事情是这样的, 昨天我分享了一个ssh反向隧道的教程
帮助我们开发时能优雅的调试
教程如下:
《如何在本地调试代码又能在公网访问api呢?答案就是 SSH 反向隧道+nginx反向代理(适合临时测试)》
结果晚上就有好奇宝宝来扫我敏感文件了
有想拿sql的,有想看git信息的,还有想拿docker的
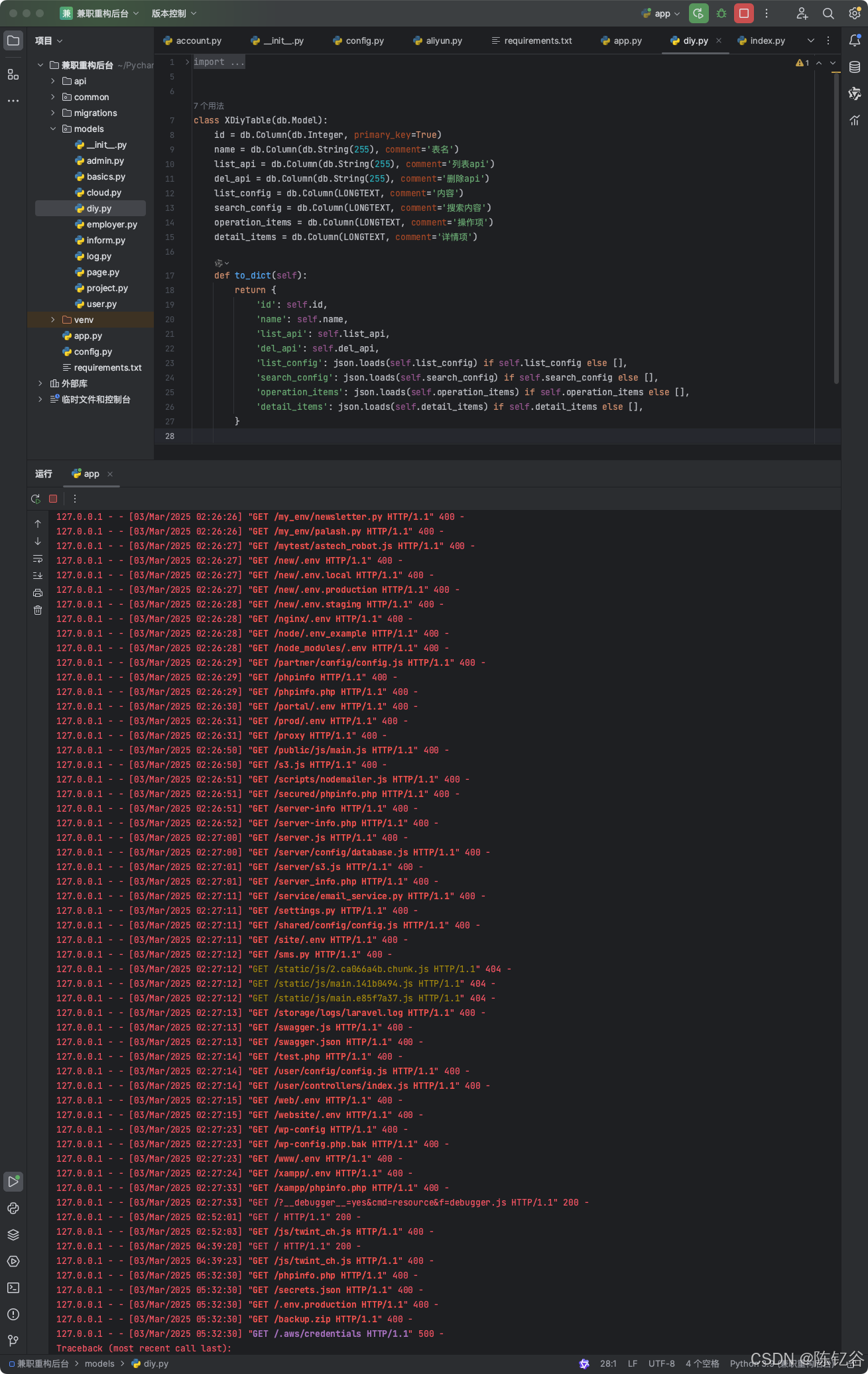
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /config.yml HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /database.sql HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /wp-config.php HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /backup.tar.gz HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /user_secrets.yml HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /config/production.json HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /config.php HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /config.xml HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET / HTTP/1.1" 200 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /wp-admin/setup-config.php HTTP/1.1" 400 -
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /_vti_pvt/service.pwd HTTP/1.1" 4
你看看有多过分,
咱就是说, 我好心做分享, 总有手痒的兄弟想看人底裤是吧
像这个
127.0.0.1 - - [03/Mar/2025 05:32:30] "GET /wp-config.php HTTP/1.1" 400 -
咱昨天都贴图了是是python代码, 为啥还以为是wordpress呢, 扫也扫的没水平呀
凌晨五点半还在扫,真是偷鸡摸狗搞惯了是吧
在这也给新手朋友提个醒,注意隐私文件限制一下访问权限
注意网络安全!
 分享SSH反向隧道教程遭敏感文件扫描
分享SSH反向隧道教程遭敏感文件扫描





















 583
583

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








