此前,Nginx只支持OSCP验证服务器证书。
目前,Nginx 1.19.0+已经支持使用OSCP验证客户端证书:https://trac.nginx.org/nginx/ticket/1534
有关Nginx双向证书验证的详细配置可以参考笔者的《Nginx双向证书校验(服务器验证客户端证书)》一文。
如下配置:
server {
listen 50443;
ssl on;
server_name example.com;
ssl_certificate D:\\nginx-1.19.1\\ssl_cert\\example-all.crt;
ssl_certificate_key D:\\nginx-1.19.1\\ssl_cert\\example-key.txt;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_verify_client on;
ssl_ocsp on;
resolver 172.16.1.251;
ssl_client_certificate D:\\nginx-1.19.1\\ssl_cert\\example-ca.crt;
#charset koi8-r;
#access_log logs/host.access.log main;
location / {
root html;
index index.html index.htm;
}
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
server{
listen50443;
sslon;
server_nameexample.com;
ssl_certificateD:\\nginx-1.19.1\\ssl_cert\\example-all.crt;
ssl_certificate_keyD:\\nginx-1.19.1\\ssl_cert\\example-key.txt;
ssl_session_cacheshared:SSL:1m;
ssl_session_timeout5m;
ssl_verify_clienton;
ssl_ocspon;
resolver172.16.1.251;
ssl_client_certificateD:\\nginx-1.19.1\\ssl_cert\\example-ca.crt;
#charset koi8-r;
#access_log logs/host.access.log main;
location/{
roothtml;
indexindex.htmlindex.htm;
}
}
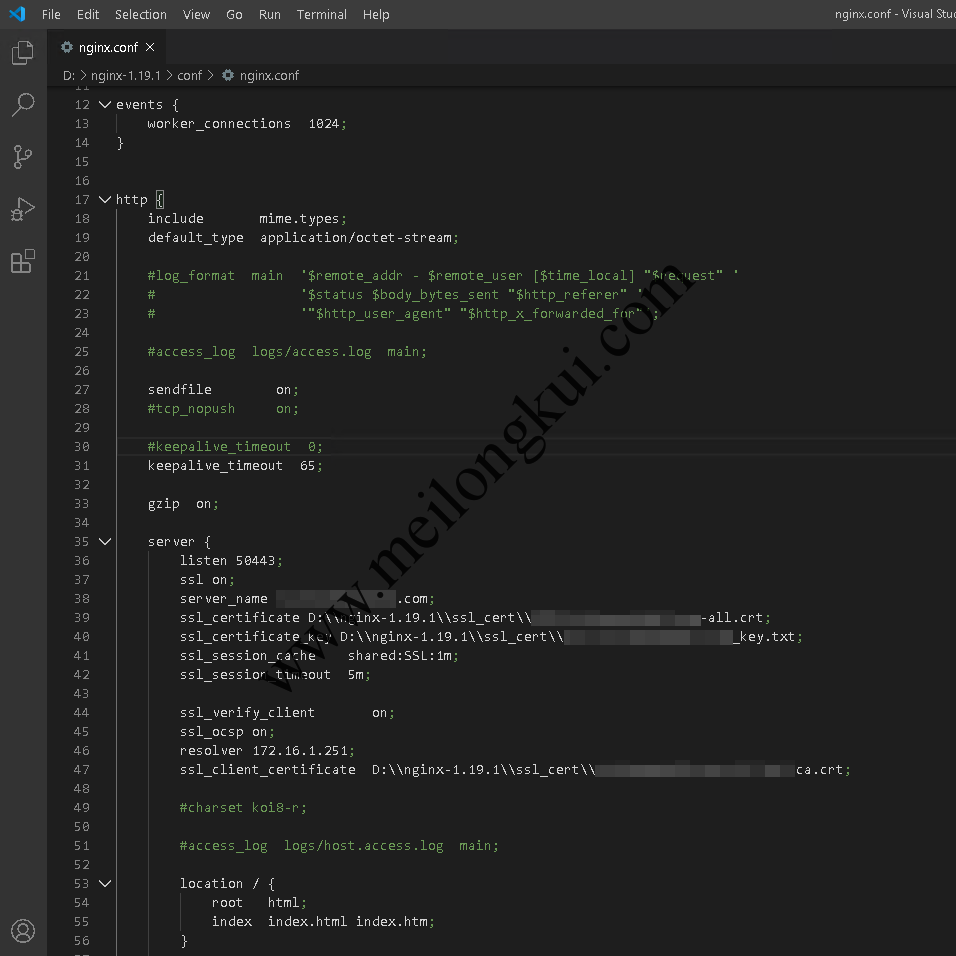
Nginx校验客户端证书配置(使用OCSP)
需要注意,其中的resolver用于:
Configures name servers used to resolve names of upstream servers into addresses
必须设置resolver,否则会报错,在error.log中可以看到,形如:
no resolver defined to resolve pki.example.com while requesting certificate status, responder: pki.example.com
1
noresolverdefinedtoresolvepki.example.comwhilerequestingcertificatestatus,responder:pki.example.com
另外,即便是启用了ssl_ocsp on,也必须通过ssl_client_certificate指定根证书,否则会报错:
no ssl_client_certificate for ssl_verify_client
1
nossl_client_certificateforssl_verify_client
这样,我们就可以观察到Nginx请求OCSP地址了(下面是OCSP地址请求失败时的报错):
WSASend() failed (10057: A request to send or receive data was disallowed because the socket is not connected and (when sending on a datagram socket using a sendto call) no address was supplied) while requesting certificate status, responder: pki.example.com, peer: 1**.***.***.***:80
1
WSASend()failed(10057:Arequesttosendorreceivedatawasdisallowedbecausethesocketisnotconnectedand(whensendingonadatagramsocketusingasendtocall)noaddresswassupplied)whilerequestingcertificatestatus,responder:pki.example.com,peer:1**.***.***.***:80
当对应的客户端证书被Revoke或OCSP访问失败时,会报错:

Nginx客户端证书校验失败
参考资料:
1、https://stackoverflow.com/questions/34102812/nginx-how-to-use-ocsp-to-verify-the-ssl-client-certificate
2、http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_ocs=-







 本文介绍了如何在Nginx 1.19.0+版本中启用OCSP验证客户端证书,详细配置步骤包括设置ssl_verify_client、ssl_ocsp、resolver和ssl_client_certificate等参数。在配置过程中,需要注意resolver的设置以避免解析错误,同时提供根证书以防止报错。当客户端证书被撤销或OCSP访问失败时,Nginx将报错。
本文介绍了如何在Nginx 1.19.0+版本中启用OCSP验证客户端证书,详细配置步骤包括设置ssl_verify_client、ssl_ocsp、resolver和ssl_client_certificate等参数。在配置过程中,需要注意resolver的设置以避免解析错误,同时提供根证书以防止报错。当客户端证书被撤销或OCSP访问失败时,Nginx将报错。
















 3238
3238

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








