本帖子只仅仅是为了我本人学习笔记,为了我自己以后复习知识点用的,切勿用在商业用途或对平台做出攻击。本人概不负责。
一下简称黑猫吧。
一、分析
ts: 1647858750696
rs: DGIAstYmuAl75cXR
signature: 261a590c26ec211edbdfb9b1ce8692d7d292c5ddbac45f2e34857841fa17e4e7
callback: jQuery111203671219046350367_1647858750679
keywords: 减肥
page_size: 10
page: 2
_: 1647858750684这其中加密的只有rs、signature。所以要逆向的也就是这两个参数。
二、找到signature加密地方
1.最开始我用了搜索,没找到正确的地方。
2.我点击Initiator跟着调用栈走,只找到了URL发送请求的地方,还是没找到加密的地方,理论上是能找到的,可能是我方法不对。
最后这两个常规方法用完之后,用了一下非常规方法。我将整个JS代码拷贝下来观察。
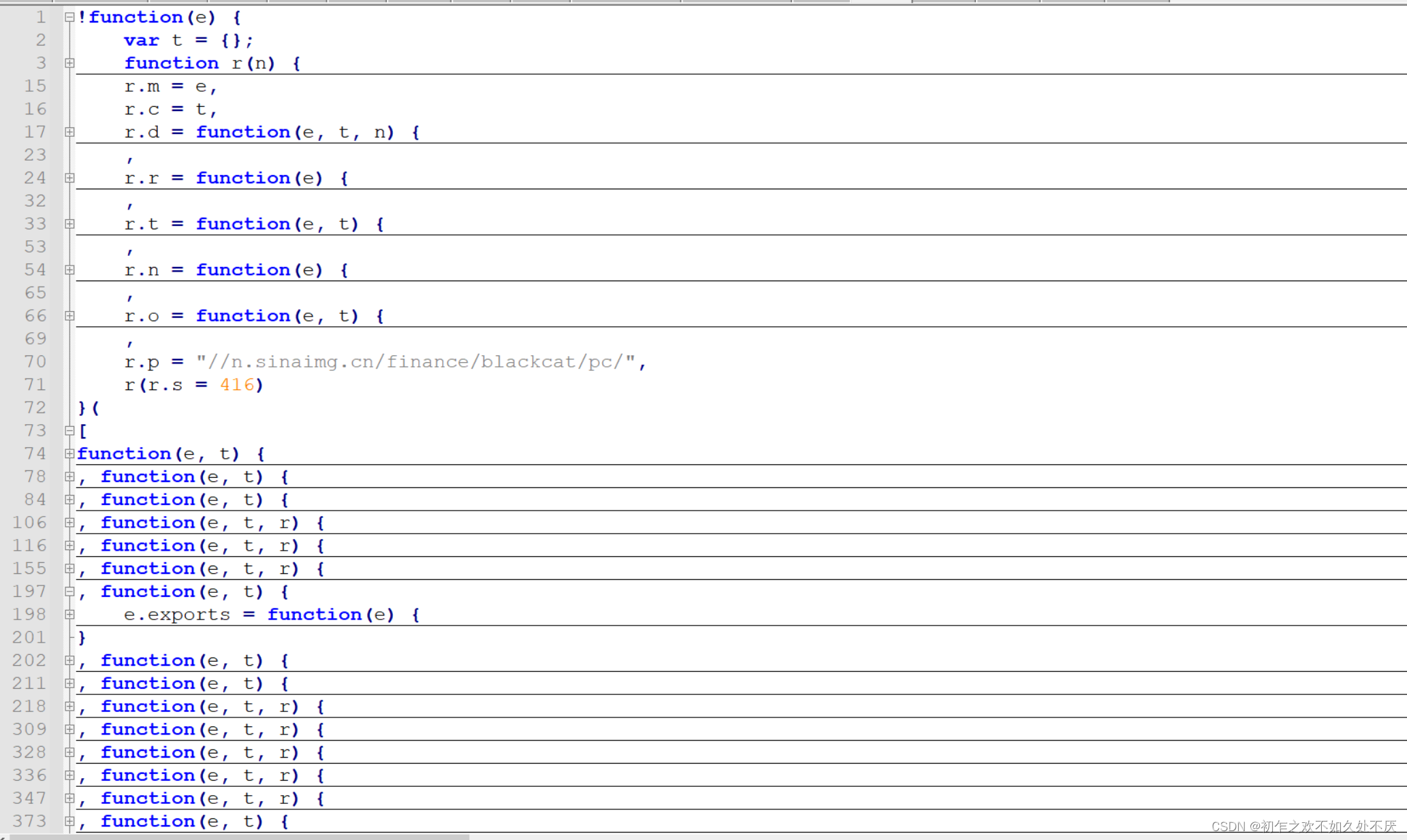
在观察整个代码结构的过程中发现了一个地方,瞬间秒懂,搜索关键词。
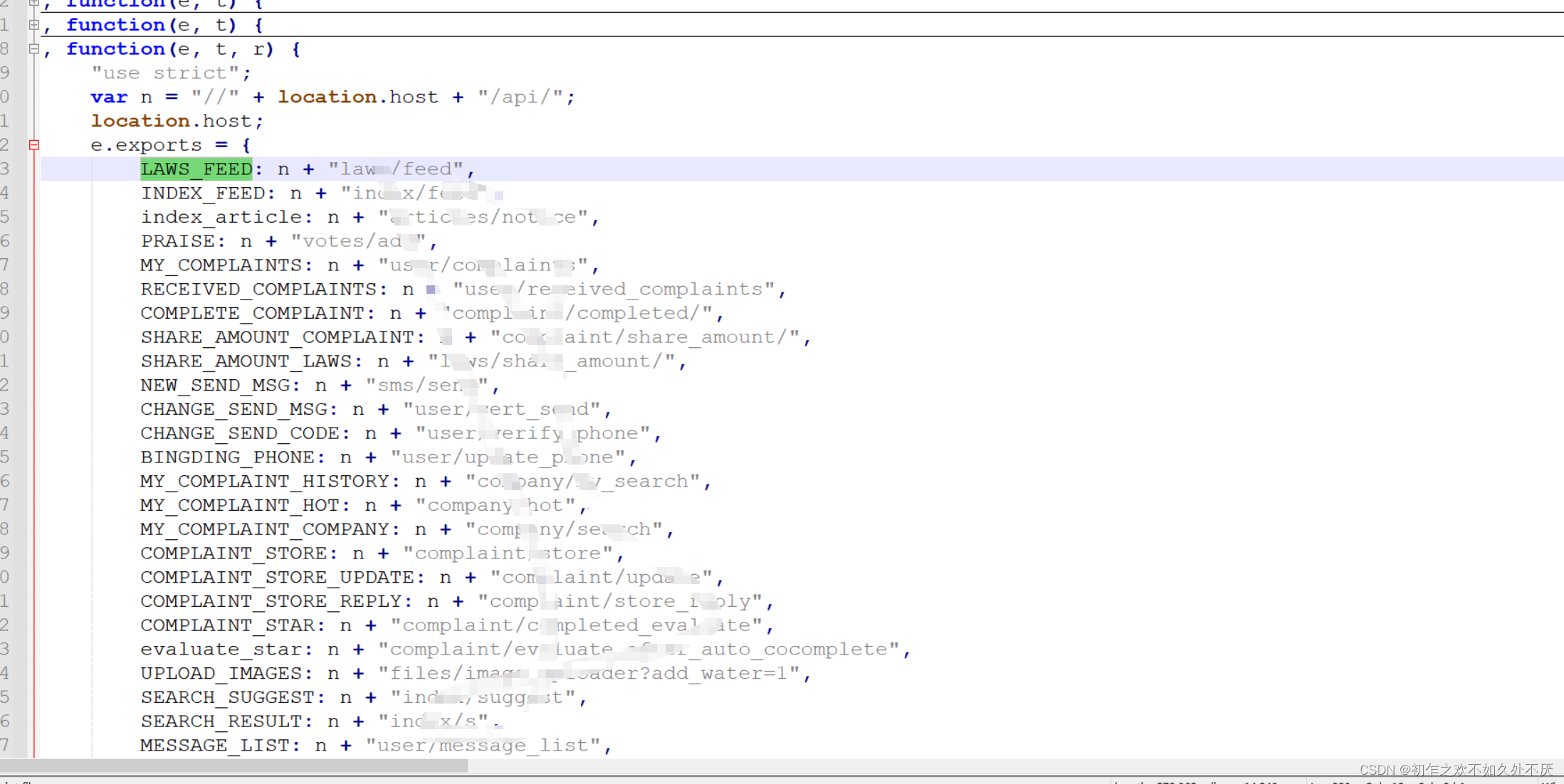
三、破解加密

l([p, b, y, d, h, u["type" + e]].sort().join(""));
p:时间戳 √
b:"kTYLEM0wEF8NQjvO"
y:"$d6eb7ff91ee257475%" =>js文件中的固定值
d:关键词
h:10
u["type" + e]]定位到这里一切就很明朗了,挨个找到p, b, y, d, h, u["type" + e],这里面b其实就是最初的时候加密参数rs,而b的加密形成也很简单就在上面不远处,我就不截图了。
注意:这里的l是SHA256加密,我最初被干扰了,因为l返回的值是列表,列表里的元组从十进制转换成16进制正好和最后的加密结果一样,默认一直当做字符串转换成16进制往上逆。后来往上逆的过程中无意间看到了HMAC、Hex让我开始慢慢怀疑;
最后就这些,这个网站其实很简单,实在不知道该怎么再去详细了,再详细就成贴代码上来了;就这吧,每周坚持逆向一个网站,从简到难,一步一步提升自己。
exports = {
LAWS_FEED: n + "laws/feed",
INDEX_FEED: n + "index/feed",
index_article: n + "articles/notice",
PRAISE: n + "votes/add",
MY_COMPLAINTS: n + "user/complaints",
RECEIVED_COMPLAINTS: n + "user/received_complaints",
COMPLETE_COMPLAINT: n + "complaint/completed/",
SHARE_AMOUNT_COMPLAINT: n + "complaint/share_amount/",
SHARE_AMOUNT_LAWS: n + "laws/share_amount/",
NEW_SEND_MSG: n + "sms/send",
