一.需求描述:
1.1 需求背景描述
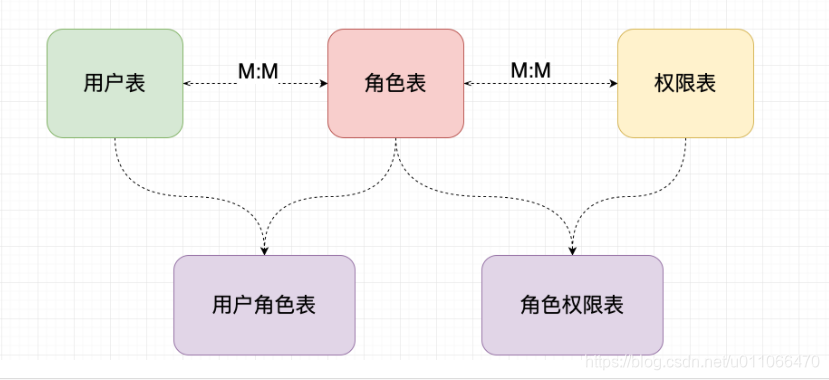
1.新建权限管理的那5张表,如下图:
新建两个用户:一个admin用户的角色为admin,ljf用户的角色为user。
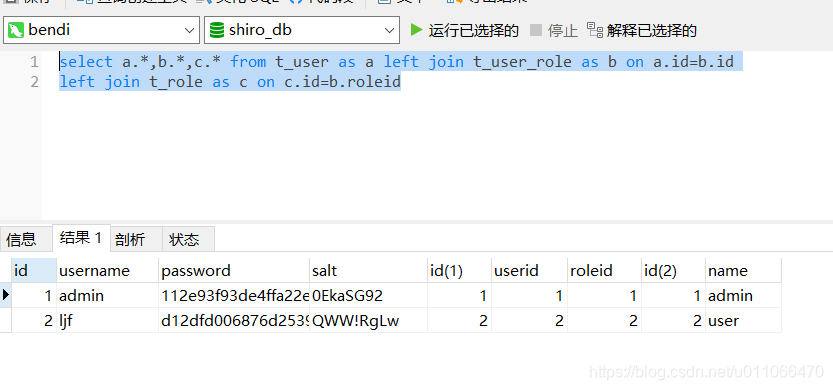
其中,admin角色能访问到:订单管理、用户管理、系统管理、日志管理。而用户角色只能够访问到订单管理
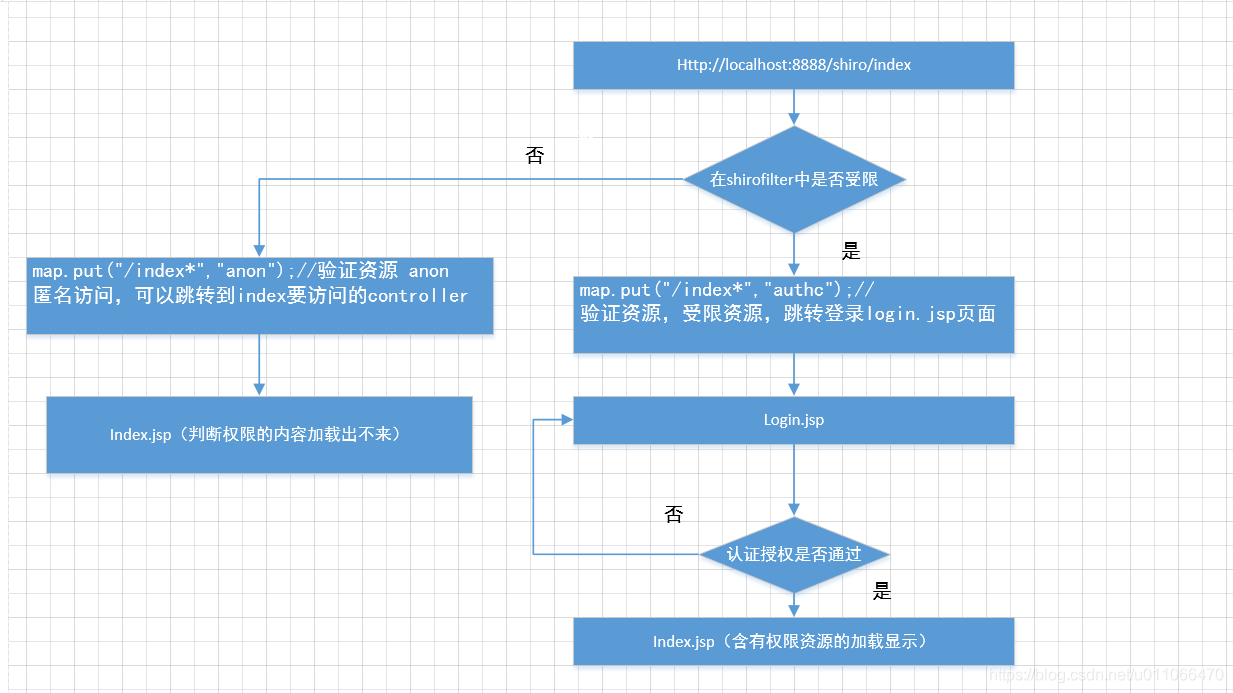
1.2 本案例的执行流程
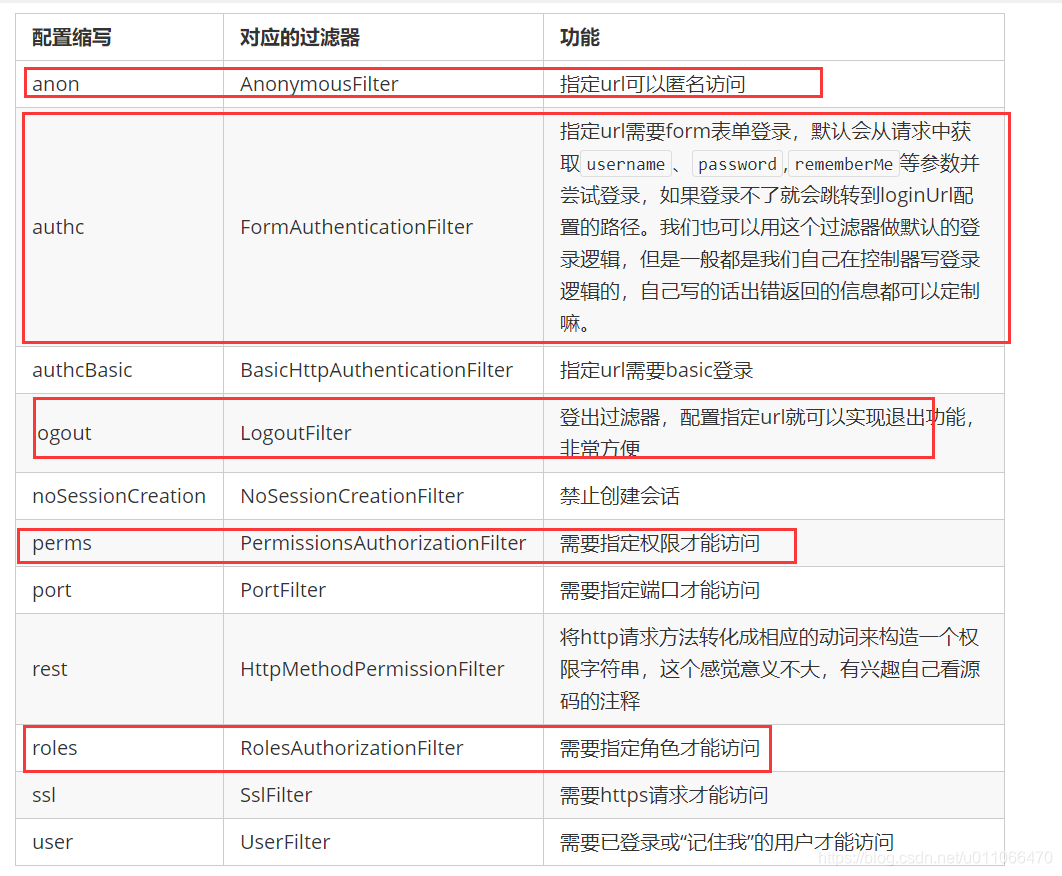
1.3 常见的过滤器
1.4 shiro的授权方式
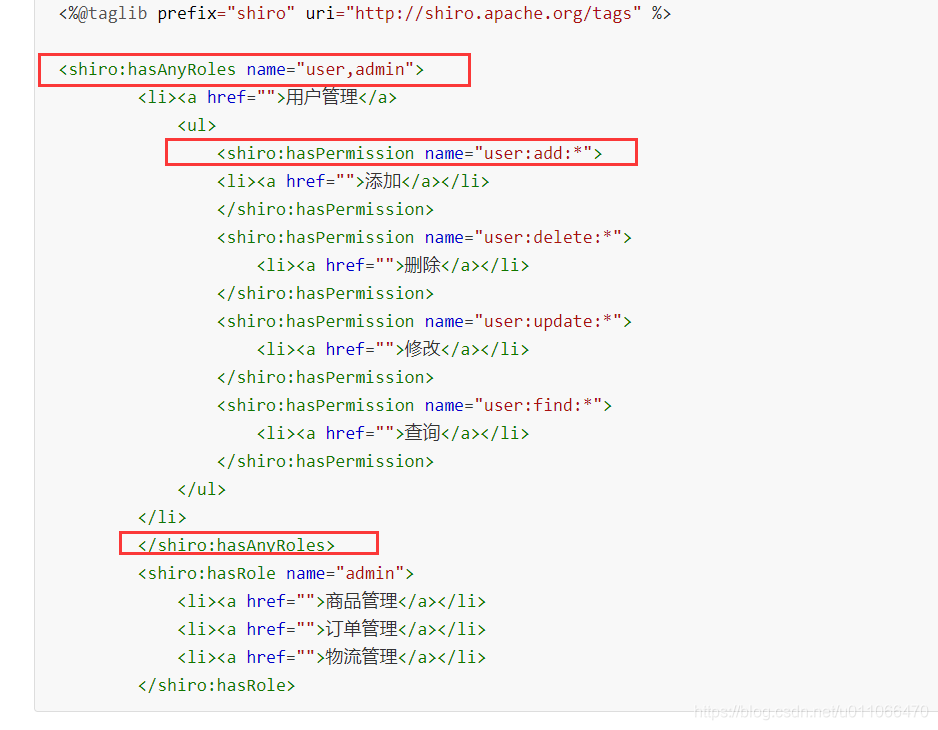
1.4.1 标签式
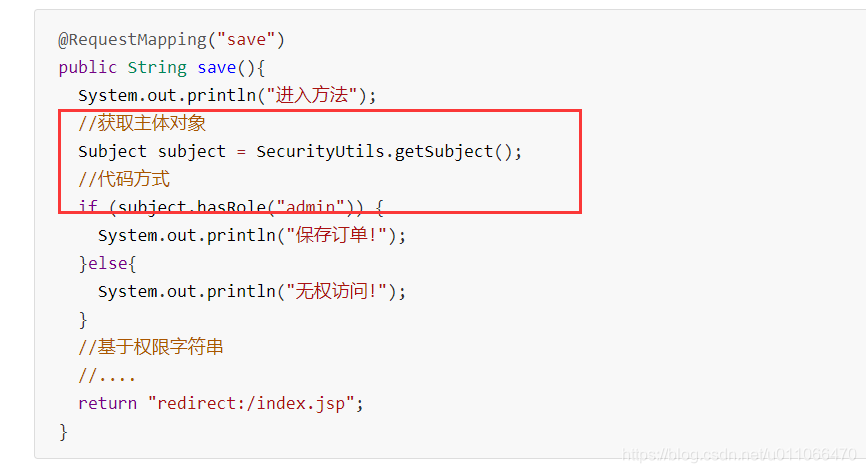
1.4.2 编程式
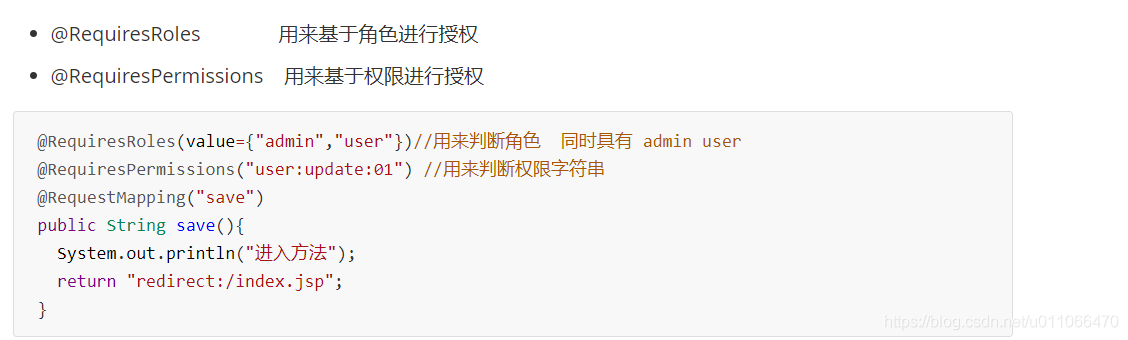
1.4.3 注解式
二.代码的实现
2.1 pom文件
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.3.4.RELEASE</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.shiro.ljf.demo</groupId>
<artifactId>spt-shiro-demo</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>spt-shiro-demo</name>
<description>Demo project for Spring Boot</description>
<properties>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-devtools</artifactId>
<scope>runtime</scope>
<optional>true</optional>
</dependency>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
<optional>true</optional>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
<exclusions>
<exclusion>
<groupId>org.junit.vintage</groupId>
<artifactId>junit-vintage-engine</artifactId>
</exclusion>
</exclusions>
</dependency>
<!-- shiro 配置文件-->
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-spring-boot-starter</artifactId>
<version>1.5.3</version>
</dependency>
<!--引入jsp解析依赖-->
<dependency>
<groupId>org.apache.tomcat.embed</groupId>
<artifactId>tomcat-embed-jasper</artifactId>
</dependency>
<dependency>
<groupId>jstl</groupId>
<artifactId>jstl</artifactId>
<version>1.2</version>
</dependency>
<!--mybatis相关依赖-->
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>2.1.2</version>
</dependency>
<!--mysql-->
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<version>5.1.38</version>
</dependency>
<!--druid-->
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid</artifactId>
<version>1.1.19</version>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
