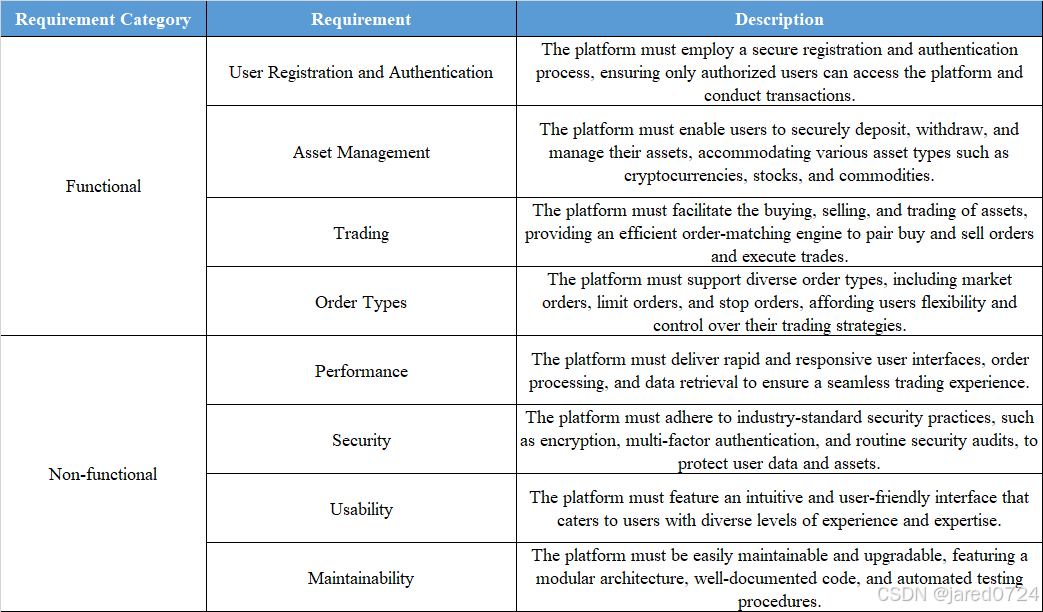

2. System Design and Implementation
2.1 Functional System Requirements
2.1.1 User Registration and Authentication
In this section, we present a comprehensive description of the design process for a login
system, detailing both frontend and backend components:
Frontend - Login Page:
a. HTML/CSS: Design the login page structure and aesthetics, incorporating input fields for
email/username and password and the "Log In" button.
b. JavaScript: Incorporate event listeners to manage user interactions, including form
submission and input validation.
c. Input validation: Establish frontend validation protocols, such as verifying field
completeness.
d. AJAX/JavaScript framework: Transmit the login data to the backend server via a POST
request targeting the designated API endpoint.
Backend - API Endpoint:
a. Web framework: Configure a route to process the login API request.
b. Input validation: Execute server-side validation of incoming data, including verification of
field completeness and email format correctness.
c. Data retrieval: Search the database for a user record corresponding to the provided
email/username.
d. Authentication: Assess the consistency between the received password and the stored
hashed password using an identical hashing algorithm.
i. If the password is consistent, proceed to the subsequent step.
ii. If the password is inconsistent, return an error response to the front.
e. Session/JWT: Generate a session or JWT containing relevant user information.
f. Response: Dispatch a successful response to the front end, incorporating the session/JWT
data.
Frontend - Authentication State:
a. Response handling: Examine the backend response to ascertain success or error presence.
b. Store session/JWT: If successful, securely store the acquired session/JWT data.
c. Redirect: Direct the user to the appropriate protected page or dashboard upon successful
login.
Frontend - Authenticated Requests:
a. Include session/JWT: For all subsequent requests to protected API endpoints, incorporate
the stored session/JWT data within the request headers.
b. Handle expired sessions: Should the backend return a response indicating session/JWT
expiration, prompt the user to re-login.
Backend - Authenticated Endpoints:
a. Middleware: Implement middleware to validate the session/JWT data in requests targeting
protected API endpoints.
b. Access control: Regulate access to specific resources based on the user's authentication
status and permissions.
The following is a flowchart of the completed process:
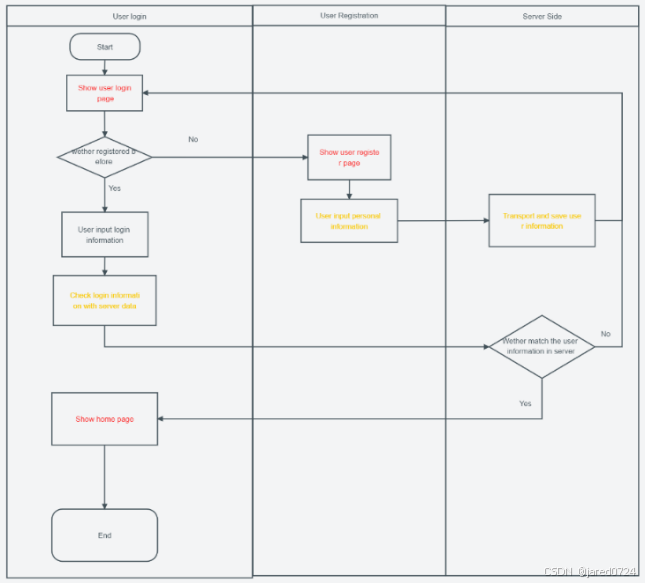
Users can access the platform by entering their unique username and password. First-time
users may also create a new account by selecting the 'register now' option. If users forget their
password, a password reset function is available. The entire login process has been designed
to be secure and efficient while providing password recovery options.
