摘要
本文深入探讨HIGRESS的安全防护机制,包括Web应用防火墙(WAF)、认证鉴权、访问控制、数据加密等核心安全特性。通过实际案例和最佳实践,展示如何构建安全可靠的API网关系统。
目录
1. 安全防护概述
1.1 安全架构
1.2 安全特性
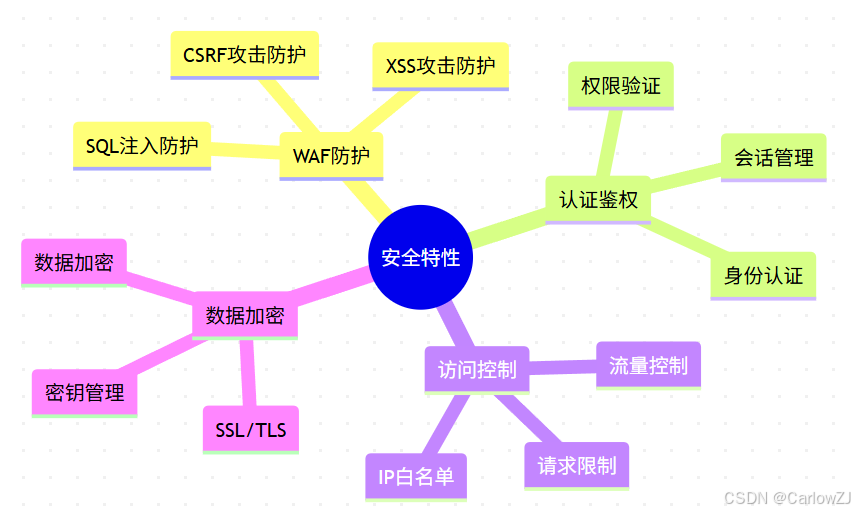
mindmap
root((安全特性))
WAF防护
SQL注入防护
XSS攻击防护
CSRF攻击防护
认证鉴权
身份认证
权限验证
会话管理
访问控制
IP白名单
请求限制
流量控制
数据加密
SSL/TLS
数据加密
密钥管理
2. WAF防护机制
2.1 WAF架构
2.2 WAF实现
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from typing import Dict, Any, List
import re
import json
from dataclasses import dataclass
import time
@dataclass
class WAFRule:
"""WAF规则"""
name: str
pattern: str
level: str
description: str
class WAFEngine:
"""WAF引擎"""
def __init__(self):
"""初始化WAF引擎"""
self.rules: List[WAFRule] = []
self.load_default_rules()
def load_default_rules(self):
"""加载默认规则"""
# SQL注入规则
self.rules.append(WAFRule(
name="sql_injection",
pattern=r"(?i)(\b(select|insert|update|delete|drop|union|exec)\b.*\b(from|into|where)\b)",
level="high",
description="SQL注入攻击"
))
# XSS攻击规则
self.rules.append(WAFRule(
name="xss_attack",
pattern=r"(?i)(<script.*?>.*?</script>|<.*?javascript:.*?>|<.*?\\s+on.*?=.*?>)",
level="high",
description="XSS攻击"
))
# CSRF攻击规则
self.rules.append(WAFRule(
name="csrf_attack",
pattern=r"(?i)(<img.*?src.*?=.*?>)",
level="medium",
description="CSRF攻击"
))
def check_request(self, request: Dict[str, Any]) -> List[Dict[str, Any]]:
"""
检查请求
Args:
request: 请求信息
Returns:
匹配的规则列表
"""
matches = []
# 检查URL
if 'url' in request:
for rule in self.rules:
if re.search(rule.pattern, request['url']):
matches.append({
'rule': rule.name,
'level': rule.level,
'description': rule.description,
'target': 'url',
'value': request['url']
})
# 检查请求头
if 'headers' in request:
for header, value in request['headers'].items():
for rule in self.rules:
if re.search(rule.pattern, value):
matches.append({
'rule': rule.name,
'level': rule.level,
'description': rule.description,
'target': f'header:{header}',
'value': value
})
# 检查请求体
if 'body' in request:
for rule in self.rules:
if re.search(rule.pattern, request['body']):
matches.append({
'rule': rule.name,
'level': rule.level,
'description': rule.description,
'target': 'body',
'value': request['body']
})
return matches
def should_block(self, matches: List[Dict[str, Any]]) -> bool:
"""
判断是否拦截
Args:
matches: 匹配的规则列表
Returns:
是否拦截
"""
# 如果存在高危规则匹配,则拦截
return any(match['level'] == 'high' for match in matches)
3. 认证鉴权机制
3.1 认证流程
3.2 认证实现
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from typing import Dict, Any, Optional, List
import jwt
import time
from dataclasses import dataclass
import hashlib
@dataclass
class User:
"""用户信息"""
id: str
username: str
roles: List[str]
permissions: List[str]
class AuthManager:
"""认证管理器"""
def __init__(self, secret_key: str):
"""
初始化认证管理器
Args:
secret_key: 密钥
"""
self.secret_key = secret_key
self.token_blacklist = set()
def generate_token(self, user: User) -> str:
"""
生成Token
Args:
user: 用户信息
Returns:
Token字符串
"""
payload = {
'user_id': user.id,
'username': user.username,
'roles': user.roles,
'permissions': user.permissions,
'exp': time.time() + 3600 # 1小时过期
}
return jwt.encode(payload, self.secret_key, algorithm='HS256')
def verify_token(self, token: str) -> Optional[Dict[str, Any]]:
"""
验证Token
Args:
token: Token字符串
