1.为什么要移动各种表?
a.这些表是编译器生成的,里面存储了非常重要的信息。
b.在程序启动的时候,系统会根据这些表做初始化的工作:
比如,将用到的DLL中的函数地址存储到IAT表中.
c.为了保护程序,可以对.exe的二进制代码进行加密操作,但问题是:
各种表的信息与客户字节的代码和数据都混在一起了,如果进行加密,那系统在初始化的时候会出问题!
总结:
学会移动各种表,是对程序加密/破解的基础.
2.移动关键:

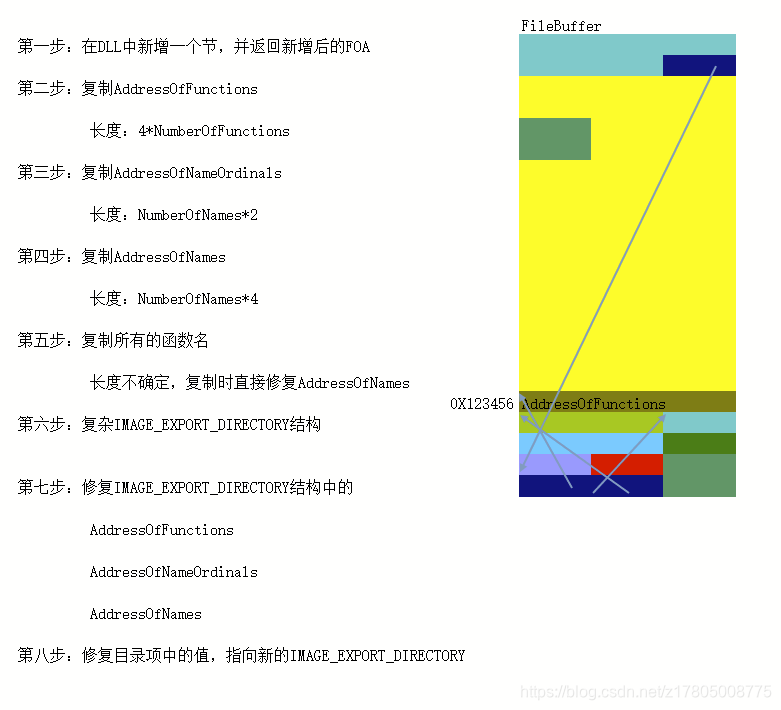
3.代码实现:
#include<stdio.h>
#include<stdlib.h>
#include<windows.h>
#define test 1
#define size_surplus_sizeofheader 0x50
DWORD ToLoaderPE(LPSTR file_path, PVOID* pFileBuffer);
BOOL MemoryToFile(PVOID pMemBuffer, DWORD size, LPSTR lpszFile);
DWORD FoaToImageOffset(PVOID pBuffer, DWORD dwFoa);
DWORD RvaToFileOffset(PVOID pBuffer, DWORD dwRva);
DWORD GetSctionEmptySpace(PVOID pFileBuffer, DWORD SectionOrdinal);
DWORD Alignment(DWORD alignment_value, DWORD addend, DWORD address);
DWORD MoveExportTable(PVOID pFileBuffer, DWORD FileBuffer, PVOID* pFileBuffer_ExportTable);
DWORD SizeOfExportTableSection(PVOID pFileBuffer);
VOID LogExportTable(PVOID pFileBuffer);
//char file_path[] = "c:\\users\\desktop\\notepad.exe";
char file_path[] = "c:\\users\\desktop\\dll1test.dll";
//char file_path[] = "c:\\users\\desktop\\ipmsg2007.exe";
char write_movexportable_file_path[] = "D:\\Lib\\dll1test.dll";
//返回PE文件大小
DWORD ToLoaderPE(LPSTR file_path, PVOID* pFileBuffer)
{
FILE *pFile = NULL;
DWORD FileSize = 0;
PVOID pFileBufferTemp = NULL;
pFile = fopen(file_path, "rb");
if (!pFile)
{
printf("(ToLoaderPE)Can't open file!\n");
return 0;
}
fseek(pFile, 0, SEEK_END);
FileSize = ftell(pFile);
printf("FileBuffer: %#x\n", FileSize);
fseek(pFile, 0, SEEK_SET);
pFileBufferTemp = malloc(FileSize);
if (!pFileBufferTemp)
{
printf("(ToLoaderPE)Allocate dynamic memory failed!\n");
fclose(pFile);
return 0;
}
DWORD n = fread(pFileBufferTemp, FileSize, 1, pFile);
if (!n)
{
printf("(ToLoaderPE)Read file failed!\n");
free(pFileBufferTemp);
fclose(pFile);
return 0;
}
*pFileBuffer = pFileBufferTemp;
pFileBufferTemp = NULL;
fclose(pFile);
return FileSize;
}
BOOL MemoryToFile(PVOID pMemBuffer, DWORD size, LPSTR lpszFile)
{
FILE *fp;
fp = fopen(lpszFile, "wb");
if (fp != NULL)
{
fwrite(pMemBuffer, size, 1, fp);
}
fclose(fp);
printf("Store file success!\n");
return 1;
}
DWORD RvaToFileOffset(PVOID pBuffer, DWORD dwRva)
{
PIMAGE_DOS_HEADER pDosHeader = NULL;
PIMAGE_NT_HEADERS pNTHeader = NULL;
PIMAGE_FILE_HEADER pPEHeader = NULL;
PIMAGE_OPTIONAL_HEADER32 pOptionHeader = NULL;
PIMAGE_SECTION_HEADER pSectionHeader = NULL;