CHANGE_SEND_MSG: n + "user/cert_send",
CHANGE_SEND_CODE: n + "user/verify_phone",
BINGDING_PHONE: n + "user/update_phone",
MY_COMPLAINT_HISTORY: n + "company/my_search",
MY_COMPLAINT_HOT: n + "company/hot",
MY_COMPLAINT_COMPANY: n + "company/search",
COMPLAINT_STORE: n + "complaint/store",
COMPLAINT_STORE_UPDATE: n + "complaint/update",
COMPLAINT_STORE_REPLY: n + "complaint/store_reply",
COMPLAINT_STAR: n + "complaint/completed_evaluate",
evaluate_star: n + "complaint/evaluate_after_auto_cocomplete",
UPLOAD_IMAGES: n + "files/image_uploader?add_water=1",
SEARCH_SUGGEST: n + "index/suggest",
SEARCH_RESULT: n + "index/s",
MESSAGE_LIST: n + "user/message_list",
GET_VIDEOID: n + "video/create_video_and_notify",
GET_AUTH_URL: n + "video/get_authed_s3_url",
REPORT_FEED: n + "articles/feed",
SELLER_FEED: n + "company/received_complaints",
SELLER_LIST: n + "company/main_search",
JURY_FEED: n + "jury/feed",
JURY_LIST: n + "jury/list_complaints",
JURY_REPLY: n + "jury/store_reply",
JURY_INVITE: n + "jury/invite",
HANDLE_INVITE: n + "jury/handle_invite",
jury_zan: n + "jury/vote",
jury_hot: n + "jury/hot",
jury_hot_comp: n + "jury/hotcomps",
jury_rank: n + "jury/rank",
invite_list: n + "jury/jury_list",
company_search: n + "user/search_recv_complaints?k=",
complaint_types: n + "company/issues",
company_billboard: n + "top_rank/rank",
company_field: n + "top_rank/rank_fields",
