Security Fundamentals
- Attacks, services and mechanisms
- Security attacks
- Security services
- Methods of defense
- Are we at risk?
- Risk assessments
Part1:Definations
- Computer Security - generic name for the collection of tools designed to protect data and to thwart hackers
- Physical Security - measures to deny unauthorized access to facilities, equipment and resources
- Network Security - measures to protect data during their transmission
- Internet Security - measures to protect data during their transmission over a collection of interconnected networks
- …
Cryptographic algorithms and protocols(4 main areas)
- Symmetric encryption: using to conceal contents of blocks or streams of data of any size
- Asymmetric encryption:(public key to encryption and private key to decryption) Used to conceal small blocks of data, such as encryption keys and hash function values, which are used in digital signatures
- Data integrity algorithm: using to protect blocks of data,such as message(from alteration)
- Authentication protocols:Schemes based on the use of cryptographic algorithms designed to authenticate the identity of entities
The field of network and internet security consists of
- Measure to deter, prevent,detect and correct security violations that involve the transmission of information.
Computer security objectives
- confidentiality:private(don’t let anyone(unauthorized) to know)
- integrity(not be modified:or Assures that information and programs are changed only in a specified and authorized manner)
- Availability: Assures that systems work promptly and service is not denied to authorized
users


Accountability:In a system, here may be have some circumstances which will disturb the enterperner,and this attribute can help to find track a specified people who responsible for it.
Part2: Security attacks
-
1.Threats kind:(3 part)
- Threat: a possible danger that might exploit a vulnerability to breach security
- Vulnerability: a weakness which allows an attacker to abuse a system
- Attack:an attempt/action to destroy, expose, alter,disable,steal or gain unauthorized access to or make unauthorized use of an asset.
-
2.Security attacks
- Interruption:This is an attack on availability
- Interception:attack on confidentiality
- Modification:attack on integrity
- Fabrication: attack on authenticity

-
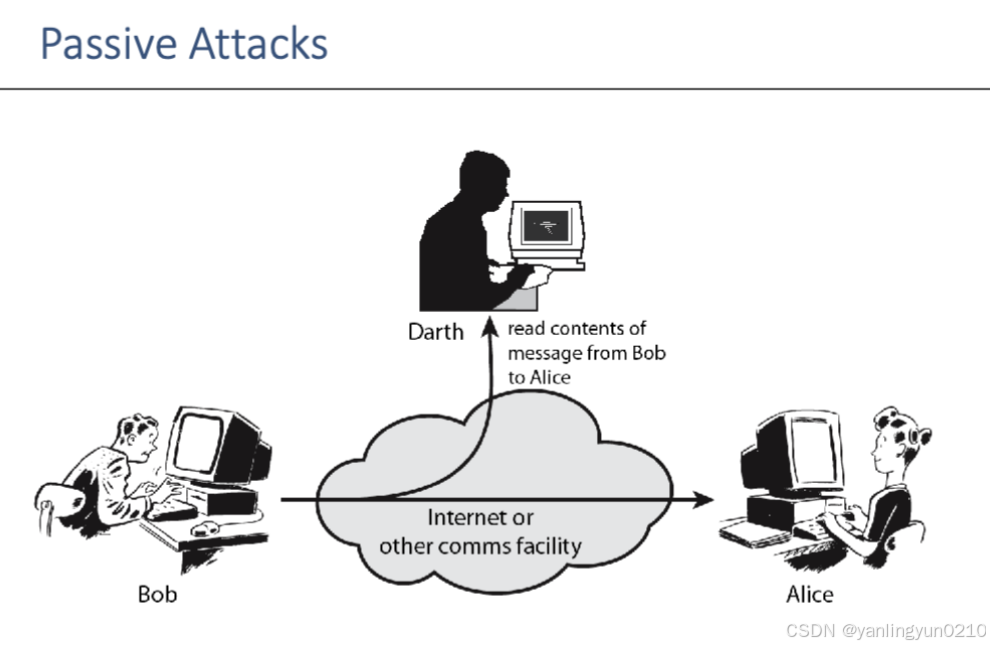
A passive attack: attempts to learn or make use of information from the system but doesn’t affect system resources
(Are in the nature of eavesdropping on, or monitoring of, transmissions.->goal:is to obtain the information that is being transmitted)
4. An active attack: attempts to alter system resources of affect their operation, and an active attack attempts to alter system resources or affect their operation.
(Involve some modification of the data stream or the creation of a false stream. Difficulty to prevent because of the wide variety of potential physical,software and network vulnerabilities.)


-
- Define of Authenticity and Accountability
- Authenticity
Verifying that users are who they say they are and that each input arriving at the system came from a trusted source - Accountability
The security goal that generates the requirement for actions of an entity to be traced uniquely to that entity























 428
428

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