Returns:
解码后的Token信息
"""
try:
# 检查Token是否在黑名单中
if token in self.token_blacklist:
return None
# 验证Token
payload = jwt.decode(token, self.secret_key, algorithms=['HS256'])
return payload
except jwt.InvalidTokenError:
return None
def blacklist_token(self, token: str):
"""
将Token加入黑名单
Args:
token: Token字符串
"""
self.token_blacklist.add(token)
def check_permission(self,
user: User,
required_permission: str) -> bool:
"""
检查权限
Args:
user: 用户信息
required_permission: 所需权限
Returns:
是否有权限
"""
return required_permission in user.permissions
4. 访问控制策略
4.1 访问控制架构
4.2 访问控制实现
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from typing import Dict, Any, Set
import time
from collections import defaultdict
import ipaddress
class AccessController:
"""访问控制器"""
def __init__(self):
"""初始化访问控制器"""
self.ip_whitelist: Set[str] = set()
self.ip_blacklist: Set[str] = set()
self.rate_limits: Dict[str, Dict[str, Any]] = defaultdict(
lambda: {
'qps': 100,
'concurrent': 10,
'requests': [],
'current_requests': 0
}
)
def add_ip_to_whitelist(self, ip: str):
"""
添加IP到白名单
Args:
ip: IP地址
"""
self.ip_whitelist.add(ip)
def add_ip_to_blacklist(self, ip: str):
"""
添加IP到黑名单
Args:
ip: IP地址
"""
self.ip_blacklist.add(ip)
def is_ip_allowed(self, ip: str) -> bool:
"""
检查IP是否允许访问
Args:
ip: IP地址
Returns:
是否允许访问
"""
# 检查黑名单
if ip in self.ip_blacklist:
return False
# 检查白名单
if self.ip_whitelist and ip not in self.ip_whitelist:
return False
return True
def check_rate_limit(self,
client_id: str,
current_time: float = None) -> bool:
"""
检查频率限制
Args:
client_id: 客户端ID
current_time: 当前时间
Returns:
是否允许访问
"""
if current_time is None:
current_time = time.time()
# 获取限制配置
limits = self.rate_limits[client_id]
# 清理过期请求
limits['requests'] = [
req_time for req_time in limits['requests']
if current_time - req_time < 1.0
]
# 检查QPS限制
if len(limits['requests']) >= limits['qps']:
return False
# 检查并发限制
if limits['current_requests'] >= limits['concurrent']:
return False
# 更新请求记录
limits['requests'].append(current_time)
limits['current_requests'] += 1
return True
def release_request(self, client_id: str):
"""
释放请求
Args:
client_id: 客户端ID
"""
if client_id in self.rate_limits:
self.rate_limits[client_id]['current_requests'] -= 1
5. 数据加密传输
5.1 加密架构
5.2 加密实现
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from typing import Dict, Any, Tuple
import base64
from cryptography.fernet import Fernet
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.primitives.kdf.pbkdf2 import PBKDF2HMAC
import os
class EncryptionManager:
"""加密管理器"""
def __init__(self, password: str):
"""
初始化加密管理器
Args:
password: 密码
"""
self.password = password.encode()
self.salt = os.urandom(16)
self.key = self._derive_key()
self.fernet = Fernet(self.key)
def _derive_key(self) -> bytes:
"""
派生密钥
Returns:
密钥
"""
kdf = PBKDF2HMAC(
algorithm=hashes.SHA256(),
length=32,
salt=self.salt,
iterations=100000
)
return base64.urlsafe_b64encode(kdf.derive(self.password))
def encrypt(self, data: str) -> str:
"""
加密数据
Args:
data: 原始数据
Returns:
加密后的数据
"""
return self.fernet.encrypt(data.encode()).decode()
def decrypt(self, encrypted_data: str) -> str:
"""
解密数据
Args:
encrypted_data: 加密数据
Returns:
解密后的数据
"""
return self.fernet.decrypt(encrypted_data.encode()).decode()
