安装中用到的软件
一、集群规划
1.1 集群主机规划
主机名 CPU 内存 IP 作用
node30 8 4G 10.10.10.30 master01/etcd01
node31 8 4G 10.10.10.31 master01/etcd02
node32 8 4G 10.10.10.32 master01/etcd03
node20 8 4G 10.10.10.20 monion01
node21 8 4G 10.10.10.21 monion02
node22 8 2G 10.10.10.22 ha01
node23 8 2G 10.10.10.23 ha02
10.10.10.100(vip)
操作系统: Centos7.7
软件版本:
kubernetes v1.25.5
containerd v1.6.13
etcd v3.5.6
Cfssl v1.6.31.2 集群架构图
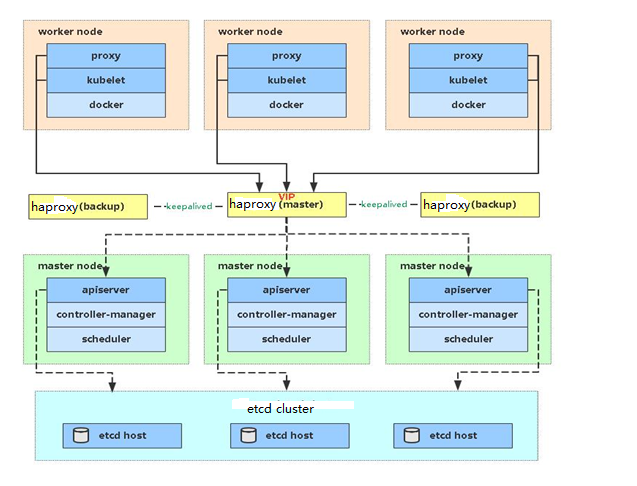
二、基础环境配置
2.1 所有环境配置hosts
echo '10.10.10.30 node30' >> /etc/hosts
echo '10.10.10.31 node31' >> /etc/hosts
echo '10.10.10.32 node32' >> /etc/hosts
echo '10.10.10.20 node20' >> /etc/hosts
echo '10.10.10.21 node21' >> /etc/hosts
echo '10.10.10.22 node22' >> /etc/hosts
echo '10.10.10.23 node23' >> /etc/hosts2.2 所有节点关闭防火墙,selinux,swap
#关闭防火墙
systemctl stop firewalld && systemctl disable firewalld
#关闭selinux
sed-ri's/(^SELINUX=).*/\1disabled/' /etc/selinux/config
setenforce 0
#关闭swap分区
sed-ri's@(^.*swap *swap.*0 0$)@#\1@' /etc/fstab
swapoff -a进一步了解一下,为什么 swap 打开对 kubelet 来说会是一个需要直接退出进程的错误呢??
一开始大家在讨论的是,如果容许 Pod 使用 Swap,应该怎么去衡量默认的 Swap 设置,以及调度器应该如何根据 Swap 来进行调度?
讨论了一段时间后,发现支持 Swap 很复杂。。。总之就是很复杂。一位大佬站出来说,真的有需要用到 Swap 的场景么?
然后大家就开始批判起 Swap 来了,Swap 带来各种性能上的不确定性啦,而且也找不到哪些场景一定要用 Swap 啦,经过大家高兴地一致决定,Swap 这个东西真的是有害而无利,而且要用起来还复杂,就是不用它好了(K8S 1.5版本)。
然后如果有人想用?一开始还是支持通过参数配置使用的,后来发现一个不推荐的用法,有人非得用,代码上各种坑,还不如大家一起坚决不用好了。
然后到了1.8后就是默认不用了,除非你强制打开,官方强烈不推荐,踩坑自己负责。
看 Issue 主要是觉得这个过程实在是一个很典型的,功能要不要的讨论,说来说去,没有明确的用户场景,就不要把一个事情搞复杂的哲学很重要。
更新--fail-swap-on flag含义
这个flag表示为:Makes the Kubelet fail to start if swap is enabled on the node.
