SAML Single-Sign On
This feature is only available on EE licensed instances of FlowForge.
FlowForge allows users to sign in through their SAML identity provider, such as Google Workspace.
The platform can be configured with multiple SAML configurations and uses the user's email domain to identify which identity provider should be used.
The user must already exist on the FlowForge platform before they can sign in via SSO.
Once enabled for a particular email domain, regular users on that domain will be directed to the Identity Provider in order to log in. They will no longer be able to log in with their local password, nor will they be able to change their email address in User Settings.
Admin users will still be able to log in with their original FlowForge username/password - this ensures they don't get locked out of the platform if there is a problem with the Identity Provider configuration.
Managing SAML SSO Configurations
The SAML SSO Configurations are managed by the platform Administrator under the Admin Settings > Settings > SSO section.
To fully configure SAML SSO, you will need to generate a configuration in FlowForge, provide some of the generated values to your Identity Provider, and copy back some values they provide.
Create a SAML SSO Configuration
-
Click 'Create SSO SAML Configuration' to create a new config
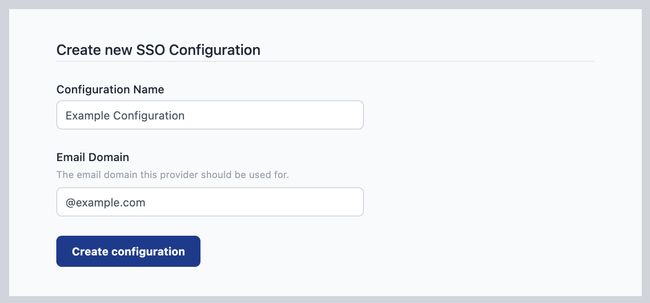
-
Give the configuration a name to help identify it, and provide the email domain name this configuration should apply to.
-
Click 'Create configuration'
At this point, the configuration has been created and metadata generated for the configuration, but it is not active.
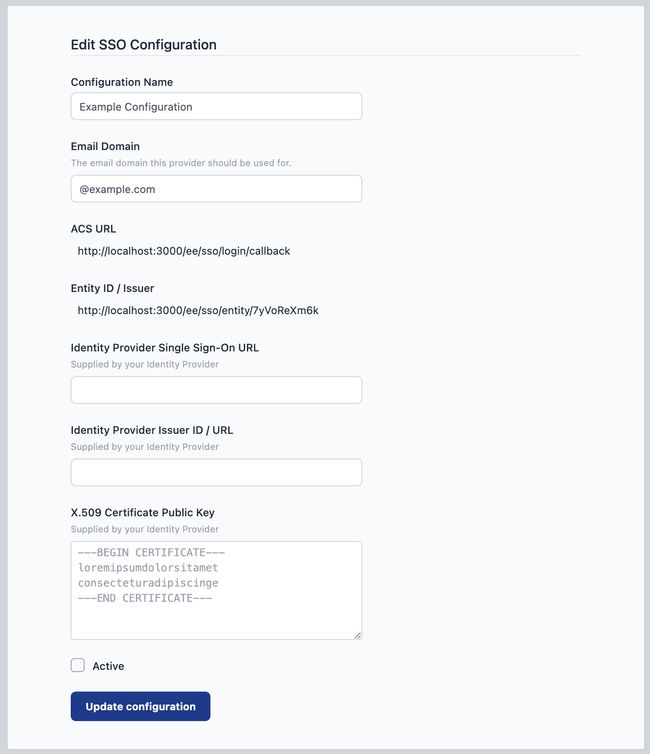
-
Copy the
ACS URLandEntity ID / Issuervalues as you will need to configure your Identity Provider with these values.
You can save the configuration at any time by clicking the Update configuration button. The configuration will only be enabled when you tick the active checkbox and save the changes.
Configure your Identify Provider
Every Identity Provider uses slightly different terminology and varies what information they require and what they provide. This can make it a tricky task to complete.
We provide specific guides for the providers we have verified below.
If you have a working configuration for a provider not listed here, please do share the details so we can add them to the list.
The general points are:
-
Your Identity Provider will supply you with some of the following values that should be entered into your FlowForge SAML SSO Configuration:
Single Sign-On URL- also referred to as 'SAML Endpoint', 'Login URL' or 'IdP SSO URL'.Issuer ID / URLX.509 Certification Public Key- the public key of a certificate used to sign SAML requests.
-
Configure the
NameIDSAML option to beEmailAddressand have it return the email of the user logging in. This is how FlowForge will verify they are a known user on the platform.
Enable your SAML SSO Configuration
Once you have setup both sides of the configuration you can enable it for use by ticking the active checkbox and clicking Update configuration.
Providers
The following is a non-exhaustive list of the providers that are known to work with FlowForge SAML SSO.
- Azure AD
- Google Workspace
- OneLogin
Google Workspace
Google provide a guide for creating a custom SAML Application here.
Google Workspace only supports HTTPS-based SSO URLs. You cannot use it when developing locally using http://localhost:3000.
The following table maps the Google Workspace terminology to the FlowForge settings.
| FlowForge Setting | Google Workspace Setting |
|---|---|
Identity Provider Single Sign-On URL | SSO URL |
Identity Provider Issuer ID / URL | Entity ID |
X.509 Certificate Public Key | Certificate |
OneLogin
Follow this guide to create a OneLogin SAML Test Connector.
| FlowForge Setting | OneLogin Setting |
|---|---|
Identity Provider Single Sign-On URL | SAML 2.0 Endpoint (HTTP) |
Identity Provider Issuer ID / URL | Issuer URL |
X.509 Certificate Public Key | X.509 Certificate |







 FlowForge的EE许可实例支持SAML单点登录,允许用户通过如GoogleWorkspace的身份提供者进行登录。平台可配置多个SAML设置,使用用户的电子邮件域来确定应使用的身份提供者。管理员可以通过AdminSettings>SSO部分管理SAMLSSO配置。用户必须先在FlowForge平台上存在,然后才能通过SSO登录。一旦启用特定邮件域名的SSO,常规用户将被定向到身份提供者登录,无法再使用本地密码登录或更改电子邮件地址。
FlowForge的EE许可实例支持SAML单点登录,允许用户通过如GoogleWorkspace的身份提供者进行登录。平台可配置多个SAML设置,使用用户的电子邮件域来确定应使用的身份提供者。管理员可以通过AdminSettings>SSO部分管理SAMLSSO配置。用户必须先在FlowForge平台上存在,然后才能通过SSO登录。一旦启用特定邮件域名的SSO,常规用户将被定向到身份提供者登录,无法再使用本地密码登录或更改电子邮件地址。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








