前文介绍使用ingress结合traefik实现了入口的动静分离,本文将在前文基础上实现ingress的https配置。
为了简单且高效,建议应用容器化部署之后,https卸载在ingress这一级实现。通俗一点来说就是用户到ingress的连接走https协议,ingress到后端服务的连接走http协议。
我们对https的配置要求也比较简单,主要如下:
1、http自动重定向到https
2、https支持虚拟主机(TLS SNI)
一、初始环境准备
1、这里为了方便测试,把前文配置的网站动态部分路由规则都拿掉,仅保留静态部分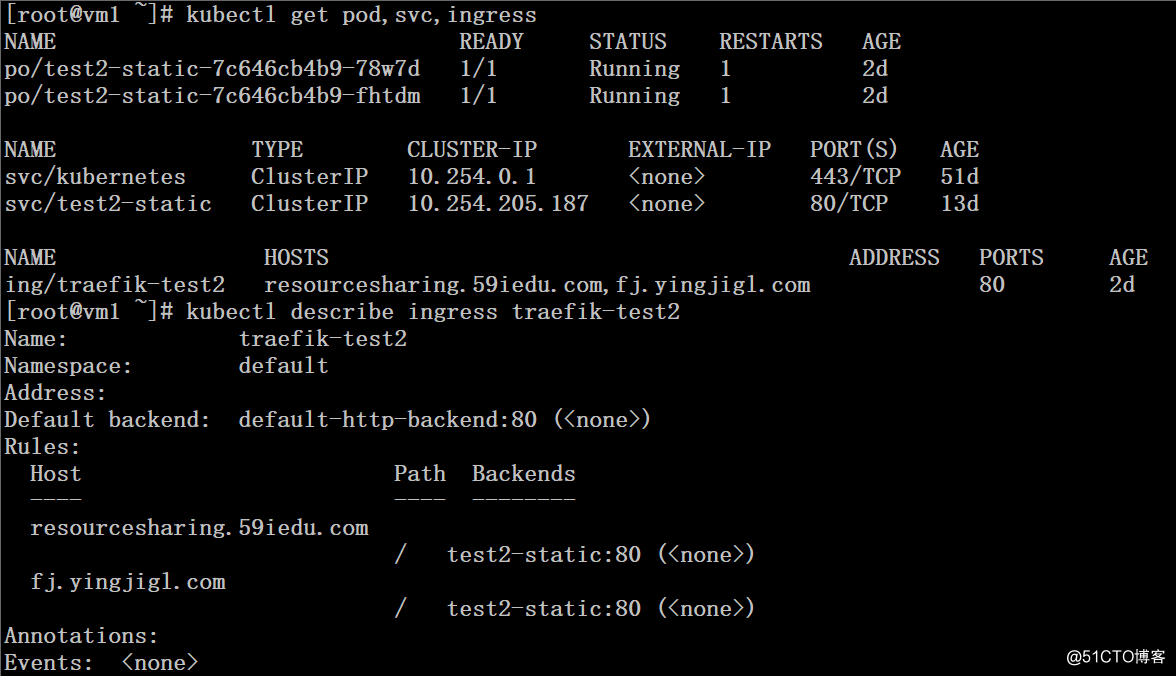
2、配置hosts解析记录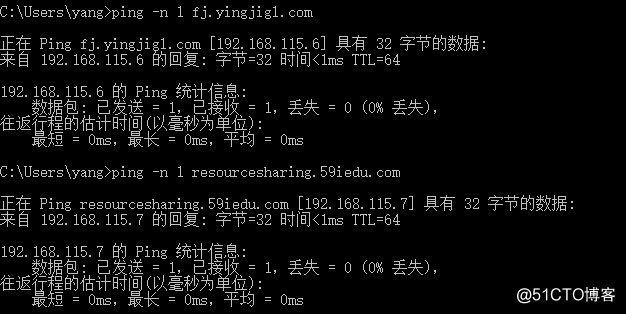
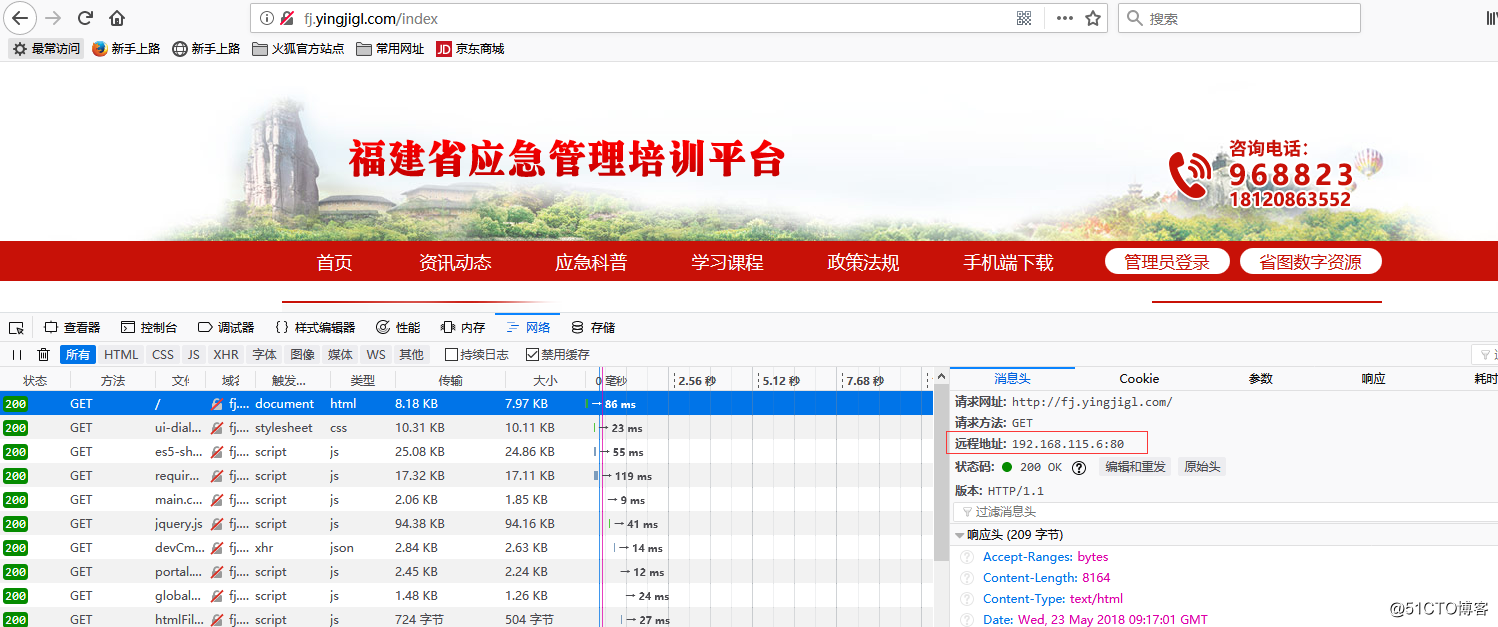
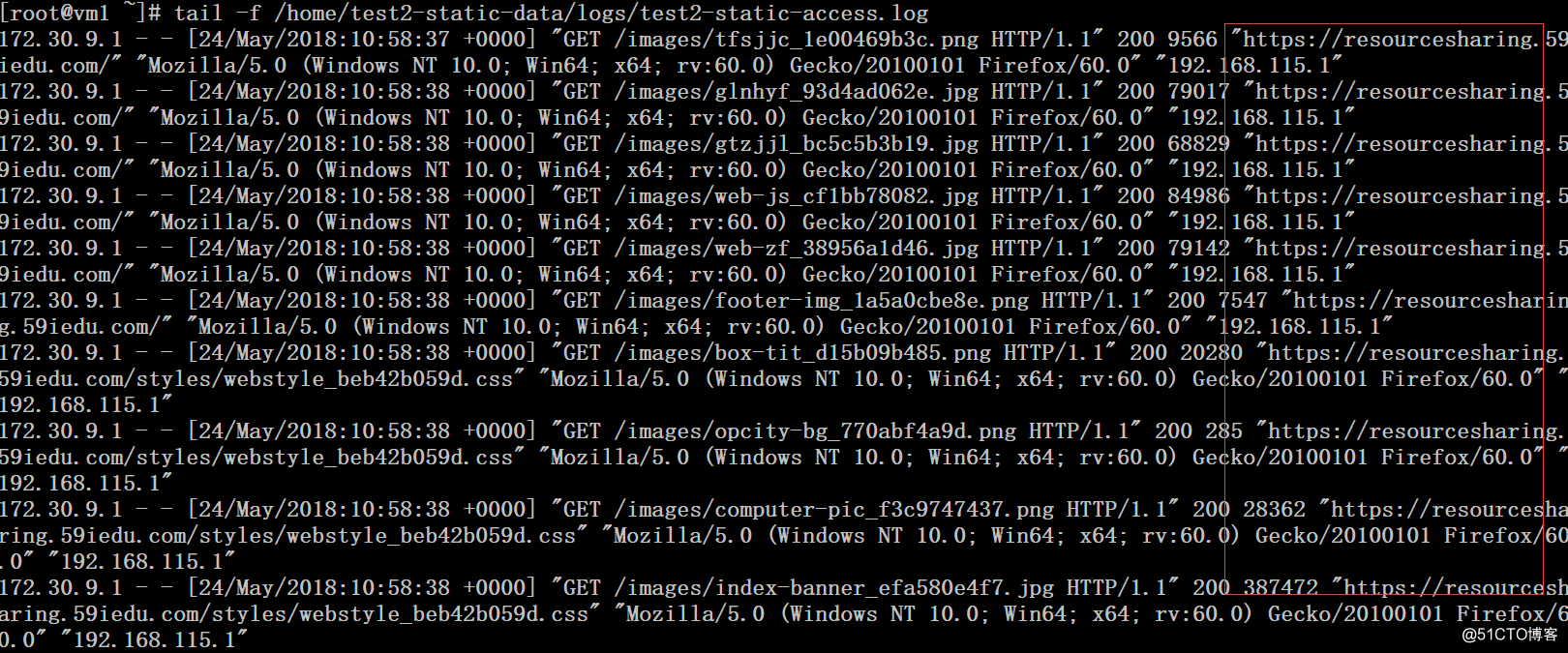
3、http访问测试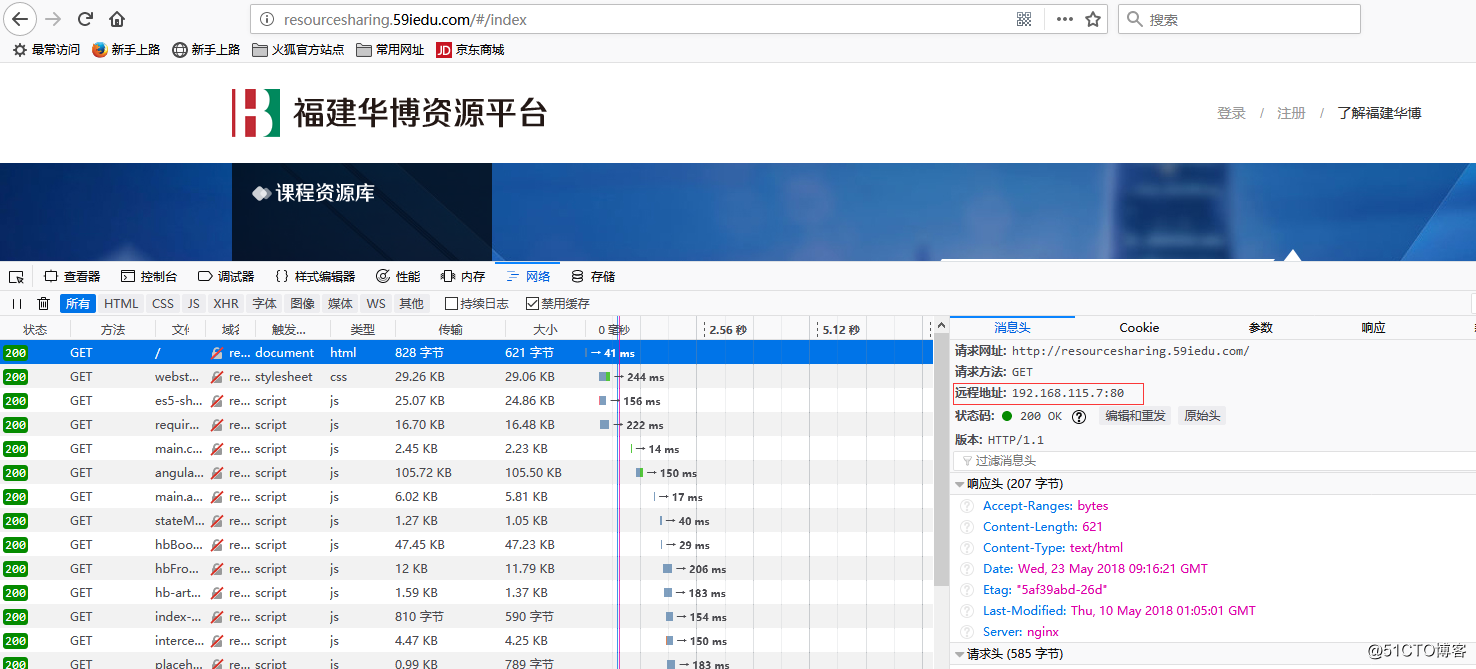
二、准备证书文件和配置文件
