有道翻译两个加密,一个是sign用了MD5加密,另一个是返回值AES加密,AES的密匙还用md5加密了一下。
https://fanyi.youdao.com/index.html#/

两次请求的参数对比一下
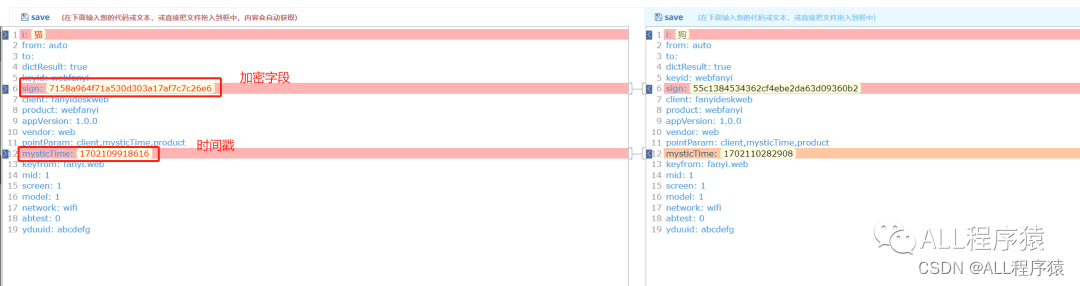
时间戳没必要管他,直接右上角搜索sign:看看
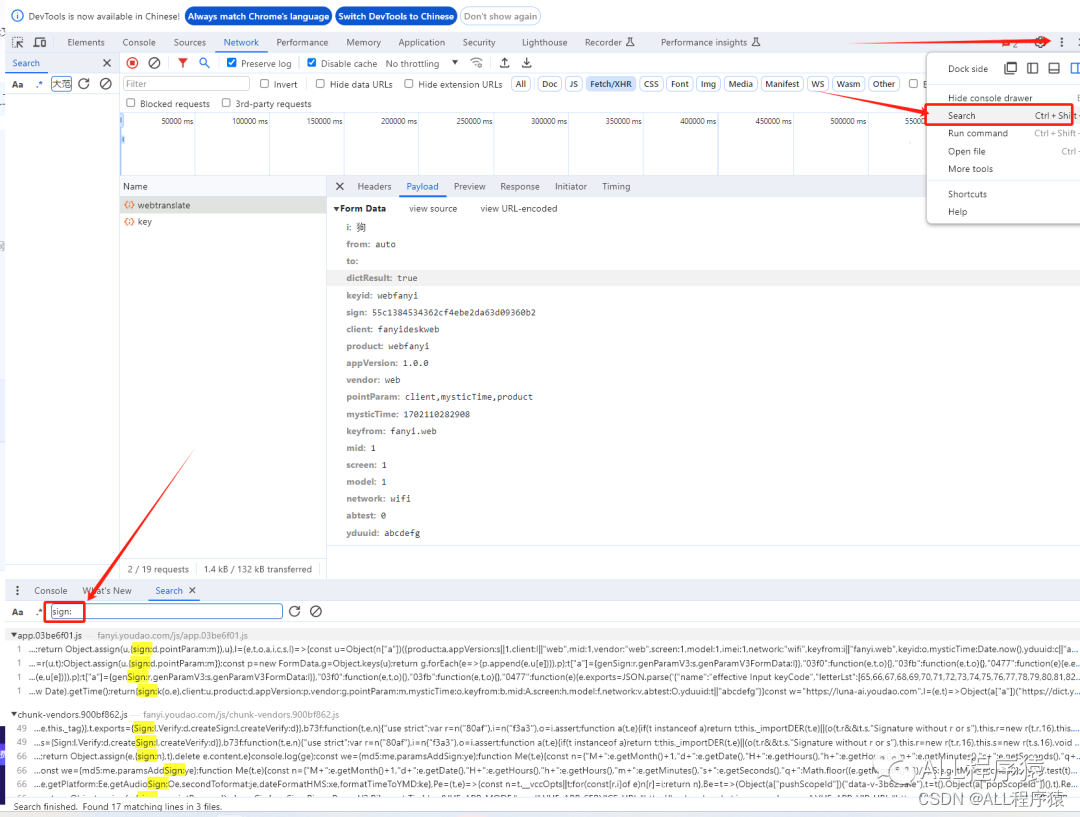
先看看第一个含有sign的,打个断点发现返回值29a…明显不对,第二个点击发现跟第一个是一样的

