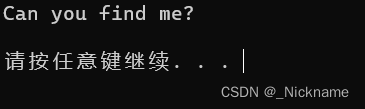
运行之后是这个东西
我们直接IDA暴力打开
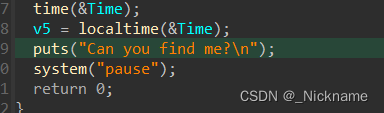
结果main函数啥也不是
(看其他人的wp知道了照que函数)
我也不知道咋找的,可能真要硬找吧
int ques()
{
int v0; // edx
int result; // eax
int v2[50]; // [esp+20h] [ebp-128h] BYREF
int v3; // [esp+E8h] [ebp-60h]
int v4[10]; // [esp+ECh] [ebp-5Ch]
int j; // [esp+114h] [ebp-34h]
__int64 v6; // [esp+118h] [ebp-30h]
int v7; // [esp+124h] [ebp-24h]
int v8; // [esp+128h] [ebp-20h]
int i; // [esp+12Ch] [ebp-1Ch]
v3 = 2147122737;
v4[0] = 140540;
v4[1] = -2008399303;
v4[2] = 141956;
v4[3] = 139457077;
v4[4] = 262023;
v4[5] = -2008923597;
v4[6] = 143749;
v4[7] = 2118271985;
v4[8] = 143868;
for ( i = 0; i <= 4; ++i )
{
memset(v2, 0, sizeof(v2));
v8 = 0;
v7 = 0;
v0 = v4[2 * i];
