拒绝服务攻击与单播逆向路由转发
实验环境
Win ENSP
实验拓扑
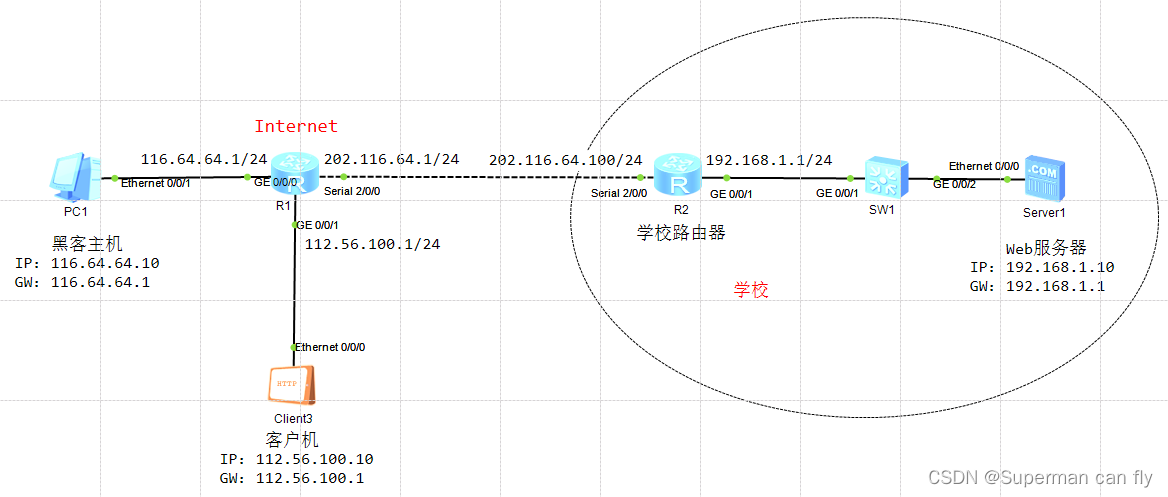
实验步骤
基本配置
路由器接口IP配置
R1
<Huawei>sys [Huawei]sys R1 [R1]undo info en [R1]int g0/0/0 [R1-GigabitEthernet0/0/0]ip add 116.64.64.1 24 [R1-GigabitEthernet0/0/0]q [R1]int g0/0/1 [R1-GigabitEthernet0/0/1]ip add 112.56.100.1 24 [R1-GigabitEthernet0/0/1]q [R1]int s2/0/0 [R1-Serial2/0/0]ip add 202.116.64.1 24 [R1-Serial2/0/0]q [R1]
R2
<Huawei>sys [Huawei]sys R2 [R2]undo info en [R2]int s2/0/0 [R2-Serial2/0/0]ip add 202.116.64.100 24 [R2-Serial2/0/0]q [R2]int g0/0/1 [R2-GigabitEthernet0/0/1]ip add 192.168.1.1 24 [R2-GigabitEthernet0/0/1]q [R2]
路由器R2静态Easy-IP配置
[R2]acl 2000 [R2-acl-basic-2000]rule 10 permit source 192.168.1.0 0.0.0.255 [R2-acl-basic-2000]q [R2]int s2/0/0 [R2-Serial2/0/0]nat outbound 2000 [R2-Serial2/0/0]q [R2]ip route-static 0.0.0.0 0.0.0.0 s2/0/0 [R2]
路由器R2静态PAT配置
[R2]int s2/0/0 [R2-Serial2/0/0]nat server protocol tcp global current-interface 80 inside 192.1 68.1.10 80 Warning:The port 80 is well-known port. If you continue it may cause function fa ilure. Are you sure to continue?[Y/N]:Y [R2-Serial2/0/0]q [R2]
验证
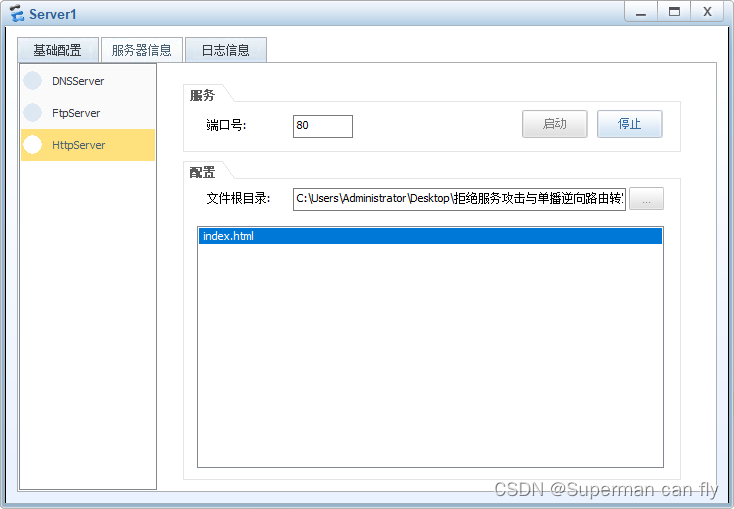
Server1
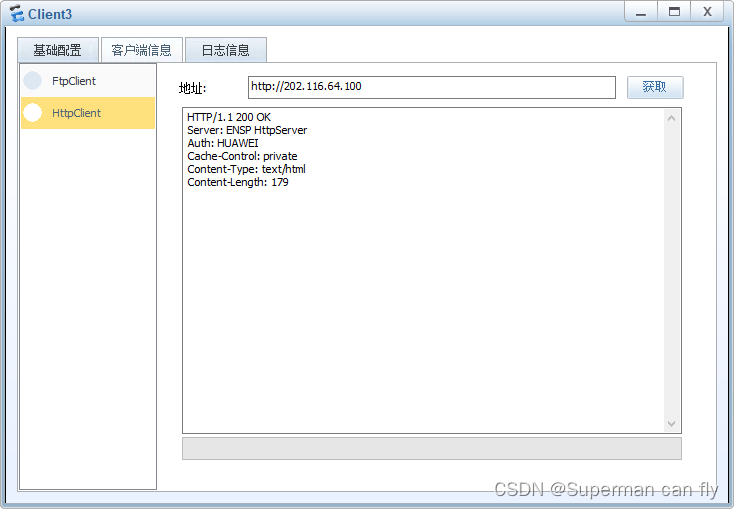
Client3
防御策略
路由器R1接口开启URPF
[R1] [R1]int g0/0/0 [R1-GigabitEthernet0/0/0]urpf strict [R1-GigabitEthernet0/0/0]q [R1]








 本文详细描述了在WinENSP环境下进行的路由器配置实验,涉及基本接口IP配置、静态Easy-IP和PAT,以及针对拒绝服务攻击的防御策略,如启用URPF。实验中展示了如何通过这些技术保护网络资源免受攻击。
本文详细描述了在WinENSP环境下进行的路由器配置实验,涉及基本接口IP配置、静态Easy-IP和PAT,以及针对拒绝服务攻击的防御策略,如启用URPF。实验中展示了如何通过这些技术保护网络资源免受攻击。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