再点击第三个搜索结果,看看第三个含有sign的,打个断点测试一下

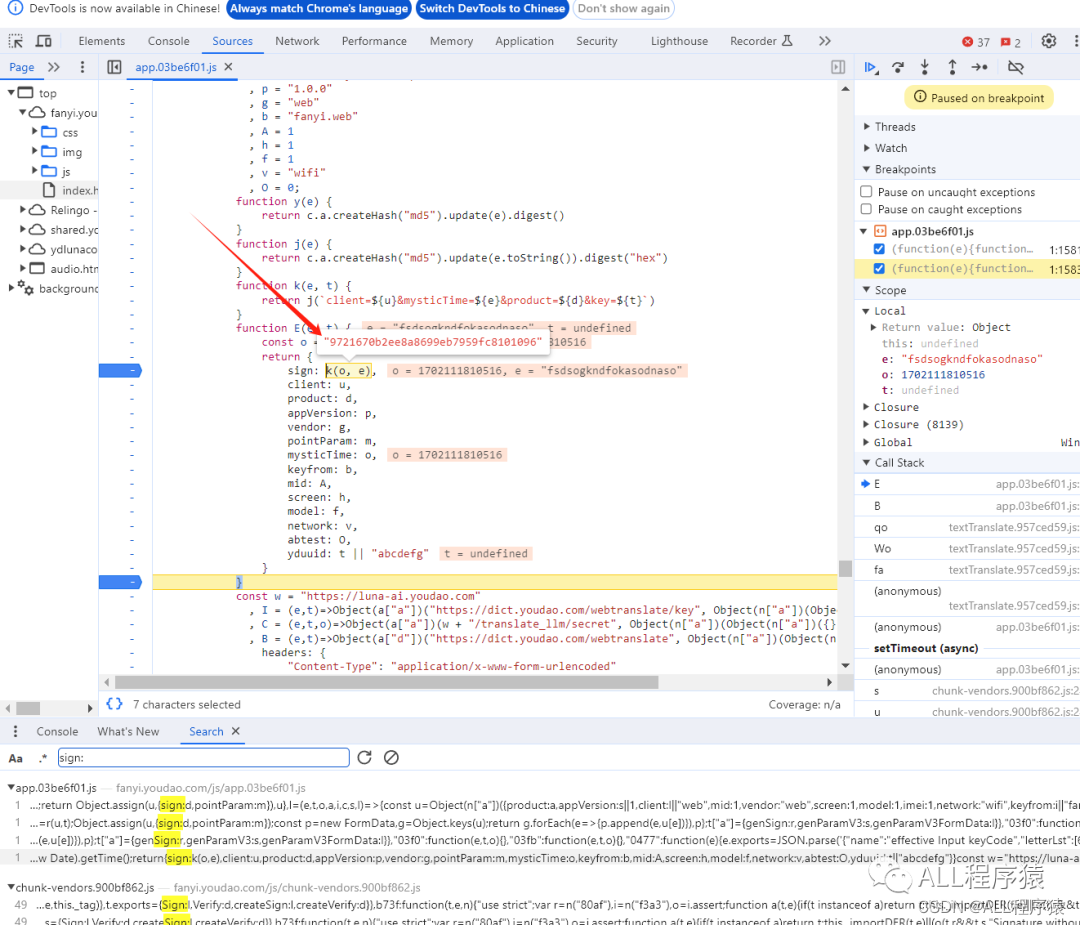
很明显这个K函数返回的就是我们需要的sign
看着这里,已经非常明显了,
k(o,e) 函数解读
o 是时间戳
e是一个固定的字符串

k函数的作用 就是组成一个 除了时间戳 不一样,其他都一样的字符串
然后交给 j函数 进行MD5加密
digest(‘hex’)的意思就是返回16进制的值

最后返回的就是sign的值
python代码如下
import time
import hashlib
mysticTime = str(int(time.time() * 1000))
u = "fanyideskweb"
d = "webfanyi"
m = "client,mysticTime,product"
p = "1.0.0"
g = "web"
b = "fanyi.web"
t = 'fsdsogkndfokasodnaso'
md5_text = f'client={u}&mysticTime={mysticTime}&product={d}&key={t}'
md5 = hashlib.md5(md5_text.encode('gb18030')).hexdigest()
print(md5)