LODWORD(v6) = v4[2 * i - 1];
HIDWORD(v6) = v0;
while ( v6 > 0 )
{
v2[v8++] = v6 % 2;
v6 /= 2i64;
}
for ( j = 50; j >= 0; --j )
{
if ( v2[j] )
{
if ( v2[j] == 1 )
{
putchar(42);
++v7;
}
}
else
{
putchar(32);
++v7;
}
if ( !(v7 % 5) )
putchar(32);
}
result = putchar(10);
}
return result;
}
这是que函数,但是你可以发现没有任何调用
que函数里面有putchar
就是输出函数
好嘛那
我直接爆改
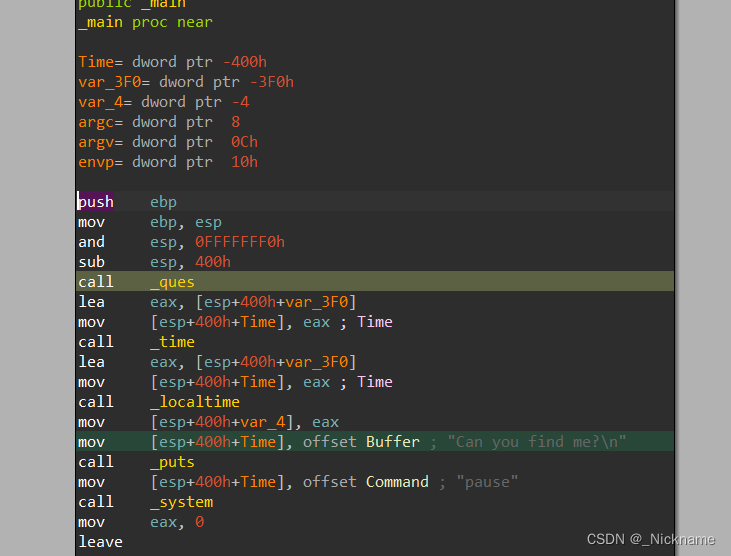
开局就调用que函数
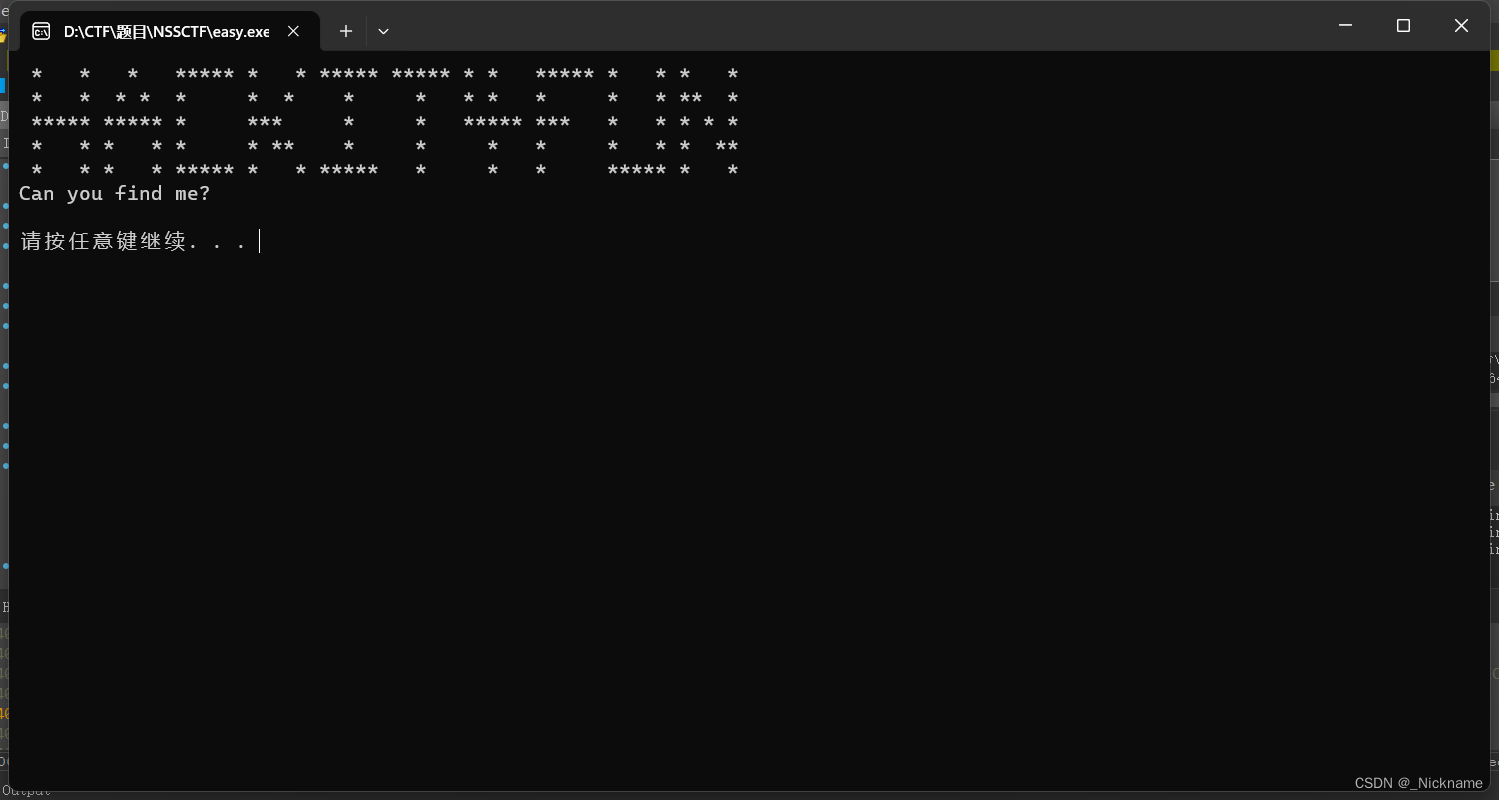
然后就...
下班拉!





 文章讲述了作者使用IDA进行代码逆向分析,发现que函数中负责字符输出,没有外部调用。作者随后直接修改代码,初始化时调用que函数,展示了在IT技术中的调试和代码动态修改过程。
文章讲述了作者使用IDA进行代码逆向分析,发现que函数中负责字符输出,没有外部调用。作者随后直接修改代码,初始化时调用que函数,展示了在IT技术中的调试和代码动态修改过程。

















 864
864

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