也就是说如果为true(默认值)就要求必须要关闭swap,false是表示即使宿主开启了swap,kubelet也是可以成功启动,但是pod是允许使用swap了,这部分代码因为经常出问题,所以直接swap在宿主上禁用会比较好。
2.3 所有时间同步
虚拟机使用VMware同步时间。
外网使用ntp
#使用chrony
#安装chrony
yum install chrony -y
#在其中一台主机配置为时间服务器
cat /etc/chrony.conf
server time2.aliyun.com iburst #从哪同步时间
driftfile /var/lib/chrony/drift
makestep 1.0 3
rtcsync
allow 10.10.10.0/16 #允许的ntp客户端网段
local stratum 10
logdir /var/log/chrony
#重启服务
systemctl restart chronyd
#配置其他节点从服务端获取时间进行同步
cat /etc/chrony.conf
server 10.10.10.121 iburst
#重启验证
systemctl restart chronyd
chronyc sources -v
^* master01 3 6 17 5 -10us[ -109us] +/- 28ms #这样表示正常2.4 使用node30节点做免秘钥
ssh-keygen
ssh-copy-id-i.ssh/id_rsa.pubnode30
ssh-copy-id-i.ssh/id_rsa.pubnode31
ssh-copy-id-i.ssh/id_rsa.pubnode32
ssh-copy-id-i.ssh/id_rsa.pubnode20
ssh-copy-id-i.ssh/id_rsa.pubnode21
ssh-copy-id-i.ssh/id_rsa.pubnode22
ssh-copy-id-i.ssh/id_rsa.pubnode23三、生成集群相关证书
3.1 安装cfssl工具
mv cfssl_1.6.3_linux_amd64 cfssl
mv cfssljson_1.6.2_linux_amd64 cfssljson
mv cfssl-certinfo_1.6.2_linux_amd64 cfssl-certinfo
chmod+x cfssl* && mv cfssl* /usr/local/bin/3.2 分发kubernetes二进制文件
#分发master组件
master="node30 node31 node32"
for i in$master;do
scp kubernetes/server/bin/{kube-apiserver,kube-controller-manager,kube-scheduler,kube-proxy,kubelet,kubectl} $i:/usr/local/bin
done
#分发node组件
node="node20 node21"
for i in$node;do
scp kubernetes/server/bin/{kube-proxy,kubelet} $i:/usr/local/bin
done
#设置kubelet的tab补齐功能
source <(kubectl completion bash)
echo"source <(kubectl completion bash)" >> ~/.bashrc3.3 创建etcd集群证书
#创建目录
mkdir /opt/pki/etcd/ -p
cd /opt/pki/etcd/
#创建etcd的ca证书
mkdir ca && cd ca
#生成配置文件
cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"etcd": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
EOF
#生成申请文件
cat > ca-csr.json <<EOF
{
"CA":{"expiry":"87600h"},
"CN": "etcd-cluster",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"TS": "Beijing",
"L": "Beijing",
"O": "etcd-cluster",
"OU": "System"
}
]
}
EOF
#生成ca证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca
#会生成ca.pem和ca-key.pem文件
#etcd服务端
#生成etcd证书申请文件
#注意:文件hosts字段中IP为所有etcd节点的集群内部通信IP,一个都不能少!为了方便后期扩容可以多写几个预留的IP。
cd /opt/pki/etcd/
cat > etcd-server-csr.json << EOF
{
"CN": "etcd-server",
"hosts": [
"10.10.10.30",
"10.10.10.31",
"10.10.10.32",
"127.0.0.1"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"TS": "Beijing",
"L": "Beijing",
"O": "etcd-server",
"OU": "System"
}
]
}
EOF
#生成证书
cfssl gencert \
-ca=ca/ca.pem \
-ca-key=ca/ca-key.pem \
-config=ca/ca-config.json \
-profile=etcd \
etcd-server-csr.json | cfssljson -bare etcd-server
#etcd客户端
#生成etcd证书申请文件
cd /opt/pki/etcd/
cat > etcd-client-csr.json << EOF
{
"CN": "etcd-client",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"TS": "Beijing",
"L": "Beijing",
"O": "etcd-client",
"OU": "System"
}
]
}
EOF
#生成证书
cfssl gencert \
-ca=ca/ca.pem \
-ca-key=ca/ca-key.pem \
-config=ca/ca-config.json \
-profile=etcd \
etcd-client-csr.json | cfssljson -bare etcd-client
#验证
pwd
/opt/pki/etcd
#tree命令验证生成的文件
tree
.