def generate_key_pair(self) -> Tuple[str, str]:
"""
生成密钥对
Returns:
(公钥, 私钥)
"""
from cryptography.hazmat.primitives.asymmetric import rsa
from cryptography.hazmat.primitives import serialization
# 生成私钥
private_key = rsa.generate_private_key(
public_exponent=65537,
key_size=2048
)
# 生成公钥
public_key = private_key.public_key()
# 序列化私钥
private_pem = private_key.private_bytes(
encoding=serialization.Encoding.PEM,
format=serialization.PrivateFormat.PKCS8,
encryption_algorithm=serialization.NoEncryption()
)
# 序列化公钥
public_pem = public_key.public_bytes(
encoding=serialization.Encoding.PEM,
format=serialization.PublicFormat.SubjectPublicKeyInfo
)
return public_pem.decode(), private_pem.decode()
6. 安全监控告警
6.1 监控架构
6.2 监控实现
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from typing import Dict, Any, List
import time
from dataclasses import dataclass
import smtplib
from email.mime.text import MIMEText
import requests
@dataclass
class SecurityEvent:
"""安全事件"""
event_type: str
level: str
source: str
message: str
timestamp: float
class SecurityMonitor:
"""安全监控器"""
def __init__(self,
alert_threshold: Dict[str, int],
notification_config: Dict[str, Any]):
"""
初始化监控器
Args:
alert_threshold: 告警阈值
notification_config: 通知配置
"""
self.alert_threshold = alert_threshold
self.notification_config = notification_config
self.events: List[SecurityEvent] = []
def record_event(self, event: SecurityEvent):
"""
记录事件
Args:
event: 安全事件
"""
self.events.append(event)
self._check_alert(event)
def _check_alert(self, event: SecurityEvent):
"""
检查是否需要告警
Args:
event: 安全事件
"""
# 检查事件数量是否超过阈值
event_count = sum(1 for e in self.events
if e.event_type == event.event_type
and time.time() - e.timestamp < 3600)
if event_count >= self.alert_threshold.get(event.event_type, 100):
self._send_alert(event)
def _send_alert(self, event: SecurityEvent):
"""
发送告警
Args:
event: 安全事件
"""
# 构建告警消息
message = f"""
安全告警
类型: {event.event_type}
级别: {event.level}
来源: {event.source}
消息: {event.message}
时间: {time.strftime('%Y-%m-%d %H:%M:%S', time.localtime(event.timestamp))}
"""
# 发送邮件告警
if 'email' in self.notification_config:
self._send_email_alert(message)
# 发送短信告警
if 'sms' in self.notification_config:
self._send_sms_alert(message)
def _send_email_alert(self, message: str):
"""
发送邮件告警
Args:
message: 告警消息
"""
email_config = self.notification_config['email']
msg = MIMEText(message)
msg['Subject'] = '安全告警通知'
msg['From'] = email_config['from']
msg['To'] = email_config['to']
with smtplib.SMTP(email_config['smtp_server'],
email_config['smtp_port']) as server:
server.starttls()
server.login(email_config['username'],
email_config['password'])
server.send_message(msg)
def _send_sms_alert(self, message: str):
"""
发送短信告警
Args:
message: 告警消息
"""
sms_config = self.notification_config['sms']
response = requests.post(
sms_config['api_url'],
json={
'phone': sms_config['phone'],
'message': message
},
headers={'Authorization': f"Bearer {sms_config['api_key']}"}
)
if response.status_code != 200:
print(f"发送短信告警失败: {response.text}")
7. 安全测试验证
7.1 测试计划
7.2 测试实现
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from typing import Dict, Any, List
import requests
import json