2.2 application配置文件
server.port=8888
server.servlet.context-path=/shiro
spring.application.name=shiro
boot_jsp_shiro.dao=debug
spring.mvc.view.prefix=/
spring.mvc.view.suffix=.jsp
#新增配置
spring.datasource.type=com.alibaba.druid.pool.DruidDataSource
spring.datasource.driver-class-name=com.mysql.jdbc.Driver
spring.datasource.url=jdbc:mysql://localhost:3306/shiro_db?characterEncoding=UTF-8
spring.datasource.username=root
spring.datasource.password=root
#mybaits的配置
mybatis.type-aliases-package=com.shiro.ljf.demo.sptshirodemo.entity
mybatis.mapper-locations=classpath:mapper/*.xml
2.3 新建实体类
2.3.1 ROLE实体类:
package com.shiro.ljf.demo.sptshirodemo.entity;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.NoArgsConstructor;
import lombok.experimental.Accessors;
import java.io.Serializable;
import java.util.List;
/**
* @ClassName: Role
* @Description: TODO
* @Author: liujianfu
* @Date: 2020/10/30 22:42:08
* @Version: V1.0
**/
@Data
@Accessors(chain = true)
@AllArgsConstructor
@NoArgsConstructor
public class Role implements Serializable {
private String id;
private String name;
//定义权限的集合
private List<MenuPerms> perms;
}
2.3.2 User实体类:
package com.shiro.ljf.demo.sptshirodemo.entity;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.NoArgsConstructor;
import lombok.experimental.Accessors;
import java.io.Serializable;
import java.util.List;
/**
* @ClassName: User
* @Description: TODO
* @Author: liujianfu
* @Date: 2020/10/29 22:57:35
* @Version: V1.0
*
* @AllArgsConstructor:它是lombok中的注解,作用在类上;使用后添加一个构造函数,该构造函数含有所有已声明字段属性参数
* @Accessors(chain = true) 开启链式编程
* @NoArgsConstructor:无参构造函数
*
*
**/
@Data
@Accessors(chain = true)
@AllArgsConstructor
@NoArgsConstructor
public class User implements Serializable {
private String id;
private String username;
private String password;
private String salt;
//定义角色集合
private List<Role> roles;
}
2.3.3 MenuPerms实体类:
package com.shiro.ljf.demo.sptshirodemo.entity;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.NoArgsConstructor;