if (!pBuffer)
{
printf("(RvaToFileOffset)Can't open file!\n");
return 0;
}
if (*((PWORD)pBuffer) != IMAGE_DOS_SIGNATURE)
{
printf("(RvaToFileOffset)No MZ flag, not exe file!\n");
return 0;
}
pDosHeader = (PIMAGE_DOS_HEADER)pBuffer;
if (*((PDWORD)((DWORD)pBuffer + pDosHeader->e_lfanew)) != IMAGE_NT_SIGNATURE)
{
printf("(RvaToFileOffset)Not a valid PE flag!\n");
return 0;
}
//printf("ImageOffset: %#x\n", dwRva);
pNTHeader = (PIMAGE_NT_HEADERS)((DWORD)pBuffer + pDosHeader->e_lfanew);
pPEHeader = (PIMAGE_FILE_HEADER)((DWORD)pNTHeader + 4); // 这里必须强制类型转换
pOptionHeader = (PIMAGE_OPTIONAL_HEADER32)((DWORD)pPEHeader + IMAGE_SIZEOF_FILE_HEADER);
pSectionHeader = (PIMAGE_SECTION_HEADER)((DWORD)pOptionHeader + pPEHeader->SizeOfOptionalHeader);
PIMAGE_SECTION_HEADER pSectionTemp = pSectionHeader;
if (dwRva <= pOptionHeader->SizeOfHeaders)
return (DWORD)dwRva;
else
{
for (int n = 0; n < pPEHeader->NumberOfSections; n++, pSectionTemp++)
{ //判断 : 文件对齐+文件偏移>file_panyi>文件偏移 (即是在文件的哪个节中)
if ((dwRva >= pSectionTemp->VirtualAddress) && (dwRva < pSectionTemp->VirtualAddress + pSectionTemp->Misc.VirtualSize))
{
return dwRva - pSectionTemp->VirtualAddress + pSectionTemp->PointerToRawData;
}
}
}
printf("RvaToFoa failed!\n");
return 0;
}
DWORD FoaToImageOffset(PVOID pBuffer, DWORD dwFoa)
{
PIMAGE_DOS_HEADER pDosHeader = NULL;
PIMAGE_NT_HEADERS pNTHeader = NULL;
PIMAGE_FILE_HEADER pPEHeader = NULL;
PIMAGE_OPTIONAL_HEADER32 pOptionHeader = NULL;
PIMAGE_SECTION_HEADER pSectionHeader = NULL;
if (!pBuffer)
{
printf("(FoaToImageOffset)Can't open file!\n");
return 0;
}
if (*((PWORD)pBuffer) != IMAGE_DOS_SIGNATURE)
{
printf("(FoaToImageOffset)No MZ flag, not exe file!\n");
return 0;
}
pDosHeader = (PIMAGE_DOS_HEADER)pBuffer;
if (*((PDWORD)((DWORD)pBuffer + pDosHeader->e_lfanew)) != IMAGE_NT_SIGNATURE)
{
printf("(FoaToImageOffset)Not a valid PE flag!\n");
return 0;
}
printf("FileOffset: %#x\n", dwFoa);
pNTHeader







 本文探讨了为何需要移动PE文件的导出表,这些表包含关键信息并用于程序初始化。在加密程序时,由于表与代码混杂,直接加密可能导致系统初始化错误。作者分享了移动和加密过程中的挑战,包括AddressOfName的匹配问题及LordPE中函数名显示错误的问题,旨在为程序加密和逆向工程提供基础。
本文探讨了为何需要移动PE文件的导出表,这些表包含关键信息并用于程序初始化。在加密程序时,由于表与代码混杂,直接加密可能导致系统初始化错误。作者分享了移动和加密过程中的挑战,包括AddressOfName的匹配问题及LordPE中函数名显示错误的问题,旨在为程序加密和逆向工程提供基础。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 1464
1464

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