├── ca
│ ├── ca-config.json
│ ├── ca.csr
│ ├── ca-csr.json
│ ├── ca-key.pem
│ └── ca.pem
├── etcd-client.csr
├── etcd-client-csr.json
├── etcd-client-key.pem #客户端私钥
├── etcd-client.pem #客户端公钥
├── etcd-server.csr
├── etcd-server-csr.json
├── etcd-server-key.pem #服务端私钥
└── etcd-server.pem #服务端公钥
#拷贝到master节点或etcd节点
master_etcd="node30 node31 node32"
for i in$master_etcd;do
ssh$i"mkdir /etc/etcd/ssl -p"
scp /opt/pki/etcd/ca/ca.pem /opt/pki/etcd/{etcd-server.pem,etcd-server-key.pem,etcd-client.pem,etcd-client-key.pem} $i:/etc/etcd/ssl/
done3.4 创建kubernetes集群各组件证书
3.4.1 生成kubernetes ca证书
#创建目录
mkdir-p /opt/pki/kubernetes/
cd /opt/pki/kubernetes/
mkdir ca && cd ca
#创建ca配置文件与申请文件
cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
EOF
#生成申请文件
cat > ca-csr.json <<EOF
{
"CA":{"expiry":"87600h"},
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"TS": "Beijing",
"L": "Beijing",
"O": "kubernetes",
"OU": "System"
}
]
}
EOF
#生成ca证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca 3.4.2 生成kube-apiserver证书
#创建目录
mkdir-p /opt/pki/kubernetes/kube-apiserver
cd /opt/pki/kubernetes/kube-apiserver
#生成证书申请文件
cat > kube-apiserver-csr.json <<EOF
{
"CN": "kube-apiserver",
"hosts": [
"127.0.0.1",
"10.10.10.30",
"10.10.10.31",
"10.10.10.32",
"10.10.10.100",
"10.200.0.1",
"kubernetes",
"kubernetes.default",
"kubernetes.default.svc",
"kubernetes.default.svc.cluster",
"kubernetes.default.svc.cluster.local"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"TS": "Beijing",
"L": "Beijing",
"O": "kube-apiserver",
"OU": "System"
}
]
}
EOF
#生成证书
cfssl gencert \
-ca=../ca/ca.pem \
-ca-key=../ca/ca-key.pem \
-config=../ca/ca-config.json \
-profile=kubernetes \
kube-apiserver-csr.json | cfssljson -bare kube-apiserver
#拷贝kube-apiserver到master节点
master="node30 node31 node32"
for i in$master;do
ssh$i"mkdir /etc/kubernetes/pki -p"
scp /opt/pki/kubernetes/ca/{ca.pem,ca-key.pem} /opt/pki/kubernetes/kube-apiserver/{kube-apiserver-key.pem,kube-apiserver.pem} $i:/etc/kubernetes/pki
done
#拷贝证书到node节点
node="node20 node21"
for i in$node;do
ssh$i"mkdir /etc/kubernetes/pki -p"
scp /opt/pki/kubernetes/ca/ca.pem $i:/etc/kubernetes/pki
done3.4.3 生成kube-proxy和ca证书
#创建目录
mkdir /opt/pki/kube-proxy
cd /opt/pki/kube-proxy
#生成ca配置文件
cat > proxy-ca-csr.json <<EOF
{
"CA":{"expiry":"87600h"},
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
}
}
EOF
#生成ca文件
cfssl gencert -initca proxy-ca-csr.json | cfssljson -bare proxy-ca
#生成客户端证书申请文件
cat > proxy-csr.json <<EOF
{
"CN": "proxy",
"key": {
"algo": "rsa",
"size": 2048
}
}
EOF
#生成证书
cfssl gencert \
-ca=proxy-ca.pem \
-ca-key=proxy-ca-key.pem \
-config=../kubernetes/ca/ca-config.json \
-profile=kubernetes proxy-csr.json | cfssljson -bare proxy
#拷贝证书到节点
##拷贝kube-proxy到master节点
master="node30 node31 node32"
for i in$master;do
scp /opt/pki/kube-proxy/{proxy-ca.pem,proxy.pem,proxy-key.pem} $i:/etc/kubernetes/pki
done
#拷贝证书到node节点
node="node20 node21"
for i in$node;do
scp /opt/pki/kube-proxy/proxy-ca.pem $i:/etc/kubernetes/pki
done3.4.4 生成kube-controller-manager证书和文件
#创建目录
mkdir-p /opt/pki/kubernetes/kube-controller-manager
cd /opt/pki/kubernetes/kube-controller-manager
#生成证书请求文件
cat > kube-controller-manager-csr.json <<EOF
{
"CN": "system:kube-controller-manager",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"TS": "Beijing",
"L": "Beijing",
"O": "system:kube-controller-manager",
"OU": "System"
}
]
}
EOF
#生成证书文件
cfssl gencert \
-ca=../ca/ca.pem \
-ca-key=../ca/ca-key.pem \
-config=../ca/ca-config.json \
-profile=kubernetes \