file_hide: n + "complaint/set_atch_hide",
company_datas: n + "company/get_stast",
name_hide: n + "complaint/set_anon",
email_vc: n + "company/email_vc",
add_email: n + "company/add_email",
del_email: n + "company/del_email",
email_list: n + "company/emails",
group_list: n + "grp_comp/feed",
group_tslist: n + "grp_comp/feed_by_co",
group_suggest: n + "grp_comp/suggs",
group_progress: n + "grp_comp/progs",
group_comps: n + "grp_comp/comps",
user_glist: n + "grp_comp/init_grpcomps",
company_glist: n + "grp_comp/recv_grpcomps",
group_reply: n + "grp_comp/store_reply",
group_join: n + "grp_comp/join_info",
group_store_sugg: n + "grp_comp/store_sugg",
group_share_img: n + "grp_comp/shr_img",
group_share: n + "grp_comp/incr_shr_amt/",
group_file_hide: n + "grp_comp/set_atch_hide",
group_can_join: n + "grp_comp/can_join",
heimao315: n + "leadership/get_items",
dataCompany: n + "company/quick_stat_list",
dataStat: n + "company/quick_stat",
join_company: n + "company/apply_settle",
message_read: n + "user/message_read",
message_read_all: n + "user/message_read_all",
top_card_time: n + "top_rank/grprank_span",
new_rank_card: n + "top_rank/grprank_card",
filed_rank_card: n + "top_rank/grprank_field_card",
top_card_list: n + "top_rank/grprank_list",
week_rank_list: n + "top_rank/riserank_list",
user_is_law: "".concat(n, "complaint/sync_lawfirm?"),
all_comp_field: "".concat(n, "complaint/qxzx_fields?"),