from dataclasses import dataclass
import time
@dataclass
class SecurityTest:
"""安全测试"""
name: str
description: str
target: str
method: str
payload: Dict[str, Any]
class SecurityTester:
"""安全测试器"""
def __init__(self):
"""初始化测试器"""
self.tests: List[SecurityTest] = []
self.results: List[Dict[str, Any]] = []
def add_test(self, test: SecurityTest):
"""
添加测试
Args:
test: 安全测试
"""
self.tests.append(test)
def run_tests(self):
"""运行测试"""
for test in self.tests:
result = self._run_test(test)
self.results.append(result)
def _run_test(self, test: SecurityTest) -> Dict[str, Any]:
"""
运行单个测试
Args:
test: 安全测试
Returns:
测试结果
"""
start_time = time.time()
try:
# 发送请求
response = requests.request(
method=test.method,
url=test.target,
json=test.payload
)
# 分析响应
is_vulnerable = self._analyze_response(response)
return {
'test': test.name,
'description': test.description,
'target': test.target,
'method': test.method,
'payload': test.payload,
'response': {
'status_code': response.status_code,
'headers': dict(response.headers),
'body': response.text
},
'is_vulnerable': is_vulnerable,
'duration': time.time() - start_time
}
except Exception as e:
return {
'test': test.name,
'description': test.description,
'target': test.target,
'method': test.method,
'payload': test.payload,
'error': str(e),
'is_vulnerable': False,
'duration': time.time() - start_time
}
def _analyze_response(self, response: requests.Response) -> bool:
"""
分析响应
Args:
response: 响应对象
Returns:
是否存在漏洞
"""
# 检查状态码
if response.status_code >= 500:
return True
# 检查响应头
if 'X-Powered-By' in response.headers:
return True
# 检查响应体
if 'error' in response.text.lower():
return True
return False
def generate_report(self) -> str:
"""
生成报告
Returns:
报告内容
"""
report = []
report.append("# 安全测试报告")
report.append(f"测试时间: {time.strftime('%Y-%m-%d %H:%M:%S')}")
report.append(f"测试数量: {len(self.tests)}")
report.append(f"发现漏洞: {sum(1 for r in self.results if r['is_vulnerable'])}")
report.append("\n## 测试详情")
for result in self.results:
report.append(f"\n### {result['test']}")
report.append(f"描述: {result['description']}")
report.append(f"目标: {result['target']}")
report.append(f"方法: {result['method']}")
report.append(f"负载: {json.dumps(result['payload'], indent=2)}")
report.append(f"是否漏洞: {'是' if result['is_vulnerable'] else '否'}")
report.append(f"耗时: {result['duration']:.2f}秒")
if 'error' in result:
report.append(f"错误: {result['error']}")
else:
report.append("响应:")
report.append(f"状态码: {result['response']['status_code']}")
report.append("响应头:")
for key, value in result['response']['headers'].items():
report.append(f" {key}: {value}")
report.append("响应体:")
report.append(f" {result['response']['body']}")
return "\n".join(report)
8. 最佳实践
8.1 安全建议
-
WAF防护
- 定期更新规则
- 监控攻击日志
- 及时处理告警
-
认证鉴权
- 使用强密码
- 定期更换密钥
- 实现多因素认证
-
访问控制
- 最小权限原则
- 定期审计权限
- 及时清理无效权限
-
数据加密
- 使用HTTPS
- 加密敏感数据
- 安全存储密钥
8.2 注意事项
-
安全配置
- 关闭调试模式
- 隐藏错误信息
- 限制管理接口
-
监控告警
- 设置合理阈值
- 及时处理告警
- 定期分析日志
-
应急响应
- 制定应急预案
- 定期演练
- 及时修复漏洞
9. 总结与展望
9.1 关键点总结
- 掌握安全防护方法
- 理解认证鉴权机制
- 学会安全测试
- 遵循最佳实践
9.2 后续建议
- 深入学习安全防护
- 了解最新安全威胁
- 掌握安全测试方法
- 实践项目应用
参考资料
扩展阅读
- 《Web安全测试》
- 《应用安全开发实践》
- 《安全架构设计》


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










