阐述
没有绝对安全的系统,也没有黑客破不掉的系统,所需要的只是时间而已… But,当时间成本大于收益成本,聪明人是不会进行尝试。
为了所谓的“相对安全”,研究代码混淆也是必要的。
探讨
Step 1
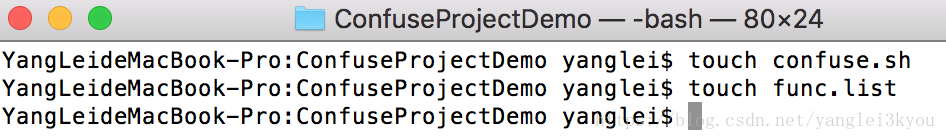
创建 confuse.sh、 func.list
终端(Terminal)可以键入
touch confuse.sh
touch func.sh
Step 2
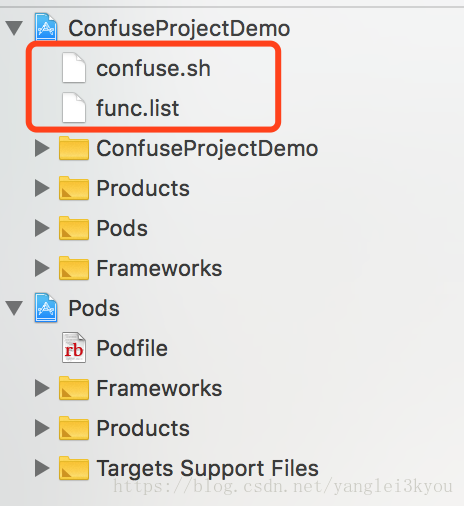
将 confuse.sh 、func.list 添加到工程中
Step 3
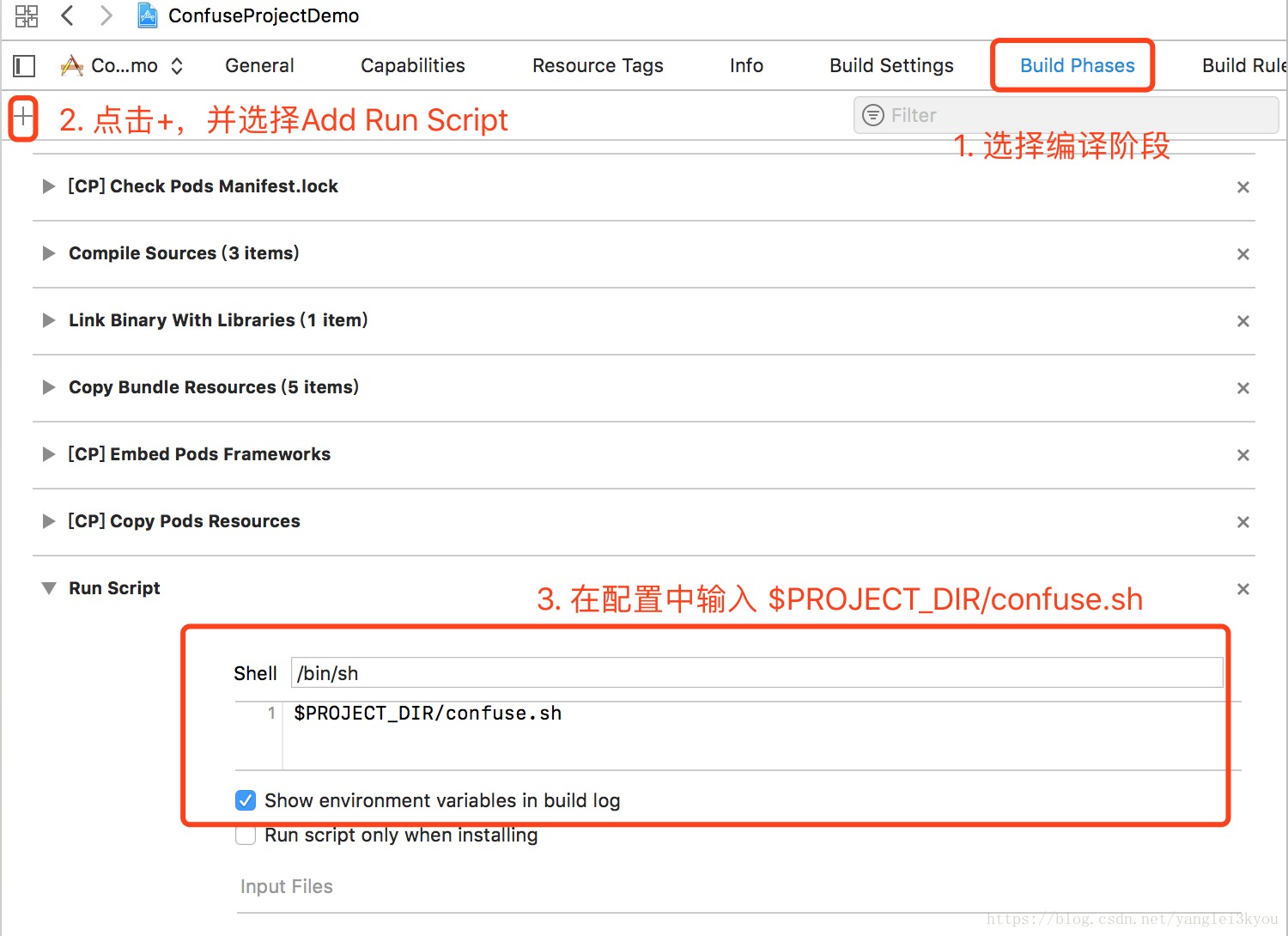
在 Build Phases 中添加 Run Script 来设置 程序启动时执行 confuse.sh
$PROJECT_DIR/confuse.sh
Step 4
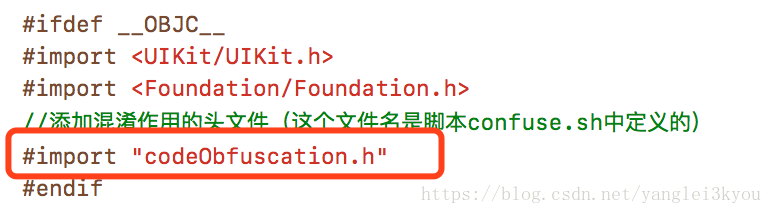
在程序PCH中引入混淆作用的头文件
(如果程序没有PCH文件,可参考 https://blog.youkuaiyun.com/yanglei3kyou/article/details/45891267 )