1、这里将两个站点的四个证书文件统一放到一个secret里面去维护
# kubectl create secret generic traefik-cert --from-file=star_59iedu_com.key \
--from-file=star_59iedu_com.pem \
--from-file=star_yingjigl_com.key \
--from-file=star_yingjigl_com.pem -n kube-system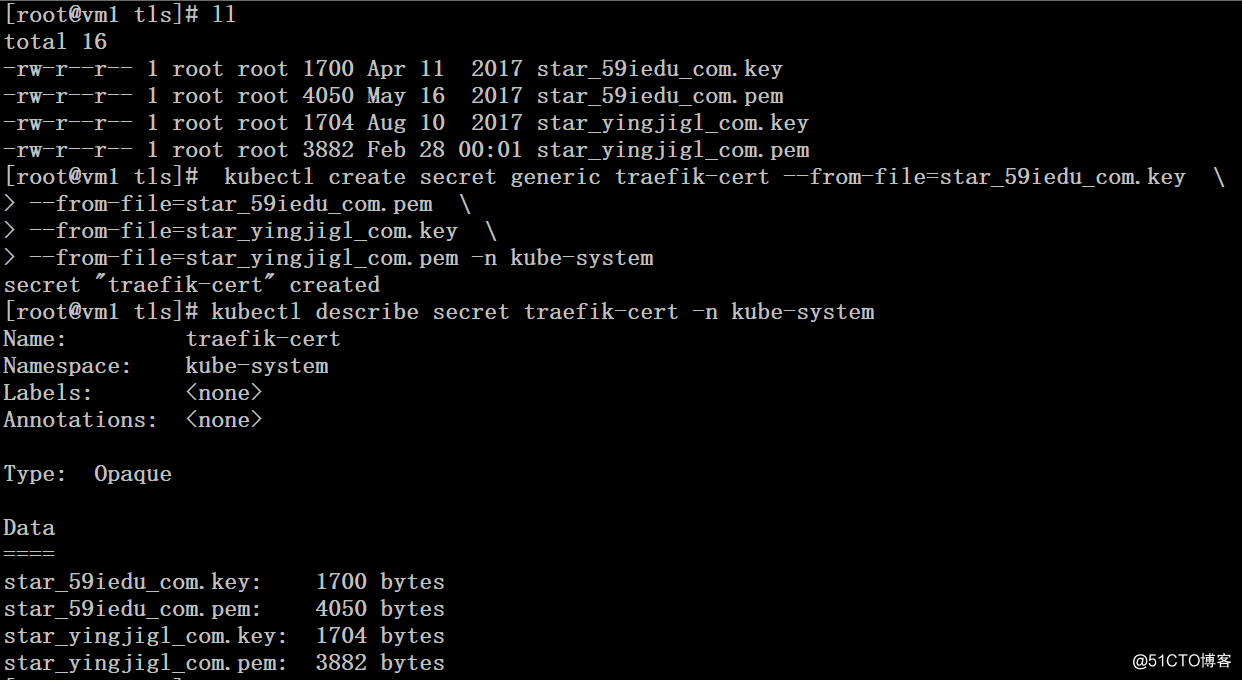
2、配置http重定向到https,同时支持多个https虚拟主机(TLS SNI)
# cat traefik.toml
defaultEntryPoints = ["http","https"]
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.http.redirect]
entryPoint = "https"
[entryPoints.https]
address = ":443"