破解了sign之后直接请求就好了
import time
import hashlib
import requests
mysticTime = str(int(time.time() * 1000))
u = "fanyideskweb"
d = "webfanyi"
m = "client,mysticTime,product"
p = "1.0.0"
g = "web"
b = "fanyi.web"
t = 'fsdsogkndfokasodnaso'
md5_text = f'client={u}&mysticTime={mysticTime}&product={d}&key={t}'
md5 = hashlib.md5(md5_text.encode('gb18030')).hexdigest()
headers = {
'user-agent': "Mozilla/5.0 (Windows; U; MSIE 9.0; Windows NT 9.0; en-US)",
'Cookie': 'OUTFOX_SEARCH_USER_ID=567189402@221.11.95.91; OUTFOX_SEARCH_USER_ID_NCOO=362527382.55008763; OUTFOX_SEARCH_USER_ID=239533326@221.11.95.145; DICT_SESS=v2|7iTj5Z0ZrypukMJL0MpB0qLRfQLRLpBRUA0HkG6LeZ0e4OLlGRHQBROGkMzGO4TFRPyhHQSh4QB06B0fqBnHwZ0UG0LwzO4gL0; DICT_LOGIN=1||1702024370417; DICT_UT=urs-phoneyd.1d7632702a3d43ef9@163.com',
'Accept': 'application/json, text/plain, */*',
'Origin': 'https://fanyi.youdao.com',
'Referer': 'https://fanyi.youdao.com/',
'Host': 'dict.youdao.com',
'Accept-Encoding': 'gzip, deflate, br',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Connection': 'keep-alive',
'Content-Length': '318',
'Content-Type': 'application/x-www-form-urlencoded',
}
data = {
'i': '小猫',
'from': 'auto',
'to': '',
'dictResult': 'true',
'keyid': 'webfanyi',
'sign': md5,
'client': 'fanyideskweb',
'product': 'webfanyi',
'appVersion': '1.0.0',
'vendor': 'web',
'pointParam': 'client,mysticTime,product',
'mysticTime': mysticTime,
'keyfrom': 'fanyi.web',
'mid': '1',
'screen': '1',
'model': '1',
'network': 'wifi',
'abtest': '0',
'yduuid': 'abcdefg',
}
url = 'https://dict.youdao.com/webtranslate'
response = requests.post(url, data=data, headers= headers)
print(response)
print(response.text)

