动态VPN:
连接下面的拓扑图:
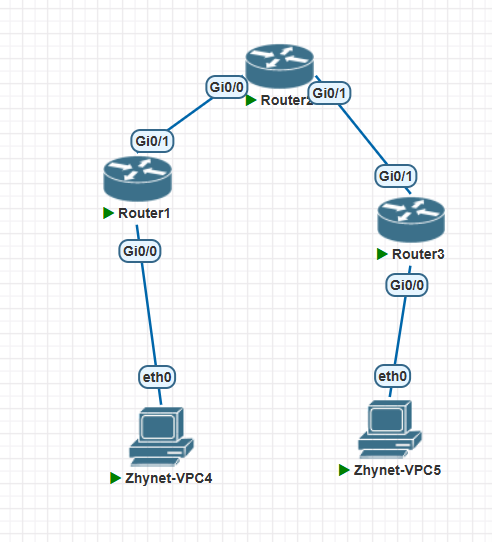
配置如之前的加密传输一样左下pc:10.1.20.254/24/ ~.1,右侧:10.1.36.254/24/~.1
R1和R3的g0/1口分别为192.168.1/2.2 /30
配置如下:
RT1
en
conf t
int g0/1
no sh
ip address 192.168.1.2 255.255.255.0
int g0/0
no sh
ip address 10.1.20.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 192.168.1.1
