问题出现后,首先检查了配置文件的问题,并没有出错,然后网上也搜了不少,一直没解决,最后,重点来了,使用其他路径时,没有报错,我就检查了方法返回的字符串路径,发现字符串路径多了一个空格!重新写了下字符串路径,问题解决。其实我发现,很多程序上出现的问题都是一些很小的问题,却总是浪费我们很多时间去查找,各位在编写程序的时候尽量仔细一点,耐心一点啦,我找这个问题差点崩溃,哈哈哈。
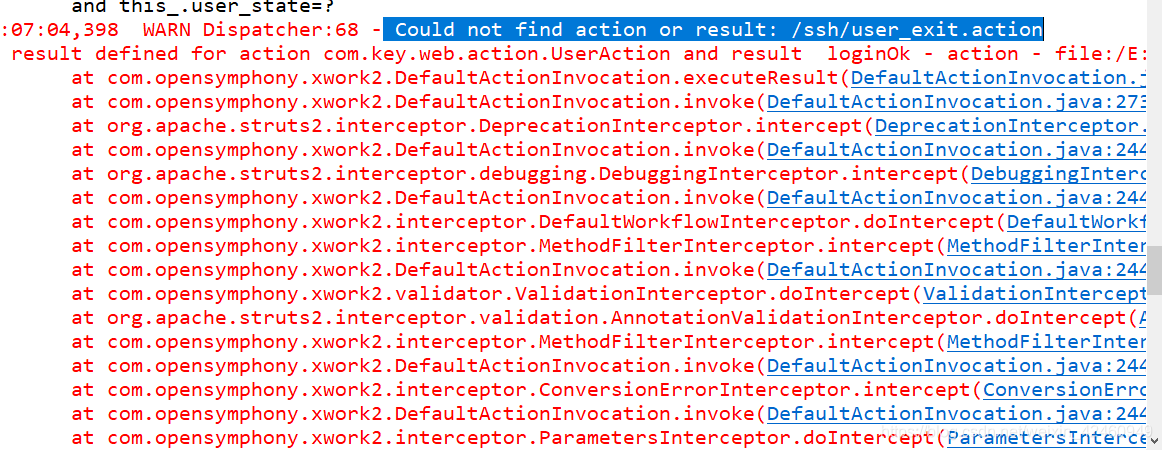
使用SSH框架编写程序时,出现 Could not find action or result: /ssh/user_exit.action问题,但配置文件没有出错
最新推荐文章于 2024-05-26 16:33:56 发布





















 1693
1693

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