import lombok.experimental.Accessors;
import java.io.Serializable;
/**
* @ClassName: MenuPerms
* @Description: TODO
* @Author: liujianfu
* @Date: 2020/11/04 22:36:19
* @Version: V1.0
**/
@Data
@Accessors(chain = true)
@AllArgsConstructor
@NoArgsConstructor
public class MenuPerms implements Serializable {
private String id;
private String name;
private String url;
}
2.4 dao层:
package com.shiro.ljf.demo.sptshirodemo.dao;
import com.shiro.ljf.demo.sptshirodemo.entity.User;
import org.apache.ibatis.annotations.Mapper;
@Mapper
public interface UserDao {
//注册数据
public void addData(User user);
//根据用户名查询用户
public User findByUserName(String userName);
//根据用户名查询所有角色
User findRolesByUserName(String username);
}
2.5 mapper:
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN" "http://mybatis.org/dtd/mybatis-3-mapper.dtd" >
<mapper namespace="com.shiro.ljf.demo.sptshirodemo.dao.UserDao" >
<!--添加数据 -->
<insert id="addData" parameterType="com.shiro.ljf.demo.sptshirodemo.entity.User">
insert into t_user values(#{id},#{username},#{password},#{salt})
</insert>
<!-- 查找用户名 -->
<select id="findByUserName" parameterType="String" resultType="com.shiro.ljf.demo.sptshirodemo.entity.User">
select id,username,password,salt from t_user
where username = #{username}
</select>
<!--通过用户查询角色 -->
<resultMap id="userMap" type="com.shiro.ljf.demo.sptshirodemo.entity.User">
<id column="uid" property="id"/>
<result column="username" property="username"/>
<!--角色信息-->
<collection property="roles" javaType="list" ofType="Role">
<id column="id" property="id"/>
<!-- rname 对应下面 findRolesByUserName的r.NAME rname-->
<result column="rname" property="name"/>
</collection>
</resultMap>
<!--通过用户查询角色 -->
<select id="findRolesByUserName" parameterType="String" resultMap="userMap">
SELECT u.id uid,u.username,r.id,r.NAME rname
FROM t_user u
LEFT JOIN t_user_role ur
ON u.id=ur.userid
LEFT JOIN t_role r
ON ur.roleid=r.id
WHERE u.username=#{username}
</select>
</mapper>
2.6 server层:
package com.shiro.ljf.demo.sptshirodemo.service;
import com.shiro.ljf.demo.sptshirodemo.entity.User;
public interface UserService {
//注册用户方法
void register(User user);
//查找用户名
public User findByUserName(String username);
//根据用户名查询所有角色
User findRolesByUserName(String username);
}
@Service("userService")
public class UserServiceImpl implements UserService {
@Autowired
private UserDao userDao;
@Override
public User findByUserName(String username) {
return userDao.findByUserName(username);
}
/**
* @author liujianfu
*根据用户名查询所有角色
* @date 2020/11/7 20:18
* @param
* @return
@Override
**/
public User findRolesByUserName(String username) {
return userDao.findRolesByUserName(username);
}
}
2.7 controller层:
package com.shiro.ljf.demo.sptshirodemo.controller;
import com.shiro.ljf.demo.sptshirodemo.entity.User;
import com.shiro.ljf.demo.sptshirodemo.service.UserService;
import org.apache.shiro.SecurityUtils;
import org.apache.shiro.authc.IncorrectCredentialsException;
import org.apache.shiro.authc.UnknownAccountException;
import org.apache.shiro.authc.UsernamePasswordToken;
import org.apache.shiro.subject.Subject;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Controller;
import org.springframework.ui.Model;
import org.springframework.web.bind.annotation.RequestMapping;
import javax.servlet.http.HttpSession;
/**
* @ClassName: UserLoginController
* @Description: TODO
* @Author: liujianfu
* @Date: 2020/10/29 08:13:50
* @Version: V1.0
**/
@Controller
@RequestMapping("user")
public class UserLoginController {
@Autowired
private UserService userService;
/**
* 用来处理身份认证
*
* @param username
* @param password
* @return
*/
@RequestMapping("login")
public String login(String username, String password, String code, HttpSession session, Model model) {
try {
System.out.println("进入login的登录方法====");
//获取主体对象
Subject subject = SecurityUtils.getSubject();
//当执行这个login的方法,就会触发在自定义的CustomerRealm的AuthenticationInfo的方法
subject.login(new UsernamePasswordToken(username, password));//!!!!