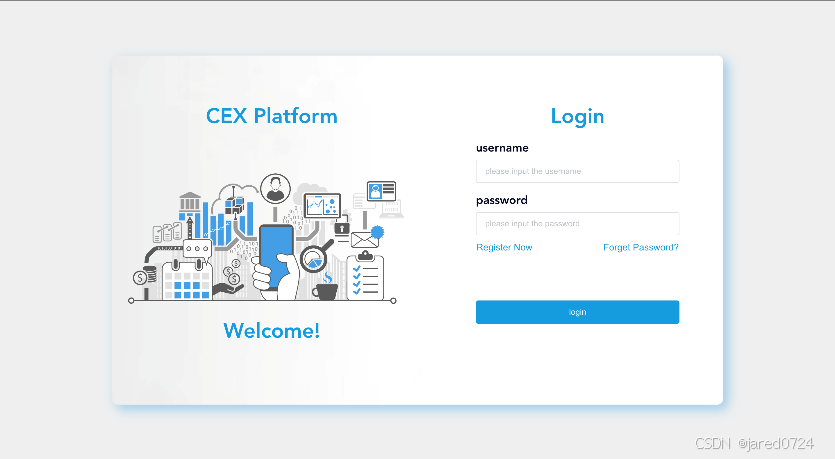
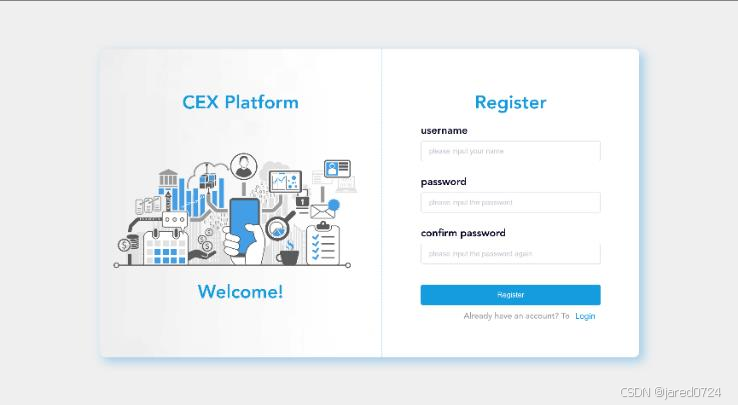
New users accessing the platform for the first time can register and create an account. They
can define a custom username and password, with the latter supporting a combination of
letters, numbers, and special symbols for enhanced security. To minimize issues arising from
input errors, users must enter their password twice during registration. This approach ensures
the utmost security for user accounts.
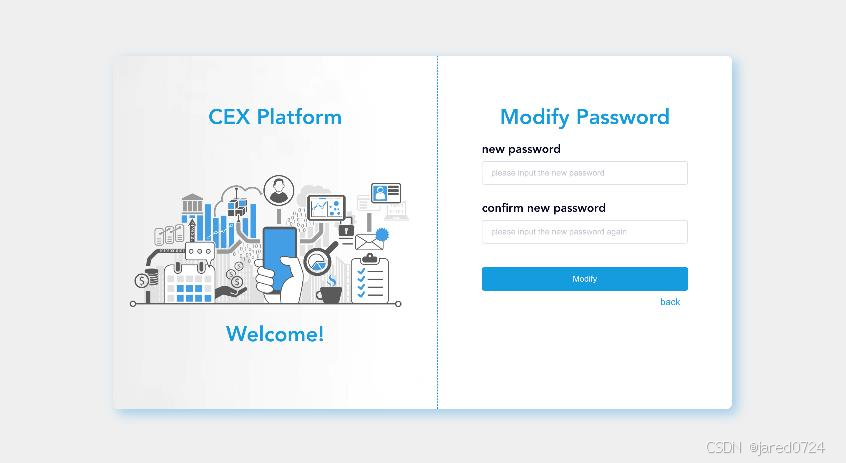
A password recovery portal is available if a user forgets their login password. Through this
portal, users can initiate a password reset process to create a new password for their account.
This feature contributes to the ongoing accessibility and security of the user's account.
2.1.2 Trade-Buy Cryptocurrency
This section presents a comprehensive system design for purchasing cryptocurrency,
encompassing frontend, backend, and external components.
Frontend - Buy Cryptocurrency Interface:
a. HTML/CSS: Construct a user-friendly interface incorporating input fields for
cryptocurrency selection, purchase amount specification, and current market price display.
b. JavaScript: Integrate event listeners to manage user interactions, such as choosing a
cryptocurrency and defining the purchase amount.
c. AJAX/JavaScript framework: Request the selected cryptocurrency's current market price
from the backend, updating the displayed price accordingly.
d. Form submission: Transmit the buy order data (cryptocurrency, amount, and price) to the
backend server via a POST request targeting the designated API endpoint.
Backend - API Endpoint:
a. Web framework: Configure a route to process the buy order API request.
b. Input validation: Execute server-side validation of incoming data, verifying field
completeness and numerical value validity.
c. Authentication: Confirm the user's authentication state using session or JWT data included
in the request.
d. User account balance: Determine if the user possesses adequate fund





 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 1170
1170