kube-controller-manager-csr.json | cfssljson -bare kube-controller-manager
#生成配置文件
#export KUBE_APISERVER="https://10.10.10.100:8443"
#--server=${KUBE_APISERVER}
kubectl config set-cluster kubernetes \
--certificate-authority=../ca/ca.pem \
--embed-certs=true \
--server=https://10.10.10.100:8443 \
--kubeconfig=kube-controller-manager.kubeconfig
kubectl config set-credentials system:kube-controller-manager \
--client-certificate=kube-controller-manager.pem \
--client-key=kube-controller-manager-key.pem \
--embed-certs=true \
--kubeconfig=kube-controller-manager.kubeconfig
kubectl config set-context default \
--cluster=kubernetes \
--user=system:kube-controller-manager \
--kubeconfig=kube-controller-manager.kubeconfig
kubectl config use-context default \
--kubeconfig=kube-controller-manager.kubeconfig
#拷贝证书到master节点
master="node30 node31 node32"
for i in$master;do
scp /opt/pki/kubernetes/kube-controller-manager/kube-controller-manager.kubeconfig $i:/etc/kubernetes/
done3.4.5 生成kube-scheduler证书
#创建目录
mkdir /opt/pki/kubernetes/kube-scheduler
cd /opt/pki/kubernetes/kube-scheduler
#生成证书申请文件
cat > kube-scheduler-csr.json <<EOF
{
"CN": "system:kube-scheduler",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"TS": "Beijing",
"L": "Beijing",
"O": "system:kube-scheduler",
"OU": "System"
}
]
}
EOF
#生成证书
cfssl gencert \
-ca=../ca/ca.pem \
-ca-key=../ca/ca-key.pem \
-config=../ca/ca-config.json \
-profile=kubernetes \
kube-scheduler-csr.json | cfssljson -bare kube-scheduler
#生成配置文件
#export KUBE_APISERVER="https://10.10.10.100:8443"
#--server=${KUBE_APISERVER}
kubectl config set-cluster kubernetes \
--certificate-authority=../ca/ca.pem \
--embed-certs=true \
--server=https://10.10.10.100:8443 \
--kubeconfig=kube-scheduler.kubeconfig
kubectl config set-credentials system:kube-scheduler \
--client-certificate=kube-scheduler.pem \
--client-key=kube-scheduler-key.pem \
--embed-certs=true \
--kubeconfig=kube-scheduler.kubeconfig
kubectl config set-context default \
--cluster=kubernetes \
--user=system:kube-scheduler \
--kubeconfig=kube-scheduler.kubeconfig
kubectl config use-context default \
--kubeconfig=kube-scheduler.kubeconfig
#拷贝文件到master
master="node30 node31 node32"
for i in$master;do
scp /opt/pki/kubernetes/kube-scheduler/kube-scheduler.kubeconfig $i:/etc/kubernetes
done3.4.6 生成集群管理员证书
#创建目录
mkdir /opt/pki/kubernetes/admin
cd /opt/pki/kubernetes/admin
#生成证书申请文件
cat > admin-csr.json <<EOF
{
"CN": "admin",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"TS": "Beijing",
"L": "Beijing",
"O": "system:masters",
"OU": "System"
}
]
}
EOF
#生成证书
cfssl gencert \
-ca=../ca/ca.pem \
-ca-key=../ca/ca-key.pem \
-config=../ca/ca-config.json \
-profile=kubernetes \
admin-csr.json | cfssljson -bare admin
#生成配置文件
#export KUBE_APISERVER="https://10.10.10.100:8443"
#--server=${KUBE_APISERVER}
kubectl config set-cluster kubernetes \
--certificate-authority=../ca/ca.pem \
--embed-certs=true \
--server=https://10.10.10.100:8443 \
--kubeconfig=admin.kubeconfig
kubectl config set-credentials admin \
--client-certificate=admin.pem \
--client-key=admin-key.pem \
--embed-certs=true \
--kubeconfig=admin.kubeconfig
kubectl config set-context default \
--cluster=kubernetes \
--user=admin \
--kubeconfig=admin.kubeconfig
kubectl config use-context default \
--kubeconfig=admin.kubeconfig
#拷贝文件到master
master="node30 node31 node32"
for i in$master;do
scp /opt/pki/kubernetes/admin/admin.kubeconfig $i:/etc/kubernetes
done





















 1440
1440

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