return "redirect:/index.jsp";
} catch (UnknownAccountException e) {
e.printStackTrace();
System.out.println("用户名错误!");
} catch (IncorrectCredentialsException e) {
e.printStackTrace();
System.out.println("密码错误!");
System.out.println("密码错误!");
model.addAttribute("error","密码错误");
return "login";
}catch (Exception e){
e.printStackTrace();
System.out.println(e.getMessage());
}
System.out.println("登录页面");
return "redirect:/login.jsp";
}
/**
* 退出登录
*/
@RequestMapping("logout")
public String logout() {
Subject subject = SecurityUtils.getSubject();
subject.logout();//退出用户
return "redirect:/login.jsp";
}
/**
* 用户注册
*/
@RequestMapping("register")
public String register(User user) {
try {
System.out.println("进入userController 层了:!!!!!");
if(user!=null&&user.getPassword()!=null){
System.out.println("user的信息不为null:");
userService.register(user);
return "redirect:/login.jsp";
}
return "redirect:/register.jsp";
}catch (Exception e){
e.printStackTrace();
return "redirect:/register.jsp";
}
}
}
2.10 shiroconfig
package com.shiro.ljf.demo.sptshirodemo.config;
import com.shiro.ljf.demo.sptshirodemo.shiro.CustomerRealm;
import org.apache.shiro.authc.credential.HashedCredentialsMatcher;
import org.apache.shiro.realm.Realm;
import org.apache.shiro.spring.web.ShiroFilterFactoryBean;
import org.apache.shiro.web.mgt.DefaultWebSecurityManager;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import java.util.LinkedHashMap;
import java.util.Map;
/**
* @ClassName: ShiroConfig
* @Description: TODO
* @Author: liujianfu
* @Date: 2020/10/28 15:11:16
* @Version: V1.0
**/
@Configuration
public class ShiroConfig {
//1.创建shiroFilter :负责拦截所有请求
@Bean
public ShiroFilterFactoryBean getShiroFilterFactoryBean(@Qualifier("securityManager") DefaultWebSecurityManager securityManager){
System.out.println("step3:>>进入过滤器");
//创建shiro的filter,配置shiroFilterFactoryBean
ShiroFilterFactoryBean shiroFilterFactoryBean = new ShiroFilterFactoryBean();
//注入安全管理器
shiroFilterFactoryBean.setSecurityManager(securityManager);
//设置过滤资源
Map<String,String> map = new LinkedHashMap<>();
//map.put("/**","authc");
/** 代表拦截项目中一切资源 authc 代表shiro中的一个filter的别名,详细内容看文档的shirofilter列表**/
//map.put("/index.jsp","authc");//验证资源
//map.put("/index*","anon");//验证资源 anon 匿名访问,可以跳转到index要访问的controller
//设置公共资源 ,anno过滤器,设置访问公共资源,放在前面
map.put("/user/login","anon");
