ctfshow-愚人杯部分wp
热身:

思考很久还是从往年愚人杯找到了类似的答案
flag:一个不能说的秘密
MISC
奇怪的压缩包
下载附件是伪加密,用010修改并解压
得到图片black.png
发现好像有字符串没显示完全,拖进010修改高度

得到字符串:5oSa5Lq66lqC5b+r5LmQ77yB77yB77yB
同时检查010中是否有别的信息

在末尾发现key=eXVyZW5qaWU=
解base64得到yurenjie
用字符串和密钥尝试了各种解码都没有结果
用foremost分离black,png得到一个压缩包
尝试用Key解密成功

得到flag.png
同样修改高度

得到flag:ctfshow{Th1s_i5_f1ag}
哇库哇库2

题目提示密码是道数学题
算式结果即位e
保留12位且四舍五入得到2.71828182846
解压得到一个图片和一个文档图片不能显示,文档内位b站视频台词
用010查看图片发现内容是png格式文件头尾确实Jpg格式并且宽高都为1
修改头尾并用crc32脚本爆破出宽高
import os
import binascii
import struct
crcbp = open("HINT.png", "rb").read() #打开图片
for i in range(2000):
for j in range(2000):
data = crcbp[12:16] + \
struct.pack('>i', i)+struct.pack('>i', j)+crcbp[24:29]
crc32 = binascii.crc32(data) & 0xffffffff
if(crc32 == 0x72DC3AB7): #图片当前CRC
print(i, j)
print('hex:', hex(i), hex(j))
得到图片长宽 0x31b 0x3a9 修改后得到图片
没找到什么有用信息
再看doc文件仔细阅读后发现每句结尾标点有点东西手撸十几个发现是ook
用word的替换功能得到
..................!?!!.?..................?.?!.?....................................!.?.........!?!!.?........?.?!.?..!.?.......!?!!.?!!!!!!?.?!.?!!!!!!!!!!!.?.......!?!!.?......?.?!.?........!.?.......!?!!.?!!!!!!?.?!.?!!!!!...............!.................!.........!.?.................!?!!.?!!!!!!!!!!!!!!!!?.?!.?!!!!!!!!!!!!!!!.?...............!?!!.?..............?.?!.?..................!.!!!!!!!!!!!.?.........!?!!.?........?.?!.?!.?.........!?!!.?!!!!!!!!?.?!.?!!!!!!!!!!!!!!!!!.!!!!!.?.........!?!!.?!!!!!!!!?.?!.?!!!!!!!!!.?.........!?!!.?........?.?!.?............!.?.......!?!!.?!!!!!!?.?!.?!!!.?.......!?!!.?......?.?!.?..!.?.............!?!!.?!!!!!!!!!!!!?.?!.?!!!!!!!!!!!!!!!!!!!!!!!!!.?...............!?!!.?..............?.?!.?..............!.?.................!?!!.?!!!!!!!!!!!!!!!!?.?!.?!!!!!!!!!!!!!!!!!.?...................!?!!.?..................?.?!.?......................!.?.
用Brinfuck/Ook!网站解码