响应码200,说明请求成功了,返回值加密罢了。
首先还是sign那里打断点,然后运行,追踪。点击调用栈往下一个追踪
具体细节自己看公众号吧
完整代码如下
import requests
import re
import random
import json
import time
import hashlib
import base64
from Crypto.Cipher import AES
def user_agent_random():
"""
随机选择一个User-Agent字符串
Returns:
dict: 随机选择的User-Agent字符串作为请求头
"""
user_agent_list = [
"Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; AcooBrowser; .NET CLR 1.1.4322; .NET CLR 2.0.50727)",
"Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0; Acoo Browser; SLCC1; .NET CLR 2.0.50727; Media Center PC 5.0; .NET CLR 3.0.04506)",
"Mozilla/4.0 (compatible; MSIE 7.0; AOL 9.5; AOLBuild 4337.35; Windows NT 5.1; .NET CLR 1.1.4322; .NET CLR 2.0.50727)",
"Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0; Acoo Browser; SLCC1; .NET CLR 2.0.50727; Media Center PC 5.0; .NET CLR 3.0.04506)",
"Mozilla/4.0 (compatible; MSIE 7.0; AOL 9.5; AOLBuild 4337.35; Windows NT 5.1; .NET CLR 1.1.4322; .NET CLR 2.0.50727)",
"Mozilla/5.0 (Windows; U; MSIE 9.0; Windows NT 9.0; en-US)",
"Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET CLR 2.0.50727; Media Center PC 6.0)",
"Mozilla/5.0 (compatible; MSIE 8.0; Windows NT 6.0; Trident/4.0; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET CLR 1.0.3705; .NET CLR 1.1.4322)",
"Mozilla/4.0 (compatible; MSIE 7.0b; Windows NT 5.2; .NET CLR 1.1.4322; .NET CLR 2.0.50727; InfoPath.2; .NET CLR 3.0.04506.30)",
"Mozilla/5.0 (Windows; U; Windows NT 5.1; zh-CN) AppleWebKit/523.15 (KHTML, like Gecko, Safari/419.3) Arora/0.3 (Change: 287 c9dfb30)",
"Mozilla/5.0 (X11; U; Linux; en-US) AppleWebKit/527+ (KHTML, like Gecko, Safari/419.3) Arora/0.6",
"Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.2pre) Gecko/20070215 K-Ninja/2.1.1",
"Mozilla/5.0 (Windows; U; Windows NT 5.1; zh-CN; rv:1.9) Gecko/20080705 Firefox/3.0 Kapiko/3.0",
"Mozilla/5.0 (X11; Linux i686; U;) Gecko/20070322 Kazehakase/0.4.5",
"Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.9.0.8) Gecko Fedora/1.9.0.8-1.fc10 Kazehakase/0.5.6",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_3) AppleWebKit/535.20 (KHTML, like Gecko) Chrome/19.0.1036.7 Safari/535.20",
]
# 随机选择一个User-Agent字符串作为请求头
headers = {
'user-agent': random.choice(user_agent_list),
'Cookie': 'OUTFOX_SEARCH_USER_ID=567189402@221.11.95.91; OUTFOX_SEARCH_USER_ID_NCOO=362527382.55008763; OUTFOX_SEARCH_USER_ID=239533326@221.11.95.145; DICT_SESS=v2|7iTj5Z0ZrypukMJL0MpB0qLRfQLRLpBRUA0HkG6LeZ0e4OLlGRHQBROGkMzGO4TFRPyhHQSh4QB06B0fqBnHwZ0UG0LwzO4gL0; DICT_LOGIN=1||1702024370417; DICT_UT=urs-phoneyd.1d7632702a3d43ef9@163.com',
'Accept': 'application/json, text/plain, */*',
'Origin': 'https://fanyi.youdao.com',
'Referer': 'https://fanyi.youdao.com/',
'Host': 'dict.youdao.com',
'Accept-Encoding': 'gzip, deflate, br',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Connection': 'keep-alive',
'Content-Length': '318',
'Content-Type': 'application/x-www-form-urlencoded',
}
return headers
mysticTime = str(int(time.time() * 1000))
url = 'https://dict.youdao.com/webtranslate'
headers = user_agent_random()
u = "fanyideskweb"
d = "webfanyi"
m = "client,mysticTime,product"
p = "1.0.0"
g = "web"
b = "fanyi.web"
t = 'fsdsogkndfokasodnaso'
md5_text = f'client={u}&mysticTime={mysticTime}&product={d}&key={t}'
print(md5_text)
md5 = hashlib.md5(md5_text.encode('gb18030')).hexdigest()
data = {
'i': '小猫',
'from': 'auto',
'to': '',
'dictResult': 'true',
'keyid': 'webfanyi',
'sign': md5,
'client': 'fanyideskweb',
'product': 'webfanyi',
'appVersion': '1.0.0',
'vendor': 'web',
'pointParam': 'client,mysticTime,product',
'mysticTime': mysticTime,
'keyfrom': 'fanyi.web',
'mid': '1',
'screen': '1',
'model': '1',
'network': 'wifi',
'abtest': '0',
'yduuid': 'abcdefg',
}
response = requests.post(url, data=data, headers= headers).text
print(response)
# 解密返回结果
decodeiv = "ydsecret://query/iv/C@lZe2YzHtZ2CYgaXKSVfsb7Y4QWHjITPPZ0nQp87fBeJ!Iv6v^6fvi2WN@bYpJ4"
decodekey = "ydsecret://query/key/B*RGygVywfNBwpmBaZg*WT7SIOUP2T0C9WHMZN39j^DAdaZhAnxvGcCY6VYFwnHl"
key = hashlib.md5(decodekey.encode(encoding='gb18030')).digest()
iv = hashlib.md5(decodeiv.encode(encoding='gb18030')).digest()
aes_en = AES.new(key, AES.MODE_CBC, iv)
data_new = base64.urlsafe_b64decode(response)
result = aes_en.decrypt(data_new).decode('utf-8')
print(result)
























 745
745

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