Step 5
在 confuse.sh 文件中填写以下内容
#!/usr/bin/env bash
TABLENAME=symbols
SYMBOL_DB_FILE="symbols"
STRING_SYMBOL_FILE="func.list"
HEAD_FILE="$PROJECT_DIR/$PROJECT_NAME/codeObfuscation.h"
export LC_CTYPE=C
#维护数据库方便日后作排重
createTable() {
echo "create table $TABLENAME(src text, des text);" | sqlite3 $SYMBOL_DB_FILE
}
insertValue() {
echo "insert into $TABLENAME values('$1' ,'$2');" | sqlite3 $SYMBOL_DB_FILE
}
query() {
echo "select * from $TABLENAME where src='$1';" | sqlite3 $SYMBOL_DB_FILE
}
ramdomString() {
openssl rand -base64 64 | tr -cd 'a-zA-Z' |head -c 16
}
rm -f $SYMBOL_DB_FILE
rm -f $HEAD_FILE
createTable
touch $HEAD_FILE
echo '#ifndef Project_codeObfuscation_h'
echo "//confuse string at `date`" >> $HEAD_FILE
cat "$STRING_SYMBOL_FILE" | while read -ra line; do
if [[ ! -z "$line" ]]; then
ramdom=`ramdomString`
echo $line $ramdom
insertValue $line $ramdom
echo "#define $line $ramdom" >> $HEAD_FILE
fi
done
echo "#endif" >> $HEAD_FILE
sqlite3 $SYMBOL_DB_FILE .dump
Step 6
在 func.list 中写出要混淆的函数名、变量名
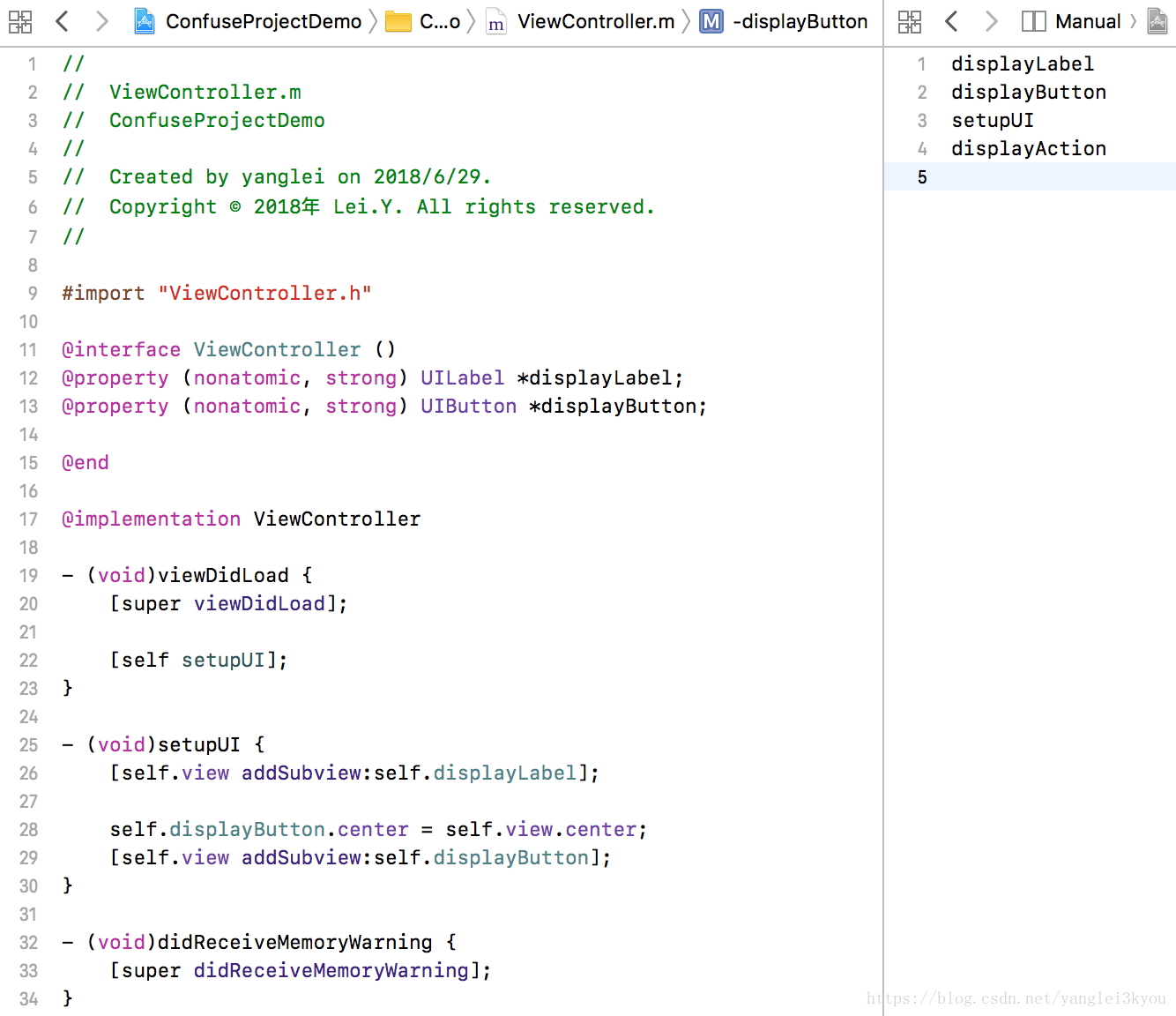
Step 7
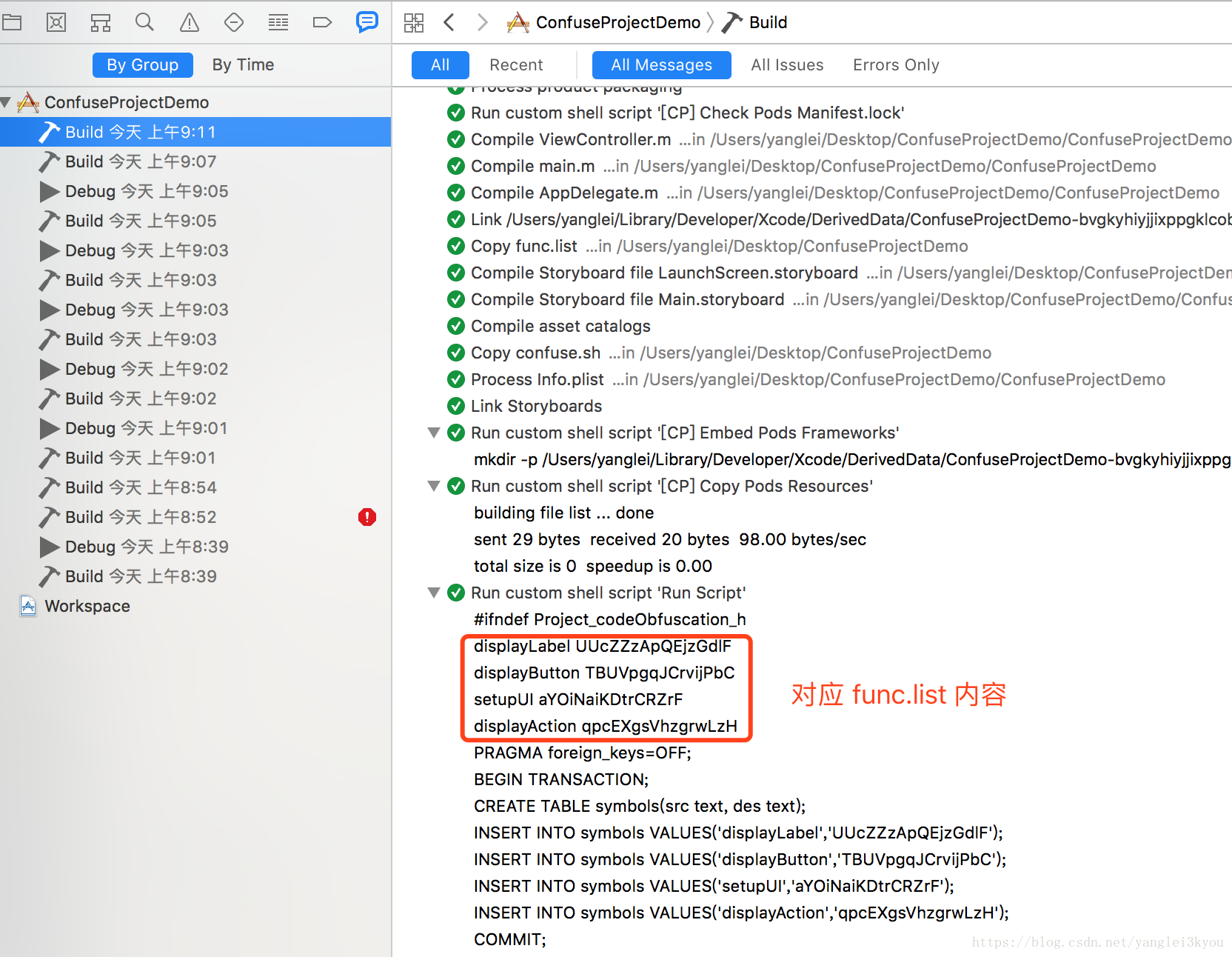
程序编译