[entryPoints.https.tls]
[[entryPoints.https.tls.certificates]]
CertFile = "/ssl/star_59iedu_com.pem"
KeyFile = "/ssl/star_59iedu_com.key"
[[entryPoints.https.tls.certificates]]
certFile = "/ssl/star_yingjigl_com.pem"
keyFile = "/ssl/star_yingjigl_com.key"# kubectl create configmap traefik-conf --from-file=traefik.toml -n kube-system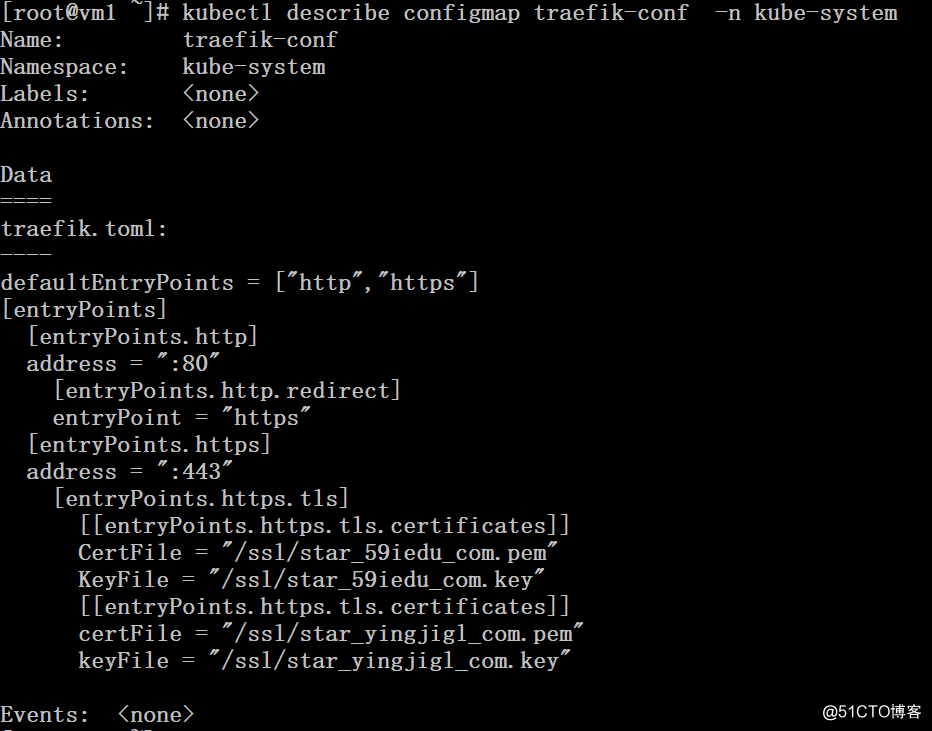
三、修改traefik配置文件
主要需要添加config和ssl volumes,其他的配置(例如:rabc、service、ingress等)保持不变,具体配置可参考前文,前文传送门:http://blog.51cto.com/ylw6006/2073718