crypto isakmp enable
crypto isakmp policy 10
hash md5
authentication pre-share
encryption 3des
group 2
exit
crypto isakmp key cisco address 0.0.0.0
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode tunnel
exit
crypto dynamic-map ruijie 10
set transform-set cisco
exit
crypto map cisco 10 ipsec-isakmp dynamic ruijie
int g0/1
crypto map cisco
RT3
en
conf t
int g0/1
no sh
ip address 192.168.2.2 255.255.255.0
int g0/0
no sh
ip address 10.1.36.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 192.168.2.1
crypto isakmp enable
crypto isakmp policy 10
hash md5
authentication pre-share
encryption 3des
group 2
exit
crypto isakmp key cisco address 192.168.1.2
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode tunnel
exit
crypto map cisco 10 ipsec-isakmp
set peer 192.168.1.2
set transform-set cisco
match address 101
exit
access-list 101 permit ip 10.1.36.0 0.0.0.255 10.1.20.0 0.0.0.255
int g0/1
crypto map cisco
exit
RT2
en
conf t
int g0/0
no sh
ip address 192.168.1.1 255.255.255.0
int g0/1
no sh
ip address 192.168.2.1 255.255.255.0
然后用右侧pcping左侧,因为左边是静态配置。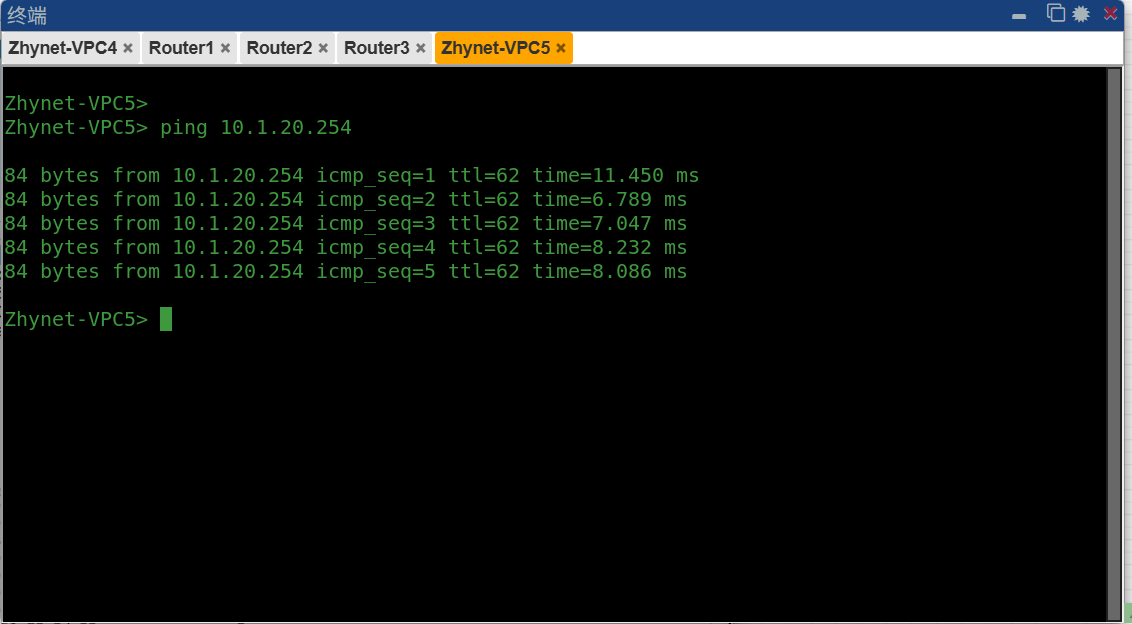
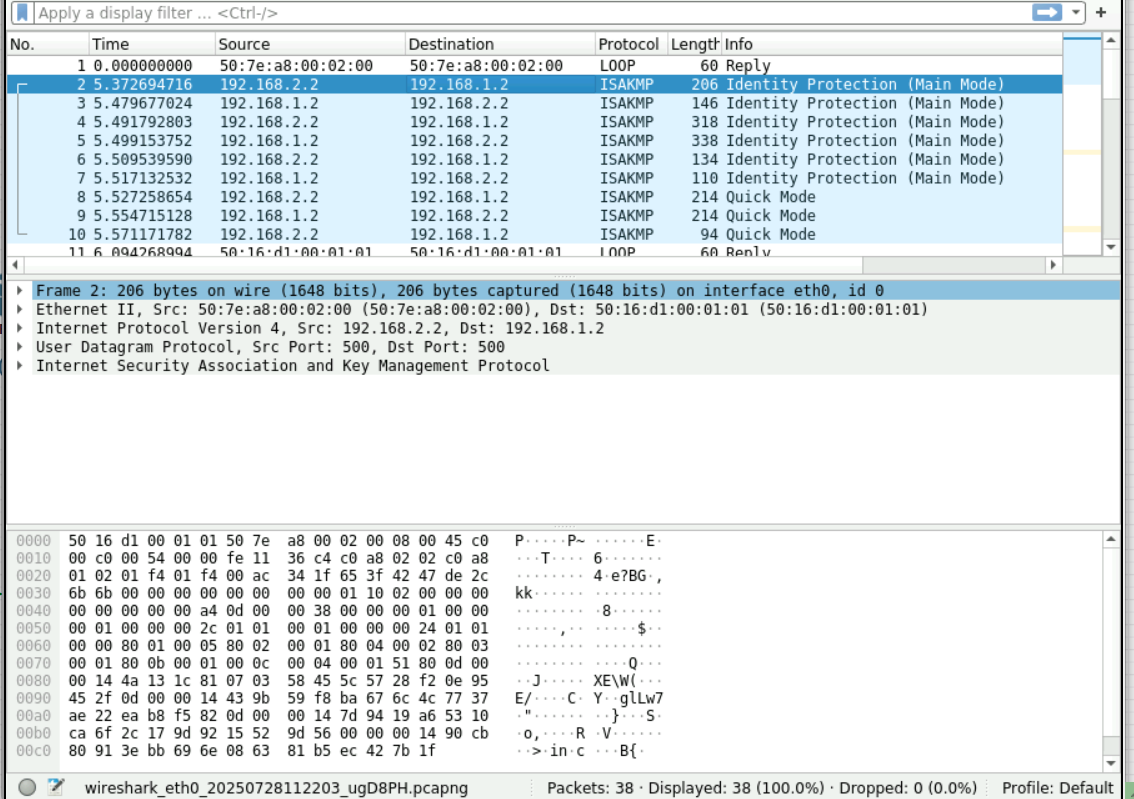
根据今天的上课所学,分析:
1:先是什么协议(udp/tcp),然后是源和目的以及传输采用的500的编号口,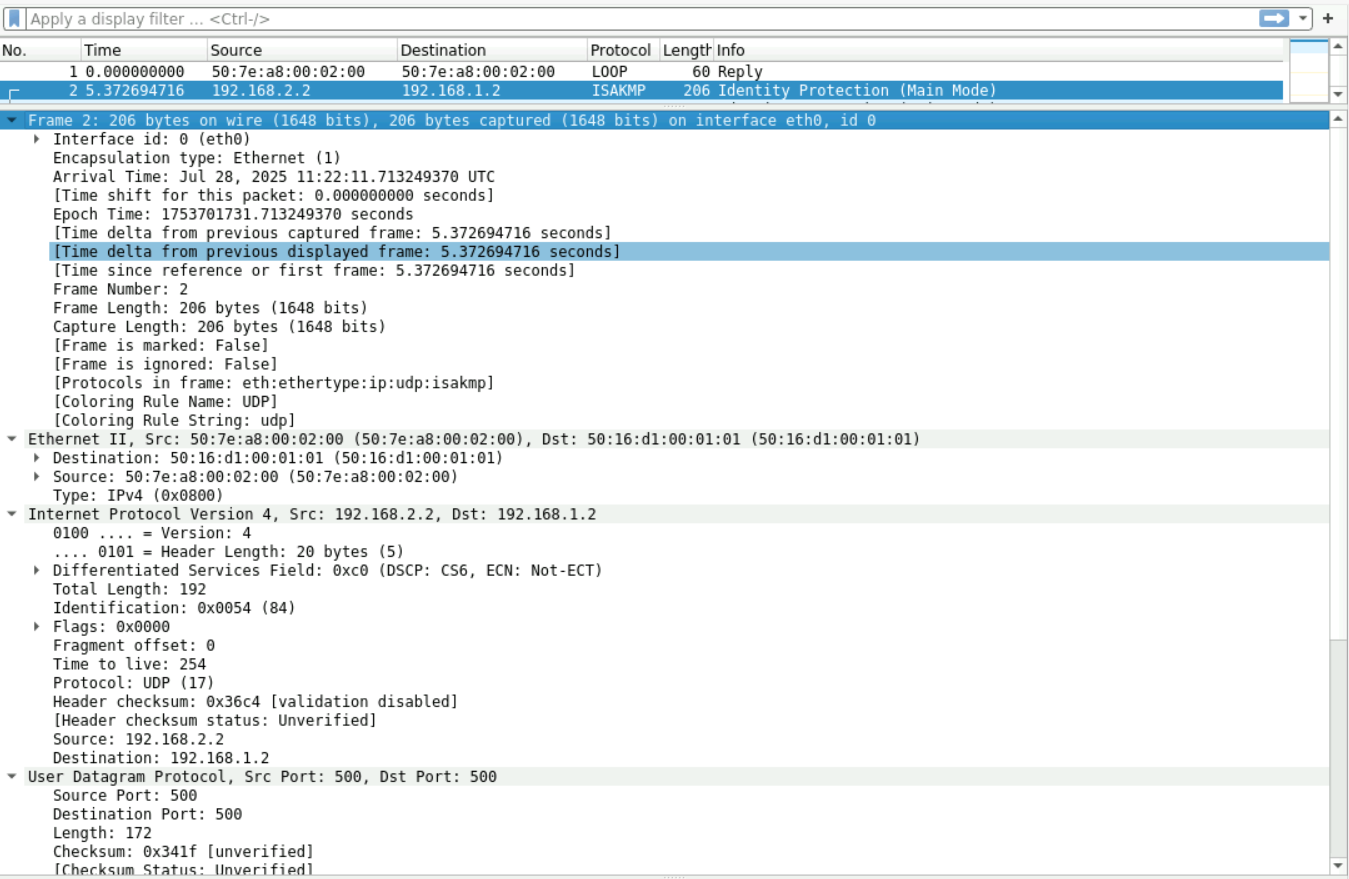
看下面的发起和响应者只有发起的序号,然后下面是基本参数如版本号,传输方式,SA载荷等
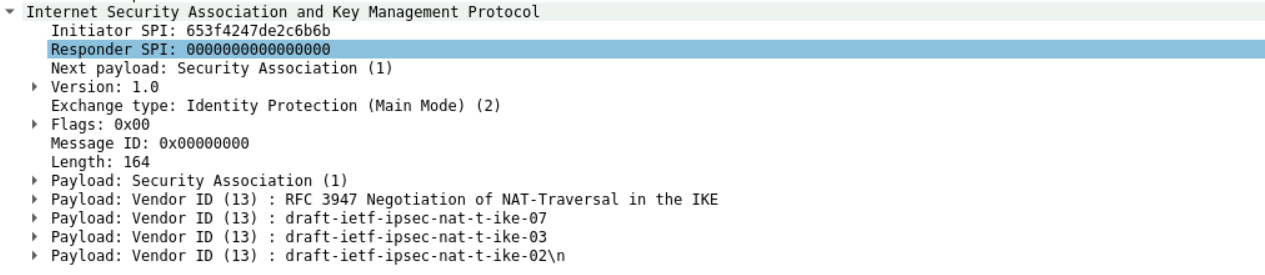
2:看图可知发起和响应互换,交流确定了isakmp的基本参数
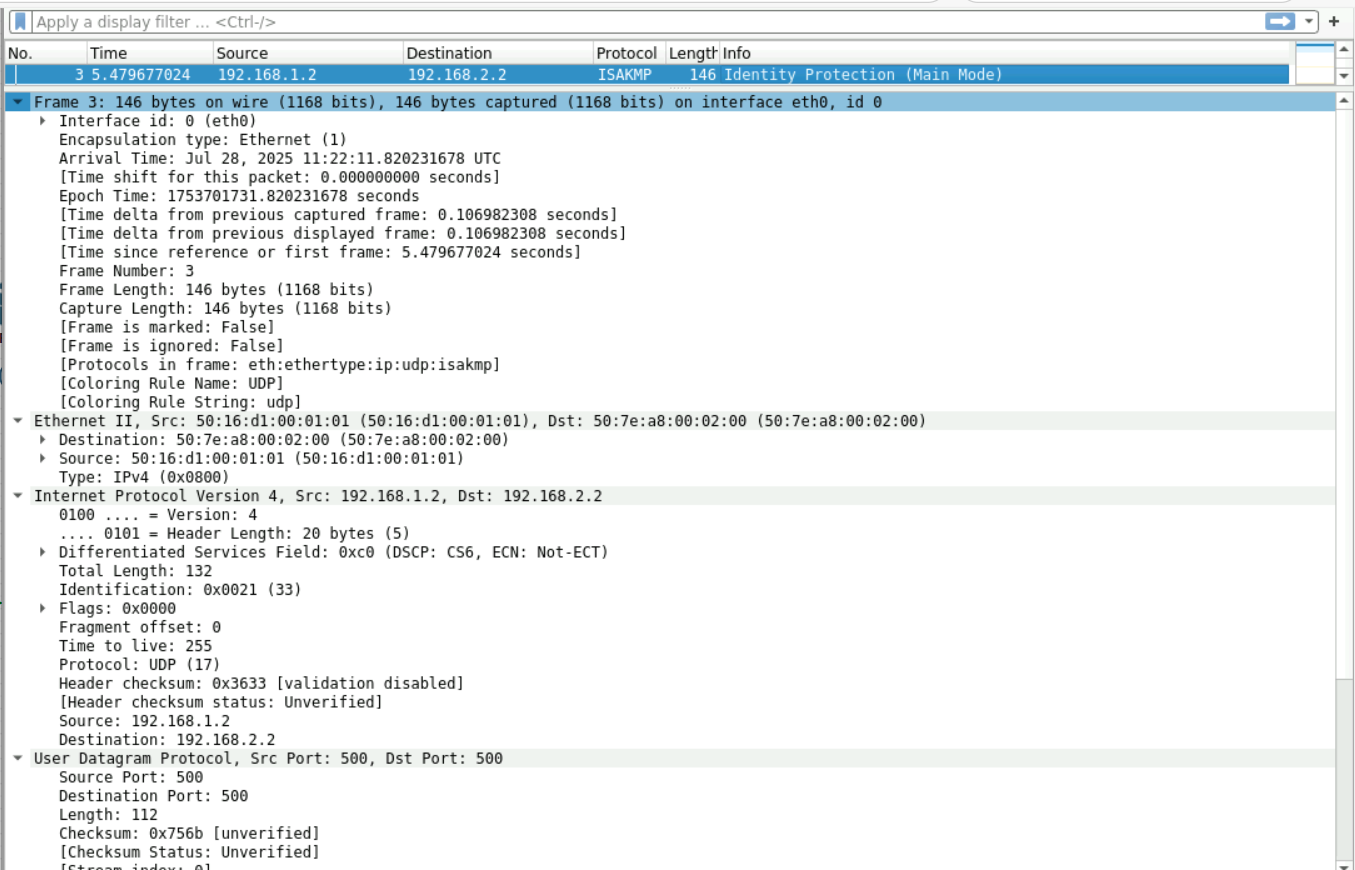
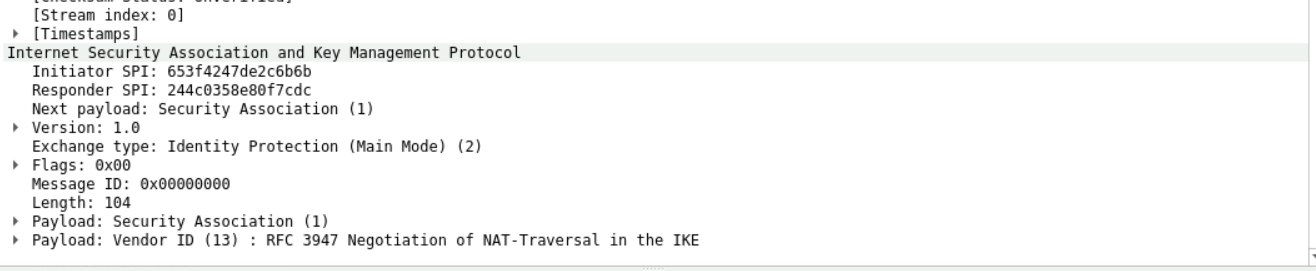
3:采用DH算法然后交换密钥
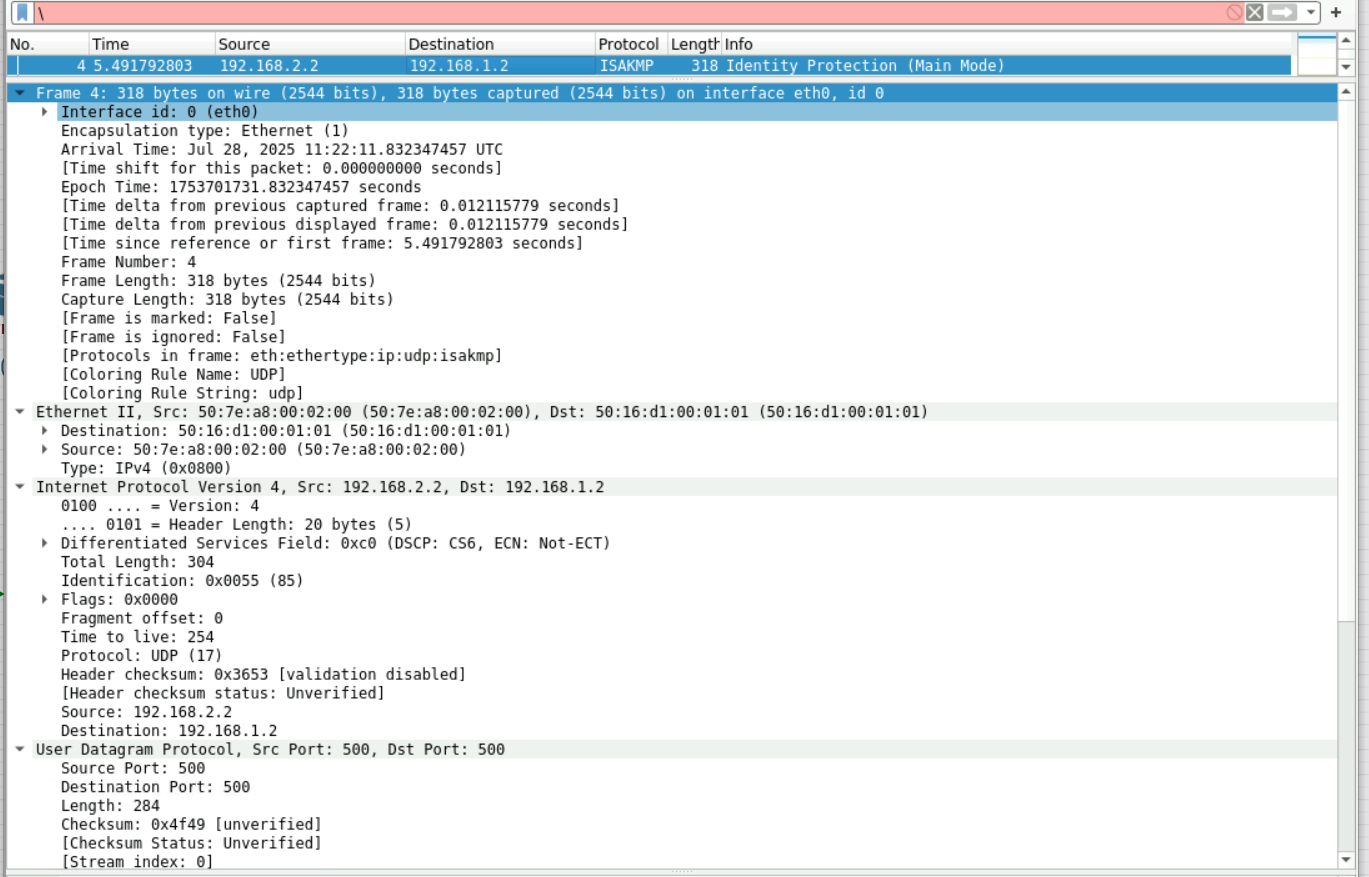