comp_is_field: "".concat(n, "company/field?"),
comp_is_tip: "".concat(n, "company/get_popup"),
comp_set_tip: "".concat(n, "company/set_popup"),
comp_is_notice: "".concat(n, "user/check_agree?"),
comp_set_notice: "".concat(n, "user/sign_agree?"),
comp_car_data: "".concat(n, "company/auto_products?")
}
逆向步骤{
1.分析参数{
ts: 1647510985452
rs: kTYLEM0wEF8NQjvO
signature: 8fd59d909ac559ad5a926e54308d135492ef688b78b163977a143cfbb046495d
callback: jQuery111207311518370923895_1647510985397
keywords: 减肥
page_size: 10
page: 2
_: 1647510985399
}
其中ts、和_目测是时间戳
rs、signature、callback不知道是什么含义,其中除了signature外其他两个都没变过
2.先从signature入手{
a.全局搜索signature没搜索到,最后走的调用栈,找到了发送请求和加密的JS文件
b.根据调用栈只找到了发送的入口,依然没找到加密的地方,而且发送入口的URL是被加密后穿过来的
c.根据b可以理解未发送入口只是被别的地方当做一个函数调用而已,向上追溯并没有追溯到
d.拷贝了整个js文件后观察到
exports={
LAWS_FEED: n + "laws/feed",
INDEX_FEED: n + "index/feed",
index_article: n + "articles/notice",
PRAISE: n + "votes/add",
MY_COMPLAINTS: n + "user/complaints",
RECEIVED_COMPLAINTS: n + "user/received_complaints",
........
SEARCH_RESULT: n + "index/s"
}
而这其中就有我们发送请求的url参数,然后针对SEARCH_RESULT全局搜索,果然找到了
}
3.破解加密参数{
l([p, b, y, d, h, u["type" + e]].sort().join(""));
p:时间戳 √
b:"kTYLEM0wEF8NQjvO"
y:"$d6eb7ff91ee257475%" =>js文件中的固定值
d:关键词
h:10
u["type" + e]]
}
}
最近有不少想学习这个的同学后台私信我,我平时偶尔看看后台消息,错过了好多小伙伴,我在优快云个人简介中留了我的联系方式,大家有想学的可以通过这个加我,记得加备注哈。


























 2114
2114

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