map.put("/user/register","anon");//anon 设置为公共资源 放行资源放在前面
map.put("/register.jsp","anon");//anon 设置为公共资源 放行资源放在前面
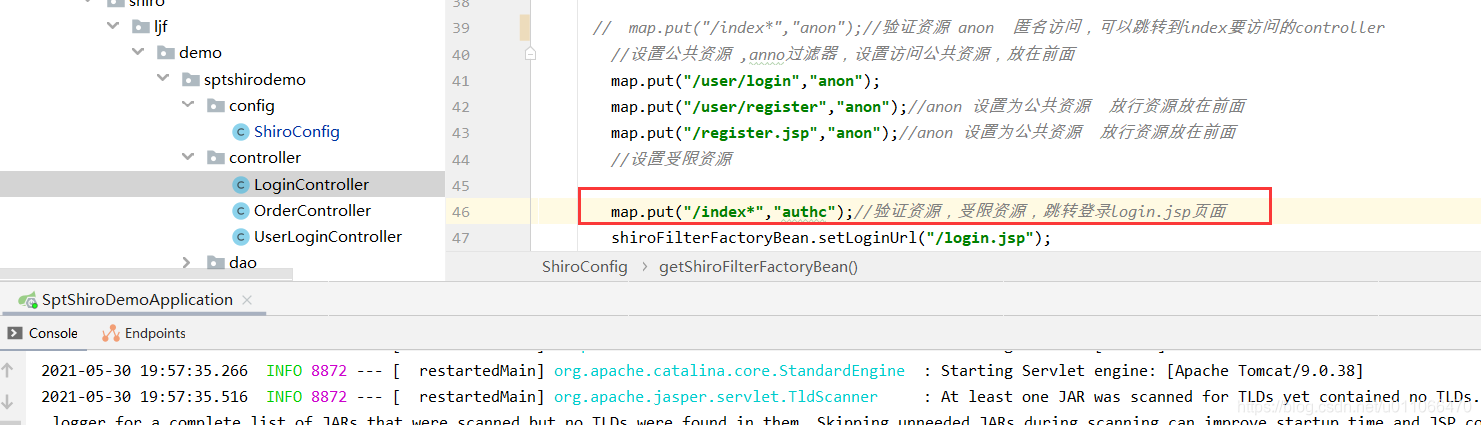
//设置受限资源
map.put("/index*","authc");//验证资源,受限资源,跳转登录login.jsp页面
shiroFilterFactoryBean.setLoginUrl("/login.jsp");
shiroFilterFactoryBean.setFilterChainDefinitionMap(map);
return shiroFilterFactoryBean;
}
//2.创建安全管理器
@Bean(name="securityManager")
public DefaultWebSecurityManager getDefaultWebSecurityManager(@Qualifier("userRealm") Realm realm){
System.out.println("step2:>> 进入securityManager方法");
DefaultWebSecurityManager defaultWebSecurityManager = new DefaultWebSecurityManager();
//给安全管理器设置
defaultWebSecurityManager.setRealm(realm);
return defaultWebSecurityManager;
}
//3.创建自定义realm
@Bean(name="userRealm")
public Realm getRealm(){
System.out.println("step1:>>进入realm方法");
//return new CustomerRealm();
CustomerRealm customerRealm = new CustomerRealm();
//修改凭证校验匹配器
HashedCredentialsMatcher credentialsMatcher = new HashedCredentialsMatcher();
//设置加密算法为md5
credentialsMatcher.setHashAlgorithmName("MD5");
//设置散列次数
credentialsMatcher.setHashIterations(1024);
customerRealm.setCredentialsMatcher(credentialsMatcher);
return customerRealm;
}
}
2.11 自定义授权方法:
package com.shiro.ljf.demo.sptshirodemo.shiro;
import com.shiro.ljf.demo.sptshirodemo.entity.User;
import com.shiro.ljf.demo.sptshirodemo.service.UserService;
import com.shiro.ljf.demo.sptshirodemo.utils.ApplicationContextUtils;
import com.shiro.ljf.demo.sptshirodemo.utils.MyByteSource;
import org.apache.shiro.authc.AuthenticationException;
import org.apache.shiro.authc.AuthenticationInfo;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.authc.SimpleAuthenticationInfo;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.authz.SimpleAuthorizationInfo;
import org.apache.shiro.realm.AuthorizingRealm;
import org.apache.shiro.subject.PrincipalCollection;
import org.apache.shiro.util.CollectionUtils;
import org.springframework.util.ObjectUtils;
/**
* @ClassName: CustomerRealm
* @Description: TODO
* @Author: liujianfu
* @Date: 2020/10/28 15:17:48
* @Version: V1.0
**/
public class CustomerRealm extends AuthorizingRealm {
/**
* @author liujianfu
* @description 授权方法
* @date 2020/10/28 16:54
* @return org.apache.shiro.authz.AuthorizationInfo
*/
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principalCollection) {