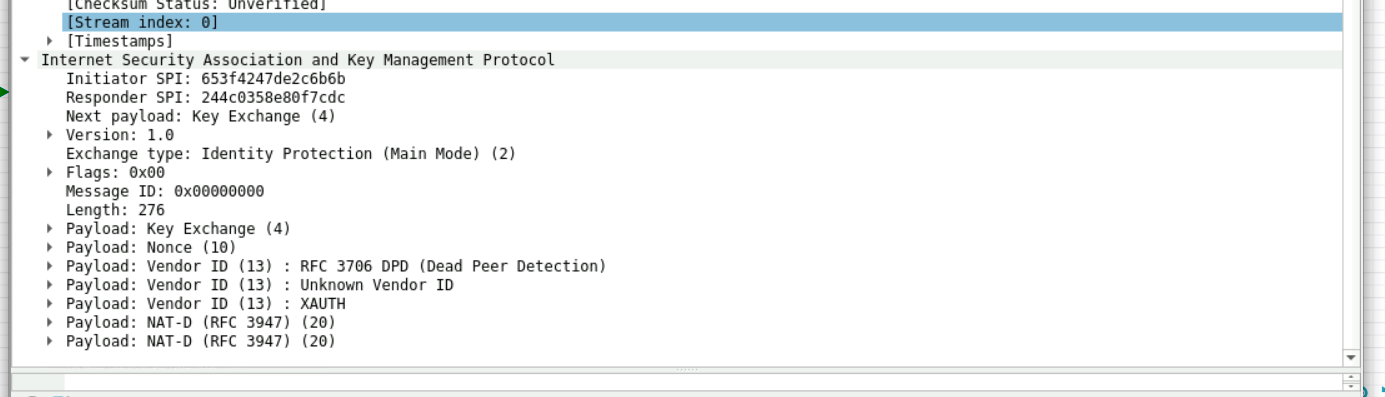
4.同3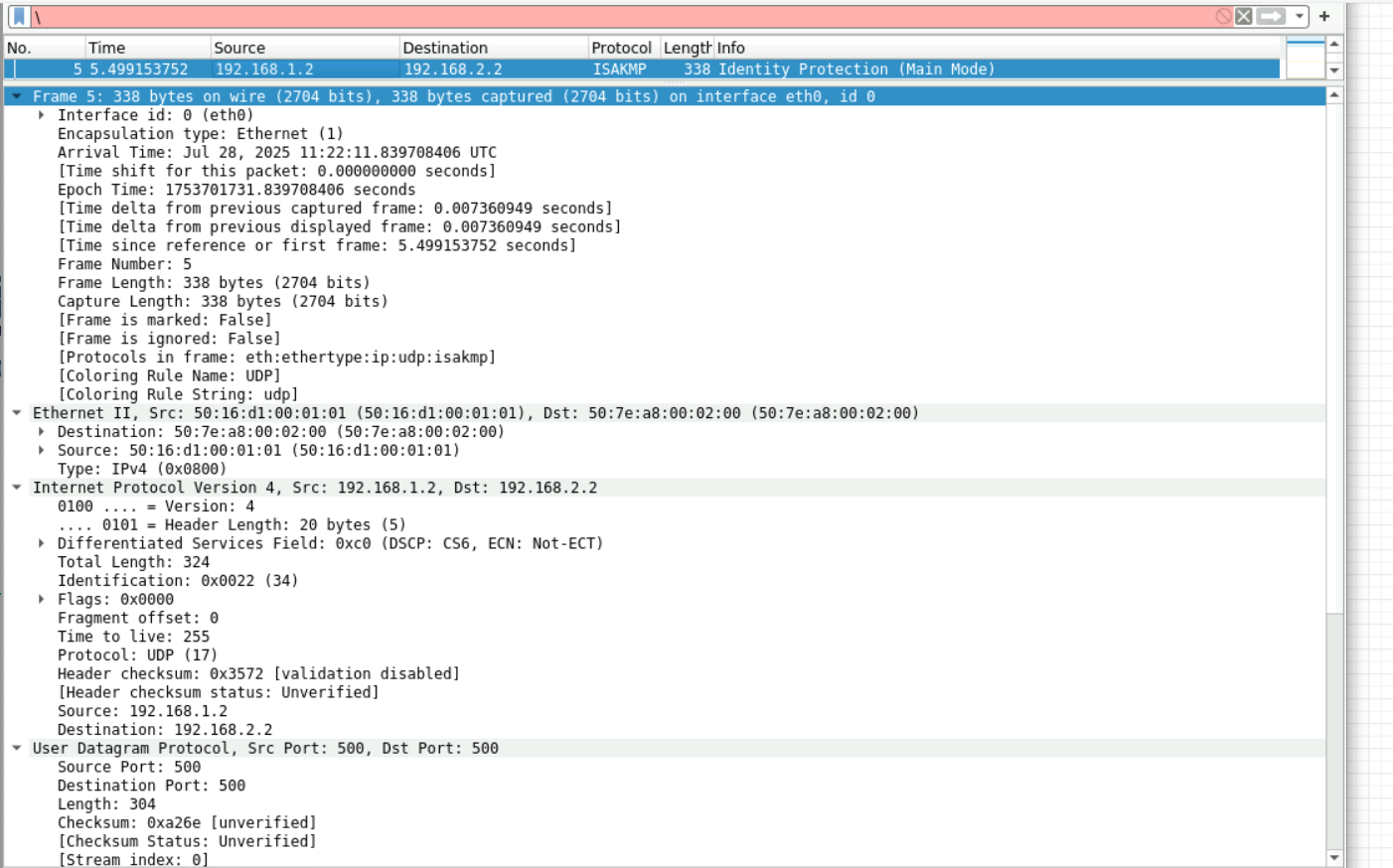
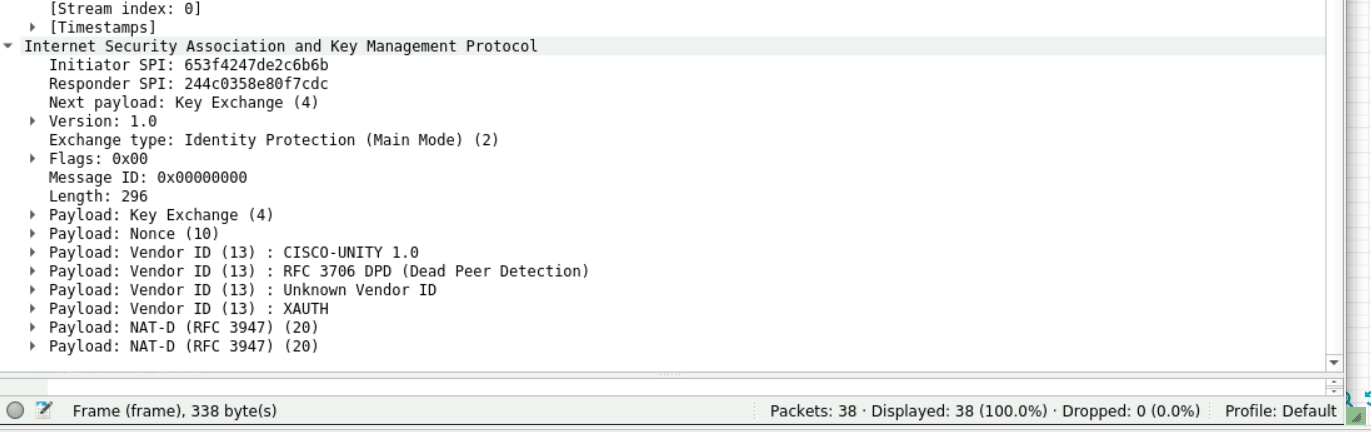
5:通过算法如HASH、DH,确认完整性,验证身份信息(都采用明文传输)
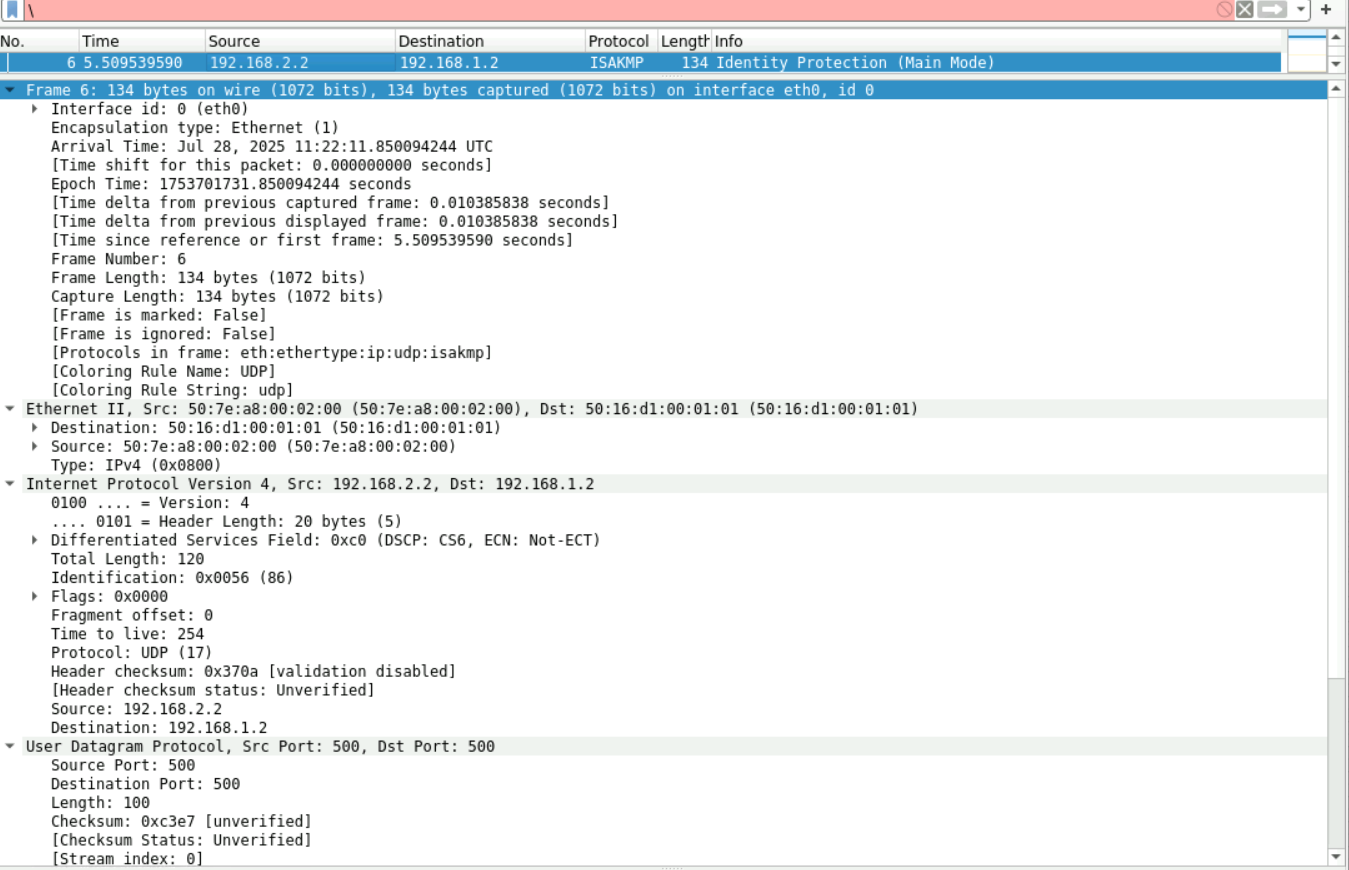
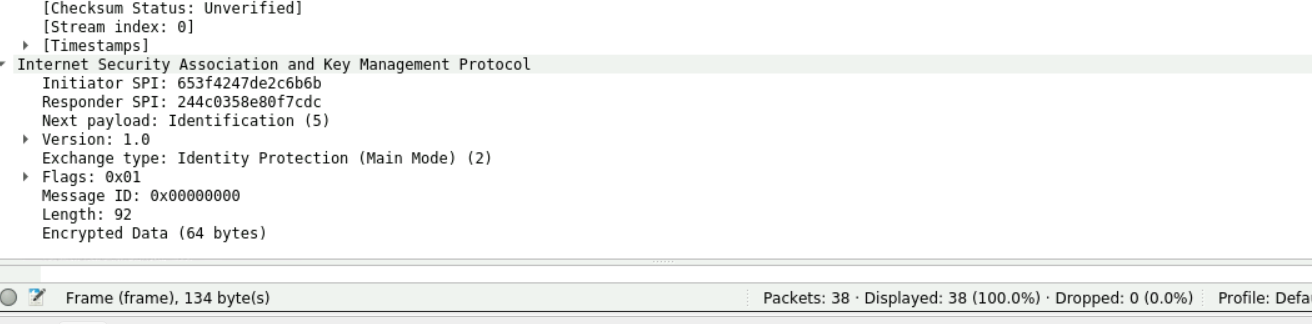
6:同上5: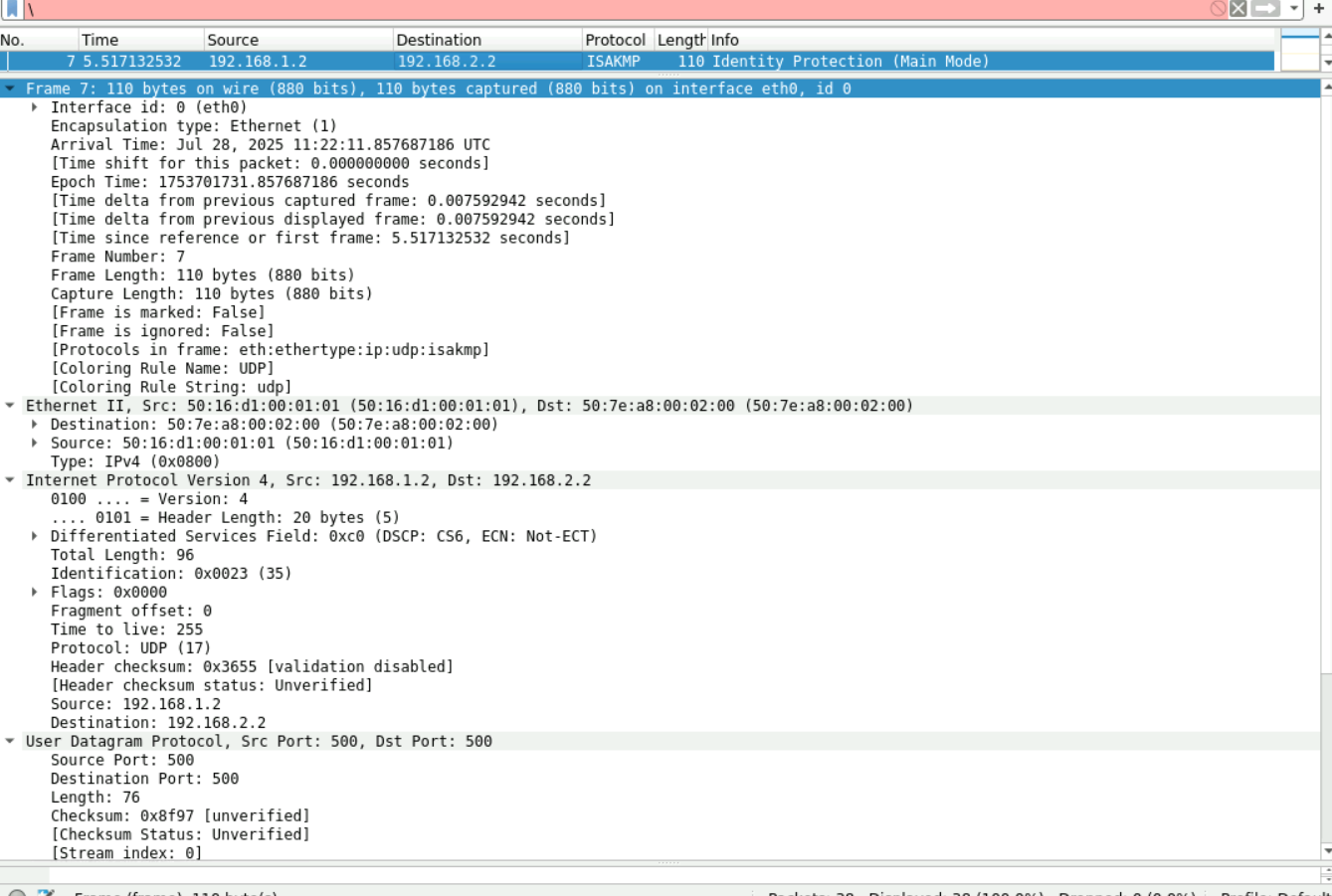