# cat traefik-deployment.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller
namespace: kube-system
---
kind: Deployment
apiVersion: extensions/v1beta1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
replicas: 2
selector:
matchLabels:
k8s-app: traefik-ingress-lb
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
hostNetwork: true
nodeSelector:
traefik: proxy
terminationGracePeriodSeconds: 60
volumes:
- name: ssl
secret:
secretName: traefik-cert
- name: config
configMap:
name: traefik-conf
containers:
- image: traefik
name: traefik-ingress-lb
volumeMounts:
- mountPath: "/ssl"
name: "ssl"
- mountPath: "/config"
name: "config"
ports:
- name: web
containerPort: 80
hostPort: 80
- name: admin
containerPort: 8081
args:
- --configfile=/config/traefik.toml
- --web
- --web.address=:8081
- --kubernetes# kubectl apply -f traefik-deployment.yaml 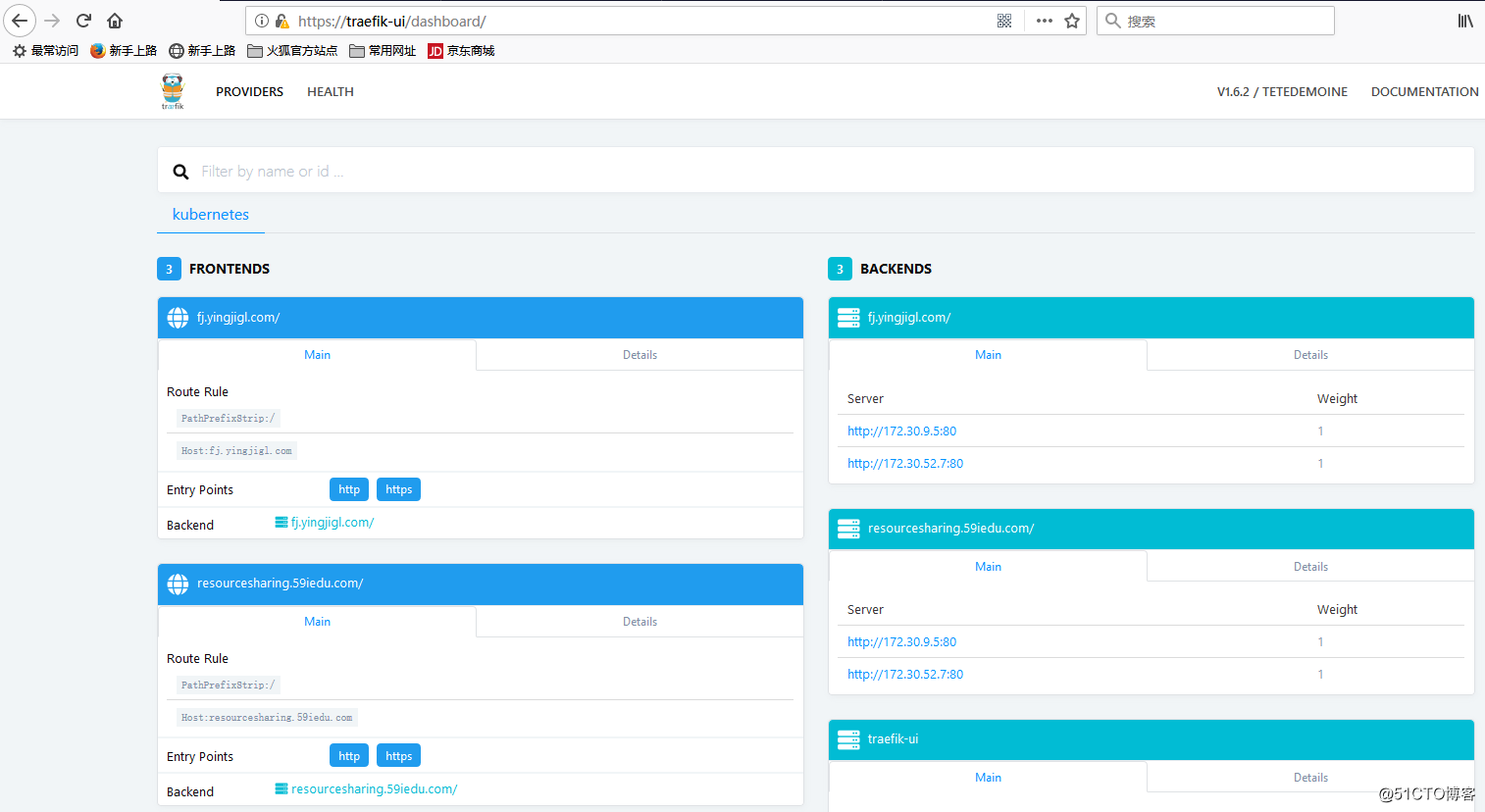
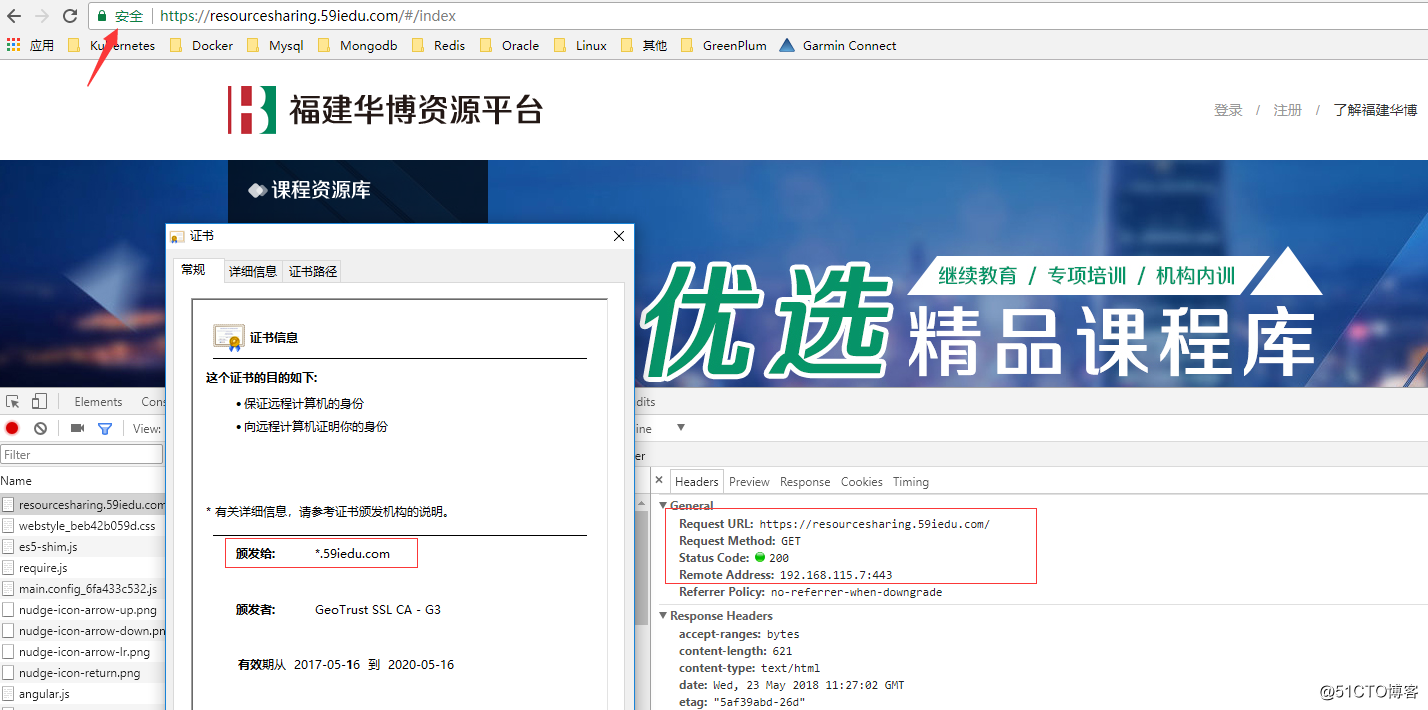
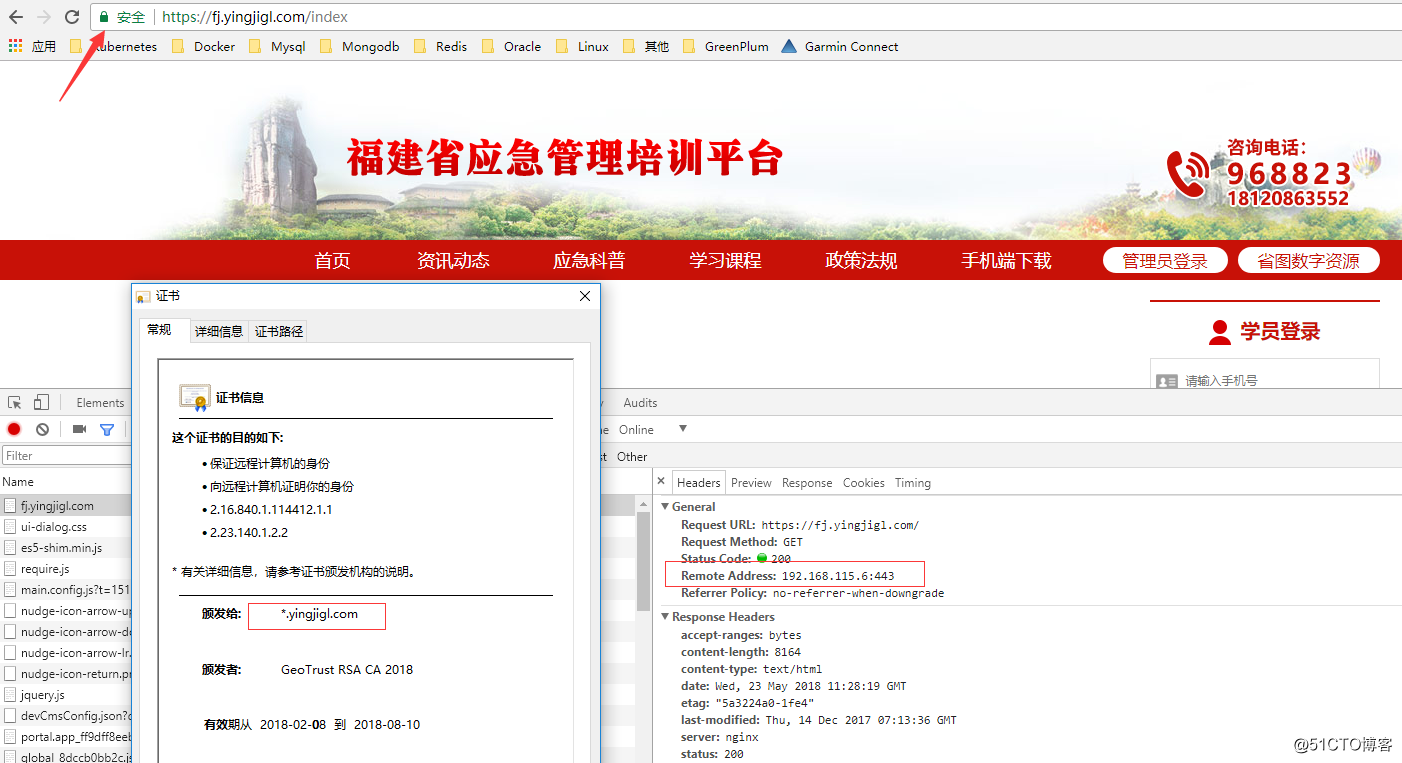
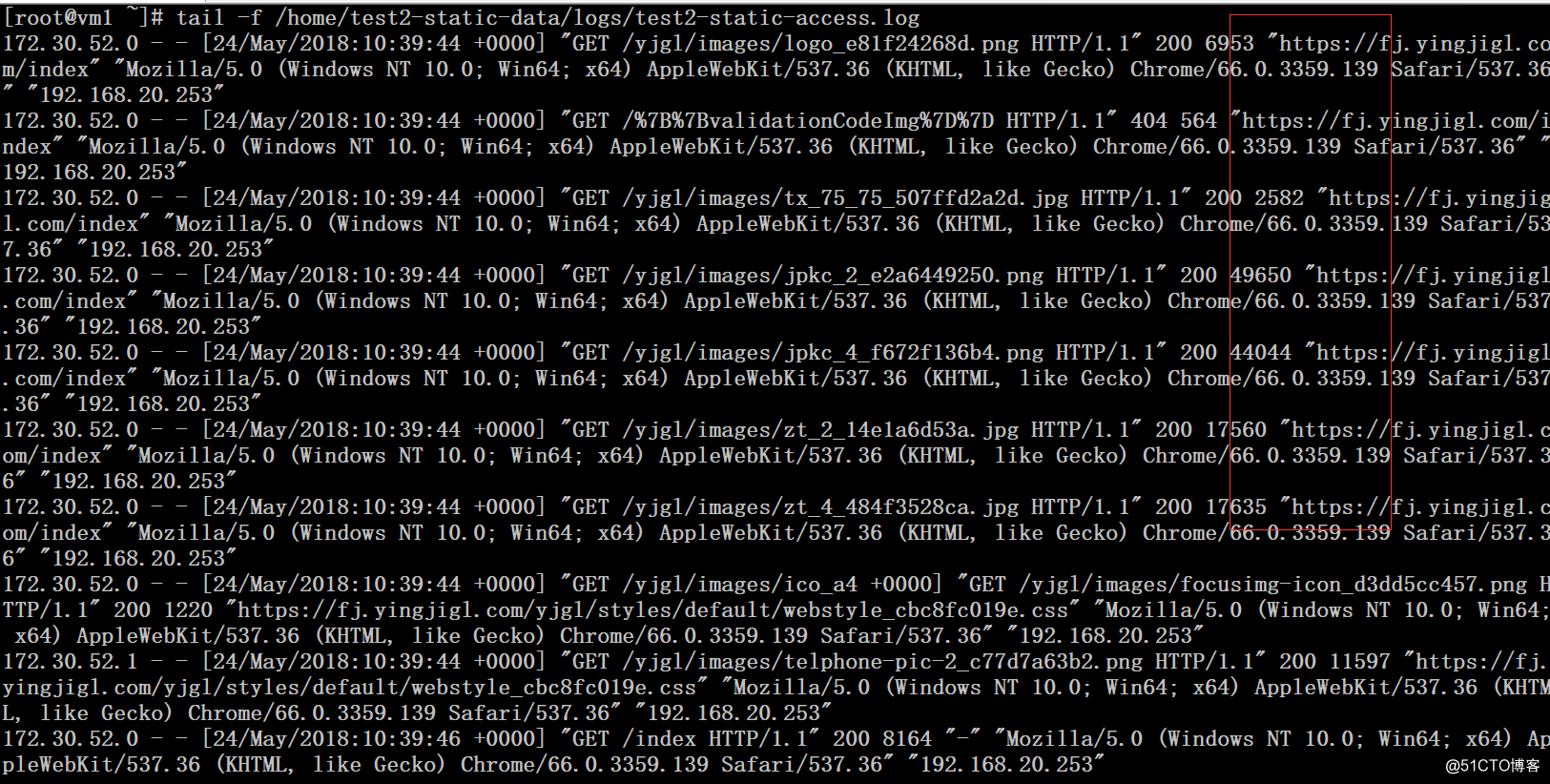
