题目:302重定向,打开页面显示如下

这个题目有2个方法可以拿到flag。
首先都是用Burp抓包。
1、用Burp抓取打开题目页面的报文,回应报文显示
304 Not Modified,既然知道是重定向的题目,点击 Give me Flag 链接,再次抓包,得到回应报文
拿到flag。
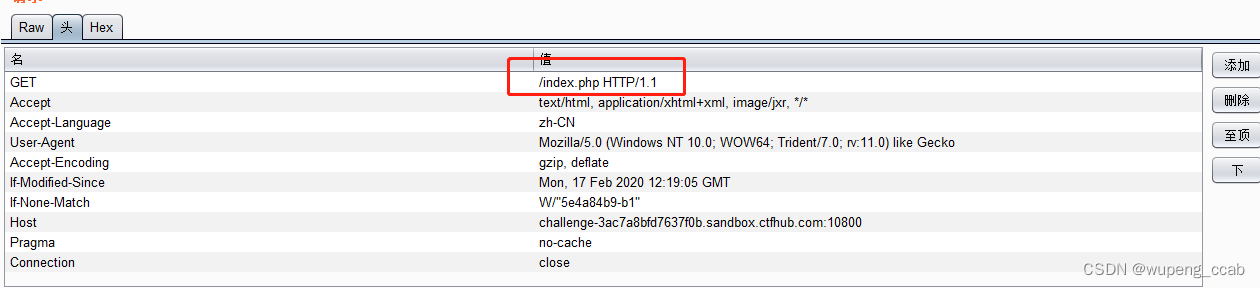
2、观察刚打开题目页面的请求报文。
GET 值里面 没有具体的URL,看回应报文里面 server:openresty 可知服务器使用了PHP环境,猜测可能由index.html 重定向到 index.php。还有注意观察Give me Flag链接地址也是index.php。构造GET /index.php HTTP/1.1 直接发包。
同样可以拿到flag 。







 文章讲述了如何通过Burp工具抓包分析,识别出302重定向的网页题目中的flag。方法一是观察NotModified响应并点击链接抓取;方法二是分析GET请求和响应,推测URL结构,直接构造GET请求获取flag。
文章讲述了如何通过Burp工具抓包分析,识别出302重定向的网页题目中的flag。方法一是观察NotModified响应并点击链接抓取;方法二是分析GET请求和响应,推测URL结构,直接构造GET请求获取flag。
















 871
871

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