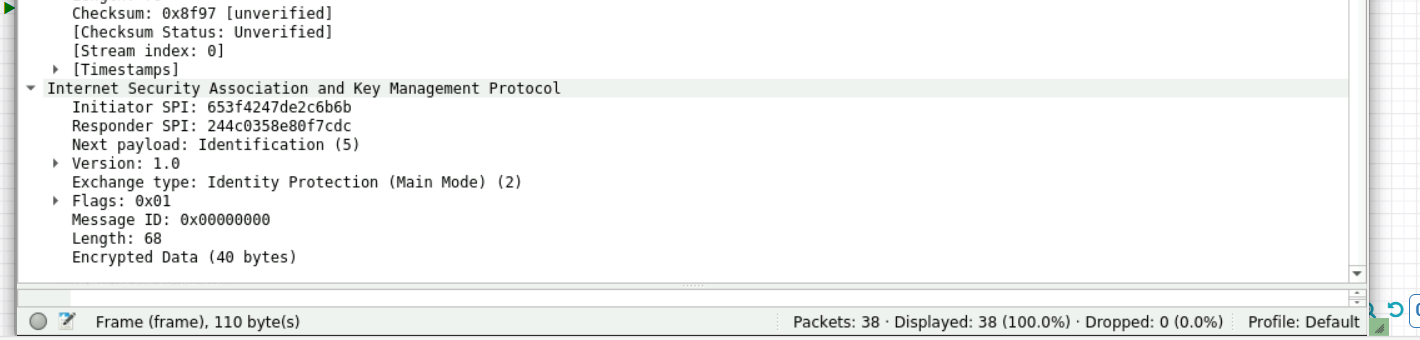
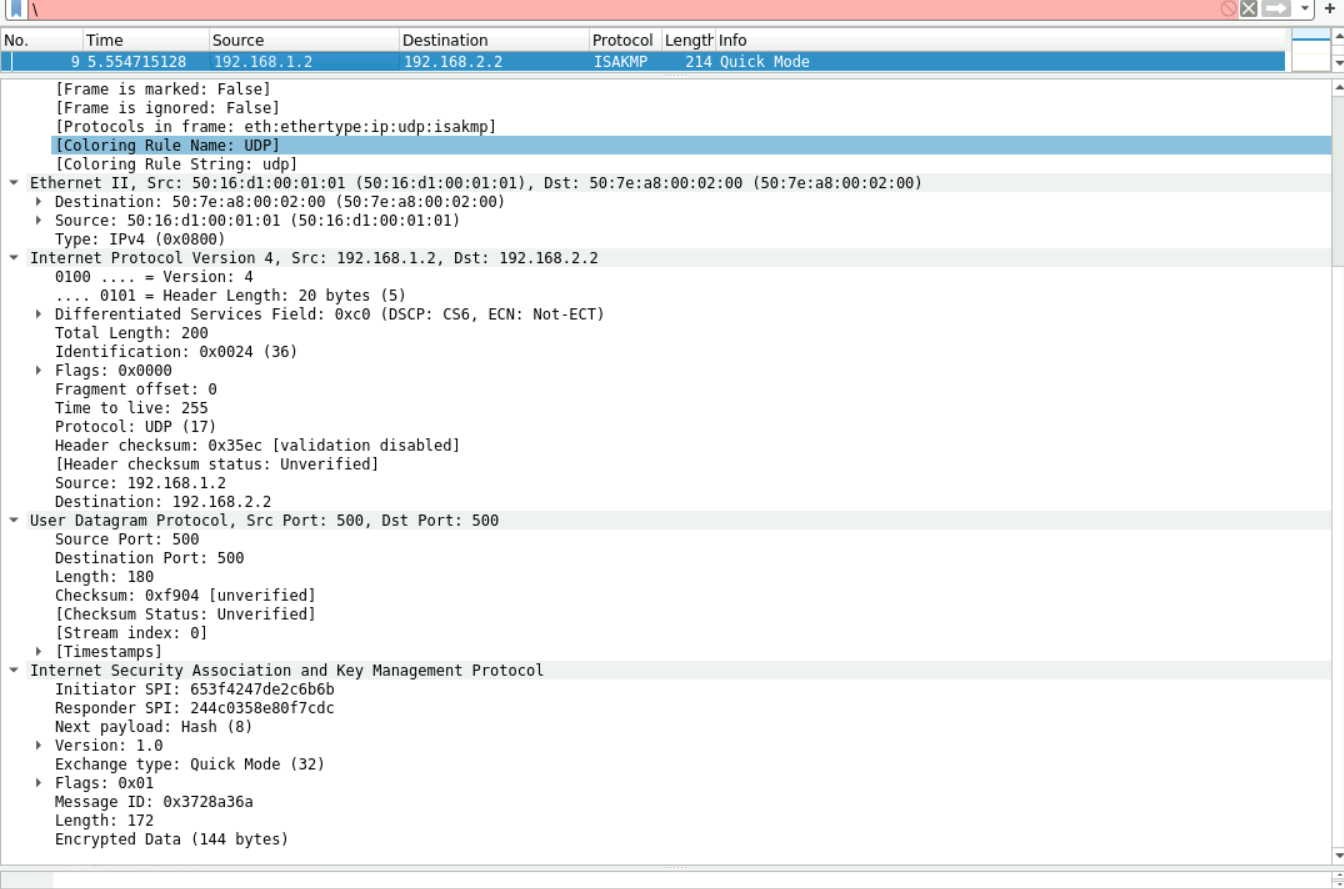
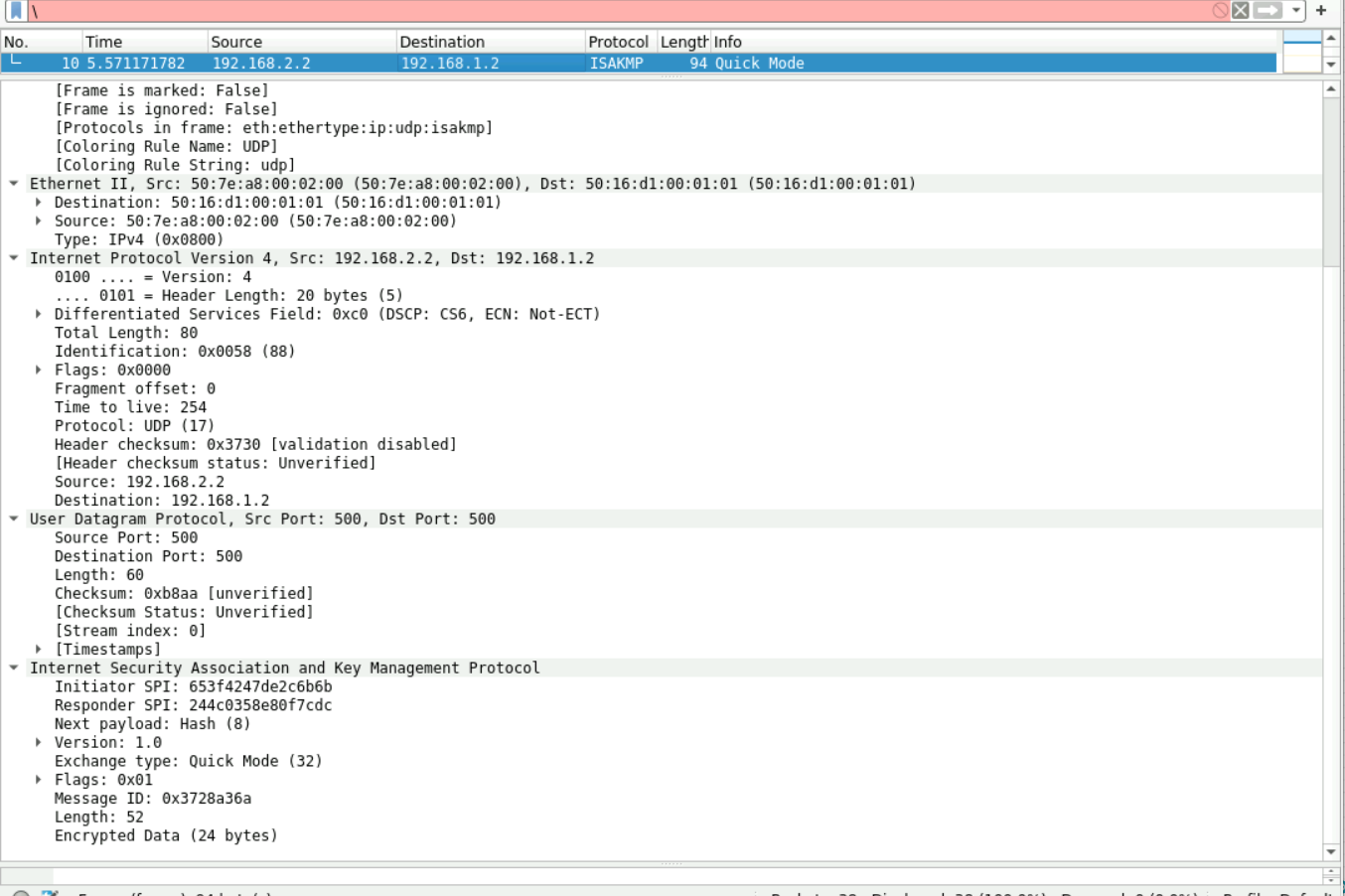
第七个报文开始加密:上面有部分被截去了就看下面部分的报文,由于为深入了解下三个报文只能抓包看看不分析:
7.
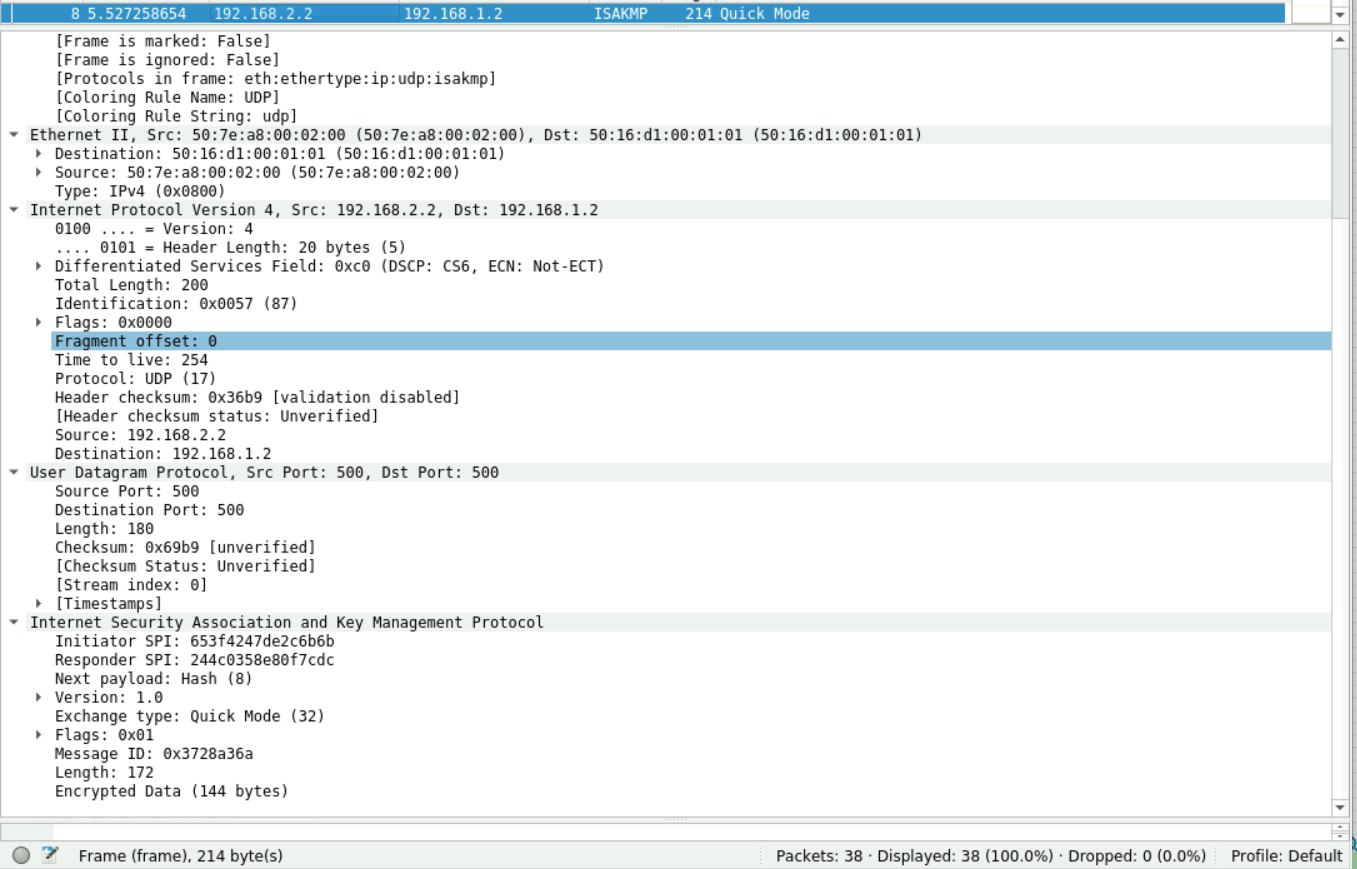
8.
9.




















 2062
2062

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