四、访问测试与验证
参考文档:
其他的需求,例如gzip压缩,tls版本和加密算法,rewrite重定向等配置也可以参考此文档
https://docs.traefik.io/configuration/entrypoints/#basic
五、其他需求
1、 使用一个统一的入口地址。
2、 默认同时支持http和https方式访问。
3、 根据实际的情况和要求来配置http访问请求重定向到https。
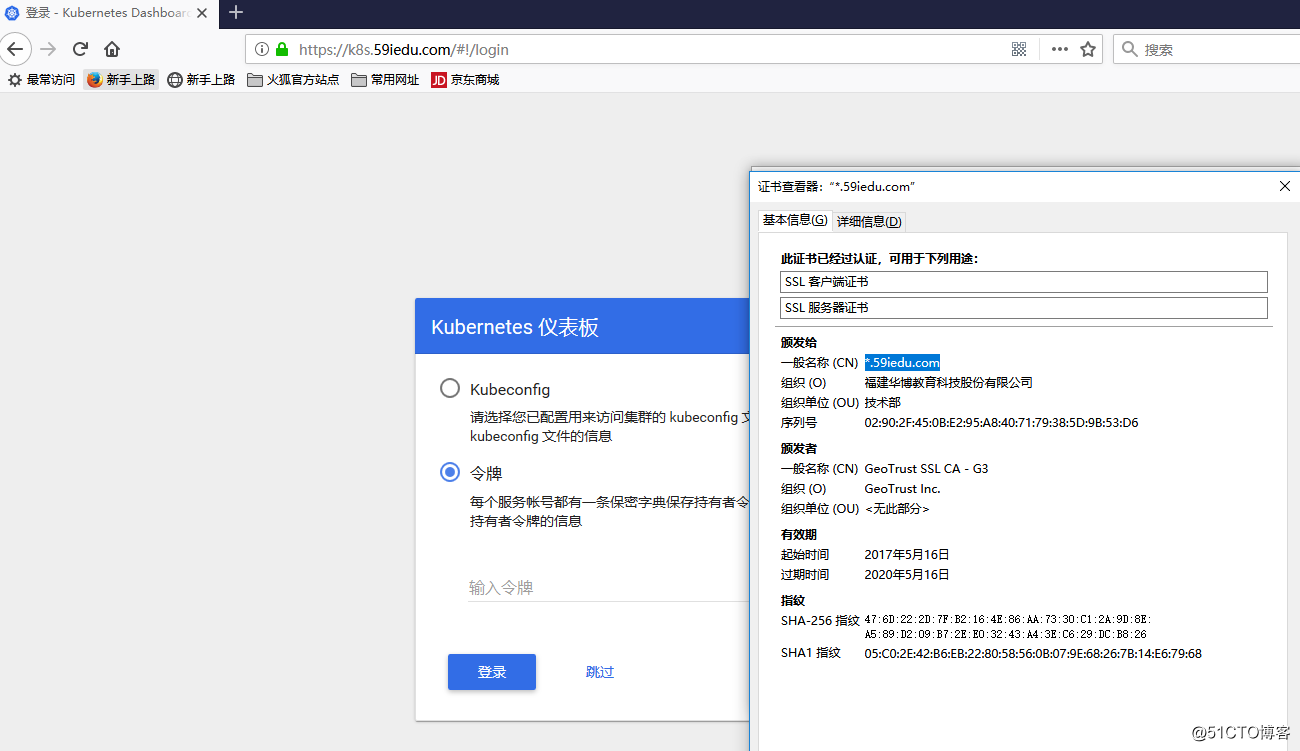
4、 兼容后端https服务(这里以dashboard为例)
# cat traefik.toml
insecureSkipVerify = true
defaultEntryPoints = ["http","https"]
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.http.redirect]
regex = "^http://k8s.59iedu.com/(.*)"
replacement = "https://k8s.59iedu.com/$1"