得到flag:ctfshow{4niya_KaWa1i!}
琴柳感
解压得到文本

就很怪,根据题目和文本内容搜到

文本中这四句不按顺序的重复出现就想到是四进制或者某种只有四个字符密文的加密
用替换按原话顺序转换为四进制得到
120313101212130312201233131313231320122112321213120213111203121112321213132012211232121311331321122112021311132212011221132112211133132212011221122312111230122112011232132112211230122112011232120212011331```
太长了在线网站不能完全转换
python写个脚本转换为十六进制
```python
n = int('120313101212130312201233131313231320122112321213120213111203121112321213132012211232121311331321122112021311132212011221132112211133132212011221122312111230122112011232132112211230122112011232120212011331',4)
print(hex(n))
#0x63746673686f777b78696e67627563656e6778696e675f796962757a616979695f7a61696b656c69616e79696c69616e62617d

cyberchef
在线网站解码得到flag:ctfshow{xingbucengxing_yibuzaiyi_zaikelianyilianba}
CRYPTO
easy_base
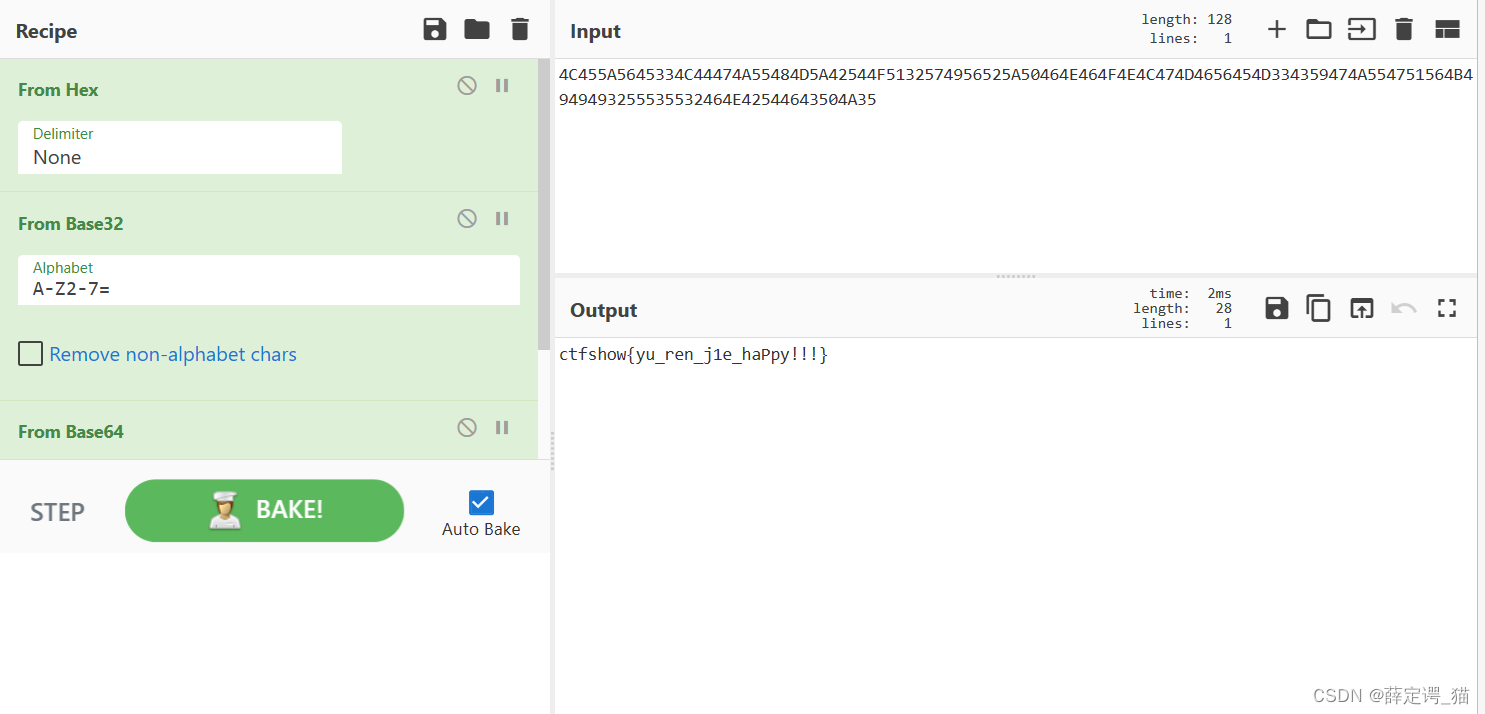
按顺序解hex,base32,base64得到flag:
ctfshow{yu_ren_j1e_haPpy!!!}
RE
easy_pyc
python反编译-在线工具

用在线网站反编译,只有一个异或和一个加减(列表里的%不太懂是什么意思)
脚本解密
int str[] = { 0x16,0x1d,0x1e,0x1a,0x18,0x9,0xff,0xd0,0x2c,0x03,0x02,0x14,0x38,0x6d,0x01,0x43,0x44,0xbd,0xf7,0x2a,0x0d,0xda,0xf9,0x1c,0x26,0x35,0x27,0xda,0xd4,0xd1,0x0b,0xc7,0xc7,0x1a,0x90,0x44,0xa1 };
for (int i = 34; i > 0; i--)
{
str[i - 1] = str[i] ^ str[i - 1];
}
for (int i = 0; i < 37; i++)
{
cout << char(str[i] - i);
}
ctfshow{Just_F00l’s_D@y_R3_Ch3ck-in!}
easy_cc
查壳:32位无壳:
拖进ida内分析

大体逻辑就是密文轮转异或"key123"
写脚本解题
int str[] = { 0x16,0x1d,0x1e,0x1a,0x18,0x9,0xff,0xd0,0x2c,0x03,0x02,0x14,0x38,0x6d,0x01,0x43,0x44,0xbd,0xf7,0x2a,0x0d,0xda,0xf9,0x1c,0x26,0x35,0x27,0xda,0xd4,0xd1,0x0b,0xc7,0xc7,0x1a,0x90,0x44,0xa1 };
for (int i = 34; i > 0; i--)
{
str[i - 1] = str[i] ^ str[i - 1];
}
for (int i = 0; i < 37; i++)
{
cout << char(str[i] - i);
}
flag:ctfshow{cc_re_good_good!}
本次比赛只解出以上题目…








 文章详细描述了多个CTF竞赛中的解谜过程,涉及图片伪加密、字符串解码、CRC32校验、Python脚本使用、四进制和十六进制转换、Ook!编码以及简单的异或加密算法。参赛者通过这些技术解出了不同类型的题目,包括热身、MISC、哇库哇库2、琴柳感和多个CRYPTO及RE题目。
文章详细描述了多个CTF竞赛中的解谜过程,涉及图片伪加密、字符串解码、CRC32校验、Python脚本使用、四进制和十六进制转换、Ook!编码以及简单的异或加密算法。参赛者通过这些技术解出了不同类型的题目,包括热身、MISC、哇库哇库2、琴柳感和多个CRYPTO及RE题目。
















 1560
1560