若 Build 成功,可在 Show the Report navigator 选项卡中查看结果
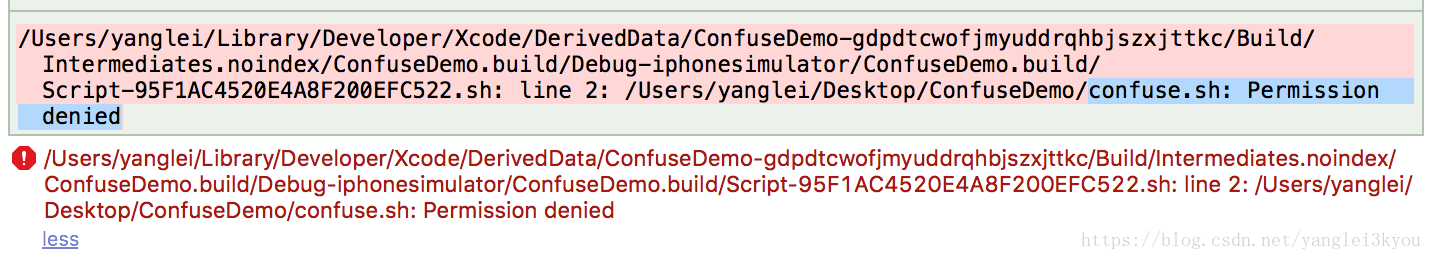
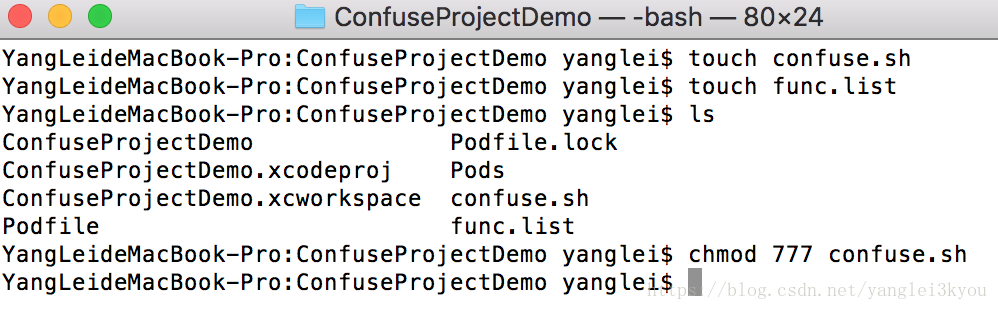
如果Build 失败,提示 Permission denied,可在终端中修改 confuse.sh 的权限,再将程序编译进行结果确认
chmod 777 confuse.sh
资料








 本文详细剖析了iOS应用中代码混淆的实践,通过使用confuse.sh工具,结合func.list文件进行函数混淆,以增强应用的安全性。在过程中可能会遇到权限问题,如'Permission denied',但通过调整权限设置可以解决,确保混淆过程顺利进行。
本文详细剖析了iOS应用中代码混淆的实践,通过使用confuse.sh工具,结合func.list文件进行函数混淆,以增强应用的安全性。在过程中可能会遇到权限问题,如'Permission denied',但通过调整权限设置可以解决,确保混淆过程顺利进行。
















 1418
1418

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