[entryPoints.https]
address = ":443"
[entryPoints.https.tls]
[[entryPoints.https.tls.certificates]]
CertFile = "/ssl/star_59iedu_com.pem"
KeyFile = "/ssl/star_59iedu_com.key"
[[entryPoints.https.tls.certificates]]
certFile = "/ssl/star_yingjigl_com.pem"
keyFile = "/ssl/star_yingjigl_com.key"
[[entryPoints.https.tls.certificates]]
certFile = "/ssl/star_huilearning_com.pem"
keyFile = "/ssl/star_huilearning_com.key"# cat dashboard-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubernetes-dashboard
namespace: kube-system
annotations:
ingress.kubernetes.io/ssl-passthrough: "true"
spec:
rules:
- host: k8s.59iedu.com
http:
paths:
- path: /
backend:
serviceName: kubernetes-dashboard
servicePort: 443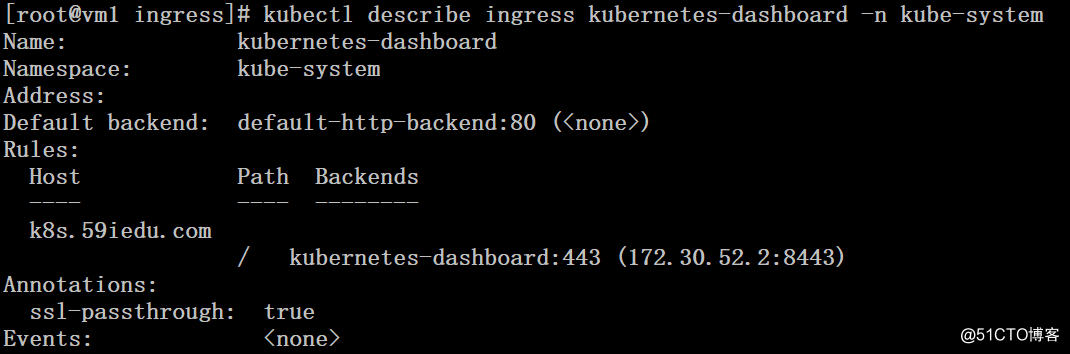







 本文详细介绍如何在Kubernetes环境中使用Traefik实现Ingress的HTTPS配置,包括证书管理、HTTP到HTTPS重定向及虚拟主机支持等内容。
本文详细介绍如何在Kubernetes环境中使用Traefik实现Ingress的HTTPS配置,包括证书管理、HTTP到HTTPS重定向及虚拟主机支持等内容。

















 91
91

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