System.out.println("进入授权部分======:");
//获取身份信息
String primaryPrincipal = (String) principalCollection.getPrimaryPrincipal();
System.out.println("调用授权验证: "+primaryPrincipal);
/**
if("ljf".equals(primaryPrincipal)){//登录的用户ljf,具有以下角色
//角色的授权
SimpleAuthorizationInfo simpleAuthorizationInfo = new SimpleAuthorizationInfo();
simpleAuthorizationInfo.addRole("admin");
simpleAuthorizationInfo.addRole("guest");
//权限字符串的授权
simpleAuthorizationInfo.addStringPermission("haha:add:01");
simpleAuthorizationInfo.addStringPermission("haha:update:02");
return simpleAuthorizationInfo;
}
**/
//根据主身份信息获取角色 和 权限信息
UserService userService = (UserService) ApplicationContextUtils.getBean("userService");
User user = userService.findRolesByUserName(primaryPrincipal);
//授权角色信息
if(!CollectionUtils.isEmpty(user.getRoles())){
SimpleAuthorizationInfo simpleAuthorizationInfo = new SimpleAuthorizationInfo();
user.getRoles().forEach(role->{
simpleAuthorizationInfo.addRole(role.getName());
});
return simpleAuthorizationInfo;
}
return null;
}
/**
* @author liujianfu
* @description 认证方法
* @date 2020/10/28 16:54
* @return org.apache.shiro.authc.AuthenticationInfo
*/
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken authenticationToken) throws AuthenticationException {
System.out.println("============================================进入认证方法==================");
/** 写死的部分
//获取身份信息
String primaryPrincipal = (String) authenticationToken.getPrincipal();
System.out.println("调用验证: "+primaryPrincipal);
//根据主身份信息获取角色 和 权限信息
if("admin".equals(primaryPrincipal)) {
System.out.println("this name:"+this.getName());
return new SimpleAuthenticationInfo(primaryPrincipal,"123",this.getName());
}
return null;
**/
//根据身份信息 ,动态从数据库中加载数据
String principal = (String) authenticationToken.getPrincipal();
//在工厂中获取service对象
UserService userService = (UserService) ApplicationContextUtils.getBean("userService");
User user = userService.findByUserName(principal);
if(!ObjectUtils.isEmpty(user)){
//设置用户名,密码,随机盐
return new SimpleAuthenticationInfo(user.getUsername(),user.getPassword(),
new MyByteSource(user.getSalt()),
this.getName());
}
System.out.println("user的名字为null:"+user);
return null;
}
}
2.12 页面
login.jsp页面:
<%@page contentType="text/html; UTF-8" pageEncoding="UTF-8" isELIgnored="false" %>
<%@taglib prefix="shiro" uri="http://shiro.apache.org/tags" %>
<!doctype html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport"
content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>Document</title>
</head>
<body>
<h>先访问index 跳转到login ,login页面提交后,认证通过后跳转到主页面,失败回到login页面,并携带提示信息</h>
<h>欢迎观看登录界面</h><br>
<h1>用户登录</h1>
<form action="${pageContext.request.contextPath}/user/login" method="post">
用户名:<input type="text" name="username" > <br/>
密码 : <input type="text" name="password"> <br>
<input type="submit" value="登录">
</form>
错误信息:${error}
</body>
</html>
index.jsp页面:
<%@page contentType="text/html; UTF-8" pageEncoding="UTF-8" isELIgnored="false" %>
<%@taglib prefix="shiro" uri="http://shiro.apache.org/tags" %>
<!doctype html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport"
content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>Document</title>
</head>
<body>
<a href="${pageContext.request.contextPath}/user/logout">退出用户</a>
<h1>人力管理系统主页V1.0</h1>
<h>欢迎登录啊!!!</h><br>
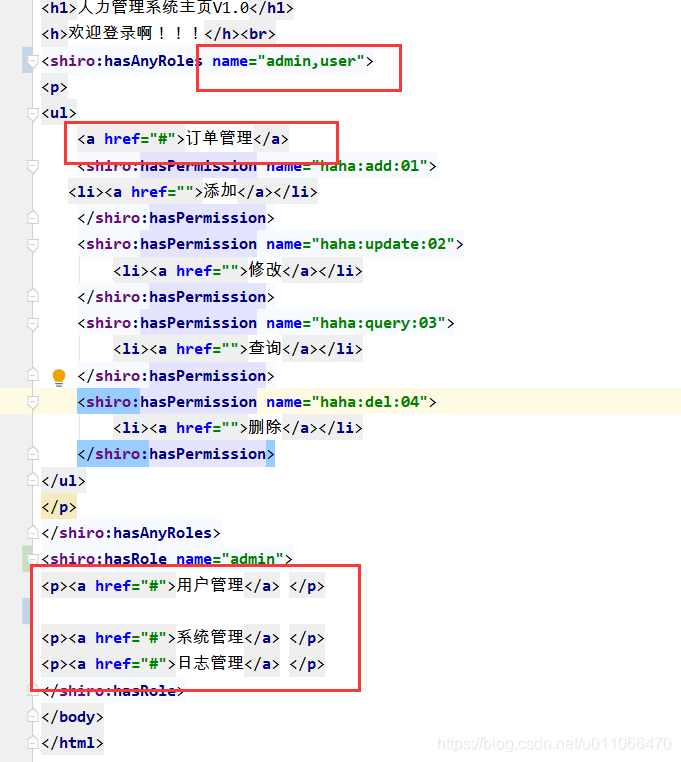
<shiro:hasAnyRoles name="admin,user">
<p>
<ul>
<a href="#">订单管理</a>
<shiro:hasPermission name="haha:add:01">
<li><a href="">添加</a></li>
</shiro:hasPermission>
<shiro:hasPermission name="haha:update:02">
<li><a href="">修改</a></li>
</shiro:hasPermission>
<shiro:hasPermission name="haha:query:03">
<li><a href="">查询</a></li>
</shiro:hasPermission>
<shiro:hasPermission name="haha:del:04">
<li><a href="">删除</a></li>
</shiro:hasPermission>
</ul>
</p>
</shiro:hasAnyRoles>
<shiro:hasRole name="admin">
<p><a href="#">用户管理</a> </p>
<p><a href="#">系统管理</a> </p>
<p><a href="#">日志管理</a> </p>
</shiro:hasRole>
</body>
</html>
三.测试访问
3.1 以用户admin进行登录:用户为admin
1.页面输入:http://localhost:8888/shiro/index 地址,走filter 因为设置/index*走验证,则跳转到login.jsp页面,所以:
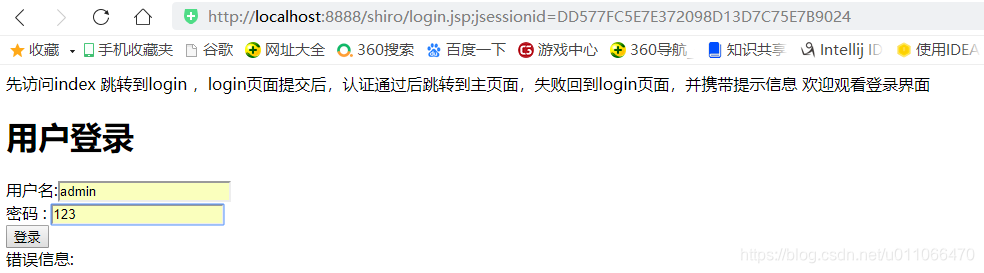
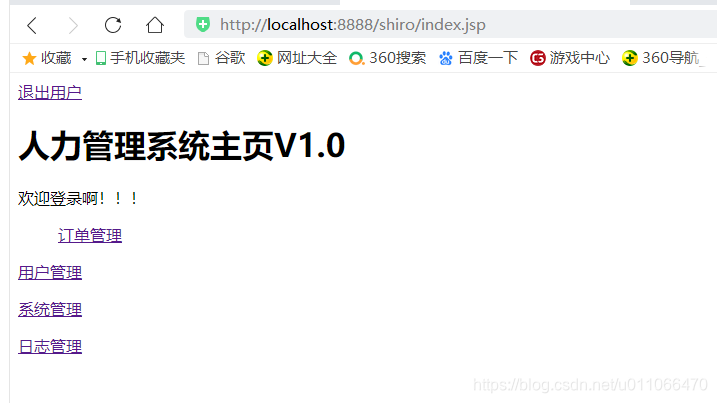
2.先访问index 跳转到login ,login页面提交后,认证通过后跳转到主页面,失败回到login页面,并携带提示信息,欢迎观看登录界面。
3.2以角色user进行登录,用户为ljf
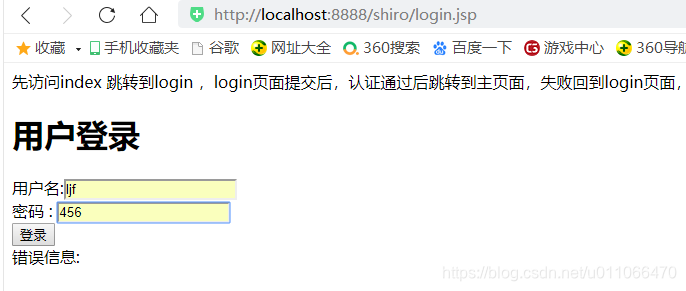
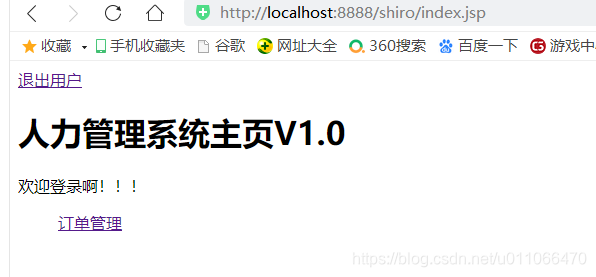
总结:实现以角色来判断,实现不同角色的授权访问
3.3 将http://localhost:8888/shiro/index设置为匿名访问
1.filter
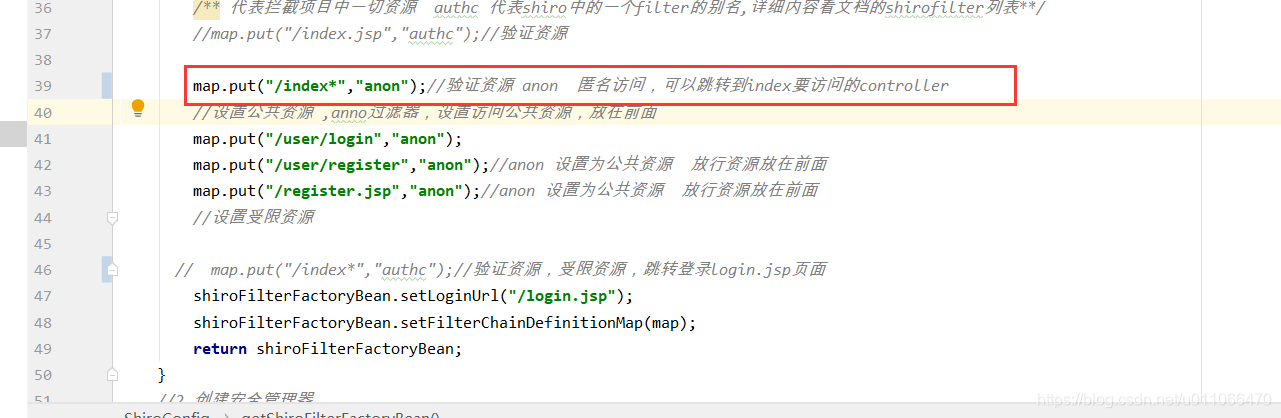
2.controller:
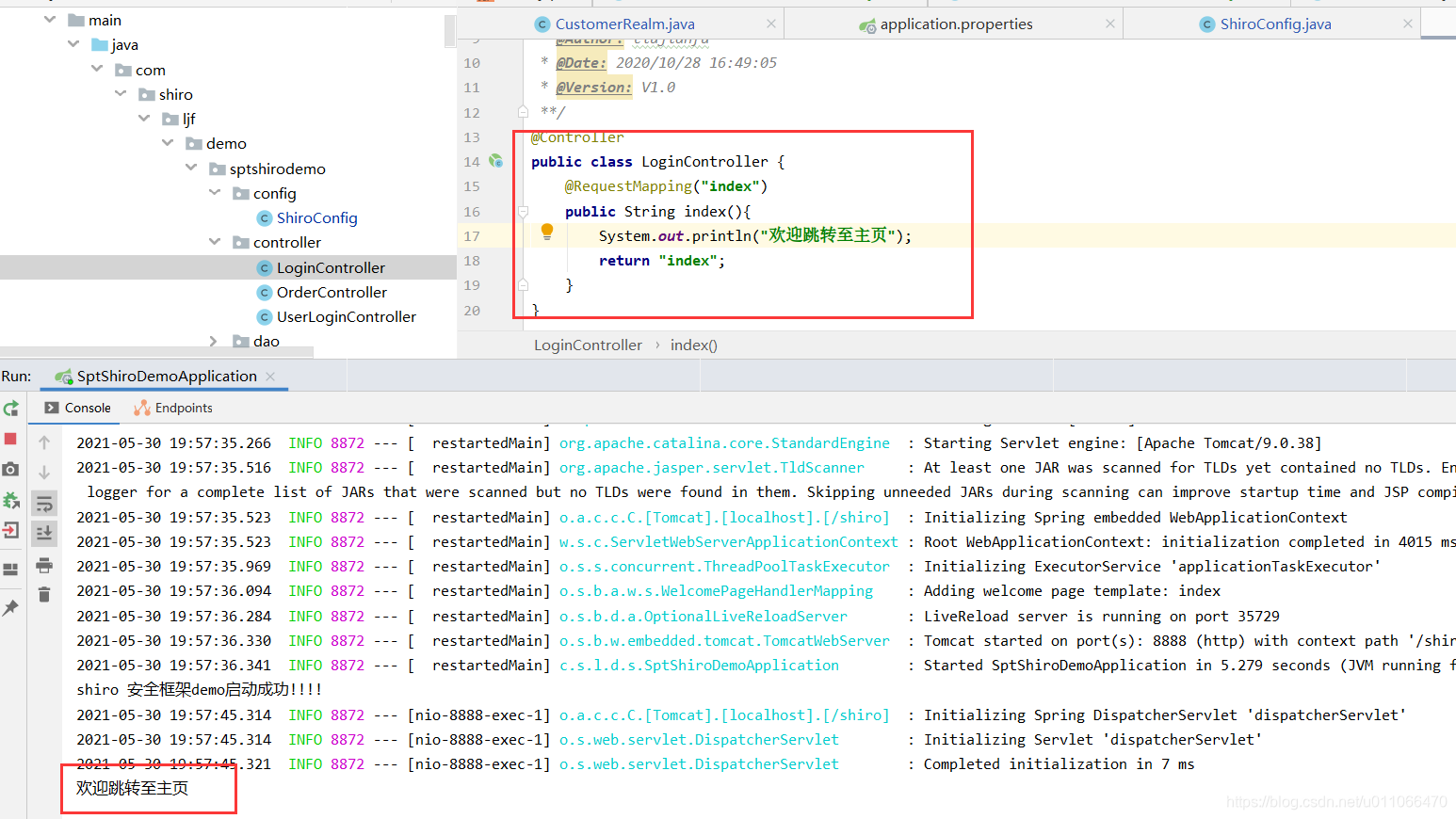
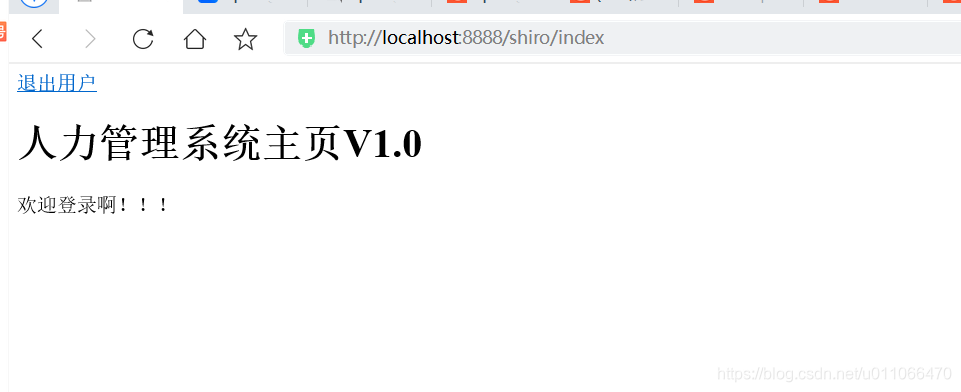
3.跳转到index.jsp页面























 409
409

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








